Ransomware Recap: Ransomware as a Service Surge, SLocker Resurfaces
 Ransomware as a service (RaaS) is designed to lower cybercrime’s barriers to entry. In a typical RaaS operation, developers write the malware, build the infrastructure needed to mount campaigns, then make it accessible for others—with underground marketplaces serving as their breeding ground. The apparent convenience and incentive of launching their own campaign, regardless of their technical knowhow, make it popular among venturing cybercriminals and script kiddies.
Ransomware as a service (RaaS) is designed to lower cybercrime’s barriers to entry. In a typical RaaS operation, developers write the malware, build the infrastructure needed to mount campaigns, then make it accessible for others—with underground marketplaces serving as their breeding ground. The apparent convenience and incentive of launching their own campaign, regardless of their technical knowhow, make it popular among venturing cybercriminals and script kiddies.
Case in point? Several ransomware families offered for sale (or rent) emerged this week touting affiliates and distributors with features beyond the ransomware’s file-encrypting capability.
Other notable ransomware families we’ve seen is the return of what can be considered the precursor of mobile ransomware, SLocker (detected by Trend Micro as ANDROIDOS_SLOCKER or ANDROIDOS_SMSLOCKER), and another with a familiar attack vector: compromised remote desktops.
Here are the highlights of this week’s ransomware recap:
FrozrLock offers affiliates “unlimited rebuilds”
Also known as AutoDecrypt, FrozrLock (RANSOM_WANTMYFILES.A) is sold in the underground for US $220 and billed as a “great security tool” that can encrypt files in minutes. Its RaaS operation lurks in Tor’s hidden service (.onion). In its homepage, FrozrLock is a C#-coded ransomware that supports .NET framework (4.5 and later versions) and employs Twofish256, AES256, and RSA4096 encryption algorithms to scramble the victim’s files. FrozrLock’s service, which fellow cybercriminals can avail by registering to its website, is packaged with a Tor-based control panel that allows distributors to create as many ransomware builds as they want. The dashboard can also purportedly monitor the infected victims. The changelogs in FrozrLock’s website indicate its developers are actively updating their service.
Trend Micro’s ongoing analysis of FrozrLock samples indicate it uses ConfuserEx, an open-source, Github-hosted utility, to obfuscate the malware. FrozrLock goes beyond deleting shadow copies (the computer’s backup of files). It abuses Cipher.exe, a command-line tool in Windows systems, to wipe the infected computer’s free disk space to ensure that the deleted shadow copies cannot be restored.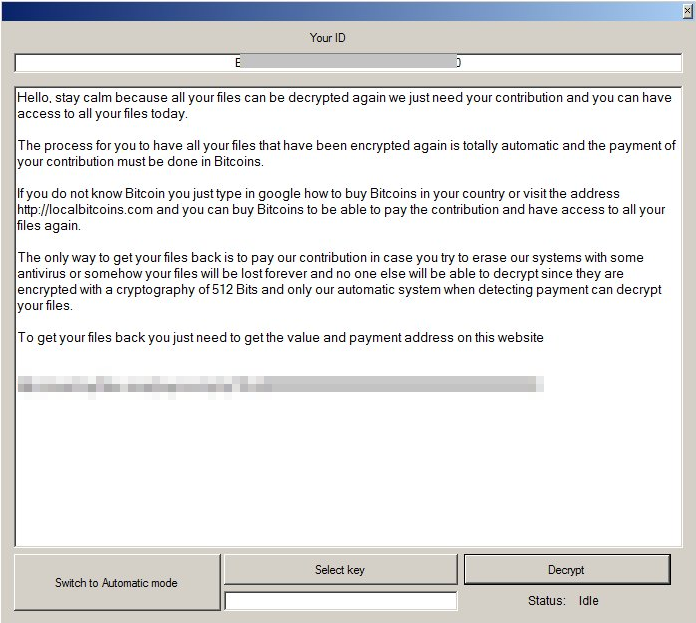
Figure 1: One of FrozrLock’s ransom notes
[READ: What does ransomware as a service (RaaS) mean for enterprises?]
Nemes1s RaaS has a support ticket for distributors
Nemes1s is in itself a copy of another RaaS, PadCrypt (RANSOM_CRYDAP), which made headlines back in February 2017 for offering a live help chat to victims.
What’s notable in Nemes1s is the series of refreshes it made to the service. These include an updated dashboard for distributors who can now see statistics such as the operating system (OS) of the infected machine, number of infections, and pending or received payments. It even has a support ticket system where distributors can ask Nemes1s’s Russian and German support members for assistance.
Given how Nemes1s’ site doesn’t have a registration section—a staple in many RaaS families—it appears that the distribution of Nemes1s’s service is restricted to a select few. It may also mean that Nemes1s’s developer is keeping a low profile to avoid drawing attention from law enforcement and security vendors, or until his service matures enough to serve more distributors.
[From the Security Intelligence Blog: Evolution of notorious ransomware as a service, Cerber]
Fatboy RaaS touts a more honest cybercriminal partnership
Fatboy (RANSOM_PHYTOCRYP.A) RaaS debuted in a Russian underground forum through a user who goes by the handle “polnowz”. Fatboy’s payment arrangement is quite unique: it uses the Big Mac Index, a benchmark for measuring purchasing power of currencies, to gauge the amount of ransom it will demand its victims. Those located in more affluent countries are extorted with a bigger sum.
Another striking feature is the lengths Fatboy’s developer goes to earn the would-be affiliate’s trust. The developer and potential distributors (or “partners”) can communicate with each other directly using the Jabber Off-the-Record (OTR) messaging service. Any payment made by the victim is received instantly by the distributor.
Fatboy is advertised to be capable of working on 32- and 64-bit Windows systems and scrambles files with AES-256 encryption keys, each of which are then encrypted with RSA-2048 algorithm. Fatboy can purportedly scan all disks and network folders, and target a massive 5,000 file types. The malware is a 15.6 kB-binary written in C++ language.
The ransomware will not work if it infects systems located in the Commonwealth of Independent States. Fatboy demands a ransom of 1 Bitcoin (roughly equivalent to US $1,860 as of May 11, 2017) and threatens victims with a certain time limit (which distributors can customize) before the files are deleted.
[From the Security Intelligence Blog: How to protect against mobile ransomware]
Mobile ransomware SLocker resurges
SLocker was one of the first ransomware to emerge in the mobile landscape, and after a lull in activity it staged a comeback with reportedly over 400 unique samples in tow. They masquerade as jailbreaking applications as well as legitimate, recreational and business apps, using obfuscation techniques to evade detection.
Based on Trend Micro’s analysis, SLocker was notable for abusing the user interface (UI) Application Programming Interface in Android to lock the device’s screen. SLocker is also known to impersonate law enforcement agencies accusing victims of crimes to capitalize its fear-mongering tactic against unwitting victims.
Several iterations of SLocker like SMSLocker also operated as banking Trojans, locking the mobile device while also pilfering its online banking credentials.
[READ: Which ransomware dominated the mobile threat landscape in 2016?]
RSAUtil ransomware targets compromised remote desktops
Another ransomware that made rounds is RSAUtil (RANSOM_DONTSLIP.A) that targets hacked remote desktop services. RSAUtil’s attack chain is multipart: a package comprising various tools and RSAUtil itself are uploaded to the compromised machine. The package—which contains configuration files, executables and dynamic -link libraries (DLL)—is then executed in order to install the ransomware.
The files in the package are the ones responsible for:
- RSAUtil’s encryption routine and the public encryption key to use in the infected file
- Erasure of event logs in the machine to remove traces of how it was compromised
- Indicating what ID number and email to use in the ransom note
- Selecting which extension name to put in the encrypted files
- Preventing the machine from being idle, sleeping or hibernating to ensure RSAUtil doesn’t get disrupted
[Infographic: A multilayered defense against ransomware]
Indeed, ransomware continues to diversify in order to hit more targets. This is particularly true for RaaS. Outsourcing cybercrime and turning it into a turnkey service puts threats such as ransomware in the hands of a wider swathe of bad guys. The result? An ever-rising number of different builds of similar ransomware in the wild with varying degrees of capabilities. Cybercriminals, too, will set their sights into other viable targets like mobile platforms as they become more prevalent among users and businesses.
While there is no silver bullet against ransomware, a proactive approach to security helps mitigate it. Some of the best practices for defending against ransomware include:
- Regularly backing up important files
- Keeping the system updated with the latest patches
- Employing virtual patching to avert attacks that use unknown vulnerabilities
- Identifying and defending common entry points used by ransomware such as email and suspicious websites
- Integrating additional layers of security to remote connections
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks