Threat Recap: Darkside, Crysis, Negasteal, Coinminer

Insights and analysis by Miguel Ang, Raphael Centeno, Don Ovid Ladores, Nikko Tamaña, and Llallum Victoria
In the past few weeks, we have spotted notable developments for different types of threats. For ransomware, a new family named Darkside surfaced, while operators behind Crysis/Dharma released a hacking toolkit. For messaging threats, a targeted email campaign was used to propagate Negasteal/Agent Tesla. Finally, for fileless threats, a coinminer was seen bundled with legitimate applications.
Read on to know more about these findings.
Darkside ransomware surfaced
A new ransomware family named Darkside (detected by Trend Micro as Ransom.Win32.DARKSIDE.YXAH-THA) has emerged. Operators behind this ransomware threaten to publish unpaying victims’ data, a similar tactic employed by operators of ransomware families such as Maze and Nefilim. The file extension used to append the names of encrypted files is based on the victim’s MAC address.
According to the ransomware's Tor webpage, the threat actors behind the ransomware check the potential target company’s financial capability. From there, they determine how much ransom their targets will pay. It was also indicated that the operators will not attack organizations under the medical, education, non-profit, and government sectors.


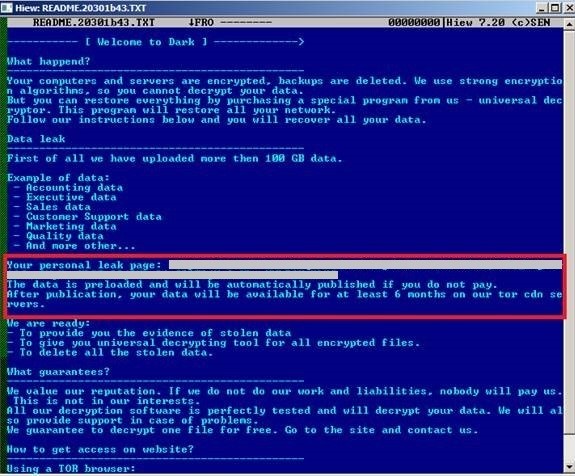
Figure 1. A Darkside ransom note
Crysis operators released a hacking tool kit
Crysis/Dharma ransomware (detected by Trend Micro as Ransom.Win32.CRYSIS.TIBGGS) has released a hacking toolkit named Toolbox, Sophos reports. Toolbox contains Mimikatz to harvest passwords, NirSoft Remote Desktop PassView to steal remote desktop protocol (RDP) passwords, Hash Suite Tools Free to dump hashes, and other tools to help find target computers and deploy the ransomware payload. With this kit, even rookie hackers can infiltrate networks easily.
Crysis operates under a ransomware-as-a-service (RaaS) model, and this hacking tool only makes it easier for affiliates to spread the ransomware to more targets.
Negasteal/Agent Tesla delivered via emails targeting bank account holders
We recently found emails that deliver Negasteal/Agent Tesla (detected by Trend Micro as TrojanSpy.MSIL.NEGASTEAL.DYSGXT) through malicious attachments. The scheme targets account holders of Krung Thai Bank. The email informs the recipient of a supposed “outward remittance transaction” worth almost US$9,000. This prompts users to download the attachment which contains a document that exploits CVE-2017-11882 (also known as Microsoft Office Memory Corruption Vulnerability), a 17-year old memory corruption issue in Microsoft Office, to download and run the malware payload.
Discovered in 2014, Negasteal has been known to send stolen information through web panel, FTP or SMTP. More recently, we spotted it being distributed through removable drives as it harvests credentials from Becky! Internet Mail.
