Bridging Security Gaps in WFH and Hybrid Setups
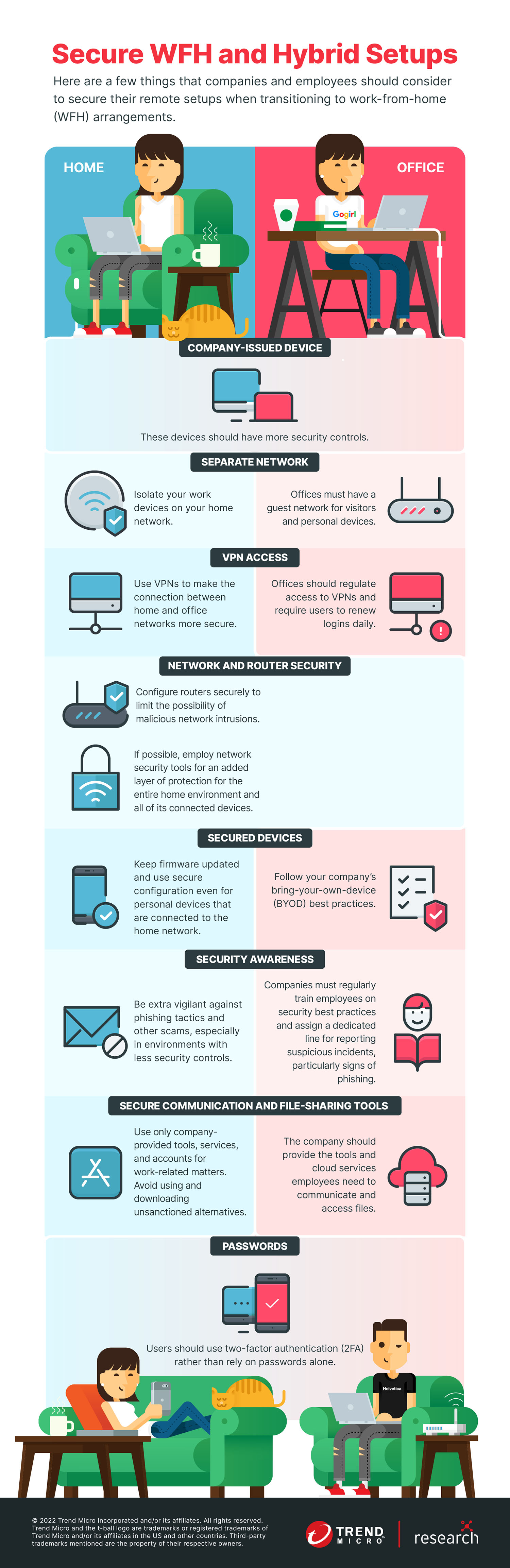
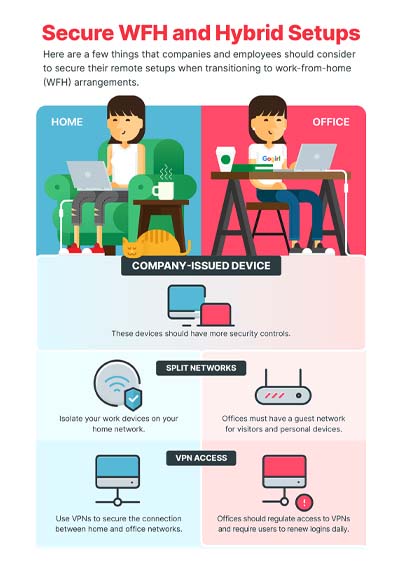 View Infographic: Secure WFH and Hybrid Setups
View Infographic: Secure WFH and Hybrid Setups
With the pandemic nearly under control, organizations all over the globe are either returning to the office, permanently switching to remote arrangements, or opting for a combination of both. Although each arrangement carries its own set of pros and cons, from a cybersecurity standpoint, the latter two present some challenges and highlight security gaps.
Hybrid and work-from-home (WFH) arrangements take employees from the safety of the more secure and monitored environment of the office. These arrangements blur the division between enterprise and home networks while subsequently expanding the attack surface for both environments. How can these security gaps be bridged?
Threats facing remote work arrangements
First, we must look at the data to see what threats thrived during that period of transition. In 2021, most organizations settled into remote setups. In our annual roundup for the same year, we noted that there was a 382% increase in blocked malicious files.
Phishing
Cybercriminals also appear to have doubled down on phishing schemes during that period. Based on our data from Trend Micro™ Cloud App Security, phishing saw a remarkable 596% increase. At a time when the workplace had already largely shifted from offices to homes, malicious actors continued to favor email as their low-effort yet high-impact attack vector to disseminate malware.
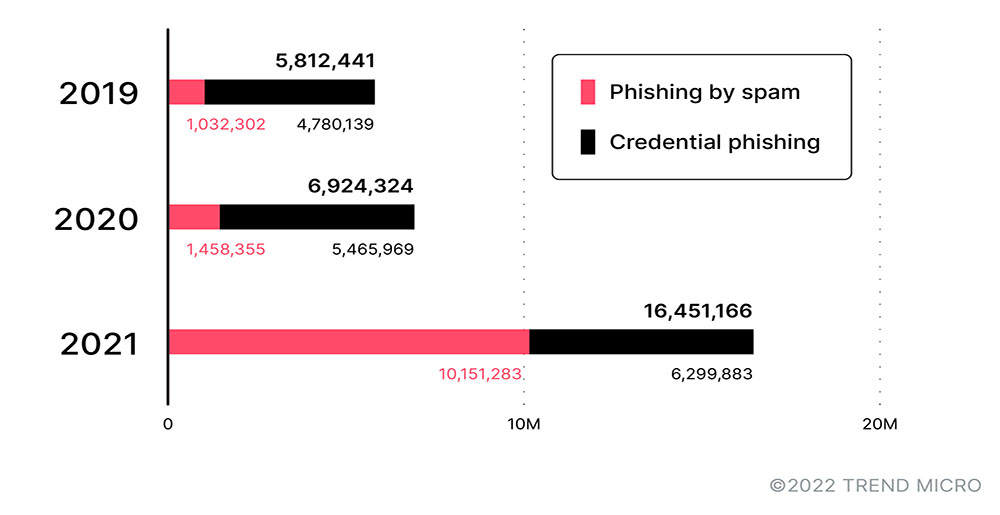
Figure 1. A comparison of the detections of spam-phishing and credential-phishing attempts from 2019 to 2021
Source: Trend Micro™ Cloud App Security
Home network threats
What about the home network? Data from our Smart Home Network solutions revealed an increase of potential malicious activity in home networks from 2019 to 2020. The number of blocked threats, as seen in Figure 2, indicates that home devices, particularly routers, were being targeted more frequently during this period. Still, this was expected as most employees who stayed at home relied on devices to stay connected and continue their activities.
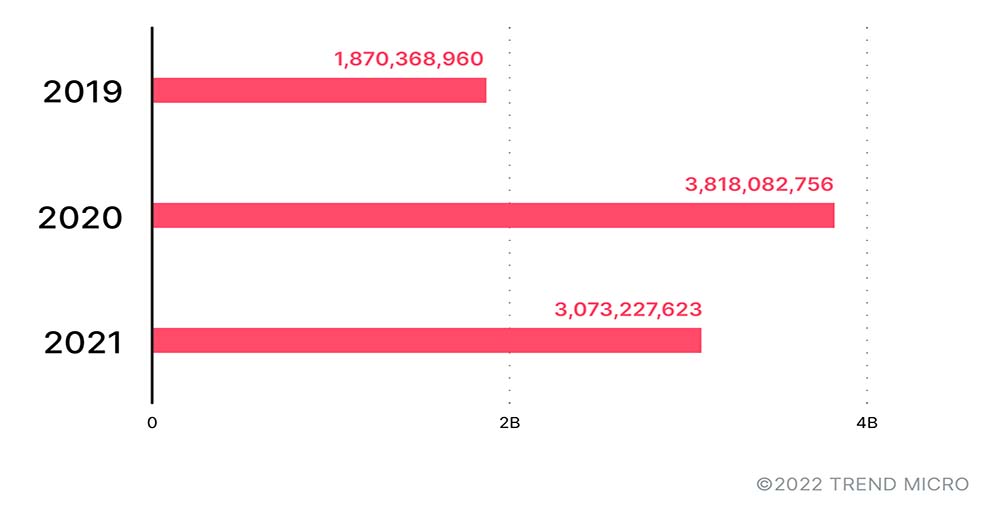
Figure 2. Smart Home Network detections showed an increase in activity from SHN-enabled devices and routers, in line with the increased reliance on online home networks during the pandemic.
File transfer risks and unsecure tools
For WFH and hybrid setups to work, employees would need access to company files from their remote locations. However, moving files can increase the probability of a data breach or the introduction of malicious files to a company network. According to a survey conducted by OpenText, 56% of US employees use personal file-sharing tools for work-related material. 76% of respondents from the same survey admitted to feeling stressed over the flood of information on a WFH setup, while 26% claimed they used 11 or more accounts, resources, tools, and apps every day — an overwhelming estimate, to say the least.
Organizations should provide their employees safe ways to transfer large file sizes and access file hosting services. They should also educate employees on what types of files are safe to share and the correct permission to assign their shared files.
VPN vulnerabilities
Virtual private networks (VPNs) allowed users to connect to secure networks while working from home. Unfortunately, unsecured vulnerabilities in VPNs have also been exploited in attacks. One of the most used vulnerabilities was CVE-2018-13379. Until today, it is the most exploited vulnerability in VPN products even though a patch for it has been available since May 2019. Other vulnerabilities that saw the most exploits were CVE-2019-11510 and CVE-2019-19781.
Organizations and individual users alike should be privy to these threats since in hybrid and WFH setups their consequences can more easily traverse both home and office networks. Given that WFH and hybrid setups test the idea of cybersecurity as a shared responsibility, what can employees and organizations do to prevent threats and bridge the security gap between office and home networks?
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks