By: Anjali Patil, Joelson Soares, and Jessie Prevost (Trend Micro Research)
- Information stealers were the most prevalent threat in the North American region in 2018. In the Latin American region, it was ransomware.
- Emotet, Powload, and malicious versions of Coinhive were among the most pervasive threats, and we expect their respective authors to continue developing them.
- Ransomware declined in volume but diversified in tactics and techniques.
- Cryptocurrency-mining malware presented cybercriminals with an alternative to ransomware. Nevertheless, ransomware cannot be completely written off, since cryptocurrency-mining malware is passive and doesn’t make the same easy money (or cause the same amount of damage) as ransomware.
- The vulnerabilities exploited by attackers in 2018 affected these industries the most: banking, technology, healthcare, manufacturing, and media.
- The most common file types attackers used to embed their malware in were Microsoft Office, Java, and Adobe-related files.
- In the Latin American region, banking malware affected Brazil the most because of the country's reliance on online banking.
- Based on feedback from Trend Micro’s MDR service, the majority of information stealers in the North American region (i.e., Ursnif and Emotet) arrived via email gateway, network, or endpoint.
Significant Threats in the North American Region
Data from our Smart Protection Network shows that information stealers were still the most prevalent malware type in the North American region. The pervasiveness of cryptocurrency-mining malware could be due to cryptocurrency’s popularity, while the decline in ransomware detections could be due to cybercriminals finding an alternative trade in cryptojacking or cryptocurrency-mining malware use.
Figure 2 shows that Trend Micro’s MDR service’s detections of information stealers in North America were slightly lower than those for cryptocurrency mining malware because MDR proactively blocked information stealers at the email gateway, network, and endpoint.
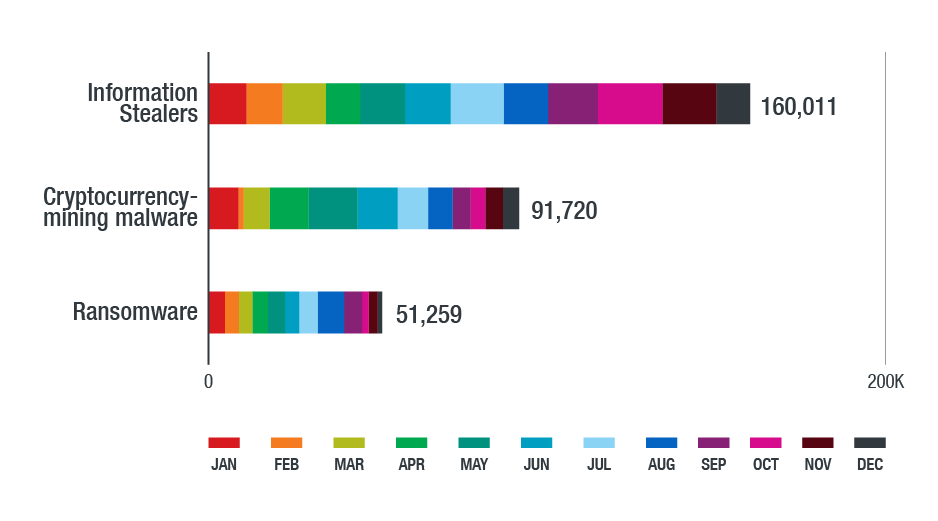
Figure 1. Detections of information stealers, cryptocurrency-mining malware, and ransomware in the North American region in 2018 (based on data from Trend Micro Smart Protection Network)
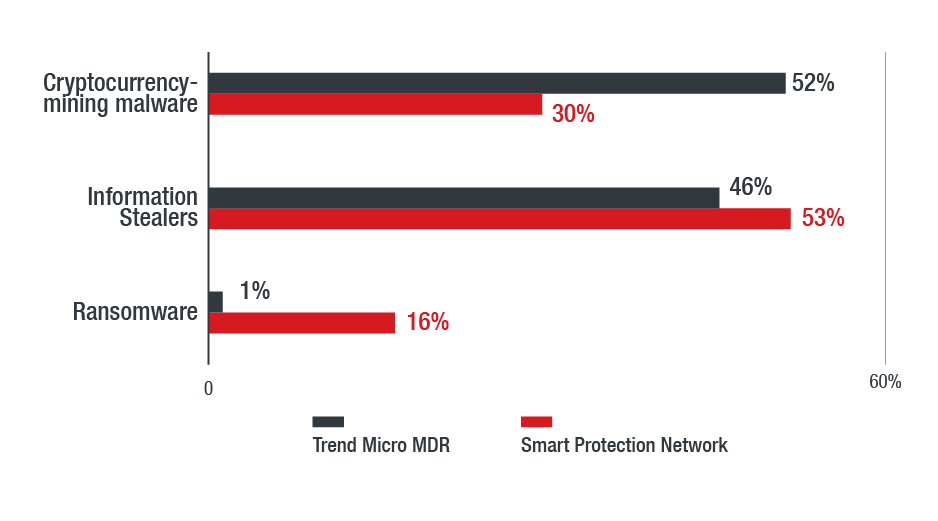
Figure 2. Comparison of detections for cryptocurrency-mining malware, information stealers, and ransomware (based on feedback from Trend Micro’s MDR sensors and Smart Protection Network)
Information Stealers Increasingly Use Fileless Techniques
Many of the threats we saw and blocked targeted Windows-based systems. Of note is the increased abuse of legitimate system administration tools such as PowerShell and Windows Scripting Host to evade detection and carry out further attacks. Powload is a classic example of an evasive threat that uses fileless techniques. It has evolved with capabilities that can bypass protections such as disabling macros inside documents or using preview mode. Indeed, data from both Smart Network Protection (Figure 3) and Trend Micro’s MDR service (Figure 4) show that Powload was the most detected threat in 2018.
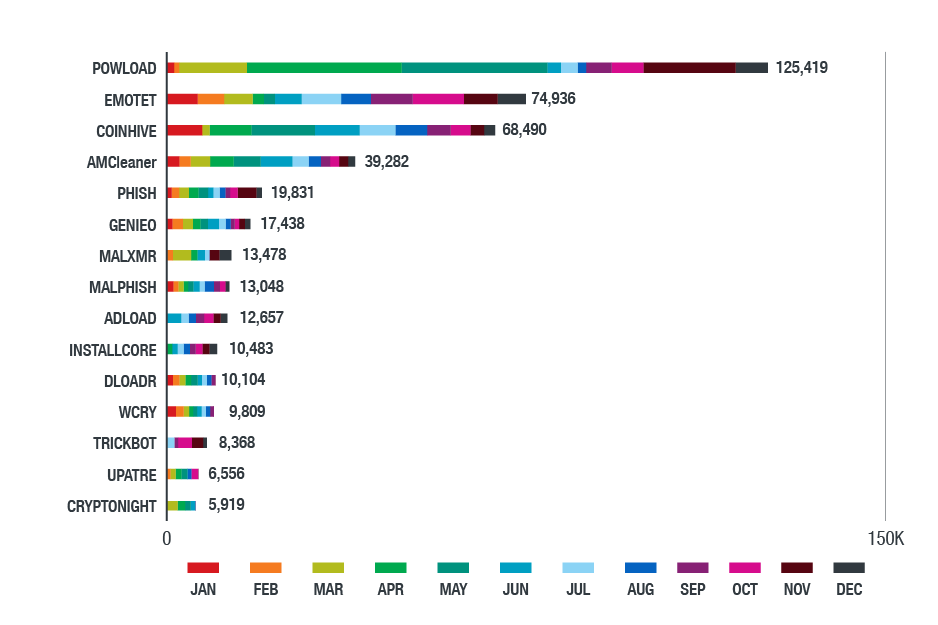
Figure 3. Top threats in the Northern American region in 2018
(based on data from Trend Micro Smart Protection Network)
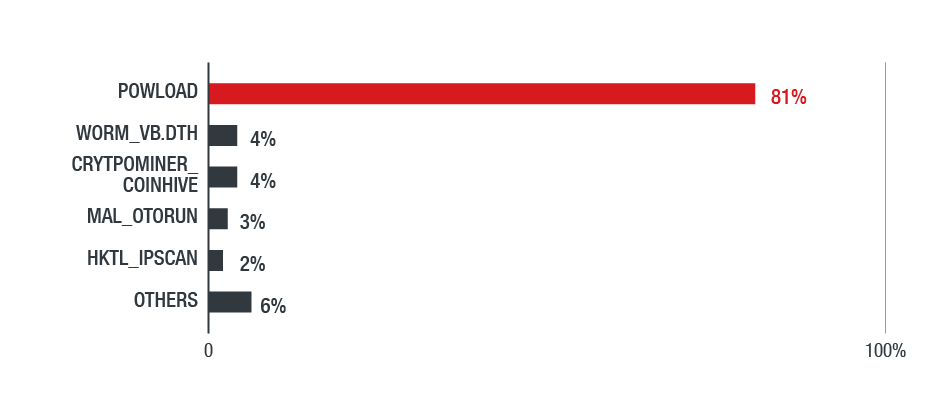
Figure 4. Distribution of top threats in the North American region in 2018
(based on feedback from Trend Micro’s MDR service)
In October, for instance, Trend Micro’s MDR team observed a huge spike of Powload-related activities in logs from monitored systems. The attackers’ modus involved hijacking email accounts and then sending attachments in response to an existing email thread that would result in the unwitting recipients downloading the data-stealing Ursnif malware. Ursnif itself went through changes in its routines and evasion tactics. The prevalence of Emotet, Ursnif, and Loki is a reflection of Powload’s pervasiveness, as these information stealers are also delivered via Powload. There were also isolated cases of worms, which had high detections simply because of the actual number of files detected in a single infection. Further, we also detected various hacking tools, which corroborate the increased instances of Powload being downloaded on endpoints via infected emails.
Apart from the notorious Emotet banking trojan, we also saw notable phishing campaigns in the North American region that delivered Ursnif via email hijacking and spam emails with attachments that redirected to phishing URLs.
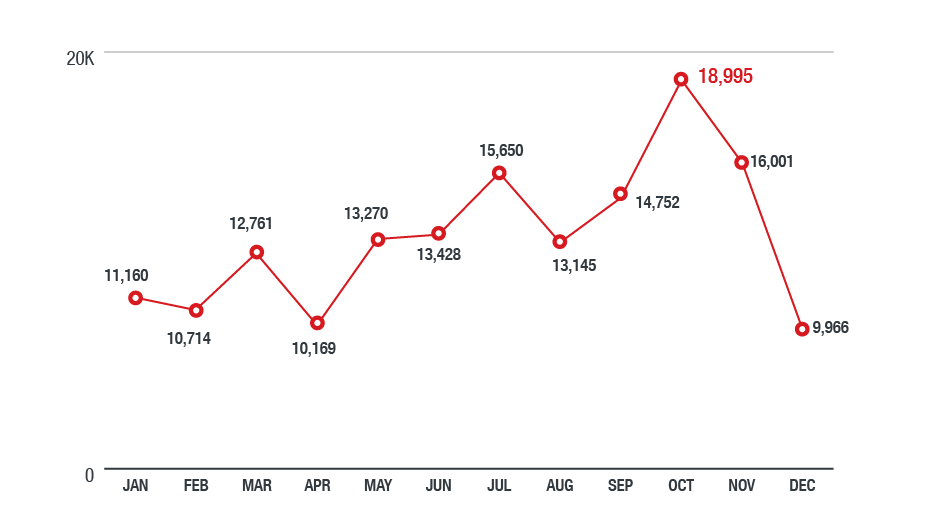
Figure 5. Detections of information-stealing malware in the North American region in 2018
(based on data from Trend Micro Smart Protection Network)
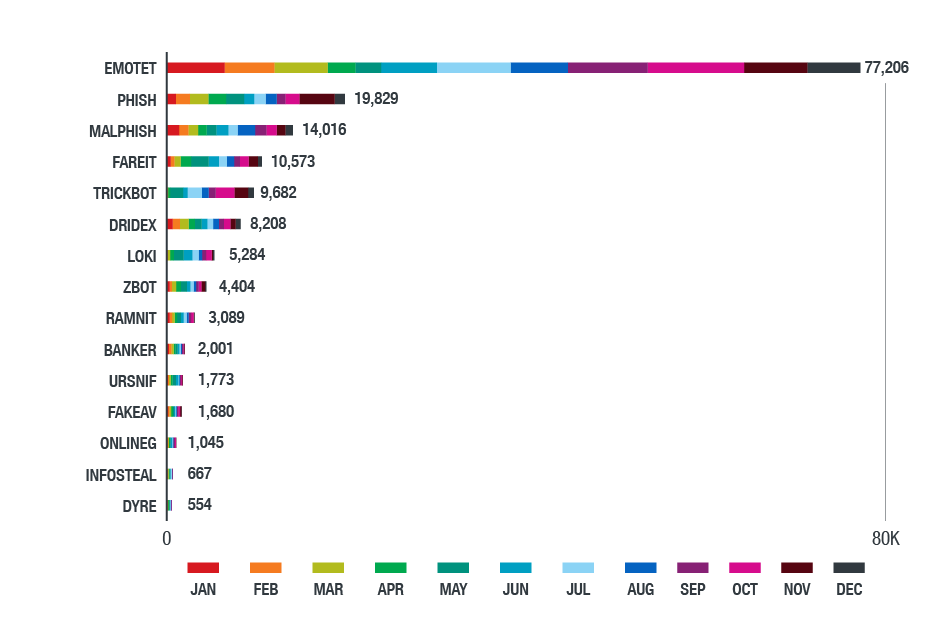
Figure 6. Top information-stealing malware in 2018 (based on data from Trend Micro Smart Protection Network)
Cryptocurrency-Mining Malware Continued to Gain Traction
Cryptocurrency-mining malware has surpassed ransomware in terms of detections. While it may not be viewed as a critical threat — by itself, it doesn’t steal data, wipe the system, or deliver other malicious payloads — it's still a security risk. Cryptocurrency-mining malware does not just steal an infected system’s computing resources and damage the system, which can result in disruptions. It also undermines the integrity of the system and its components, as well as the privacy of the data stored in it.
We also noticed that endpoints affected with cryptocurrency-mining malware tended to be more vulnerable to other types of malware. Some threats, for instance, added cryptocurrency-mining functionalities to their ransomware.
Meanwhile, Gandcrab is still the most detected ransomware family in North America, followed closely by WannaCry (WCry) and Locky. The number of ransomware families markedly decreased, but they diversified in tactics and techniques. Ransomware’s decline could be attributed to better user awareness and law enforcement's efforts in taking down its authors or distributors. With more victims refusing to pay the ransom, the stealth and seemingly easier profit gained from cryptocurrency-mining malware present a more lucrative alternative for cybercriminals.
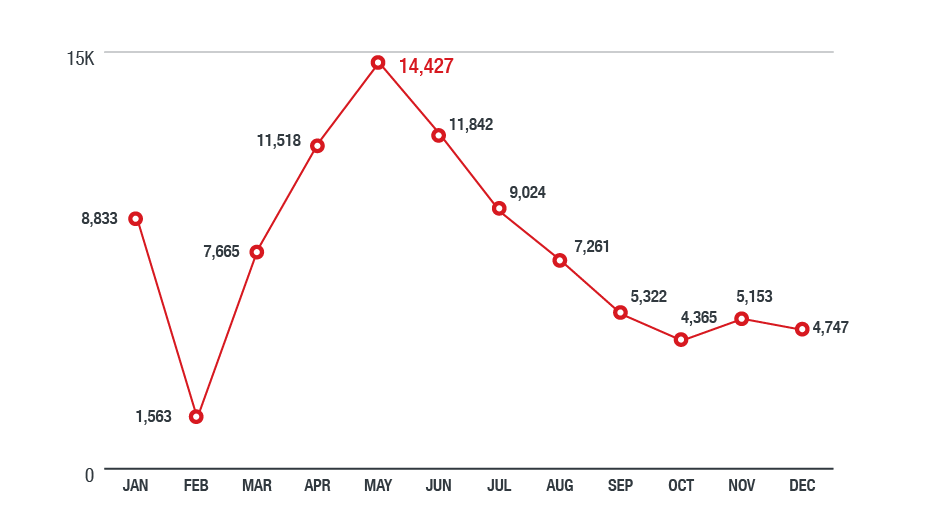
Figure 7. Detections of activities related to malicious cryptocurrency mining in the North American region in 2018 (based on data from Trend Micro Smart Protection Network)
Figure 8. Top cryptocurrency-mining malware families detected in the North American region in 2018
(based on data from Trend Micro Smart Protection Network)
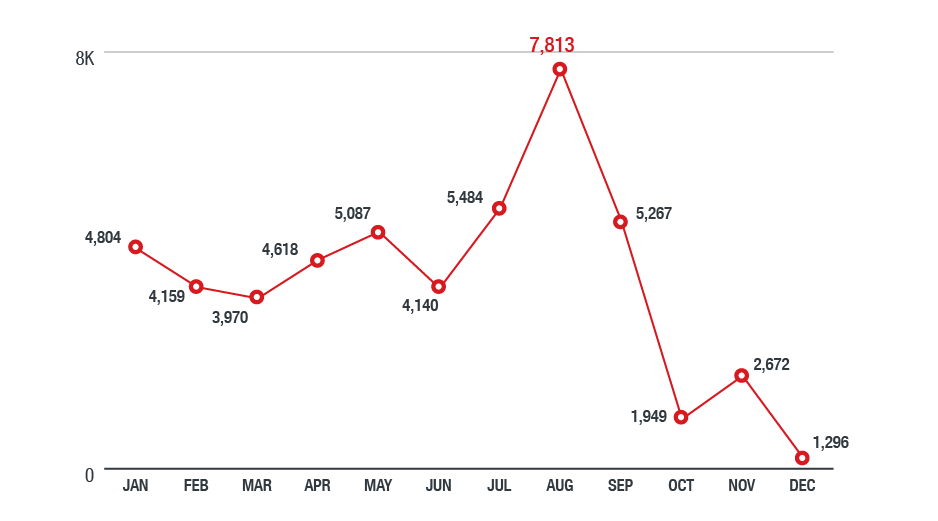
Figure 9. Ransomware detections in the North American region in 2018
(based on data from Trend Micro Smart Protection Network)
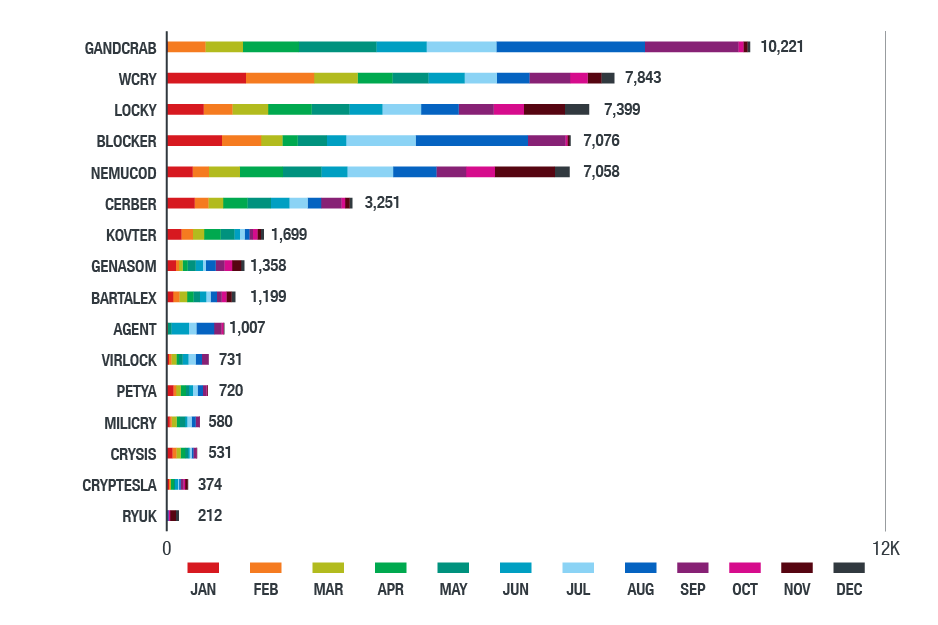
Figure 10. Top ransomware families detected in the North American region in 2018
(based on data from Trend Micro Smart Protection Network)
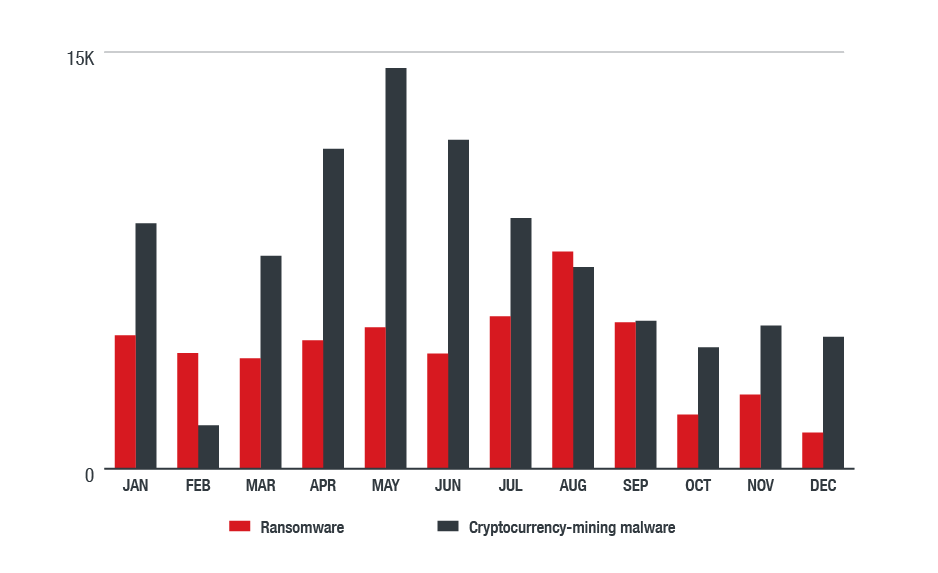
Figure 11. Comparison of detections of ransomware and cryptocurrency-mining malware in the North American region in 2018 (based on data from Trend Micro Smart Protection Network)
Vulnerabilities Affect Banking and Healthcare Industries the Most
Old vulnerabilities remain a challenge for many organizations, particularly those that might find it difficult to update mission-critical systems or networks that have to be kept up and running. The most exploited file vulnerabilities in 2018 also illustrated why information stealers like Ursnif and Loki as well as ransomware families such as WannaCry were prevalent. They are listed below in order of detections, from highest to lowest:
- CVE-2017-0147: A security flaw related to the Shadow Brokers hacking group's leak.
- CVE-2017-11882: A 17-year old vulnerability in Microsoft Office.
- CVE-2017-0199: A security flaw in the Windows Object Linking and Embedding (OLE) interface in Microsoft Office that could also be exploited via a PowerPoint slideshow.
- CVE-2017-0158: A critical vulnerability in Microsoft Internet Explorer.
- CVE-2010-0840: A vulnerability in a Java Runtime Environment component.
- CVE-2017-8570: A remote code execution vulnerability in Microsoft Office.
- CVE-2017-8759: A security flaw in .NET Framework.
- CVE-2012-1723: A critical security flaw in a Java Runtime Environment component.
- CVE-2013-2729 and CVE-2010-0188: Vulnerabilities in Adobe Reader and Acrobat.
Figure 12 shows the applications whose vulnerabilities were most exploited last year. For attackers, a standard browser is sometimes all it takes to find vulnerable sites to exploit. The industries of organizations that were most affected by exploits and malware attacks were banking/finance, healthcare, technology, manufacturing, and media. The banking/financial and healthcare sectors consistently being affected was in line with our detections for information stealers.
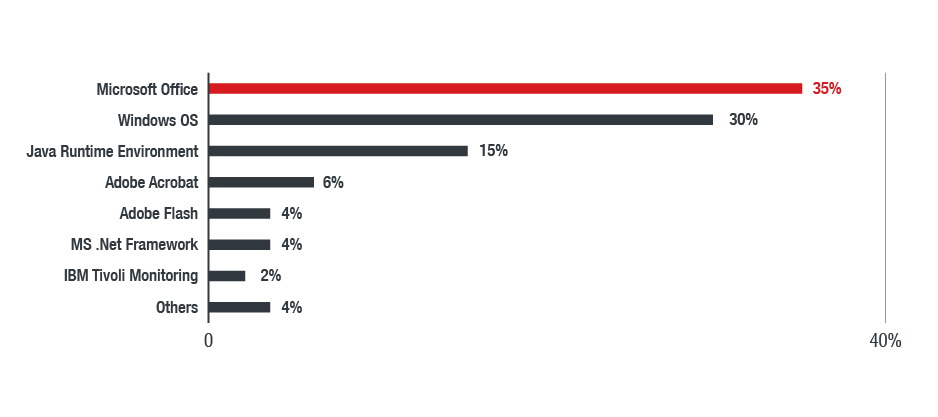
Figure 12. Applications whose vulnerabilities were most exploited in the North American region in 2018
Significant Threats in the Latin American Region
Ransomware still reigned in the Latin American region, although cryptocurrency-mining malware gained further traction. WannaCry/WCry, in particular, is the top threat in the region. WannaCry’s destructive capabilities (self-propagation and stealthy use of attack vector) are compounded by cybersecurity issues in the region, which could make it easier for attackers to breach an organization’s online perimeter or steal a user’s personally identifiable information. This is particularly true in Brazil, whose populace heavily relies on online and mobile banking.
WannaCry, the most detected ransomware in the region, affected organizations in government, energy, healthcare, telecommunication, manufacturing, technology, and financial sectors the most. Other notable threats include worm information stealers like Bondat, which significantly affected the education, healthcare, transportation, and banking industries. They spread via removable drives and have self-replicating and command-executing capabilities. Cryptocurrency-mining malware, especially malicious versions of Coinhive, largely affected manufacturing and retail companies. Consistent with our findings in previous quarters, downloaders like Downad (aka Conficker) and trojans like Gamarue (aka Androm, Andromeda, or Bundpil) were still prevalent despite being old threats.
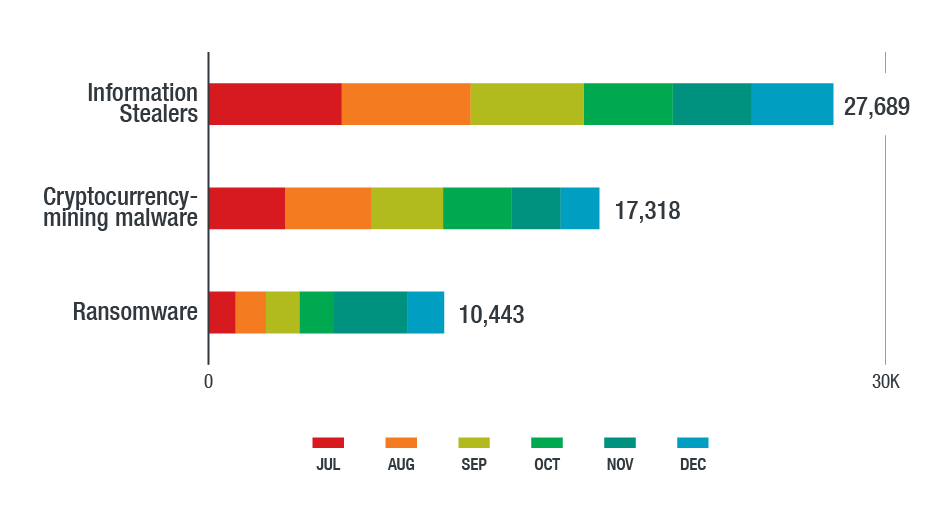
Figure 13. Detections of information stealers, cryptocurrency-mining malware, and ransomware in the Latin American region in the second half of 2018 (based on data from Trend Micro Smart Protection Network)
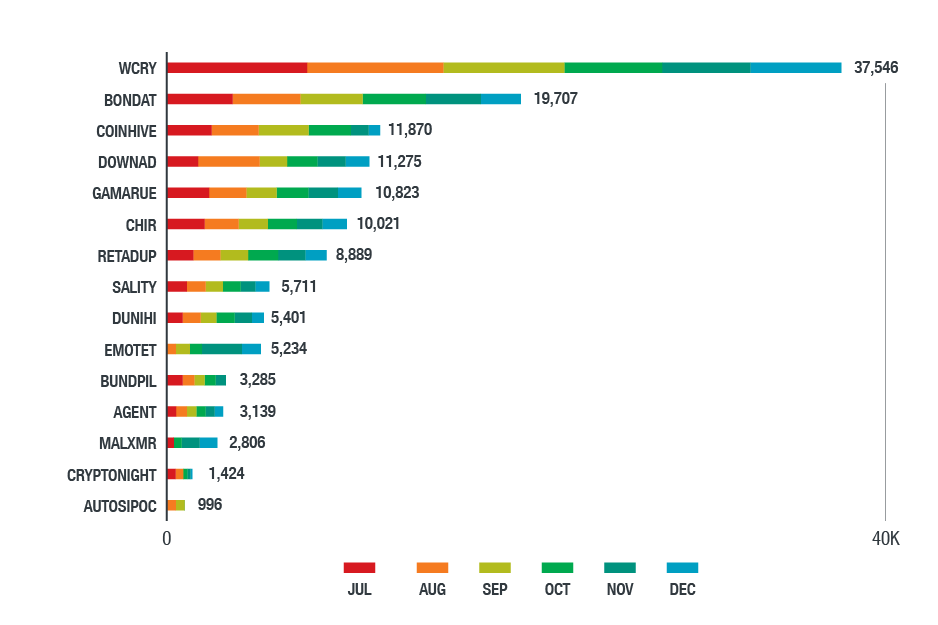
Figure 14. Top threats in the Latin American region in the second half of 2018
(based on data from Trend Micro Smart Protection Network)

Figure 15. Distribution of detections among the top ransomware families detected in the Latin American region in the second half of 2018 (based on feedback from Trend Micro’s MDR service)
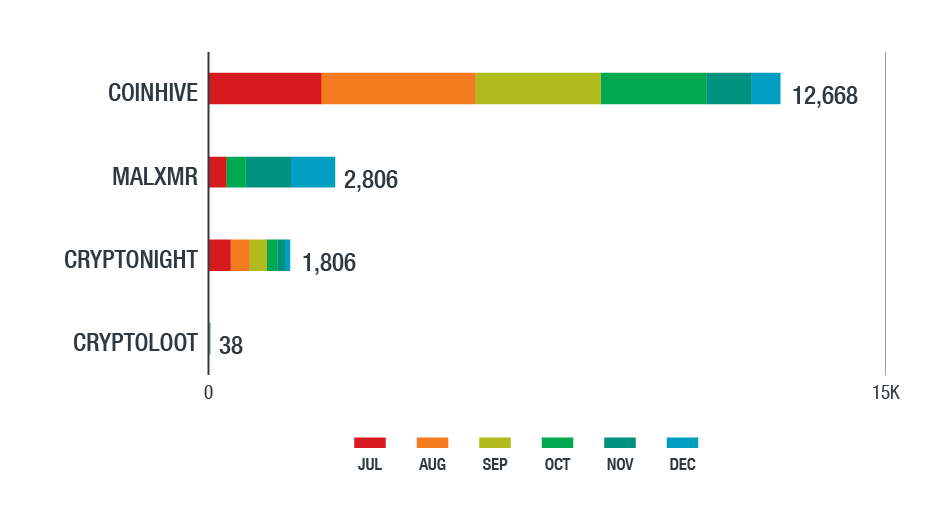
Figure 16. Top cryptocurrency-mining malware families detected in the Latin American region in the second half of 2018 (based on data from Trend Micro Smart Protection Network)
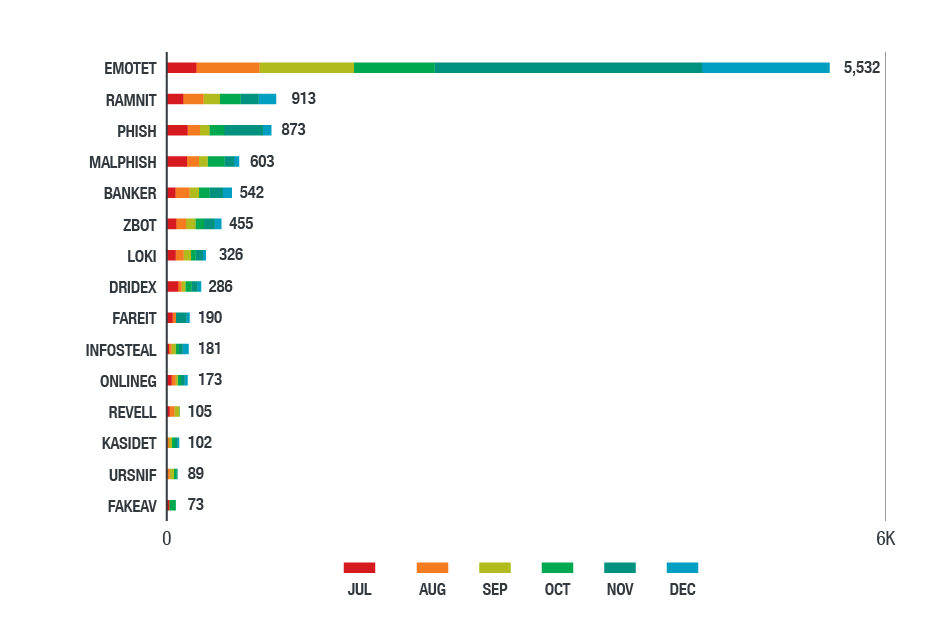
Figure 17. Top information stealers detected in the Latin American region in the second half of 2018
(based on data from Trend Micro Smart Protection Network)
How Managed Detection and Response Helps
The North and Latin American regions differed in specific forms of malware that affected them the most, but their threat landscapes weren’t far off in terms of the prevalence of malware families (e.g., WannaCry, Emotet, Coinhive) and their adverse impact. The threats’ increased complexity is also notable. In the Latin American region, for instance, we saw attackers constantly honing the tactics and techniques they used against their targets. These included configuring backdoors to make them more difficult to detect, abusing legitimate tools to deliver payloads, and using disk-wiping malware as a diversion to access their targeted system or network.
While many of today’s threats are from years past, their staying power in both regions is a reflection of how they’ve evolved to bypass traditional security defenses. This highlights the need to equip organizations with actionable insights that can help them promptly identify, respond to, and remediate threats. However, many organizations may not have the financial resources to accommodate this. Moreover, investment in security tools doesn’t necessarily translate to effective cybersecurity either. Today’s cybersecurity skills gap can make it more challenging to find the expertise needed to run or manage these tools. Bandwidth is also needed to process and sift through voluminous security incidents and alerts could also overwhelm and lessen the efficiency of the security team, which also doubles as IT staff in many organizations.
Managed detection and response helps by providing the right combination of people, process, and technology. Trend Micro’s managed detection and response (MDR) service provides alert monitoring, alert prioritization, investigation, and threat hunting services. By applying machine learning models to customer endpoint data, network data, and server information, the service will be able to correlate and prioritize advanced threats. Threat researchers investigate prioritized alerts to determine the extent and spread of the attack. They work with customers to provide detailed remediation plans. This service allows customers to investigate security alerts without the need to hire qualified incident response staff.
Trend Micro Solutions
Backed by 30 years of threat research experience, Trend Micro’s MDR service provides access to experts who are proficient with live response and are familiar with products that can provide meaning to security incidents that happen to organizations and their industries. Trend Micro’s MDR service is backed by specialists who protect an organization’s IT environments through a comprehensive security technology stack. Our experts have the necessary tools and technologies to analyze threats and help organizations maintain a good security posture.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks