Islands of Telecom: Risks in IT
There is much more to the internet than applications, servers, and ordering pizza online. There is also telecommunications, and we liken this backend ecosystem to an island resort: the big attractions that it has founded on the “shores” of information technology (IT). To discover the hidden gems that most tourists in telecom miss, a reader should venture off the beaten path.
Telecom is a rich place to visit with its own cultures, traditions, and language. Located under IT, the industry of telecommunications is the 135-year-old bedrock of the said field. Research from the largest companies in the world fill the “gardens” of these islands, all of which are connected to each other but separate from the culture of IT. Telecommunications is an excellent spot to enjoy the results of some of the greatest and longest research investments in the last 200 years.
We break down the makeup of the island with 11 travel activities and feature the benefits and potential areas of concern. We also include the recommendations for tourists visiting the islands when they take their vacation from IT.
Culture, Traditions, and Language of the Islands of Telecommunications
Much like small islands found clumped together, wherein their connecting landmass can only be seen when explored from under water, telecommunications as an industry and as a study share common characteristics in IT. These common characteristics enable the continuous services and functions enjoyed by users. At the same time, they subject the ecosystem to threats and problems that we identify here.
Tap on the different areas of the Islands of Telecom to learn more about potential concerns and how to mitigate the risks.
Harsh environment
Telecommunications has a culture distinct from that of “mainland” IT. The drivers of telecom have bank-like regulations, while as a utility, telecom is expected to be “always on.” Combined, both typically rely on hardware that is more expensive than and completely different from that of IT. This hardware is further organized into types of network that do not exist in IT, such as cellular radio access network (RAN), mobile network operator (MNO), and mobile virtual network operator (MVNO).
Delegated government functions
Telecommunications performs a number of functions that are government-specific, such as 9-1-1, lawful intercept, police car radio communication, and the maintenance of emergency communications for a variety of purposes.
Distributed billing network
Telecommunications uses a distributed billing network where phones are similar to PoS machines and SIM cards are similar to credit cards. Unlike in IT where stolen information requires a buyer, telecom traffic can be directly monetized by criminals via roaming megabytes and minutes having a direct value. By routing hacked calls to a criminal number, criminals receive payment from either the victim or their telecommunications carrier.
Roaming
The islands of telecommunications are interconnected, allowing visitors to move from one island to another (i.e., roaming). Just as with physical islands where what occurs in one island would not be visible in another, a criminal that performs a crime on one island might not be visible in the security functions of another. The “island boat tour” of roaming is the foundation that connects all the Islands of Telecommunications in this report.
IMSI-IMEI Binding
In our metaphor of an island vacation, meeting someone and making a meaningful, binding relationship could be a priority. One example of a meaningful relationship is the binding of a phone hardware identifier (that is, the International Mobile Equipment Identity or IMEI) and a phone telecom network identifier (that is, the International Mobile Subscriber Identity or IMSI). By binding IMEI and IMSI together in a harmonized way, this “marriage” of identifiers becomes resistant to hardships such as fraud and other attacks.
These identifiers (IMSI and IMEI) can “share a room,” which in this case could be described by the mobile subscriber number called the Mobile Station International Subscriber Directory Number (MSISDN) of the device — in this case, its phone number. This IMSI-IMEI binding makes the phone number more resistant to abuse, in the same way that a hotel room is more resistant to abuse since there are more people watching it.
IMSI is a combination of numbers consisting of up to 15 digits. It is linked to a particular SIM card as one of its identifiers and is normally programmed into a SIM card by the manufacturer. The connection between IMSI and the phone number (also known as the MSISDN in telecom terms) is that IMSI is used inside the telecom operator network the way IP addresses similarly work in IT networks. Meanwhile, the phone number plays the role of the human-readable domain names.
IMEI is a 15-digit number burned into a mobile device (functioning as a radio module interface) and is similar to the media access control (MAC) address of a network card or the vehicle identification number (VIN) used by the automotive industry. Part of this number can be used to decode the vendor and model of a device, like iPhone XX or Samsung Galaxy XX. Devices that support several radio interfaces (or SIM cards) have, in general, several IMEI.
IMSI and IMEI can be retrieved with applications on the mobile device and are often used as the unique identifier, which is bound to a particular customer or device. Google and Apple have best practices for unique identifiers and almost block access to hardware identifiers in their recent operating system versions.
This pair of hardware identifiers can be used as a means of payment, as an electronic government ID for fraud prevention, or even as a requirement for creating accounts for some services. IMSI, IMEI, or the combination of both can be used for multifactor authentications (MFAs). Marketing and promotional campaigns often use them to identify customers, while an “advertising ID” is provided in modern mobile operating systems. It is also plausible for operational technology (OT) to identify unauthorized access (such as stealing the SIM card from a robot and putting it into a USB dongle to hack a factory) by binding IMSI and IMEI.
Both IT and OT industries tend to consider the IMSI, which can be considered as a hardware representation of the subscriber, while the IMEI can be considered a hardware representation of the equipment. They are assumed to be tightly and securely connected, and therefore IT app security can rely on these numbers. However, this presumption is incorrect: This trust can be exploited in different ways such as spoofing, SIM swapping, telecom proxies, and various gateways.
There are also devices where the IMEI can be reprogrammed. An IT app can be tricked into believing that nothing anomalous has occurred, when in fact the security context has been changed to allow an attacker to have control. In underground forums, we track special software solutions currently used by cybercriminal actors to trick anti-fraud systems. These solutions allow criminals to forge key parameters used for SIM/device identification, including IMEI, IMSI, SIM serial number, and carrier network information. These tools can be used for business process compromise (BPC) — one of several ways to conduct a digital product supply chain attack — to create accounts in different services or to initiate payments using stolen credit cards.
Examples:
The Canadian Wireless Telecommunications Council launched an IMEI blacklist for stolen phones in 2013. This list can be used to verify if a device is stolen based on its IMEI (that is, the device hardware serial number). If the phone attempts to perform billable activity with a SIM card, the SIM could also be blocked based on the activity. This is an “after-the-fact" lookup. A proactive version of this can be used to combine IMSI and IMEI as a single identity with assigned permissions, and to allow activities based on those approved.
With appropriate permissions, activities such as common telecom attacks are unlikely to work since robots should not be making long distance calls, cars should not be sending bulk email spam, and traffic lights should not be sending enormous amounts of SMS. However, this approach can be limiting based on the accepted activities of the device. For instance, some car models can receive over-the-air (OTA) SMS to initiate large downloads. It is true, therefore, that in all identity and access management (IAM) privilege systems, expected user behavior must be known prior to assigning permissions over bound devices.
Recommendations that telecommunications companies (telcos) or IT teams can request their provider for:
In the “island vacation” way of describing telecom to IT, an effective way of handling these risks requires good communication. When the systems responsible for IMEI and IMSI logs are harmonized (which is achieved with IMSI-IMEI binding), abuses of IMSI, IMEI, and phone numbers can be more easily detected, similar to how a guest immediately knows if their hotel room has been broken into. This harmonization is also called Cyber-Telecom Identity Federation (i.e., the unity of IT and telecom logs), which can identify inconsistencies between app identifiers, IMSI, and IMEI. As long as IT and telecom domains are separate, it is hard to mitigate those risks.
App developers should follow Google’s best practice guides for the unique identifiers. It is also recommended that they use MFA if a service is critical, such as payment transactions, enterprise virtual private network (VPN), and enterprise single sign-on (SSO), among other processes.
SIM-Enabled Vehicles
In an island vacation, the idea of taking an island tour by car, boat, or helicopter is something that many people like. In telecommunications, this is the idea of roaming mobility, where mobile devices (including phones and connected vehicles) can move from one radio network (or island) to another without needing to ask for configuration or permission.
To take these island-hopping trips, guests have to pay for them. The payment for moving from one island to another during a tour could be paid for using a credit card during a vacation. But in telecommunications, it is paid with the device’s SIM card, which can be likened to a “telecom credit card.” Vehicles with the ability to bill their SIM can roam from one radio to another network seamlessly.
As a vacationer, a tourist on the boat trusts the pilot to take them to a destination that only the pilot knows of (which is the point of paying them). On the other hand, a malicious pilot can take a vacationer to places they don’t want to go to, and it would be hard for the passenger to tell the difference until it is too late. Something similar can also happen in telecom, in which a mobile device can find itself in a security context that can only be detected when it is too late.
Vehicles as “cellphones with wheels, wings, or propellers,” have a feature that cellphones and other radios do not: the ability to move mass around using wheels or propellers. This mass can be valuable, dangerous, or both.
This mass can be some or all of the following:
- Cargo, which can represent money and theft
- People, which can represent danger and death
- Body of the vehicle, a ram if moving or an obstacle if not
- Multiple vehicles as a fleet
- The nature of a vehicle as a system element with delegated authority, representing the semi-autonomous authority of the system’s owner, and therefore the abuse of anything it can do
These can be combined by an attacker in many ways, including:
- Moving the vehicle to an arbitrary location to remove its cargo (theft) or to add cargo for stealthy delivery (for example, illegal drugs).
- Moving the vehicle and not letting people out of the moving vehicle, for the sake of fear of kidnapping and extortion.
- Moving a fleet of vehicles to a location such as a downtown area or toward highway traffic using an aggregator and having them all stop and become unresponsive as an example of extortion or denial of service (DoS) against a city.
- Performing fraudulent SIM-based telecom billing as a fleet, using its role as a system element with delegated authority to place large numbers of roaming long distance calls to expensive international phone numbers controlled by the attacker. This would result in hundreds of thousands or millions of US dollars in fraud for which the SIM owners would be responsible for paying. A secondary effect is that the connectivity of the fleet could be blocked at the telecom level when the fraud is detected.
- Many other combinations of mass, malice, and timing in physical space as previously reported.
These interactions and others are exploitable based on the technology architectures used, which are driven by the purpose of the vehicle (unmanned, passenger, land, air, or sea).
Vehicle designers might want their vehicles to be capable of traveling at speed in coordination with other vehicles, or via remote locations such as the sky or the sea. For these kinds of vehicles with varying capabilities, specific considerations with corresponding technologies are needed, such as:
- Speed, which would require cellular technology, specifically intercellular handoff requiring a telecom core network (4G or 5G).
- Coordination with other vehicles, which could require Wi-Fi or 4G if the coordination is between vehicles traveling at slow speed, or 5G if the coordination is between vehicles traveling at high speed.
- Navigation in or to remote locations, such as the sky (which would require Global System for Mobile Communications Association [GSMA] drone air traffic control) or the sea (which would require maritime controls for large oceanic cargo drones, including 5G satellite).
Generally, the slower, shorter-range, and less dangerous vehicle is more likely to be non-5G and therefore non-SIM-based. However, if it must move Beyond Visual Line of Sight (BVLOS) as a drone, an autonomous ocean vessel, or an autonomous car, it will be 5G since higher-quality 5G data is necessary. If the vehicle is slow, operates on short range, and functions in a non-public space, it might tolerate poor data quality and might be operable using Wi-Fi, 4G, or other “best-effort" radio protocols. Such vehicles might be non-4G and non-cellular, and therefore do not have SIM cards. Warehouse drone forklifts are less likely to be SIM-based or 5G. Autonomous vehicles such as cars, highway trucks, and long-range drones are very likely to be 5G. Drone ocean vessels are potentially 5G and satellite, meaning ports and harbors are likely to be federated to allow fine-grained coordination of docking.
eSIMs (5G era cellular) and SIMs (4G and pre-4G cellular) are the source of identity for this class of fast, dangerous, and long-range capable vehicles. Any of the attacks described in this paper can be performed on SIM-enabled vehicles: fraud as a way of getting a target victim blocked (black flag DoS), self-monetizing billing fraud (similar to credit card fraud) against the SIM card of the autonomous vehicle, and redirection of the SIM communication path to a criminal-controlled network that can set security to be lower (allowing interception and/or injection of false data or malware).
In addition, rule-based attacks can be used against the vehicle, and variations of these function against land, sea, and air vehicles. The complexity of a connected vehicle can be seen in Philippe Z Lin’s article on connected buses in Taiwan.
Figure 1. A number of rules-based attacks can be used against connected vehicles.
Since autonomous vehicles must follow rules such as laws, legal loopholes can be used against them. Vehicles might not be allowed in certain spaces identified by images (such as street signs or ground markings), so spoofing these in a simple way with paint or adhesive tape could deny access or capture the vehicle. Areas associated with specific vehicle behaviors can be simulated using radio identifiers, causing a particular behavior at an attacker’s request.
Recommendations that telcos or IT teams can request their provider for:
- Sensor federation. By harmoniously connecting logs from sensors in vehicles, unusual patterns of events can be detected and addressed either proactively or after the fact.
- Zero trust architecture. This means of handling and human device identity and privilege is much more granular than traditional IAM methods, and it restricts lateral movement in networks, even when those networks are multiple kinds of devices or users (including devices that are also users, such as autonomous cellular vehicles).
- IAM. This should be modified to address the cellular telecom mobile class of vehicles, such as 5G vehicles. This requires additional logs and metadata to be bound by IAM privileges, such as movement from one area triggering an alert, or movement beyond an allowed speed. These “mobility” behaviors should then trigger appropriate security responses.
- SIM subscriber management federation for both humans and machines. SIM cards should be considered as a kind of privileged access and should have specific IAM rules to prevent SIMs from taking unusual actions. These actions might include “impossible behaviors,” such as preventing cars from sending SMS spam, oceangoing ships from rerouting voice traffic, or long distance calls being placed from flying drones.
- Business enterprise security architecture review for exploitable systemic use cases. Business security architecture, which applies a “hacker mindset” to business cases early in the design process, should be performed while changes are cheap yet significantly effective. Many easily exploitable business-level design flaws, which are immediately obvious to a hacker with design skills, can be corrected.
Voice Interception
When visiting the “Islands of Telecom,” a tourist has to be aware of potentially losing their luggage (content). This could happen as they momentarily put their luggage down beside them to hail a taxi, or while registering for a room inside a hotel, or during any other transfer point between means of travel. The loss of a concentrated package with all the things that a traveler needs can be very disruptive to having a good vacation. The content of the luggage (the “payload”) is of value to an attacker for reselling or even for gathering information about an individual and their home. Examples of such data would be information on luggage tags and information inside the luggage.
In a similar way, the payload of voice communications can be stolen (intercepted) to extract its value. Since voice communication is considered concentrated value, it is highly desirable to criminals. An attacker can even select the highest-value luggage content at a glance based on how nice the suitcase is. This maps to telecom attacks where an attacker selects their victims by the nicest source or destination (such as if a victim is an executive or works for a bank).
Despite the emergence of audio “deepfakes,” voice conversations are still the most trusted type of communication where the most sensitive secrets are spoken. Compared to landline phone calls, calls through mobile operators are often considered more secure. However, this statement is true only when the resources of an attacker are limited. Starting from a budget of several hundred US dollars, an attacker can hack into a legitimate indoor small cell that a telecommunications company installs in private spaces (such as bars, offices, and shopping centers where signal needs to be enhanced) and intercept calls and data. In another instance, an attacker can buy a war box to force victim phones to fall back to the less secure GSM, and then intercept the voice call and data with a rogue base station. Rogue base station attacks can also be used in places with weak or no signal, such as parking lots, underground structures, and rural areas. With a budget of several thousand US dollars, due to a lack of proper security configuration on the telecom side, an attacker can pay to access SS7 and intercept calls from remote geographical locations.
The key point is that internal telecom infrastructure is considered as a trusted environment, and interconnection with different telecom operators when users are roaming is based on this trust. An attacker exploits this inter-carrier trust to implement remote attack scenarios. Having access to telecom infrastructure in a foreign country is often enough to conduct voice call redirection and interception.
Voice call interception attacks are more likely being used against C-level executives, politicians, lawyers, traders, and activists. This class of attack bypasses information security while accessing high-value concentrated content (that is, a voice). Access to this information gives serious competitive advantage and can be used to influence the outcome of negotiations in stock trading or even for purposes of extortion. Wiretapping is stealthy and often cannot be detected on the IT side of the infrastructure.
Examples:
- A private investigation agency in Italy bribed contacts in government agencies to wiretap chosen users of Telecom Italia, in addition to many similar cases in the country.
- UK and US intelligence agencies remotely hacked into Uganda’s phone network to intercept voice calls of high-profile figures of that country.
- Chinese researchers disclosed a sophisticated method to downgrade a victim’s connection from Long-Term Evolution (LTE or 4G LTE) to GSM.
- GCHQ hacked the biggest Belgian telco to conduct man-in-the-middle (MitM) attacks.
- The International Institute of Cyber Security released an online tutorial for pentesters to intercept VoIP calls and voice packets.
Recommendations that telcos or IT teams can request their provider for:
It is important to ensure that telecom operators have extra security tools to enforce and straighten default inter-carrier trust. Special types of telecommunication firewalls can be deployed from the provider’s side for this purpose. Technical detections can be implemented with telecom and law enforcement collaboration.
Users are encouraged to use voice applications that support point-to-point encryption. If possible, users should disable GSM on their phones. If “normal” voice calls are inevitable, they are advised to enable Voice over LTE (VoLTE) and make sure that internet protocol security (IPsec) is enabled — otherwise, it would be as clear as a GSM/2G phone call. It is also recommended that users switch to flight mode in areas with weak signals if they cannot do any of the aforementioned suggestions.
The financial algorithms indicating abuse can generate logs that can be federated (combined or harmonized) with telecom logs, if available. These combined logs can be set to report on anti-money laundering (AML) audit and controls (including fraud and billing abuses). This can also be set to trigger fraud-specific algorithms such as Benford's Law (a statistical law commonly used in detecting fraud). Incident response can then track this abuse as a set of predictable and alertable criminal behaviors.
The visibility of a unified security operations center (SOC) covering an OT network, an IT network, and a campus network environment is important. An attack that crosses from one silo to another cannot be detected, but a unified SOC can see all.
SMS interception
When things are going well on an island vacation, a tourist might meet a lovely person in the bar and decide to give them their room key, as well as a meaningful look before leaving the pool bar. This key and its matching room number are two critical pieces (factors) of information that can’t be misplaced, or access will be denied. If, however, the key or its room number is taken while the guest was paying for the drinks, the thief of the two-factor authentication (2FA) token — the key with the room number — can now enter their new friend’s hotel room and steal something from it while they are in the shower. At a minimum, the tourist will lose a friend and the opportunity to connect. Worse, the hotel can even blame the guest for their losses. If the guest is attacked in their room, in the dark, the hotel might also leave the guest with the responsibility of someone else’s actions, with numerous witnesses who saw the guest and their new friend together earlier (that is, logging systems showing legitimate 2FA token access).
In a similar way, text messages are used are to grant network access as a second factor, often along with public identifiers such as a username (which works as a kind of room number for the internet).
SMS is not encrypted any more than the teeth of a metal key are a secret to the person holding it: They can see they key’s teeth and make a copy if they choose to do so. In fact, anyone who has ever held the metal key can make a copy and use it anytime in the future. This is similar to sniffing (using cellular radio) or capturing (using roaming vulnerabilities) the content of an SMS.
SMS-based authentication is nowadays a common gadget in the toolboxes of both IT and web developers. In addition to authentication apps running on cellphones, SMS is thought to be a reliable fallback option and a good way to receive one-time passwords (OTPs) for logging in or processing transactions. However, SMS is transmitted in cleartext within the telecom network, making it prone to interception and downgrade attack. A downgrade attack involves the use of a radio jammer or a crafted radio signal packet to make a cellphone downgrade from a newer generation network (such as LTE) to an older, less secure one (such as GSM).
A telecom network is usually protected. However, the definition of “protected” depends on how a telco perceives the term “security domain” and how communications across domains should be protected (that is, while the term is defined, it does not include how big or small it should be). In reality, a telecom core network is usually one domain, meaning that data within the core network is only protected from outside and not inside. It is thus possible for any insider or hacker within the telecom network to intercept SMS in cleartext. OTPs and authentication codes can also be stolen within the telecom, even though no direct evidence has been publicly reported to date.
A more common risk is the GSM/2G protocol, which is outdated but still widely used worldwide. In areas where SMS is transmitted over GSM, the SMS is in cleartext and can be decoded over the air. While it means that the attacker has to be within the vicinity of the victims, there are many ready-to-use products and open-source software for amateurs and researchers. In the service area of 4G/5G, SMS cannot be caught over the air. Therefore, advanced hackers could either choose to downgrade to a less secure network like GSM, or attack telecom-native protocols.
SMS is also used as a backup channel for remote sites in OT. Industrial routers and cellular OT devices support commands over SMS or at least remotely via SMS. Since GSM (being older) has a much wider range of coverage compared to other, newer generations of telecommunications technology, it is more susceptible to OTA SMS interception. Moreover, attackers can fake caller IDs to bypass the “trusted caller list,” or even use a rogue base station to send SMS commands. Due to the lack of “mutual authentication” in GSM, a rogue base station with a very strong signal can take over a cellular device without proving that it is the correct base station.
For general users, there is a less technical and social engineering way to overtake SMS: SIM swapping. There are many reports about stolen bitcoin wallets and bank account transfers. The attacker pretends to be the victim, calls the victim’s telecom service center, and claims that they lost their SIM card (or a similar story). Once the subscriber account and phone number are transferred to the attacker’s SIM, all text messages are sent to the attacker.
Examples:
Researchers have demonstrated how to steal a Gmail account and take control of a bitcoin wallet by using SS7 to intercept a password recovery SMS. Many cryptocurrency investors have also reported stolen bitcoins after falling victim to SIM swap scams, with one report disclosing up to US$24 million in losses. Meanwhile, Twitter disabled its “tweet from SMS” function after its CEO’s account got hacked and posted inappropriate tweets via SMS.
In some cases, malware is developed to steal short messages. A malware dubbed as “MessageTap” is reported to hack SMS centers in telecom for political reasons. Another malware pretending to be Android tools was used to steal 2FA codes of Google accounts.
Recommendations that telcos or IT teams can request their provider for:
IT people should be aware that SMS is not a reliable way of authentication. There are many substitutes: a mobile app authenticator, a physical OTP generator, and a mobile phone push-notice, to name a few. Revised Payment Service Directive (PSD2) in Europe also mandates at least two factors among listed means of MFA, where SMS is only a “possession element” and should be combined with other factors.
It is hard for a network to distrust SMS because it is limited by network coverage. If it is ever possible, IT teams can request an upgrade to LTE or satellite connection and disable GSM for better security. Some devices support a “trusted caller” feature and block SMS from unlisted callers. Even though it is possible to fake a caller ID, enabling this function protects devices to an extent. If SMS is never used in an industrial control system (ICS), security teams can ask the telco to disable it in both public and private Access Point Name (APN).
Data Interception
Sometimes, even a modern traveler with a cellphone will receive an old-style, hard-copy message that they can pick up at a hotel’s front desk.
Depending on how modern the hotel is, they might not perform much (or any) authentication on someone asking for “their” messages. Additionally, inexperienced and tired staff members working late at night might ask for less information than those at peak hours. Similarly, an attacker who wants the content of the message (intercept the data) can simply come back at a later time to attack a weaker kind of message security.
When talking about telecom, generally the older the technology, the more inferior the authentication methods. If a telecom carrier operates multiple types of telecom at once (3G, 4G, and 5G, for instance), much of the data of a newer technology (5G) can be intercepted by using an easier or older technology (3G or 4G).
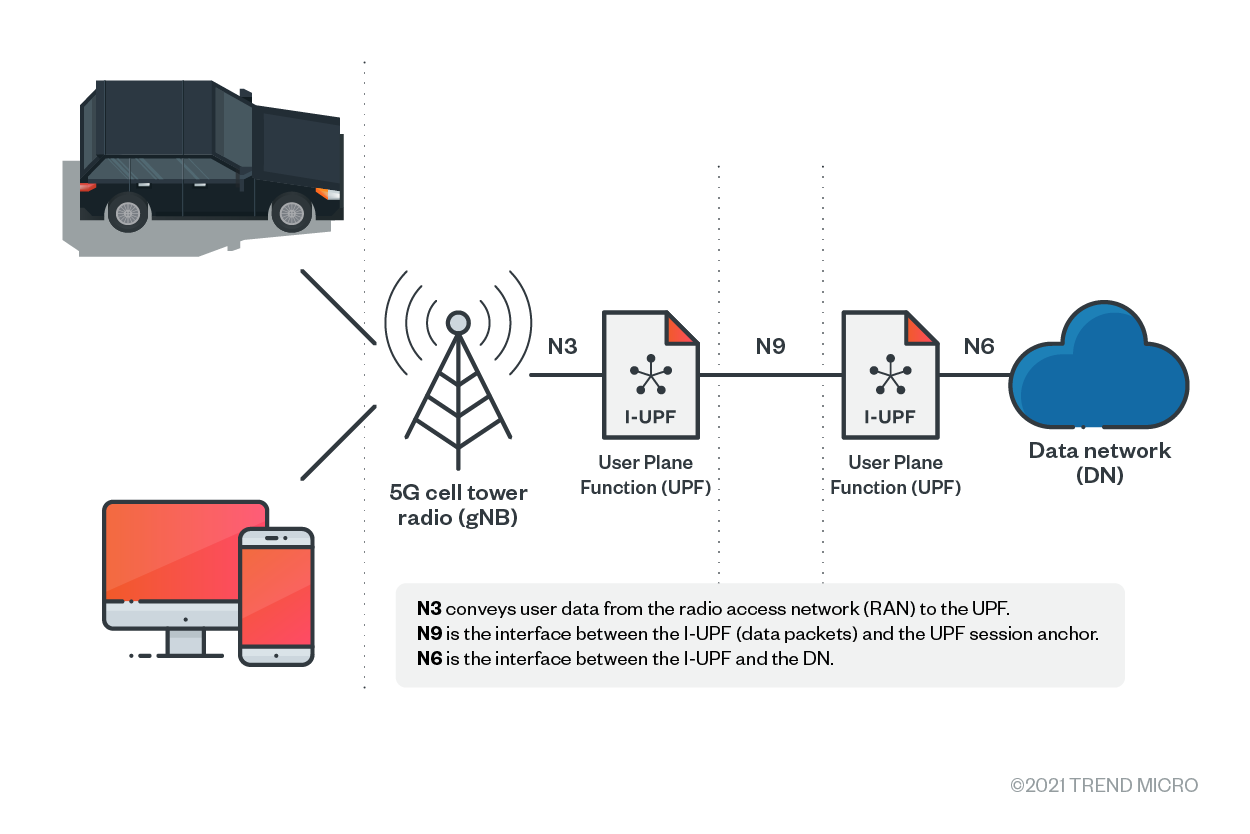
In cellular telecom, data packets are transmitted from cell phones to base stations over radio, encapsulated, sent back to the core network, and finally reach the internet. The mechanism is designed to keep the data connection intact while moving. This is illustrated in the following figure.
Figure 2. Data transmission via cellular network
There are several points where data can be intercepted (from left to right):
- Data can be intercepted from a cellphone, if a piece of malware is pre-loaded or installed.
- In terms of cellular (due to lack of LTE coverage or a downgrade attack), a rogue base station can be used to “forward” the data packets.
- A base station is the place where radio signal is converted into cellular (GPRS Tunnelling Protocol GTP) packets.
- The link between base station and core network is not necessarily protected by VPN or IPsec, and therefore could be intercepted if the link is physically accessible.
- Data packets inside the core network (the blocks between a cell tower and a data network on the chart) could be encrypted and certificates could be signed by a certificate authority. However, the packets are transmitted in cleartext in earlier (pre-5G) generations of the core network. App owners and programmers cannot simply rely on their telco in terms of encryption.
- The gateway to a data network is under the realm of a carrier operator, but we can only assume that it is secured well.
Moreover, when a user is roaming in another cellular network, data packets are switched via interconnecting networks. Unencrypted data can also be easily extracted from there.
Although many applications support end-to-end encryption and websites are mostly in HTTPS nowadays, there are still many services that transmit data or URLs in cleartext, thus potentially falling victim to data interception. For example, Trend Micro Research identified some online banking and financial technology (FinTech) API calls that have the user’s ID, password, GPS coordination, session token, account number, and other personal details in the passed URL. As a result, a user’s money could be stolen, or in the worst case scenario, a user’s personally identifiable information (PII) could be leaked.
Examples:
Belgacom, the largest telecom provider in Belgium, was hacked back in 2011. According to reports, the hacker was able to intercept encrypted and unencrypted data flow. However, we don’t have more details on where and how the data was intercepted. More recently, Cybereason has disclosed an advanced persistent threat (APT) campaign infiltrating 10 telecommunication companies. Even though call detail records (CDR) were the main target of the attackers, it is very likely that they have the capability to intercept transmitted data.
Recommendations that telcos or IT teams can request their provider for:
Many common services are now encrypted by default. IT teams should not use their unencrypted precedents. Rather, they should always use internet relay chat (IRC) over SSL, simple mail transfer protocol (SMTPS), internet messages access protocol (IMAPS), HTTPS, and message queueing telemetry transport (MQTTS). Companies should not assume data security over a carrier network. E-commerce platform providers, online retailers, and point-of-sale (PoS) providers should pay special attention to data security and integrity, where Payment Card Industry Data Security Standard (PCI DSS) has defined the baseline security standards to protect payment cards and membership data both in storage and in transmission. FinTech companies are suggested to follow the regulation of Revised Payment Services Directive (PSD2), even if they are not in Europe and in addition to local regulations.
Campus Networks
On vacation, a tourist might choose to stay at an all-inclusive resort. In telecom, this resort is called a campus network. There, all their needs as a traveler are provided for, and unique needs can also be met with a small amount of preparation (kind of like a concierge). As a closed or non-public facility (also called a Non-Public Network or NPN in telecom), a higher standard of security can be assumed, sometimes incorrectly. These kinds of resorts or campus networks attract a lot of attention from attackers since they concentrate a lot of “treasure” in a single place. Just as an expensive market attracts pickpockets intent on stealing from rich tourists, resorts and NPN campus networks attract their own kinds of thieves.
In addition, NPN networks and resorts, by their nature, have policing that is separate from the outside area. These non-public places have their own vulnerabilities that specifically arise from this customization and separation.
An NPN or a campus network is a cellular network deployed in limited geographic areas on regulated radio bands or Civil Band Radio Service (CBRS) bands. It is proposed to smart factories, big warehouses, international ports, and healthcare facilities. Sensors, programmable logic controllers (PLCs), actuators, and autonomous guided vehicles (AGVs) used in warehouses can be connected to campus networks where data is intentionally kept local and connectivity is required to be fast and stable.
A campus network can be operated by a telecom, an operational contractor, or by the IT department of the entity that uses it. The difference in domain knowledge between IT and cellular operator is huge, thus raising the communication cost to a great extent. Whether the telecom or the IT department is the operational team, the campus network is similar to the IT network from the perspective of misconfigurations, infiltration, DoS, network scanning, DNS spoofing, and identity spoofing, among other potential gaps and attacks. Despite the physical layers being different between the LTE/5G campus network and Wi-Fi, the campus network is a wireless network that needs to be secured with a firewall, an intrusion detection system and intrusion prevention system (IDS/IPS), and cybersecurity solutions. Moreover, SIM cards can be compromised and used to infiltrate the network for lateral movement. An unknown pair of IMSI (the unique ID on a SIM card) and IMEI (the unique ID on a cellphone and a cellular MODEM) is comparable to an unknown MAC address that tries to connect to the company Wi-Fi and should be cut off immediately.
The campus network uses commercial off-the-shelf (COTS) components, such as standard rack-mount servers, routers, firewalls, gateways, and operating systems. Zero-day or unpatched one-day vulnerabilities can be used to infiltrate the campus network. Unsecure operations, administration and management (OAM) networks can be used by hackers as well. Limited by radio power regulations, small base stations are usually deployed and connected to exclusive or existing routers. The risk of misconfigurations (such as virtual local area networks or VLANs that are not properly segregated), unsecure routers, or unencrypted communication between base stations and the core network can be very high, causing impact on device attachments, authentications, data security, and service level.
Since a campus network provides IP-based data connections, generic vulnerabilities and mitigations also apply to it. For example, sensor readings that can be injected and impersonated might result in miscalculated volume of goods, wrong temperature, the opening of valves that should not be opened, or interrupted production lines. Application-level inspections should be added on top of the security provided by the campus network.
Examples:
Since the LTE/5G campus network is still new, we are not aware of any breach to date. Several research papers are worthy of study:
- Positive Technologies’ research on 5G security issues
- “Attacks from 4G/5G Core Networks: Risks of the Industrial IoT in Compromised Campus Networks,” a Trend Micro Research on campus network security and demos to attack an ICS
- Ericsson’s business and architectural overview, A Guide to 5G Security in Industrial 4.0
- National Institute for Standards and Technology’s (NIST) 5G Cybersecurity: Preparing a Secure Evolution to 5G
Recommendations that telcos or IT teams can request their provider for:
LTE/5G does not mean increased cybersecurity per se. LTE/5G still needs professional configuration, maintenance, proper installation of cybersecurity appliances, and periodic patches for it to be kept secured. A campus network management system can be used to detect and manage unlisted IMSI/IMEI pairs. In case of an anomaly, a user device can be disconnected or quarantined on demand. Asset management is crucial and should enlist every single SIM card and eSIM. A unified SOC that can oversee the entirety of the IT, OT, and campus network could help identify attacks that go across the boundaries of their respective expertise.
The connection between base stations and the core network should not be overlooked. It should be protected by VPN or IPsec, even when they are all located inside the campus. Security teams should protect the RAN and verify whether a downgrade attack is possible. They should also disable null encryption schemes and inspect known vulnerabilities that lead to null encryption.
The communication channels found in mobile equipment — such as industrial routers, PLC, sensors, and actuators with cellular connectivity — should be encrypted and integrity-protected, just like SSL/TLS used in HTTPS, secure Lightweight Directory Access Protocol (LDAPS), and MQTTS, to name a few.
It is also recommended to have an exclusive person in the IT team to communicate with the operational contractor or to set up an exclusive team to operate the campus network.
Critical Equipment
Resorts are like small cities, and they have special rules for citizens (aka tourists) that are often superior to what others on the island might experience, such as customized security and flight arrangements. Another example would be rules requiring heightened protection for these important services. Over the last hundred years or so, telecom has inherited almost every type of critical service: from those provided to high profile executives and celebrities, to those services responsible for maintaining emergency services, including nuclear reactor telemetry.
Mobile phones that belong to high-profile government employees, C-level executives, police officers, and journalists are obviously valuable targets. Together with financial fraud, an attacker can have the capabilities to map locations and profile movements of these high-value targets. Phones are just one class of mobile devices that can be used for such activities, and there are other mobile device classes that could be targeted to cause severe impact, either on individual devices or on the whole infrastructure that a user is associated with. Individual devices include mobile equipment that are used by public safety and emergency services in the healthcare industry to notify doctors about patient transfers from remote locations. Despite the primary function of these devices being different from that of a cellphone, SIM cards in these devices bring a similar range of capabilities for an attacker — sometimes even wider. An attacker can implement fraud schemes against the equipment, for instance. In this case, defenders are often limited to mitigation capabilities since typical mitigations (like temporarily blocking a SIM card) can leave an impact on human lives or affect sensitive government functions. These complex situations involve SIM cards used not only in the healthcare industry, but also those used in the areas of public safety and emergency services, where devices can be used to implement impersonation attacks.
For SIM cards used in Industry 4.0 environments or remotely controlled telemetry sensors such as those installed at gas and oil pipes, mitigation can be implemented during planned maintenance windows. They can also require interruption of core business processes. The impact of mitigation can be higher compared to ongoing fraud losses.
Those classes of IIoT equipment can be subjects of attacks and abuses in a similar way that a smart phone can be subjects to such, including sending fraudulent messages, making subscriptions and committing a variety of telecom and payment card frauds. Together with these, extortion can be used to monetize access to equipment by implementing business service outage against these devices.
The other group of risks is related to customer self-management portals. These portals help in managing telecom-related services for big telecom customers and infrastructures like smart cities, smart roads, smart vehicle fleet management, and smart factories. The portals are typically web-based and use password-based authentication. Access to these portals gives an attacker capabilities to control SIM-related operations at scale. This means that an attacker can initiate mass SIM provisioning, gain access to phone numbers that belong to sensitive customers or equipment, and massively initiate and redirect calls, SMS, and data. Since billing of controlled SIM cards can be directly linked to organizational bank accounts, those intrusions can be used by an attacker to initiate fraud, force organizations to unknowingly participate in money laundering operations, and manipulate sensitive functions of critical infrastructures.
An attacker can also implement a mass smart infrastructure DoS and even extort their victims. By accessing this portal, the attacker could change the policy related to different groups of SIM cards. These changes to the SIM cards could include increasing spending limits to increase criminal revenue from SIM card fraud or to enable stealthy money laundering operations. By enabling international voice calls or SMS to expensive criminal-controlled phone numbers, an attacker can turn even stationary factory SIM-enabled equipment into victims of mass fraud. Attackers can take over control of equipment by pushing new configuration files or by initiating a credentials reset. Using their access to equipment like cameras with vehicle plate recognition or face recognition capabilities, attackers can hide traces of crimes that they commit, or precisely trace potential victims. By faking the configuration of speed-capture cameras, dropping speed limit settings significantly (for instance, 30 km/h instead of 50 km/h), an attacker can initiate an avalanche of falsified charges and overload processing facilities. By slightly affecting speed limit settings (for example, by setting the speed limit at 77.5 km/h instead of 80 km/h), an attacker can trigger a huge volume of corner cases with questionable charges against citizens and leverage this to polarize a population against its government. Attackers can also use these methods to trace the movement of VIP cars moving inside smart city infrastructures.
Additionally, legitimate infrastructures that are related to critical mobile-connected equipment can be used by attackers to initiate attacks on other organizations. By getting access to equipment with facial recognition capabilities, an attacker can trace and predict movements, groups, and persons of interest, and then leverage those capabilities for more effective monetization, hiding their own traces, or even planting fake evidence.
By accessing a smart road infrastructure, an attacker can manipulate traffic lights to redirect road traffic or to manipulate road signs to initiate traffic jams during critical events like political campaigns, concerts, or sport events.
