Zip within A Zip Contains Locky Ransomware
Publish Date: 25 gennaio 2017
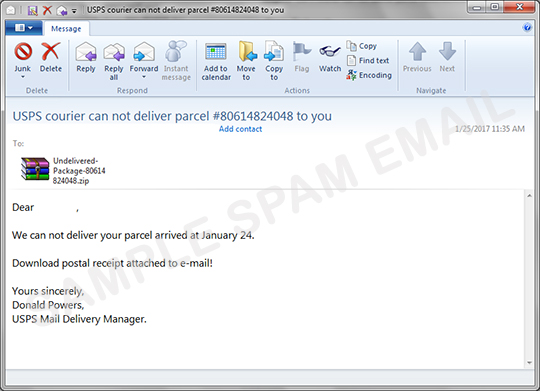
A number of users may receive an email on a supposed confirmation for their parcel delivery. This spammed message contains a .zip file that has another .zip file in it. The said .zip file has a .lnk (a file extension used by Microsoft to link to an executable file) file attachment. In this case, the said executable is a variant of the Locky ransomware family. The ransomware has the capability to lock user's machine and change desktop background with an image of a ransomware note. The note indicates instructions on how the user can decrypt files through payment.
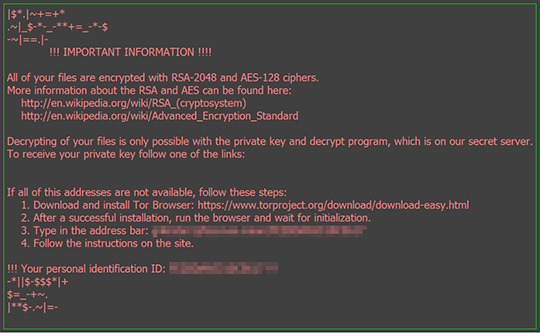
Users should be aware of unsolicited emails and never open any attachments therein. Employing security solutions with anti-spam and anti-malware techniques provide a proactive defense against such threat.
Data/ora di blocco Spam: : 25 gennaio 2017 GMT-8
TMASE
- Motore TMASE: :8.0
- Patrón TMASE: :2844