Online Dating Websites Lure Japanese Customers to Scams
By Alex Y. Chen
 Scams have become more rampant in recent years by utilizing various social engineering techniques. Whether through social media, emails, or mobile apps, cybercriminals have been able to lure victims into clicking on fraudulent links so that they can steal vast amounts of money from unwitting individuals. In fact, schemes that involve romantic themes and routines through online dating are among the most widespread.
Scams have become more rampant in recent years by utilizing various social engineering techniques. Whether through social media, emails, or mobile apps, cybercriminals have been able to lure victims into clicking on fraudulent links so that they can steal vast amounts of money from unwitting individuals. In fact, schemes that involve romantic themes and routines through online dating are among the most widespread.
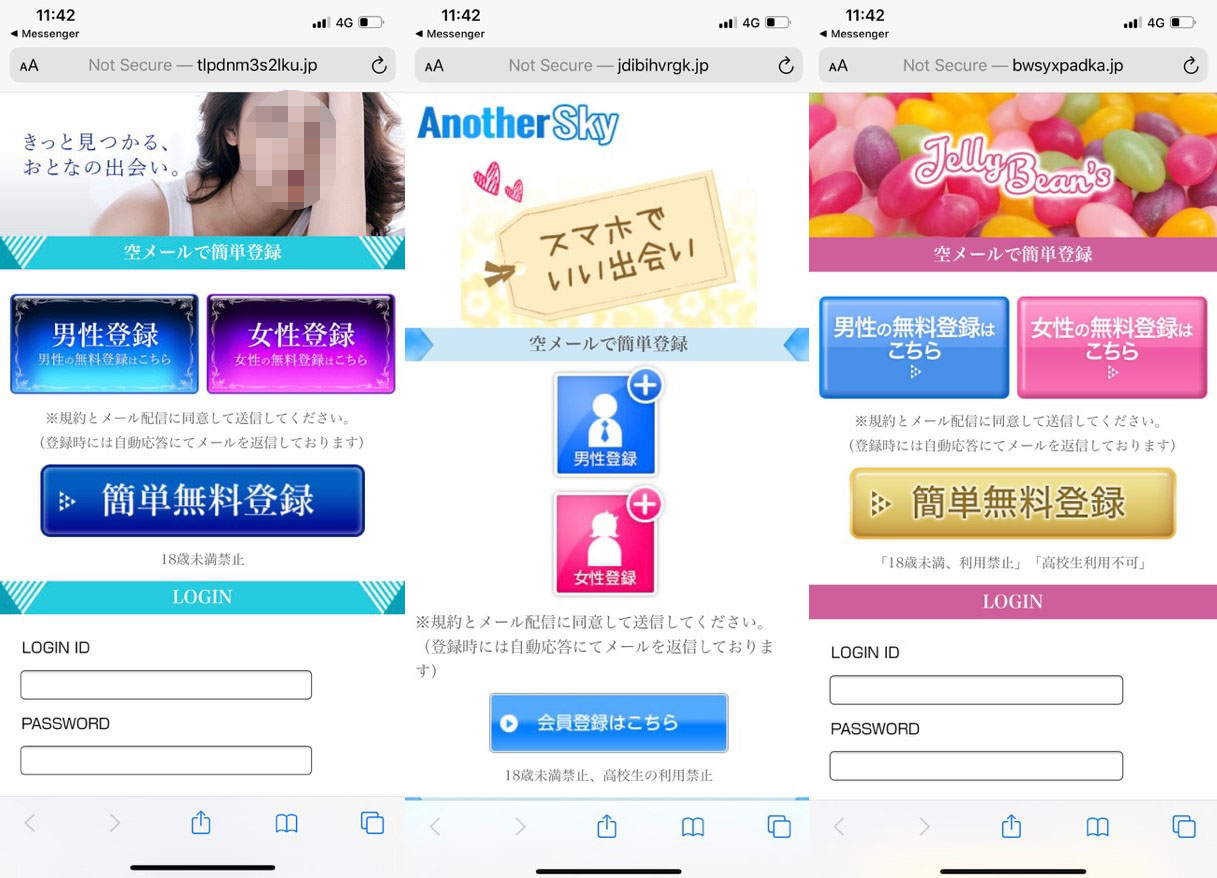
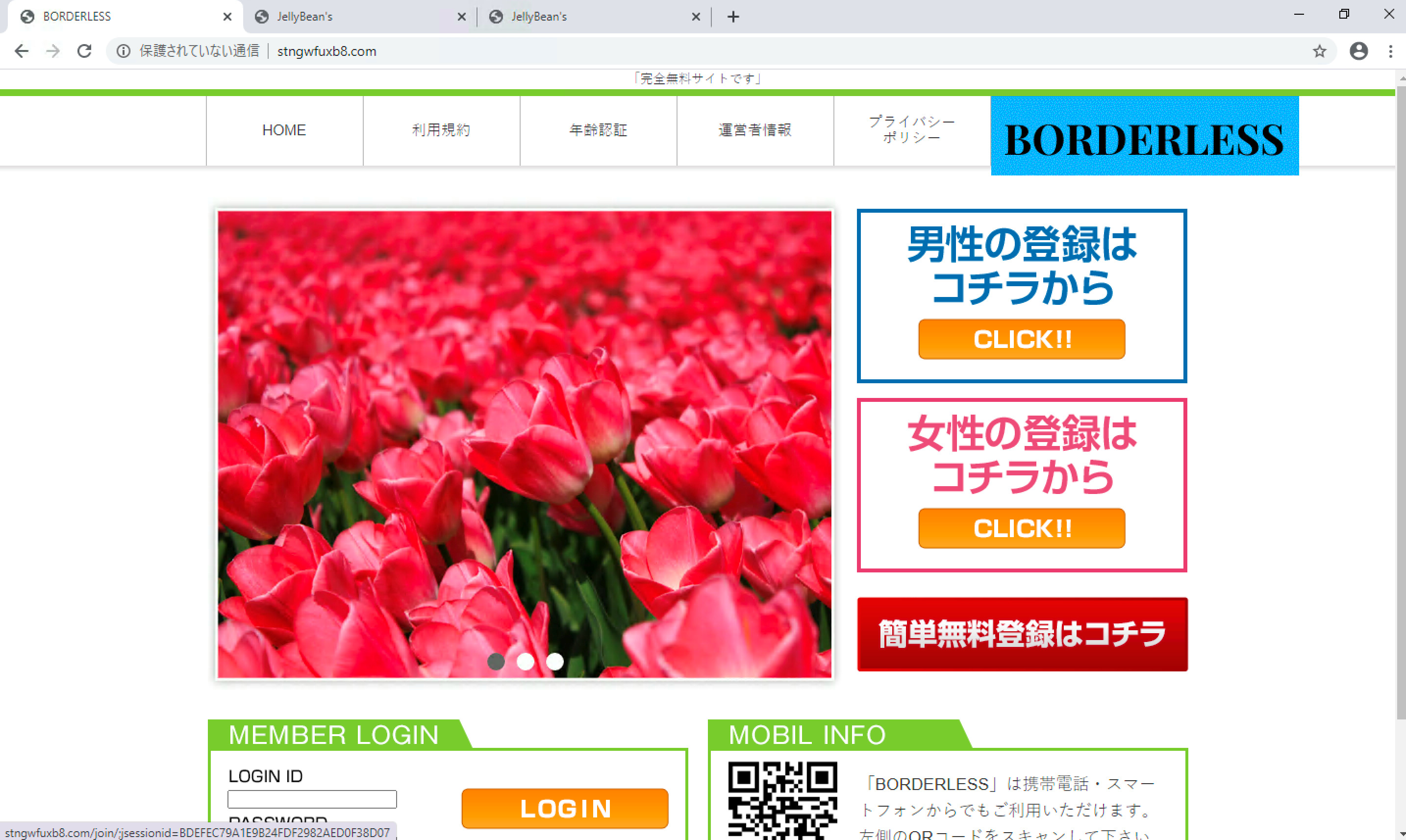
In fact, we found two different websites with exactly the same layout, brand, and offered dating services. This has also been reported on another article by Sakuradot.
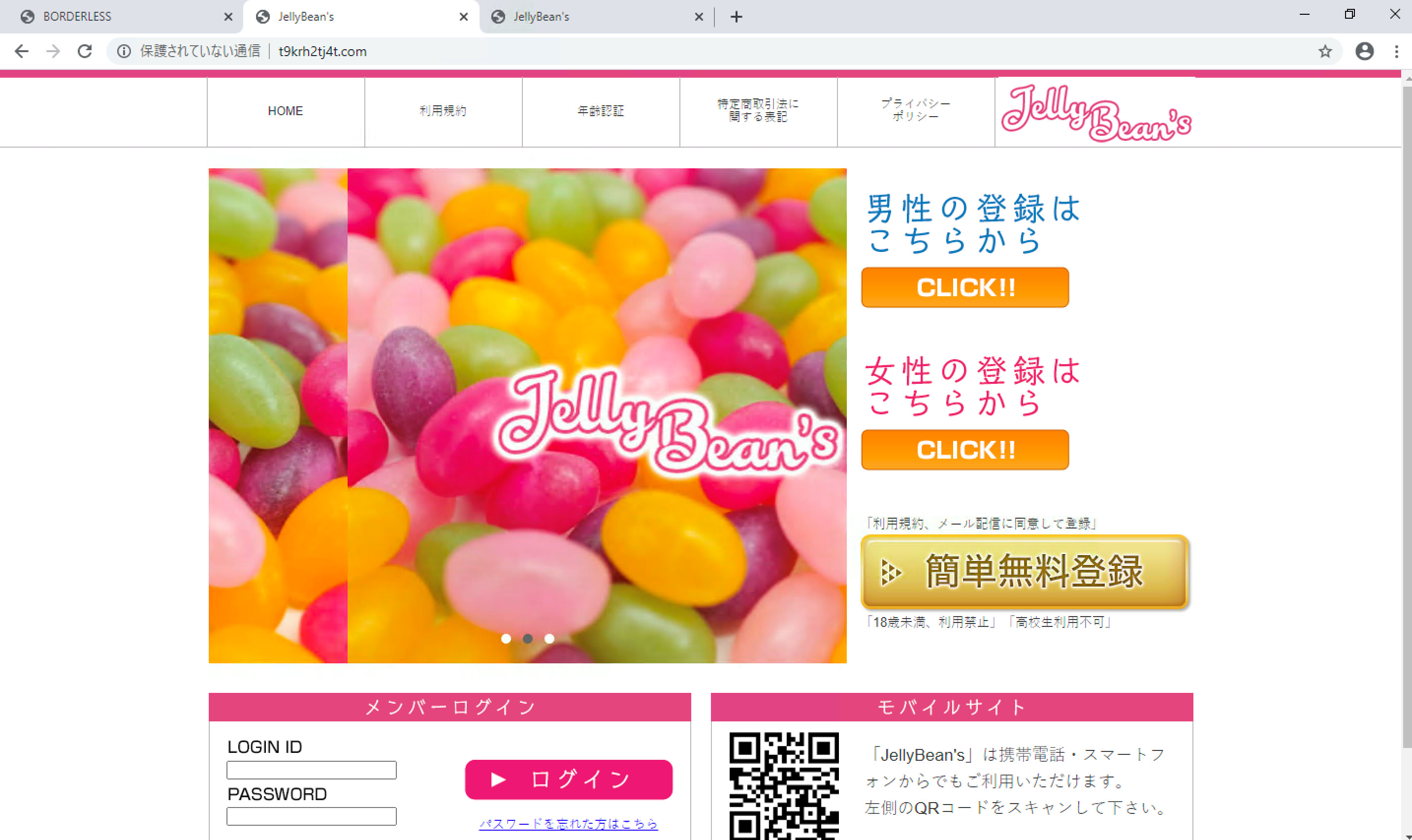
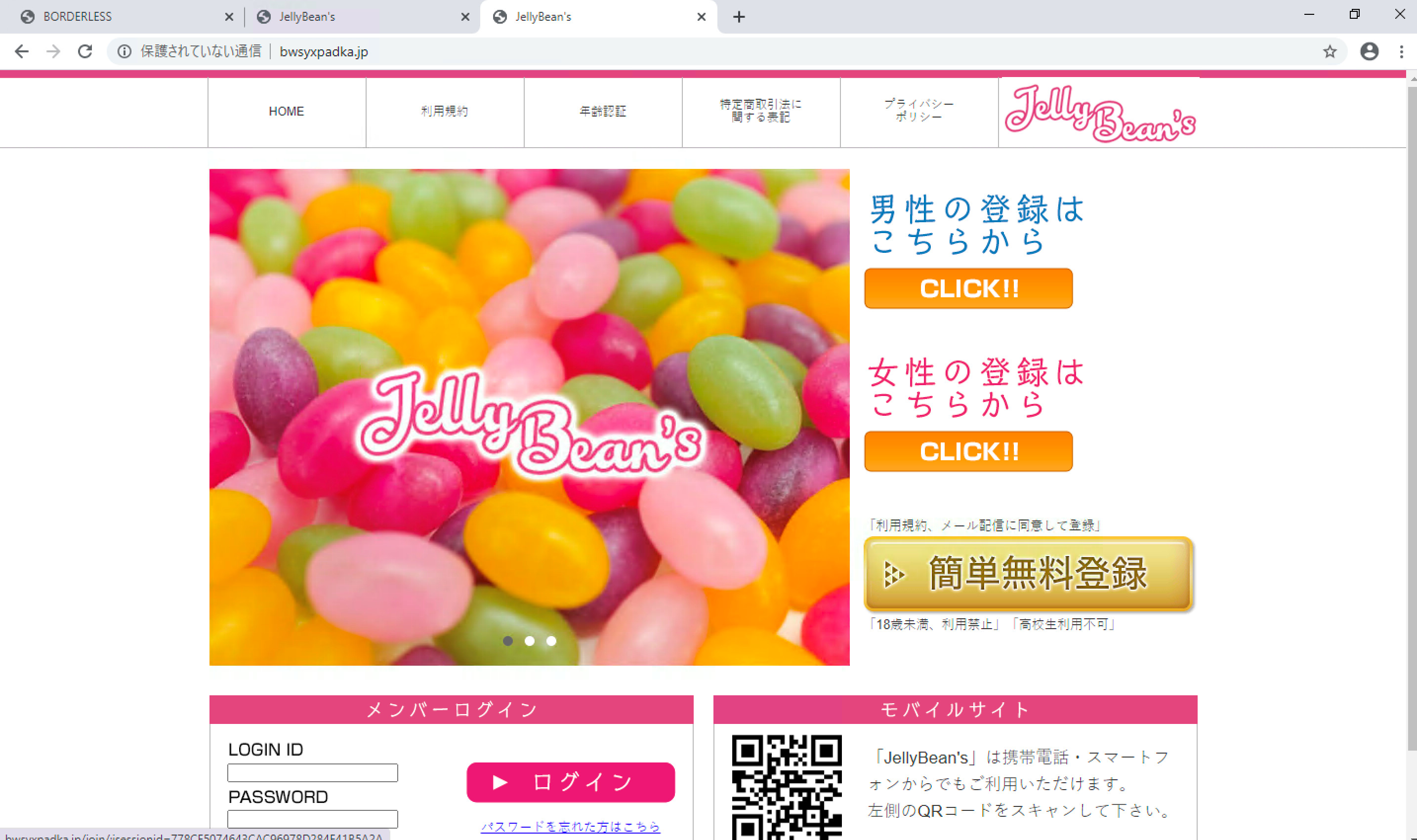
Figure 3. Different websites with exactly the same layout
Delivery
Primarily, potential victims of these dating scams are sent messages that inform them of the dating websites via text, messaging apps, and social media. These messages also include a link to the websites. After visiting the sites and reading about their company information, we found that none of the cited locations of these companies are in Japan. There is also no evidence that these addresses are real office locations. Additionally, after looking at what are likely fake profiles of registered female members, it becomes apparent that these dating websites are aimed at male subscribers who are looking for dates online.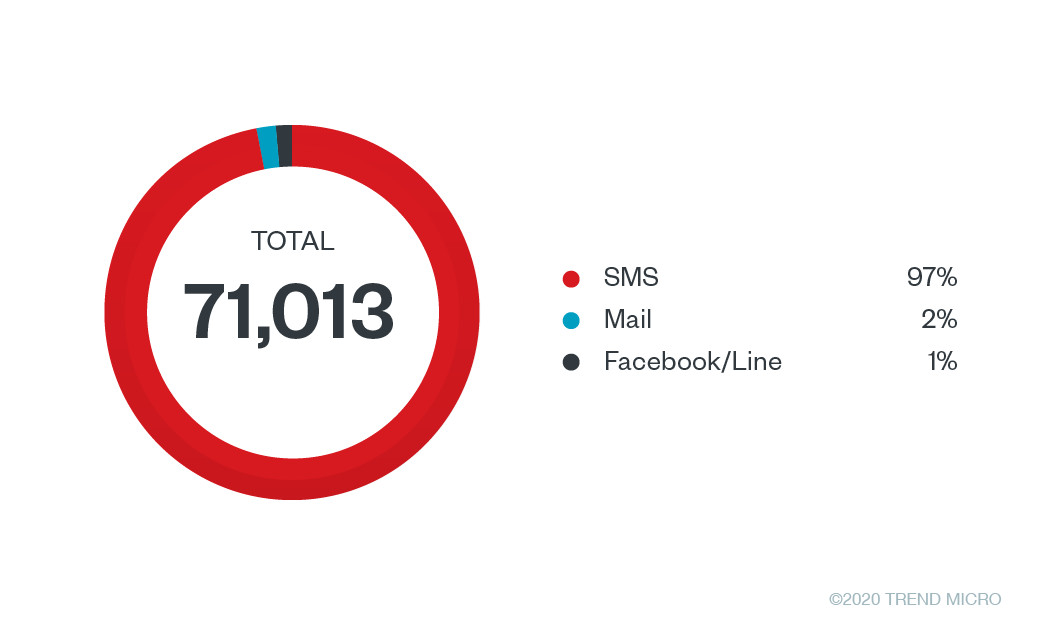
Figure 4. Percentage of malicious links’ delivery methods
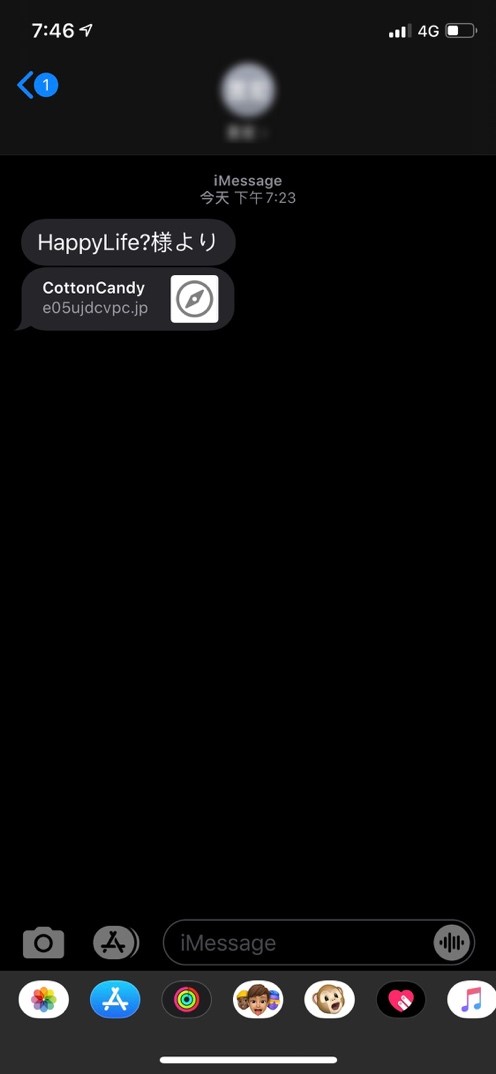
Figure 5. Victims getting a message with the malicious link
Moreover, after checking the locations of the company listings, we found it suspicious that their respective offices are located in other countries or islands outside of Japan, such as the Caribbean Islands, Hong Kong, and the Philippines. Grammatical errors in Japanese are also evident on these sites, making it likely that the writer is not a local.
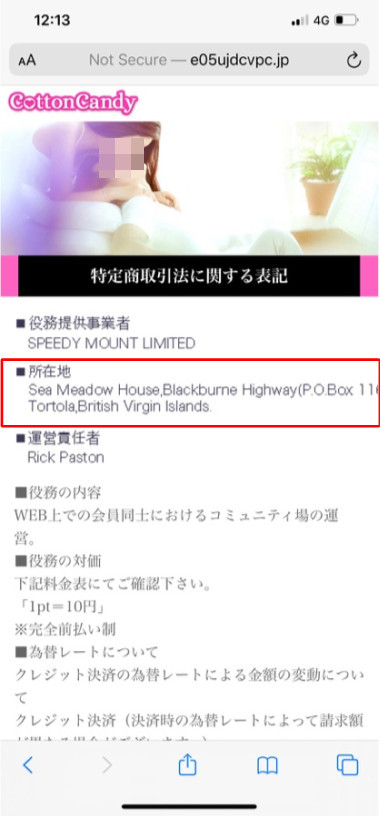
Figure 6. Registered address not in Japan
Appearing legitimate
In another routine, selecting an option labeled "特定商取引法に" (roughly translated from Japanese as “Commercial Transaction Law”) leads to a page describing the website and company as legitimate entities. This is seemingly in an effort to convince the user of the site’s authenticity and legality, but Japanese customers usually ignore this option on websites since it’s not a requirement to select it.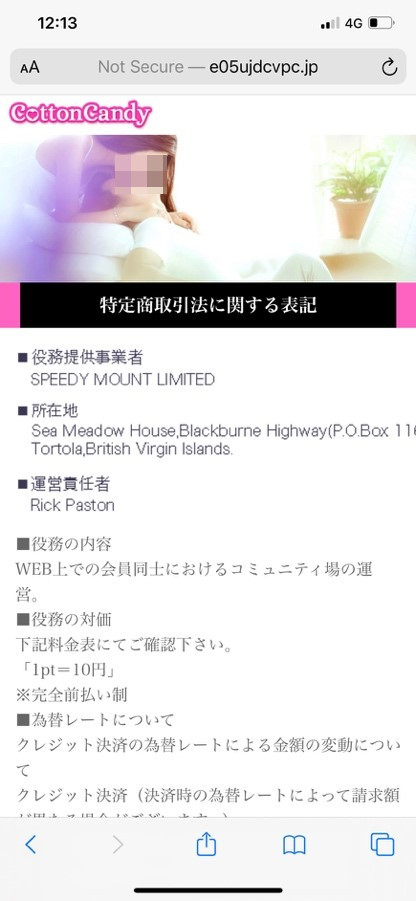
Figure 7. Buttons and details that make the website appear legal
It is also worth noting that when it comes to transactions, legitimate dating sites provide authentication numbers that the customers can use to secure their paid services. In Japan, all legal dating sites are required to register for authentication by the respective Japanese government agencies and are thus verifiable through these numbers. On the other hand, these fake dating websites have no such numbers.
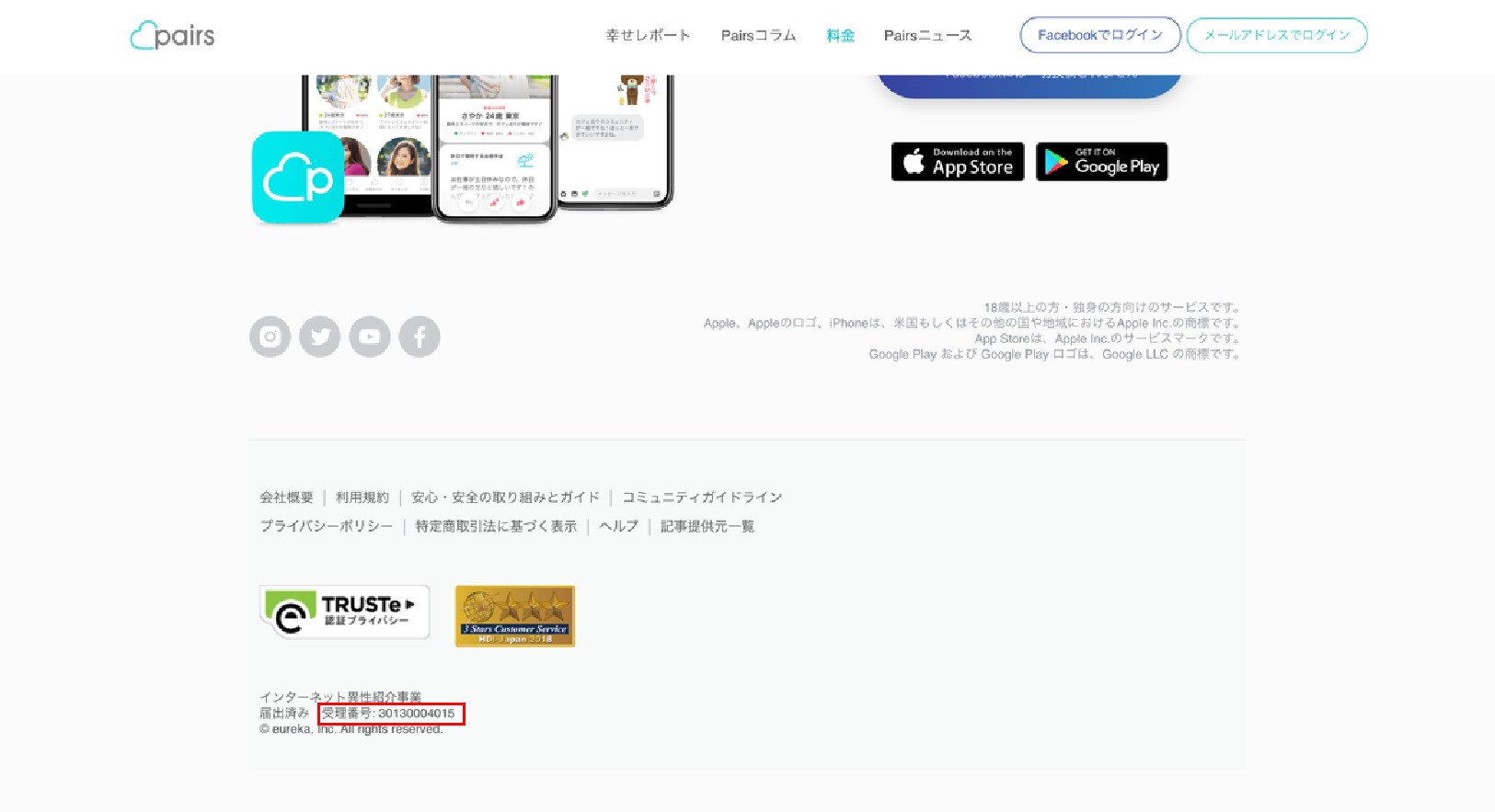 Figure 8. Legitimate Japanese dating websites have authentication numbers issued by the government
Figure 8. Legitimate Japanese dating websites have authentication numbers issued by the governmentStealing information, promising money
In one of the routines, the user is redirected to a dating page where they can follow instructions on how to register as an exclusive member and purchase points. The instructions carry a red flag, however, by claiming that a purchase of at least 1,000 points can yield “support money” for the subscriber that is in turn worth JP¥600,000,000 (est. equivalent of US$5.7 million).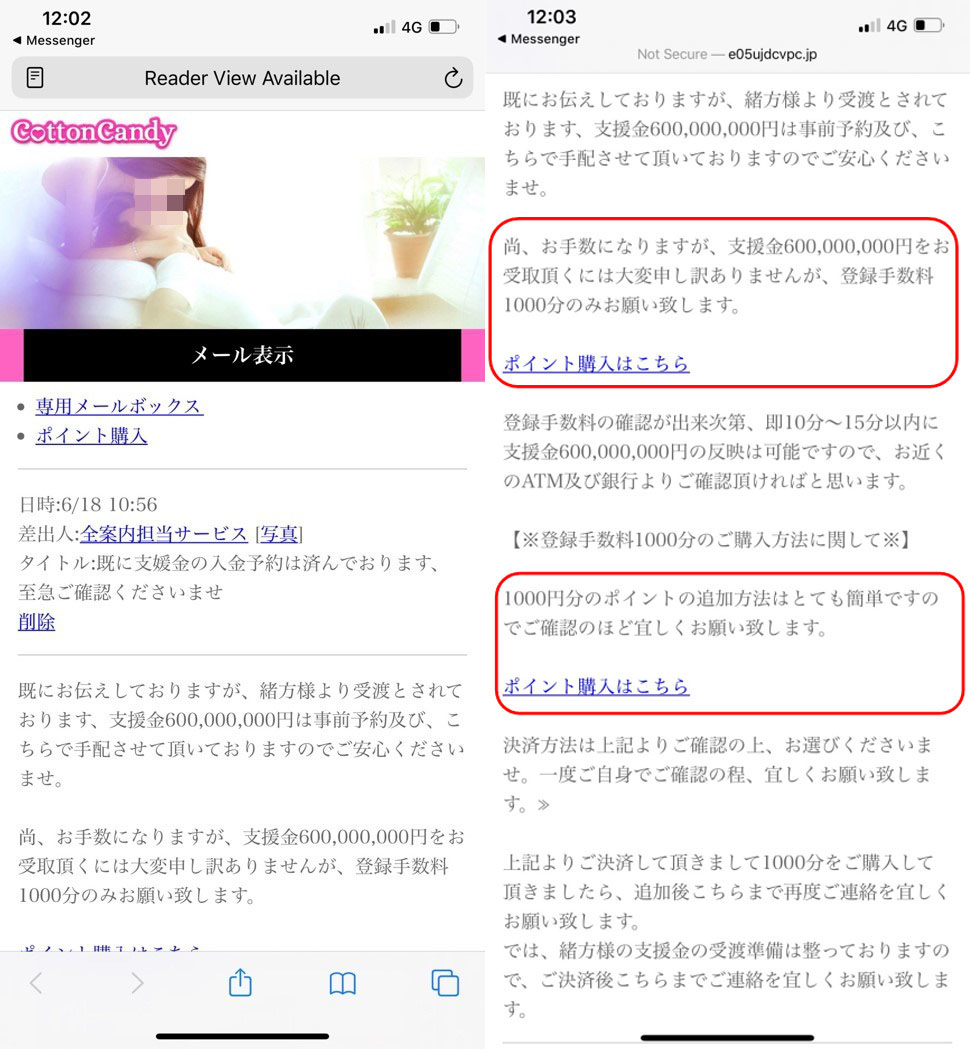 Figure 9. Instructions for membership, purchase of points, and “support money”
Figure 9. Instructions for membership, purchase of points, and “support money”
The points allow the subscriber to avail of the website’s matching services. JP¥10 (est. equivalent of US$0.095) is equivalent to 1 point in the website and supposedly provides service features such as sending a private message or email to another member (1,000 points). Meanwhile, other features require no point usage, such as sending a message via a public message board and looking into their profile data, among others.
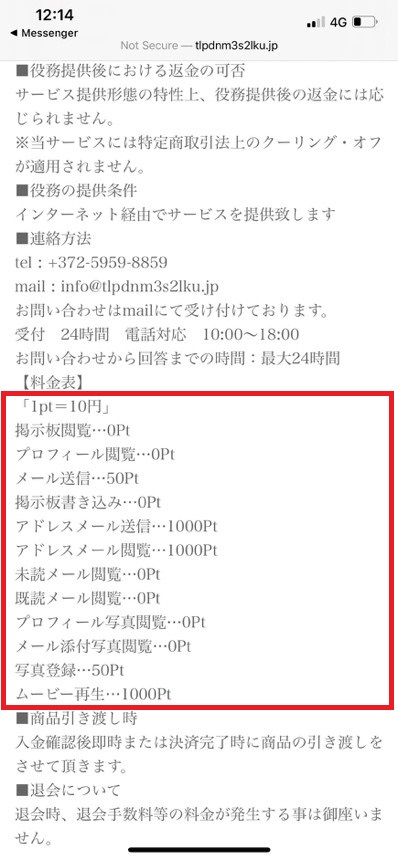
Figure 10. Website services equivalent to points
Only after the user has made one or several purchases will they realize that both the registration and points are worthless. A quick online search of the domain used for the registered email address would also raise suspicions, as the query returns no results for the addresses.
Figure 11. Fake domains and email addresses
By this stage, however, the user has already given their information and credit card data. From an HTML analysis, we found that the cybercriminals can use an image file to display some pieces of information, such as company address and owner. Unfortunately, this also allows hackers to easily replace the sensitive information listed such as IDs, emails, and financial credentials for use in other malicious activities.
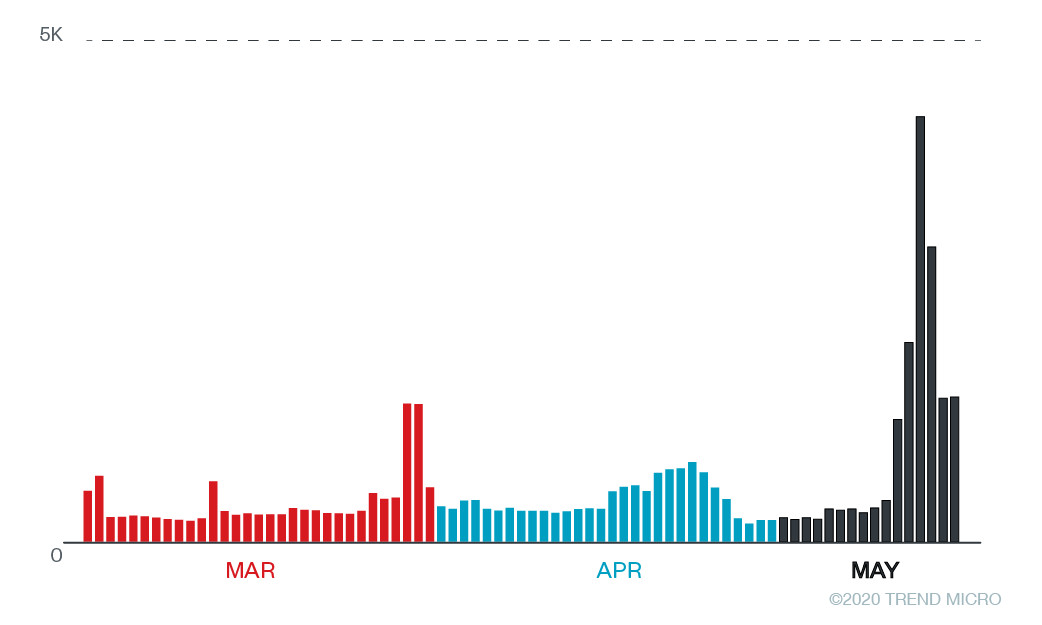
Looking at the rates of visits to these websites from March to June reveals that there has been a steady number of visits and transactions in these malicious websites.
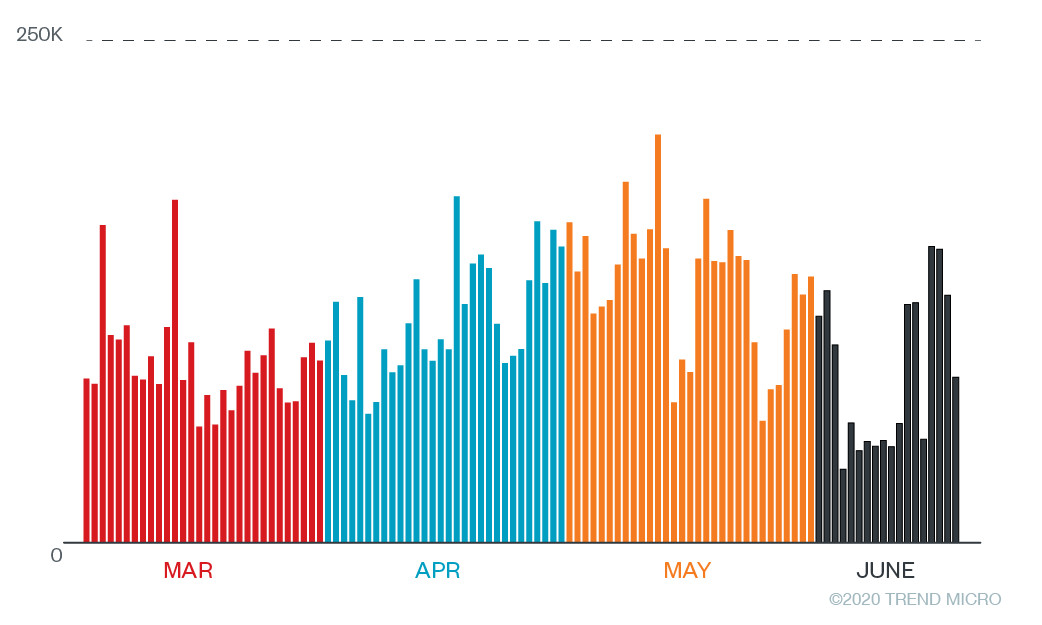
Figure 12. Number of visits to malicious online dating websites by URL per day
Best practices and security recommendations
Scams lure potential victims by proposing products and services that are trending or that respond to an individual’s wants or needs. Furthermore, cybercriminals are always on the lookout for opportunities to profit at the expense of other people. The financial and personal information of the victims can be subsequently used by the cybercriminals to conduct other unlawful activities. In particular, fake dating websites can serve as research and development grounds for more sinister attacks, or possibly lure victims of other nationalities who may have a basic understanding of the language.
Here are some best practices users can follow in order to avoid falling prey to such scams:
- Read through and examine the website’s language and requirements. Errors, unverified site credentials, and dubious promises of financial returns can be red flags or indicators of malicious intent and cybercriminal activities.
- Check the URLs of the websites that request access to personal and financial information.
- Install and enable multilayered protection systems capable of detecting, blocking, and mitigating malicious websites, apps, and emails.
Trend Micro solutions
Trend Micro endpoint solutions such as the Smart Protection Suites and Trend Micro™ Worry-Free™ Business Security detect and block the malware and the malicious domains they connect to. Trend Micro™ Email Security™ thwarts spam and other email attacks. The protection it provides is constantly updated, ensuring that the system is safeguarded from both old and new attacks involving spam, BEC, and ransomware. Trend Micro™ Web Security™ Advanced, powered by XGen™, provides you with forward-looking threat protection on web threats, URL filtering, and application control, plus enterprise-grade features.
Indicators of Compromise (IoCs)
hxxp://bgmdvusqbsx[.]jp
hxxp://bwsyxpadka.jp[.]com
hxxp://crsiystr399[.]jp
hxxp://cwiabwtrrt[.]jp
hxxp://e05ujdcvpc[.]jp
hxxp://fzfhrcnigx[.]jp
hxxp://hjrotpembre[.]jp
hxxp://irevkxcntfh[.]jp
hxxp://jco81viaxgd[.]jp
hxxp://jfngctgxai[.]jp
hxxp://jx7o3v6hayz[.]jp
hxxp://kgwhha-erwgh[.]com
hxxp://knikwuyehb[.]jp
hxxp://meowth-torracat[.]com
hxxp://metapod-indeedee[.]com
hxxp://oeuqxqhqwwb[.]jp
hxxp://olrgmjevheg[.]jp
hxxp://pbbdyw[.]com
hxxp://r98kh6pghst[.]jp
hxxp://rfigaqsbxvo[.]jp
hxxp://rhkeqphylm[.]jp
hxxp://rtbpca[.]com
hxxp://rtuguu[.]com
hxxp://sentret-quilladin[.]com
hxxp://silver-jewel77[.]com
hxxp://u6mto68r6xh[.]jp
hxxp://wayfnek[.]com
hxxp://xlskwfdbrec[.]jp
hxxp://zk1kio0h2i3[.]jp
hxxp://3sls5kxvp0re[.]jp
hxxp://6cw1olssx5[.]jp
hxxp://9twhququija[.]jp
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks