Botnet Rises in the Name of Chuck Norris
Publish Date: 2010年3月15日
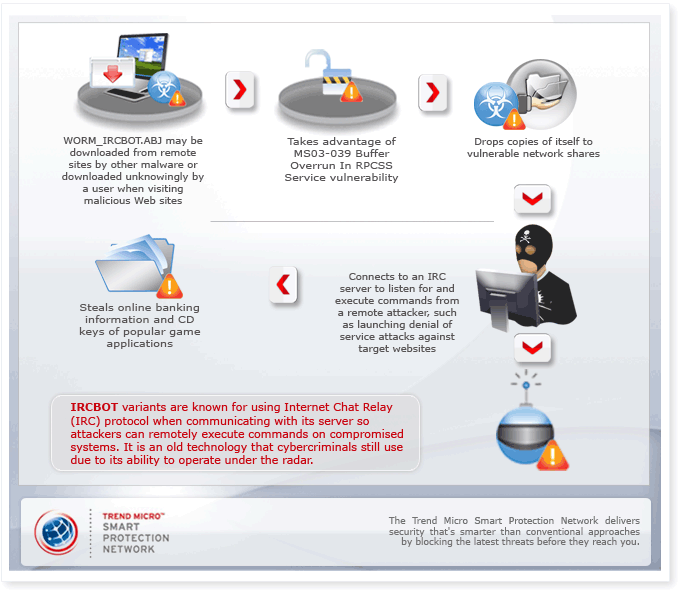
How does this threat get into users' systems?
WORM_IRCBOT.ABJ may be downloaded from remote site(s) by other malware or by an unknowing user when visiting a malicious Web site. It takes advantage of the MS03-039 Buffer Overrun In RPCSS Service vulnerability to propagate copies of itself across networks. This vulnerability systems users running Microsoft Windows NT, 2000, XP and Server 2003 platform. It tries to access a vulnerable network share by guessing usernames and passwords of password-protected systems via brute force attack.
How does this threat affect users?
WORM_IRCBOT.ABJ modifies registry entries to disable affected systems' Windows Firewall settings and disable the Restrict Anonymous and Enable DCOM features of Windows. It also has a backdoor component that allows its perpetrators to issue commands and gain complete control over the affected system.
How does this threat make money for its perpetrators?
WORM_IRCBOT.ABJ monitors the websites that the affected user visits. If the user visits an online banking website that is included in its list of target banks, this worm logs the user keystrokes to retrieve sensitive personal information such as login credentials, account numbers and PIN. It also retrieves CD key information of popular gaming applications that may be installed in the user's system.
What is the driving force behind this threat?
As in any other botnet-related attack, the perpetrators behind this attack aim to spread copies of itself to widen its network of zombie computers that they can manipulate in order to launch denial of service attacks against target websites, as well as to ultimately gain profit from the information it gathers from affected systems.
WORM_IRCBOT.ABJ may be downloaded from remote site(s) by other malware or by an unknowing user when visiting a malicious Web site. It takes advantage of the MS03-039 Buffer Overrun In RPCSS Service vulnerability to propagate copies of itself across networks. This vulnerability systems users running Microsoft Windows NT, 2000, XP and Server 2003 platform. It tries to access a vulnerable network share by guessing usernames and passwords of password-protected systems via brute force attack.
How does this threat affect users?
WORM_IRCBOT.ABJ modifies registry entries to disable affected systems' Windows Firewall settings and disable the Restrict Anonymous and Enable DCOM features of Windows. It also has a backdoor component that allows its perpetrators to issue commands and gain complete control over the affected system.
How does this threat make money for its perpetrators?
WORM_IRCBOT.ABJ monitors the websites that the affected user visits. If the user visits an online banking website that is included in its list of target banks, this worm logs the user keystrokes to retrieve sensitive personal information such as login credentials, account numbers and PIN. It also retrieves CD key information of popular gaming applications that may be installed in the user's system.
What is the driving force behind this threat?
As in any other botnet-related attack, the perpetrators behind this attack aim to spread copies of itself to widen its network of zombie computers that they can manipulate in order to launch denial of service attacks against target websites, as well as to ultimately gain profit from the information it gathers from affected systems.