
Blink and it seems like a new crippling vulnerability has popped up. Organizations may become hyper-fixated on defending against the newest, shiniest threats, but they also need to be cognizant of n-day vulnerabilities and unpatched legacy systems. Vastly different threats require a multi-prong approach across their entire IT infrastructure, including private and public clouds.
Intrusion detection and prevention systems (IDPS) are critical to providing comprehensive threat protection against known and undisclosed vulnerabilities. We look at the difference between intrusion detection systems (IDS) and intrusion prevention systems (IPS) and how to make an informed vendor decision to enhance your security posture and reduce cyber risk.
IDS vs. IPS
The difference between IDS and IPS comes down to what action they take when an intrusion is detection.
IDS will only provide an alert about a potential incident, from there it’s up to the SOC analyst to investigate and determine if further action is required. Common IDS types are:
1. Network intrusion detection systems (NIDS): Monitors traffic through various sensors placed on the network.
2. Host intrusion detection systems (HIDS): Placed directly on devices to monitor traffic so network administrators have more control.
3. Protocol-based intrusion detection systems (PIDS): Placed at the front of a server and monitors traffic going to and from devices.
4. Application protocol-based intrusion detection systems (APIDS): Monitors traffic across a group of servers.
5. Hybrid IDS: A combination of the above types of intrusion detection systems.
IPS is designed to block or remediate (depending on your post-scan settings) the detected intrusion. The four types of IPS are:
1. Network-based intrusion prevention systems (NIPS): Monitors and protects the entire network.
2. Wireless intrusion prevention systems (WIPS): Monitors any wireless networks owned by an organization.
3. Host-based intrusion prevention systems (HIPS): Deployed on critical devices or hosts.
4. Network behavioral analysis (NBA): Monitors for anomalous behavior within patterns of a network.
IDS + IPS = IDPS
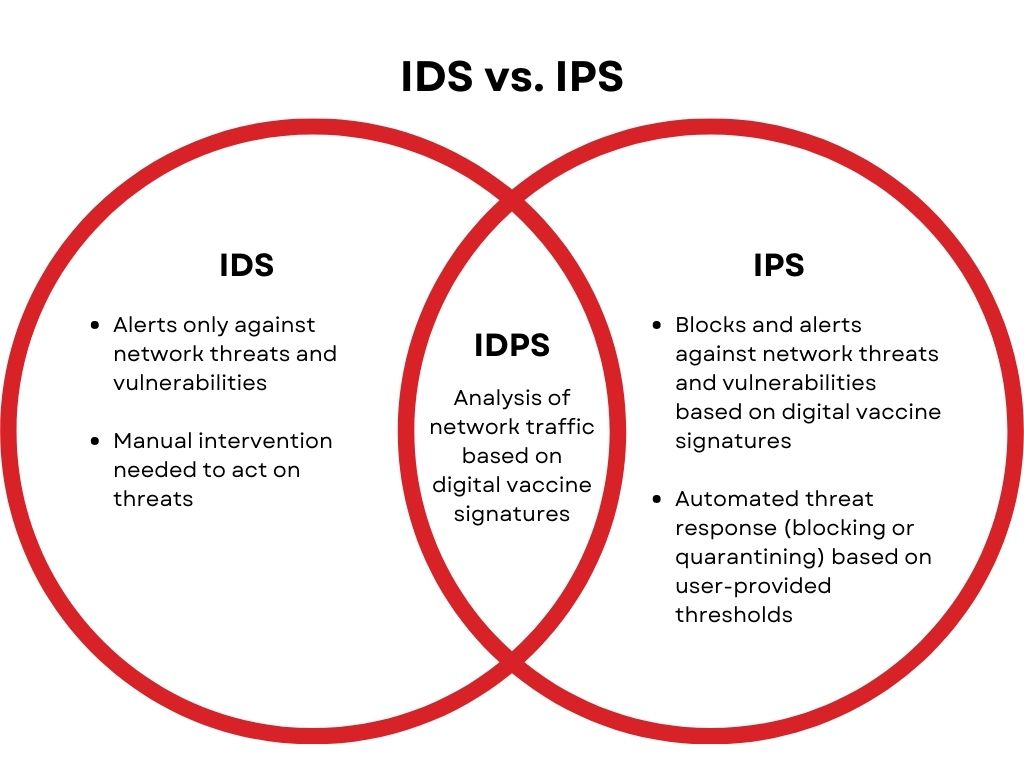
Don’t get stuck choosing between on or the other. Ideally you want to find an IDS and IPS solution that integrate – forming IDPS – for full detection and response capabilities. IDS will give you a deep understanding of how traffic is moving across your network, while IPS provides active network security by preventing and remediating detections.
Making an informed decision
Not all security solutions are the same. Some vendors are marketing masters who make a lot of noise in the industry, but in reality, they have subpar products. First, you need to assess and prioritize your organization’s risk to get the full picture of what you need from a solution. Then, you’re ready to shop. To make an informed and educated decision about your intrusion detection and prevention solutions, ask the following technical and non-technical questions:
Technical questions:
1. What technologies does the product use to detect threats? Look for a combination of deep packet inspection, threat reputation, URL reputation, on-box SSL inspection, and advanced malware analysis on a flow-by-flow basis to proactively detect threats. This will also help reduce the number of false positives, freeing up security teams to perform other tasks.
2. What technologies does the product use to prevent threats? With stretched security teams and staff shortages, a solution that leverages automation is key. Customizable post-scan actions and policies should be automated as well virtual patching to efficiently protect vulnerable and critical systems.
3. Does it extend to the cloud? With most organizations adopting a hybrid cloud model, protection across on-premises and cloud environments is critical. Make sure that the same protection offered for on-premises networks is extended to the cloud, like virtual patching, shielding against vulnerabilities, blocking exploits, and defending against known and zero-day attacks.
4. Does it integrate with other security products? The last thing you want is to add more point products to your portfolio. Not only do point products hinder visibility, but attacks rarely stay in siloes. To properly investigate and limit the scope of a threat, you need full visibility across the attack surface. A vendor with a cybersecurity platform simplifies security for overstretched teams by providing a single-pane-of-glass view into their infrastructure. Be wary of vendors trying to sell you a point-product bundle with reduced pricing; a true platform will integrate with the vendor’s ecosystem and play nicely with third-party solutions.
5. Is it scalable? The cloud has enabled businesses to spin-up projects instantaneously, which means you need an agile and scalable solution to provide immediate protection.
Non-technical questions:
1. What is the pricing structure? Don’t get stuck with underutilized subscriptions. A pay-as-you-grow approach with flexible licenses that can be easily reassigned across deployments ensures you won’t overspend and underutilize.
2. What support do you provide to help deployment and for future issues? Many vendors will “ghost” you after the sale, which can result in costly shelfware and slow adoption. The right vendor will act as a partner by helping with deployment, making sure all the necessary features are being used, quickly responding to inquiries or issues, and providing ongoing education to enhance your teams’ skillsets.
3. Do you have a threat intelligence program? The threat landscape is constantly evolving, and your solution should be as well. A global threat intelligence program – the key word being global – makes sure your solutions are backed with the latest security filters that cover an entire vulnerability to protect against potential attack permutations, not just specific exploits. For zero-day coverage, look for a vendor with a proven record in zero-day disclosure and an agnostic bug bounty program to help you pre-emptively protect your systems and limit the scope of an attack.
4. Do you have any market accolades or peer reviews to share with me? Anyone can say they’re #1, but can they prove it? Check out renowned industry analysts such as Gartner, Forrester, IDC, Omdia, and MITRE for objective reports. Also, a vendor with a large customer base won’t be shy about sharing peer reviews to help you better understand how their solution can address your security and business needs.
Next steps
For more information on attack surface risk management, check out the following resources:

