Crypto-Ransomware Goes "International", Adds Extended Deadline
 CryptoLocker’s emergence in October 2013 was a chief example of how cybercriminals are refining their techniques and tools instead of creating new ones. Since its discovery, we have seen the emergence of many variants of crypto-ransomware. According to our findings that year, most of the detected global infections were seen in the US, while UK and Canada had their share of infections as well.
CryptoLocker’s emergence in October 2013 was a chief example of how cybercriminals are refining their techniques and tools instead of creating new ones. Since its discovery, we have seen the emergence of many variants of crypto-ransomware. According to our findings that year, most of the detected global infections were seen in the US, while UK and Canada had their share of infections as well.
Last July 2014, a crypto-ransomware known as Critroni or Curve-Tor-Bitcoin (CTB) Locker was discovered. According to our research, this particular variant, like other ransomware will encrypt files for a specific amount. However, it will not drop any text files instructing the victim how to decrypt the files, rather, it displays a large dialogue box that that prompts the user to enter a transaction ID.
Recently, we observed recent improvements to the CTB Locker malware which includes a “free decryption” service, an extended deadline to decrypt the files, and an option to change the language of the ransom message. Additionally, we have also seen an increase of these attacks in several regions mainly in Europe-Middle East Africa, China, Latin America, and in India. The CTB-Locker malware arrives via spammed emails which are sent in different languages, along with a seemingly urgent message to trick the user into opening the attachment.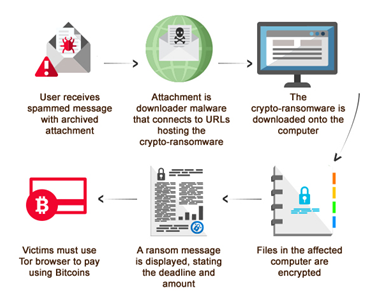
Users affected by Crypto-ransomware may find their files or documents inaccessible due to the malware’s encryption which consequently results in data loss as well as critically hampering the user’s productivity, especially if their systems contain work documents or other sensitive data.
What can you do to prevent an attack?
- Filter email messages carefully
Many users unwittingly open emails as part of their routine. However, it is important to be wary of emails coming from unverified sources. Though some emails may look legitimate in nature, it’s always best to check the sender’s address, subject line, and of course email contents for anything that appears suspicious. Do not open links embedded in emails as they are most likely malicious.
- Backup documents
Remember the 3-2-1 rule? Three backup copies of your data on two different media, and one of those copies in a separate location.
- Update your software regularly
It’s always better to be safe than sorry. Though no known ransomware were found to exploit vulnerabilities, updating your software to the latest version adds a layer of protection against general online threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks