Loki Delivered as CAB File Attachment
Analysis and insights by Miguel Ang
 We found in our honeypot a spam sample that delivers the info stealer Loki through an attached Windows Cabinet (CAB) file. The email that bears the malicious file poses as a quotation request to trick the user into executing the binary file inside the CAB file.
We found in our honeypot a spam sample that delivers the info stealer Loki through an attached Windows Cabinet (CAB) file. The email that bears the malicious file poses as a quotation request to trick the user into executing the binary file inside the CAB file.
CAB is a compressed archive file format usually associated with various drivers, system files, and other Windows components installations.
The email has the header “REQUESTING QUOTATION,” seemingly coming from a client who is interested in availing the products and/or services offered by the receiver. The attachment supposedly contains the quotation request.
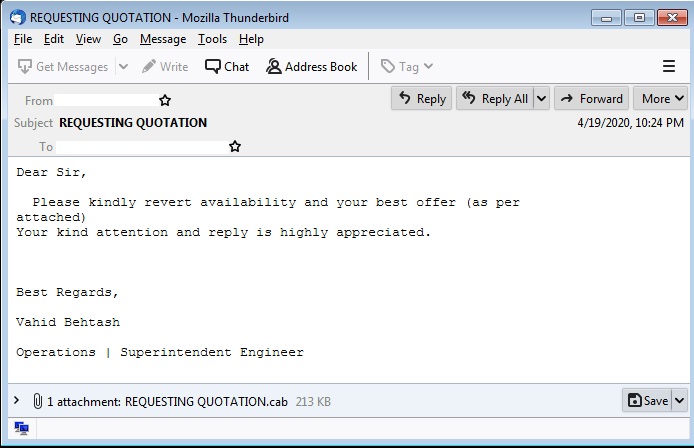
Figure 1. Sample email for Loki campaign
The CAB file attachment carries a binary file, which is a .NET compiled dropper that eventually executes Loki. The .NET dropper makes use of several layers of encrypted .NET modules that are then invoked.
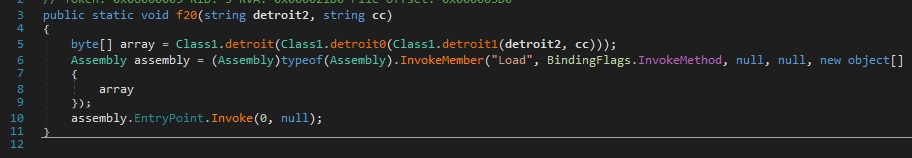
This will eventually lead to the execution of the Loki binary via process hollowing. Process hollowing is a malware technique that involves loading legitimate processes on the system and having it serve as a container for malicious code, thus remaining undetected. The technique was recently used by Monero Miner to evade detection.
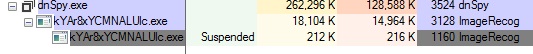
Figure 3. Loki binary executed via process hollowing
Protection against info stealers and other malicious attachments
- Never download attachments or click links on emails from unfamiliar senders. This may lead to the installation of malware.
- Be careful with sharing email addresses. Don’t share contact details on public web forums, social media, and other channels.
- Be informed of the latest spam campaigns. Knowing the topics and contents of malicious emails can help avoid even those that use the most convincing social engineering techniques.
-
Trend Micro™ Deep Discovery™ Email Inspector – Employs machine learning, detection engines, password extraction, and custom sandbox analysis to detect advanced malware.
-
Trend Micro™ Email Security – Offers email sender analysis and authentication, as well as protection against unknown malware, URL, and AI-based fraud.
-
Trend Micro™ Cloud App Security – Provides advanced threat and data protection for Microsoft Office 365, Google G Suite, and cloud file-sharing services
Indicators of Compromise
| File Name | SHA-256 | Trend Micro Pattern Detection |
Trend Micro Predictive Learning Detection |
| REQUESTING QUOTATION.cab | 35a5cb85a5fbea3fdbd568aacedca42c4488877c1c2ee4 79fe21c1534e070866 |
TrojanSpy.MSIL.LOKI.TYQH
|
n/a |
| KYAr8xYCMNALUlc.exe | 3f713f94f2c6c981a93cc9e01894da2da3a1448290936 19eb960f469e245fa17 |
n/a | Troj.Win32.TRX.XXPE50FFF034 |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks