RANSOM_REDEYE.THFOGAH
Ransom:Win32/Redeye (MICROSOFT); W32/Generic!tr (FORTINET)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It drops an AUTORUN.INF file to automatically execute the copies it drops when a user accesses the drives of an affected system.
It encrypts files found in specific folders. It drops files as ransom note.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following files:
- %System Root%\Save1.txt
- %System Root%\autorun.inf
- %System Root%\Windows\Nope.txt
- %System Root%\Windows\Detect.txt
- %System Root%\Windows\AfterMBR.txt
- %System Root%\redeyebmp.bmp -> used as wallpaper
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.)
It drops the following copies of itself into the affected system:
- %User Temp%\{malware name}.exe
(Note: %User Temp% is the user's temporary folder, where it usually is C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\AppData\Local\Temp on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
Autostart Technique
This Ransomware adds the following registry entries to enable its automatic execution at every system startup:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
Windows Update = %User Temp%\{malware name}.exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
Windows Update = %User Temp%\{malware name}.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Winlogon
Shell = %User Temp%\{malware name}.exe
Other System Modifications
This Ransomware adds the following registry entries as part of its installation routine:
HKEY_CURRENT_USER\Control Panel\Desktop
WallPaper = %System Root%\redeyebmp.bmp
HKEY_CURRENT_USER\Software\ShortCutInfection
Mr.Wolf = True
It modifies the following registry entries:
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows Defender
DisableAntiSpyware = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows Defender
DisableRoutinelyTakingAction = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
System
WindowsDefenderMAJ = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
System
WindowsDefenderMAJ = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows Script Host\Settings
Enabled = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows Script Host\Settings
Enabled = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_CURRENT_USER\Software\Policies\
Microsoft\Windows NT\SystemRestore
DisableSR = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows NT\SystemRestore
DisableSR = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\Software\Policies\
Microsoft\Windows NT\SystemRestore
DisableConfig = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows NT\SystemRestore
DisableConfig = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\SYSTEM\CurrentControlSet\
Services
USBSTOR = 4
(Note: The default value data of the said registry entry is 3.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services
USBSTOR = 4
(Note: The default value data of the said registry entry is 3.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
System
DisableTaskMgr = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
System
DisableTaskMgr = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\SOFTWARE\Policies\
Microsoft\Windows Defender
ServiceKeepAlive = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\
Microsoft\Windows Defender
ServiceKeepAlive = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_CURRENT_USER\SOFTWARE\Policies\
Microsoft\Windows Defender\Signature Updates
ForceUpdateFromMU = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\
Microsoft\Windows Defender\Signature Updates
ForceUpdateFromMU = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_CURRENT_USER\SOFTWARE\Policies\
Microsoft\Windows Defender\Signature Updates
UpdateOnStartUp = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows
DisableCMD = 2
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows\System
DisableCMD = 2
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft
DisableCMD = 2
HKEY_CURRENT_USER\Software\Policies\
Microsoft\Windows
DisableCMD = 2
HKEY_CURRENT_USER\Software\Policies\
Microsoft\Windows\System
DisableCMD = 2
HKEY_CURRENT_USER\Software\Policies\
Microsoft
DisableCMD = 2
HKEY_CURRENT_USER\Software\Policies\
Microsoft\MMC\{8FC0B734-A0E1-11D1-A7D3-0000F87571E3}
Restrict_Run = 1
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\MMC\{8FC0B734-A0E1-11D1-A7D3-0000F87571E3}
Restrict_Run = 1
HKEY_CURRENT_USER\SOFTWARE\Policies\
Microsoft\Windows Defender\Real-Time Protection
DisableRealtimeMonitoring = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\
Microsoft\Windows Defender\Real-Time Protection
DisableRealtimeMonitoring = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\SYSTEM\CurrentControlSet\
Services
SecurityHealthService = 4
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services
SecurityHealthService = 4
(Note: The default value data of the said registry entry is 2.)
HKEY_CURRENT_USER\SYSTEM\CurrentControlSet\
Services
WdNisSvc = 3
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services
WdNisSvc = 3
(Note: The default value data of the said registry entry is 2.)
HKEY_CURRENT_USER\SYSTEM\CurrentControlSet\
Services
WinDefend = 3
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services
WinDefend = 3
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
System
EnableLUA = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
NoControlPanel = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
NoRun = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
NoRun = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
System
DisableRegistryTools = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
System
DisableRegistryTools = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
NoDrives = 4
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
NoDrives = 4
File Infection
This Ransomware avoids infecting the following files:
- desktop.ini
Propagation
This Ransomware drops the following copies of itself in all physical and removable drives:
- {Logical Drives}:\windows.exe
It drops an AUTORUN.INF file to automatically execute the copies it drops when a user accesses the drives of an affected system.
Process Termination
This Ransomware terminates the following processes if found running in the affected system's memory:
- SbieCtrl
- ProcessHacker
- procexp64
- msconfig
- taskmgr
- chrome
- firefox
- regedit
- opera
- UserAccountControlSettings
- yandex
- microsoftedge
- microsoftedgecp
- iexplore
Other Details
This Ransomware connects to the following URL(s) to get the affected system's IP address:
- http://{BLOCKED}.{BLOCKED}tic.com/
It does the following:
- Modifies lnk files to point to:
cmd.exe "" /c start &explorer /root,\ {malware path}\" & exit - Disables the following programs on a 64bit machine:
- a2start.exe
- AdwCleaner.exe
- attrib.exe
- Autoruns.exe
- Autoruns64.exe
- bcdedit.exe
- chrome.exe
- cmd.exe
- ComboFix.exe
- control.exe
- csrss.exe
- explorer.exe
- firefox.exe
- gpedit.msc
- HitmanPro.exe
- HitmanPro_x64.exe
- iexplore.exe
- iExplore.exe
- iExplore64.exe
- logoff.exe
- mb3-setup-1878.1878-3.3.1.2183.exe
- mbam.exe
- microsoftedge.exe
- microsoftedgecp.exe
- mmc.exe
- MSASCuiL.exe
- msconfig.exe
- mspaint.exe
- notepad.exe
- notepad++.exe
- opera.exe
- powershell.exe
- recoverydrive.exe
- Rkill.com
- RKill.exe
- Rkill.scr
- Rkill64.com
- RKill64.exe
- Rkill64.scr
- rkill-unsigned.exe
- rkill-unsigned64.exe
- rstrui.exe
- sethc.exe
- svchost.exe
- taskkill.exe
- taskmgr.exe
- UserAccountControlSettings.exe
- userinit.exe
- wininit.exe
- winlogon.exe
- yandex.exe
- ZAM.exe
- Executes the following commands via cmd:
vssadmin delete shadows /all /quietNetSh Advfirewall set allprofiles state off"shutdown", "-r -t 00 -f" -winlogon.exe
It displays the following:
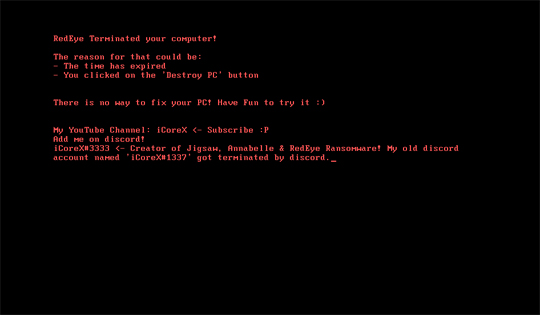
Ransomware Routine
This Ransomware encrypts files found in the following folders:
- %User Profile%\My Documents
- %User Profile%\My Music
- %User Profile%\My Pictures
- %User Profile%\Downloads
- %User Profile%\Desktop
- D:\
(Note: %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000, XP, and Server 2003, or C:\Users\{user name} on Windows Vista and 7.)
It appends the following extension to the file name of the encrypted files:
- .RedEye
It drops the following file(s) as ransom note:
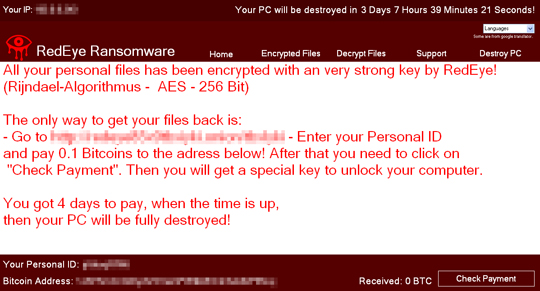
The "Destroy PC" option shows the following window:
SOLUTION
NOTES:
Restore the system from backup or reinstall the operating system (OS). The system may be made bootable by doing a system repair using a Windows installer disk.
Did this description help? Tell us how we did.


