SCADA In The Cloud - A Security Conundrum? [blog]
Two of the hottest buzzwords circulating in the IT world today are “SCADA” and “cloud computing.” Combining the two technologies has been talked about and is starting to garner more attention because of the potential cost savings, system redundancy, and uptime benefits.
Like most IT companies, industrial control system (ICS) devices can benefit from cloud use. The cloud is and will remain a viable business additive for traditional IT worldwide. SCADA devices do not differ from IT devices in that they also require redundancy, security, reduced costs, and uptime. There are several ways that SCADA in the cloud can be approached and installed, but each has their own potential security issues.
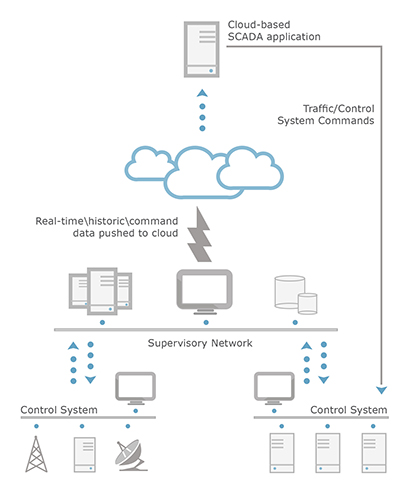
Figure 1. Example of SCADA application hosted in the cloud
Broadly speaking, there are two ways SCADA can be deployed in the cloud. It can either be completely in the cloud, or only partially. Whichever method is used, there are security concerns that should be considered and addressed prior to implementing SCADA in the cloud in any fashion. These include:
- lack of authentication
- lack of control
- lack of encryption
- nature of data
- the logging conundrum
- web application attacks
My paper SCADA in the Cloud- a Security Conundrum discusses not only these concerns, but also how to address these potential problems.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One