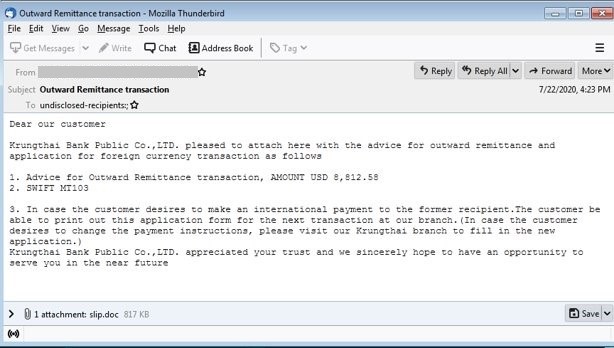
Figure 2. Sample email with malicious attachment containing Negasteal
Legitimate applications bundled with coinminer
We also found legitimate applications such as TeamViewer, Rufus, and YTD Video Downloader bundled with a fileless coinminer (detected by Trend Micro as Coinminer.Win32.MALXMR.THHADBO). These installers do not come from official download centers or app stores. Upon download, the legitimate application and a malicious script (VBS file) are dropped into the user’s system. The malicious script then connects to a site to download the coinminer loader, which will then be used to load the coinminer.
Bundling coinminers and other malware types with legitimate installers of applications (such as video conferencing apps) is not a novel strategy; however, users who are not yet too familiar with this fact might unwittingly download from suspicious sources and inadvertently compromise their systems.
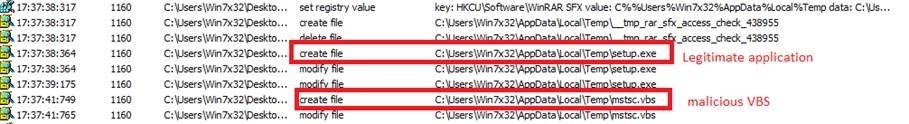
Figure 3. Coinminer bundled with TeamViewer installer
Figure 4. Obfuscated VBS file
Defense against a variety of threats
The fast-paced nature of the cybersecurity landscape means that threats emerge at every turn, creating a never-ending race between threat actors and security researchers. Enterprises and individual users should keep abreast of developments so that they can perform the necessary actions to prevent these threats from compromising their systems. As the popular adage says, “knowing is half the battle”.
To tackle a variety of threats, enterprises and users are advised to develop good security practices with the help of the following:
- Only download apps from official download centers or app stores.
- Never click links and download attachments from emails or any other messages that come from untrustworthy sources.
- Regularly update software and applications to ensure that the latest vulnerabilities are patched.
- Equip systems with security solutions that can block and defend against threats.
The following solutions can help secure against a variety of threats:
- Trend Micro Apex One™ and Apex One Endpoint Sensor – Employs behavioral analysis that protects against malicious scripts, injection, ransomware, and memory and browser attacks related to fileless threats.
- Trend Micro XDR – Connects email, endpoints, servers, cloud workloads, and networks to detect and respond to threats earlier.
- Trend Micro™ Email Security – Uses enhanced machine learning and dynamic sandbox analysis for file and URL to stop email threats.
Overall, a multilayered security approach is advised to guard all possible threat entry points.
Indicators of compromise
Darkside ransomware
| SHA-256 | Trend Micro pattern detection |
| 9cee5522a7ca2bfca7cd3d9daba23e9a30deb6205f56c12045839075f7627297 |
Ransom.Win32.DARKSIDE.YXAH-THA |
URL
- hxxp://darksidedxcftmqa[.]onion/
Crysis/Dharma ransomware
| SHA-256 | File name | Trend Micro pattern detection |
| 1cec5e4563e2c1570353e54a4ecc12ab4d896ab7227fd8651adcd56b884c0c1c | GdAgentSrv.de.dll | HackTool.Win64.CVE20160099.A |
| 28042dd4a92a0033b8f1d419b9e989c5b8e32d1d2d881f5c8251d58ce35b9063 | process-hacker-2-39.exe | PUA.Win32.ProcHack.A |
| 3680b9e492f49abc108313c62ceb0f009d5ed232c874cae8828c99ebf201e075 | takeaway.exe | Ransom.Win32.CRYSIS.TIBGGS |
| 47dc3672971c242154a36622145de7060f17f56af75d21e2130e4f57089f5e48 | takeaway.exe | Ransom.Win32.CRYSIS.TIBGGS |
| 75d9d85b152e030eb73d17c691203b49bf593ea6a4bddeae48ca255b22c2d36d | takeaway_ps1 | Trojan.PS1.CRYSIS.AA |
| 77cbab006cf6a801dbd1c752659bddf28562fb8681d20305dd1dc0b1e105c67a | takeaway.exe | Ransom.Win32.CRYSIS.TIBGGS |
| 78983ad10fe05fadccb201dd3e8c7f952e93332433a42e3d331531c5497d1330 | winhost.exe | Ransom.Win32.CRYSIS.TIBGGQ |
| b0b8fd4f6ab383014ea225c2b7776735af059f526cd7c4fdbdcb2e99d074ade7 | takeaway.exe | Ransom.Win32.CRYSIS.TIBGGS |
| b2d2f4ecbc680d590743044744b3ff33c38e4aeb0ada990b0ae7be8291368155 | takeaway.exe | Ransom.Win32.CRYSIS.TIBGGS |
| b5a69f7c4a3681a753f3512e3b36ac06c6ddbb1129a3e87f8c722ff4f9834f0a | purgeMemory.ps1 | Trojan.PS1.KILLSVC.Ahacktool |
| edef024abe48d6ed7b4757d63a8fd448a8ecf1ad15afd39cc97c97b27ed4498e |
takeaway.exe | Ransom.Win32.CRYSIS.TIBGGS |
| ef5f2ce1a4d68d656400906ae906b0c7e7f61017f14840a7ac145d59ee69a4bd | takeaway.exe | Ransom.Win32.CRYSIS.TIBGGS |
| f47e3555461472f23ab4766e4d5b6f6fd260e335a6abc31b860e569a720a5446 | NS2.ex | HackTool.Win32.NetTool.A |
Negasteal/Agent Tesla
| SHA-256 | Trend Micro pattern detection |
| 58e74875b3659fa34aa1ecefba1a43cc049b7bb1c83de5a26ec8045c60f1099e |
Trojan.W97M.CVE201711882.YQUOOUM |
| 6991150c06b278712b052377ef768ca80923ff9c3396e7de18fa0fbce7211c96 | TrojanSpy.MSIL.NEGASTEAL.DYSGXT |
Coinminer
| SHA-256 | Trend Micro pattern detection | Trend Micro machine learning detection |
| 12434186b803afd5e75b77bf8439d968 ef0bb18ed8a871a279b95fe0a6c4e132 |
Coinminer.Win32.MALXMR.THHADBO |
Troj.Win32.TRX.XXPE50FFF036 |
| 2da7be1ed9f13424c7b747caea0030b5 b19007597640e9700add15bc8d236a1e |
Trojan.Win32.MALXMR.THHADBO | Not Applicable |
| 329788672911aaed64ba2add41a09f93 b878bf8a3291c1309988acadb3643141 |
Trojan.VBS.MALXMR.THHADBO | Not Applicable |
| 663e4b7c209e864faaf598d791a9a6958 c70f75bf974853d59bd15bc2a931163 |
Trojan.Win32.MALXMR.BX | Not Applicable |
| 9dade12201cc88cbd90f2fbaf4d50e51 2d4a377debad6714f19e10195e3a91be |
Trojan.Win32.MALXMR.BX | Not Applicable |
| a24f84fa1302c9f4b68791532d2d7dbb 0269e2ac2f245652164934289a1ba37e |
Trojan.Win32.MALXMR.BX | Not Applicable |
| a78c0bd4cf9f4e21dea1fa67e92a6498 c5df83c3ae57bb1f02d40da44e55cd69 |
Coinminer.Win32.MALXMR.THHADBO | Troj.Win32.TRX.XXPE50FFF036 |
| ae54783709a60e685846b3812d4e65b 54672c8c40d2e8499fa92255ef89b7375 |
Trojan.Win32.MALXMR.BX | Not Applicable |
| cd4b97c42b5ce9540f141498e2fdd4d5 66ea0b835d0c295994bf644744b5d4dd |
Trojan.Win32.MALXMR.BX | Not Applicable |
URLs
- hxxps://pastebin[.]com/raw/jimA8sdx
- hxxp://135[.]181[.]34[.]1/min3/loader23435345465446[.]jpg
- hxxps://pastebin[.]com/raw/Yvyd9wXa
- monerohash[.]com:3333
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks