Spam Campaign Targets European Users With Microsoft Office Vulnerability (CVE-2017-11882)
An active Microsoft Office and WordPad spam campaign is targeting European users, using languages such as Romanian and files that allow attackers to exploit the CVE-2017-11882 vulnerability. According to a series of tweets published by Microsoft Security Intelligence on June 7, this campaign could infect endpoints just by the opening of a malicious rich text format (RTF) attachment. Microsoft cautions users against opening these spam emails and strongly recommends applying security updates as soon as possible. 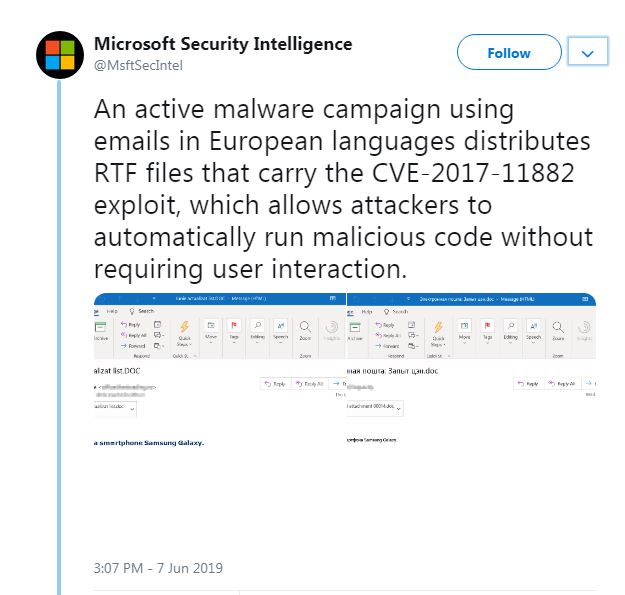
Figure 1. A screen capture of Microsoft’s spam campaign warning on Twitter
CVE-2017-11882 is a remote code execution vulnerability that allows specially crafted RTF and Word documents to be generated. Once these malicious documents are opened, they will immediately execute commands within the system. Though this vulnerability has been patched since 2017, Microsoft detected that it’s still being actively used in attacks. It also reported an increased use of this exploit in the past weeks with this new spam campaign.
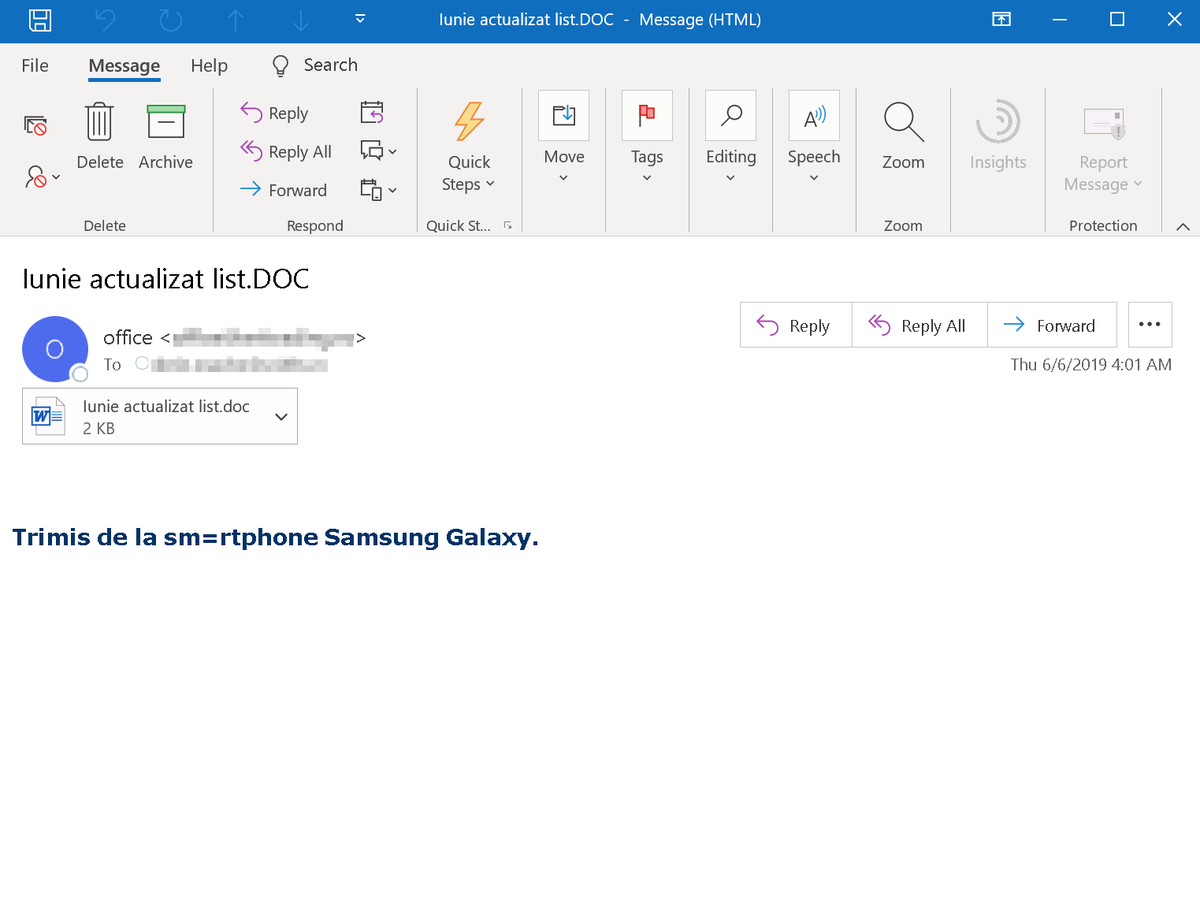 Figure 2. An example of a malicious spam email attachment (image from Microsoft Security Intelligence official tweet)
Figure 2. An example of a malicious spam email attachment (image from Microsoft Security Intelligence official tweet)
In the current spam campaign, Microsoft Security Intelligence said that, in order to download the backdoor payload, the malicious RTF attached in the spam email runs multiple scripts of various types, such as VBScript, PowerShell, and PHP, among others. As of writing time, the malicious domain the backdoor tries to connect to is not accessible; hence, an infected endpoint will not be able to connect to the malware’s C&C server. The payload could, however, be replaced by the attackers with a working one.
In a test that Bleeping Computer ran on one of the sample documents, it observed that after opening the malicious document, the document immediately executed a script taken from Pastebin. The script then executed a PowerShell command, downloaded a base64 encoded file, and saved it in the system as an executable file (%temp%\bakdraw.exe).
For persistence, Bleeping Computer reported that the executable is downloaded to %UserProfile%\AppData\Roaming\SystemIDE, and SystemIDE, a scheduled task, will be configured.
Trend Micro security solutions powered by machine learning
Trend Micro security solutions powered by machine learning help protect against various email threats.
For protection against spam and threats, enterprises can take advantage of Trend Micro endpoint solutions such as Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security. Both solutions protect users and businesses from threats by detecting malicious files and spammed messages, and block all related malicious URLs. Trend Micro Deep Discovery™ solution has a layer for email inspection that can protect enterprises by detecting malicious attachments and URLs.
Trend Micro Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. It protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions. Trend Micro Email Reputation Services detects the spam mail used by this threat upon arrival.
Trend Micro Deep Security™,Vulnerability Protection, and TippingPoint™ solutions provide virtual patching that protects endpoints from threats that abuse unpatched vulnerabilities.
Indicators of Compromise
|
SHA256 |
Detection Name |
|
ffb19eb696cc1c11b426d2c2b3ec801ba39b74d6b1772cd6fff09fecd596dd75 |
Trojan.W97M.CVE201711882.THFOFAI |
|
0bddc023f2c6c6befa1d12b1b3eaa86caa6119fd7d234d01f95bc72cc56a5eb9 |
Trojan.W97M.CVE201711882.THFOFAI |
|
816917f687595167f03365df571b225c36d47ec7566b10e1101575c1b30905b3 |
Trojan.Win32.TASKER.N |
|
712a857b17778c6439f374ef8c02f03536f20131cbb49d7483c14b854156eada |
Trojan.Win32.TASKER.N |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks