By Dr. Marco Balduzzi
Blockchain technology continues to be widely adopted by enterprises for its numerous benefits, and it has inevitably attracted the attention of malicious actors. The secure, decentralized nature of blockchain does present a challenge to cybercriminals, yet it is not immune to attacks. Breaches to blockchain networks can lead to significant financial losses, the exposure of sensitive personal or proprietary information, and disruptions in service due to denial of service (DoS) attacks, among other consequences.
In the last part of our blockchain series, we will explore the spectrum of current and potential future threats that are intrinsically linked with the adoption of blockchain technology in enterprise environments. Our aim is to elevate awareness among businesses and stakeholders about the cybersecurity risks that accompany the benefits of blockchain. By casting light on these issues, we seek to aid organizations across the globe in bolstering their defenses and securing their digital assets against the sophisticated threats of today and tomorrow.
DefiLlama, an aggregator of decentralized financial information, reports that hacks have resulted in losses exceeding US$200 million in just June 2024 alone, with the cumulative total reaching over US$8 billion. Comparing this with Zeus, which was once considered the largest and most lucrative botnet ever, the financial impact of blockchain threats is staggering, accounting for more than 115 times the losses. Between 2007 and 2010, members of the Zeus gang stole a total of US$70 million.
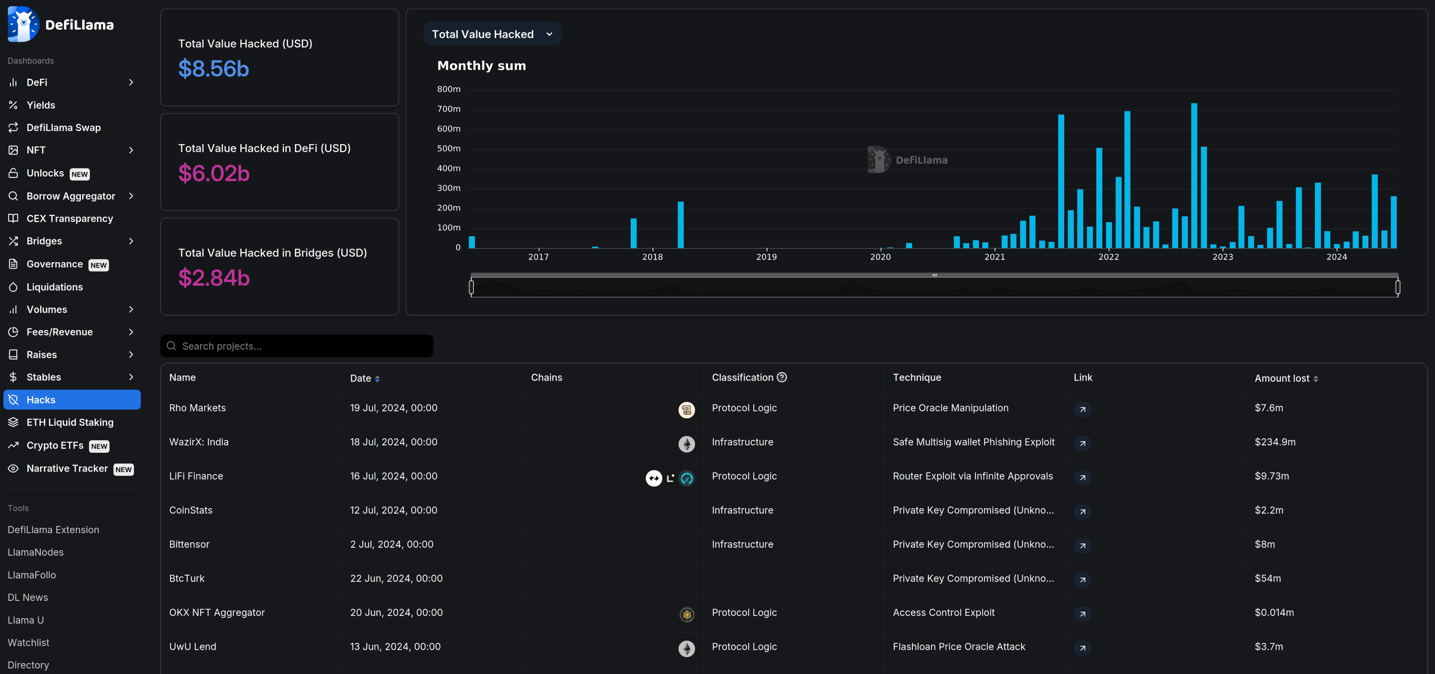
Figure 9. Reports on DefiLlama hacks
Source: defillama.com
Rekt, another popular website tracking public hacks against the blockchain ecosystem, reports a similar situation with millions of dollars stolen daily. For example, on July 22, 2024, an exit scam targeting regular users lead to a total loss of over US$2 million. The same website features a leaderboard of the most significant hacks; by aggregating the losses from the top 10 hacks, the total amounts to US$5 billion over the past three years, corroborating the reports from DefiLlama.

Figure 10. Rekt’s leaderboard of hacks
Source: rekt.news
Setting aside the hacks against blockchains, which represent just a subset of all malicious activities within the blockchain ecosystem, let us now turn our attention to the amount of money transferred through addresses identified as illicit.
Chainalysis, a platform for blockchain analysis and threat intelligence, estimates the market for crypto crime to be at US$24.2 billion dollars for 2023. As the report rightly points out, these figures represent conservative estimates based on the illicit addresses that have been identified to date. It is likely that one year from now, these totals will have increased as more addresses are flagged as illicit. For example, the 2023 report initially estimated the illicit transaction volume for 2022 to be 20.6 billion. However, a year later (today), the revised estimate for 2022 has risen to 39.6 billion.
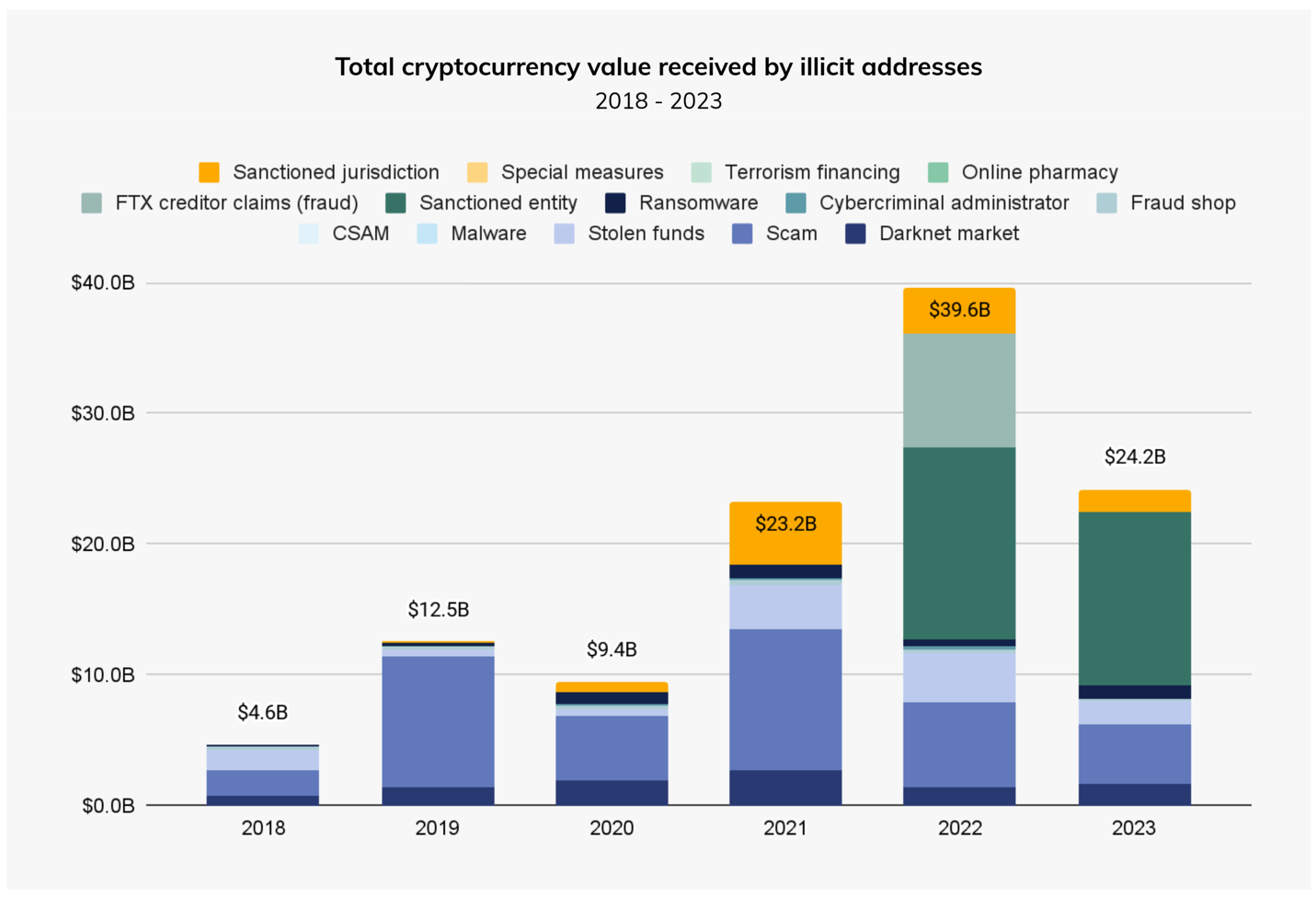
Figure 11. Total cryptocurrency value received by illicit addresses
Source: chainanalysis.com
As we have observed, blockchain technology is associated with many malicious activities. We will now examine the different categories of threats that this technology encounters with specific focus on the risks associated with the adoption of private or hybrid blockchains within enterprise environments.
| Category | Threat | Discovery |
|---|
| Smart Contract Exploits | Vulnerability Exploits | Bugs or vulnerabilities in smart contracts can be exploited to execute unauthorized actions, steal funds, or alter the intended functionality of the contract. |
| Logic Flaws | Flaws in the smart contract logic can be manipulated to produce unintended outcomes or drain resources. |
| Inside Attacks | Privilege Abuse | An insider with administrative access could alter records, disrupt services, or leak sensitive data. |
| Collusion | Multiple insiders could coordinate to compromise the blockchain’s integrity, potentially rewriting transaction histories or forging consensus. |
| Data Integrity Attacks | Chain pollution | Insertion of false data into the blockchain, which can undermine the trust and veracity of the chain. |
| Tampering | Data can be intercepted and altered before being recorded on the blockchain, especially if communication channels are insecure. |
| Replay Attacks | Attackers capture and retransmit valid transactions to create duplicates, disrupting the transaction history. |
| Consensus Mechanism Attacks | 51% Attack | In private blockchains with a limited number of nodes, an entity controlling the majority of nodes could dominate the consensus mechanism, allowing for double-spending or altering transaction records. |
| Sybil Attack | Attackers create multiple fake nodes to gain majority control over the network, manipulating the consensus process or flooding the network. |
| Interoperability issues | Potential protocol mismatches when working with multiple chains or using exchanges. |
| DDoS Attacks | Network Overload | Attackers flood the network with excessive traffic, overwhelming nodes and causing legitimate transactions to fail or be delayed. |
| Node Targeting | Specific nodes are targeted to disrupt the network's functionality, potentially leading to a breakdown in consensus. |
| Endpoint Attacks | Compromised Devices | Devices used to interact with the blockchain can be compromised, allowing attackers to intercept transactions, alter data, or steal credentials. |
| Man-in-the-Middle (MitM) Attacks | Attackers intercept and possibly alter the data exchanged between endpoints and the blockchain, compromising transaction integrity and confidentiality. |
| Software and Configuration Attacks | Exploiting Software Bugs | Vulnerabilities in the blockchain software can be exploited to cause crashes, unauthorized access, or data manipulation. |
| Configuration Errors | Misconfigured nodes or network settings can open vulnerabilities that attackers can exploit to gain unauthorized access or disrupt operations. |
| Cryptographic Attacks | Key Management Attacks | Poor key management practices can lead to the exposure or theft of cryptographic keys, compromising the security of the blockchain. |
| Breaking Encryption | Advances in computing power (e.g., quantum computing) or cryptographic techniques could potentially break the encryption used to secure blockchain transactions and data. |
| Targeted Scams | Phishing | Phishing attacks can trick users into revealing their credentials, allowing attackers to gain unauthorized access to the blockchain. |
| Social Engineering | Attackers manipulate individuals into performing actions or divulging confidential information that can compromise the blockchain’s security. |
Table 2. Threats associated with blockchain technology
Business impact
In this section, we will elaborate on the business impacts that may arise from potential breaches of enterprise blockchains. Given blockchain's wide applicability for solving specific problems — as previously detailed, such as improving supply chain item tracking or reducing the costs associated with claim reconciliations — the specific impacts of breaches can vary from one use case to another. Nevertheless, the information described here is generalized and intended to apply to a broad range of use cases.
| Category | Impact | Description |
|---|
| Data Integrity and Confidentiality | Data Tampering | Successful attacks can compromise the integrity of the data stored on the blockchain, leading to incorrect or manipulated records, which can impact decision-making and operational accuracy. |
| Confidential Information Exposure | Unauthorized access can result in the exposure of sensitive information, including intellectual property, trade secrets, or personal data of customers and employees. |
| Financial Loss | Direct Financial Impact | Attacks such as theft of assets via smart contract exploits or key management failures can lead to direct monetary losses. |
| Operational Disruption | Downtime resulting from DDoS attacks or compromised nodes can significantly disrupt business operations, resulting in revenue loss and incurring costs related to system restoration and mitigation efforts. |
| Operational Disruption | Business Continuity | Attacks can disrupt business processes, causing delays and interruptions that affect the delivery of services and products. |
| Recovery Costs | The cost of responding to and recovering from an attack, including forensic investigations, restoring data from backups, and implementing stronger security measures, can be substantial. |
| Reputational Damage | Loss of Trust | Customers, partners, and stakeholders may lose trust in the enterprise if the blockchain is compromised, affecting the company's reputation and future business prospects. |
| Brand Damage | Public knowledge of security breaches can harm the company's brand, leading to long-term reputational damage and loss of market position. |
Table 3. Business impact of breaches of enterprise blockchains
Conclusion
In this series, we have delved into the potential risks that blockchain technologies, such as those based on Ethereum, present for corporate entities. Through extensive research conducted in recent months, we have documented the growing trend of blockchain adoption among large organizations and consortiums, aimed at streamlining business operations, reducing expenses, and offering improved services on a global scale.
This rapid adoption has also attracted the attention of organized criminals and malicious actors intent on exploiting these systems for financial theft, operational sabotage, or the exfiltration of confidential data from private blockchains. Aside from external threats, enterprises face internal risks such as misconfigurations and insider threats, which can compromise the integrity and security of blockchain implementations.
Our findings emphasize the importance of raising awareness in a domain that is still maturing and often lacks the necessary expertise. As blockchain technology continues to emerge, its proper implementation and deployment within enterprise environments come with significant challenges and a high potential for error. These issues underscore the urgent need for enterprises to establish robust and secure architectures, implement thorough bug validation procedures, and maintain vigilant monitoring systems to detect and thwart potential attacks.
Before deployment, organizations must first ensure that they have a strong foundational understanding of the technology. It is important to invest in education and training for the relevant staff members, including IT professionals, developers, and security personnel. This will enable the organization to manage and maintain the blockchain effectively, as well as to develop and enforce best practices for its use.
Organizations should also establish clear policies regarding the governance of the blockchain, detailing who has authority to make changes to the ledger and under what circumstances. Regular audits should be performed to ensure compliance with these policies and to detect any irregularities.
Certainly, the auditing of smart contracts is a critical component of maintaining a secure private blockchain environment. Before deploying any smart contract, it is essential to conduct a thorough audit to examine the code for potential vulnerabilities, errors, or inefficiencies. Audits should be performed by experienced professionals who specialize in smart contract security. These experts will scrutinize the contract's codebase using both automated tools and manual inspection techniques to ensure that it behaves as intended, even under adversarial conditions. Regular audits should be scheduled, especially when contracts are updated or when the underlying blockchain platform is upgraded.
Finally, a continuous monitoring approach is needed. This involves setting up real-time monitoring systems (sort of IDSes for blockchains) that can detect unusual activities indicative of a security breach or operational anomaly. These systems should be equipped with automated alerts to notify the security team immediately when potential issues are detected. Furthermore, organizations should conduct periodic reviews of the monitoring system itself to ensure that it remains effective against evolving threats and that it is calibrated to the correct thresholds for anomaly detection.
We hope that this series will serve as a valuable resource for organizations looking to integrate blockchain networks, as well as for IT and security managers tasked with implementing adequate defensive measures to ensure the ongoing operational integrity of their enterprises.




 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One