Examples:
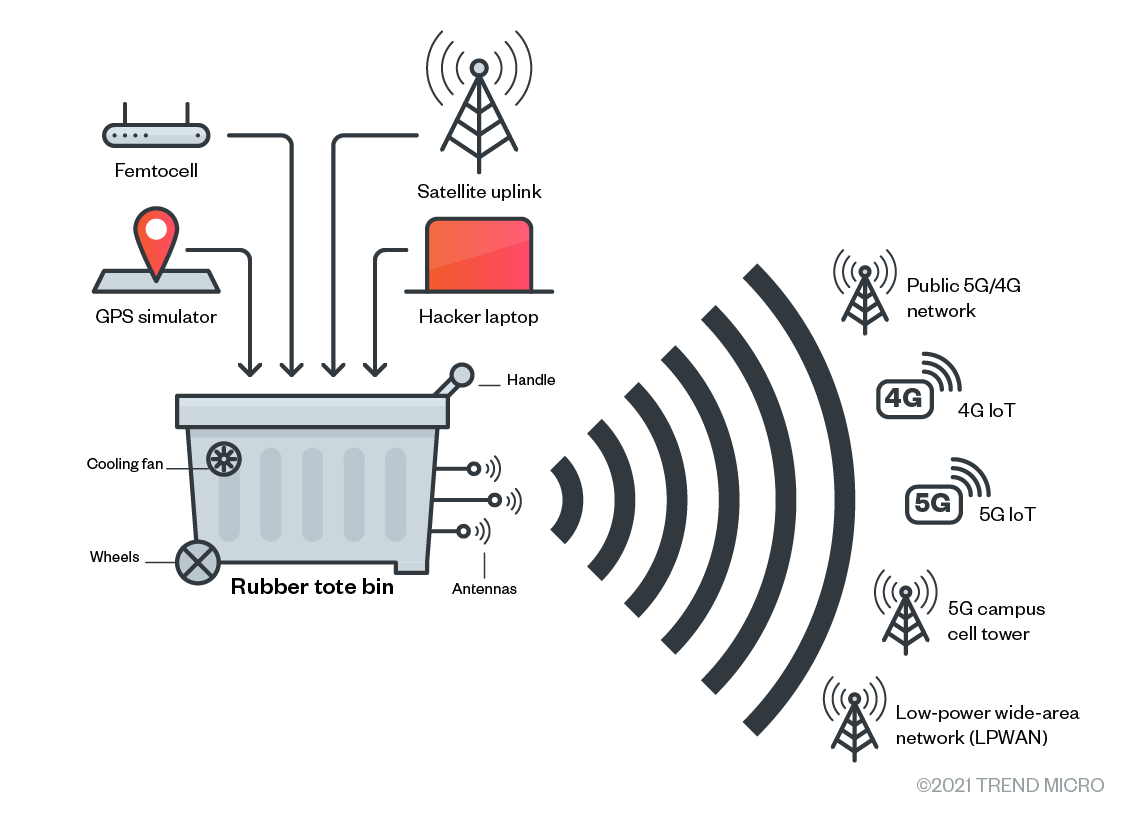
Telemetry related to real-time traffic jams in Moscow was manipulated by telemetry injected from GPS simulation devices.
Recommendations that telcos or IT teams can request their provider for:
The deep integration of critical and smart infrastructures with telecom brings extra capabilities and risks. The said risks should be considered throughout all the project development life cycle steps and addressed during or before infrastructure deployment. If these risks are not addressed properly, an attacker can use techniques that allow their persistent presence and continued monetization. This presence can avoid detection if the volume of the fraud is lower than that of the detection threshold. In case the fraud is detected accidently, it will remain unmitigated if the cost of mitigation is greater than the cost of the fraud.
SIM Billing
When traveling, it is important to have money to have fun. While credit cards work just as well in the mainland of IT, in the Islands of Telecom, SIM cards are used instead. All billable telecom activities (long-distance calls, roaming, cellular data) are billed to the telecom business account represented by the SIM card.
SIM cards are effectively small credit cards that fit into cellphones. The cellphones perform services for the user, and the cost of these services are billed by the telco to the SIM card. This SIM billing is the foundation of the global business model on which cellphones depend.
On the other hand, the entire fraud industry can be summarized as the abuse of billing. Since SIM cards are similar to credit cards (and credit card fraud is considered very mature), the industry of SIM card billing fraud is significantly large and mature as well. Most credit card frauds have a corresponding SIM fraud. Nevertheless, there is also a number of fraudulent activities enabled by telecom technology that do not have a corresponding credit card version.
One can assume there are many methods of credit card fraud and that these work on SIM cards as well. Stealing a credit card and using it to make purchases works on SIMs, too, and so does pretending to be someone else to obtain multiple credit cards to use for online purchases. Using credit cards to pose as someone else to authenticate access, access a website, or appear older all work with SIM cards as well.
SIM cards can also vary slightly from credit cards at times. Credit cards usually have a credit limit, but SIMs often do not. Credit cards have credit card fraud detection, while SIM cards have a greatly reduced method of alerting. While credit cards are used as a kind of soft authentication method to verify that a person’s identity is who they say they are — a low-risk example — SIM cards are directly used for hard network authentication. By that point, the credit card concept of “relative risk” is irrelevant since the criminal who controls the SIM card controls the transaction. Examples of this can be found in the Europol-Trend Micro Cyber Telecom Report 2019.
SIM billing is subject to many fraudulent activities, including inter-carrier fraud such as international revenue sharing fraud (aka IRSF, wherein a criminal colludes with an unclear carrier to falsify billing), short stopping (playing man-in-the-middle between two billing carriers), tromboning (hiding one kind of network behind another or sending domestic mobile calls via international routes), and other schemes. In these examples, the fraudulent customer phone account of Carrier B (controlled by the hacker) is called by the hacked victim customer phone account of Carrier A since the subscriber (hacked phone) called the hacker’s phone under Carrier B. Carrier A pays Carrier B, who then pays the hacker. Most telecom frauds are technical variations of this.
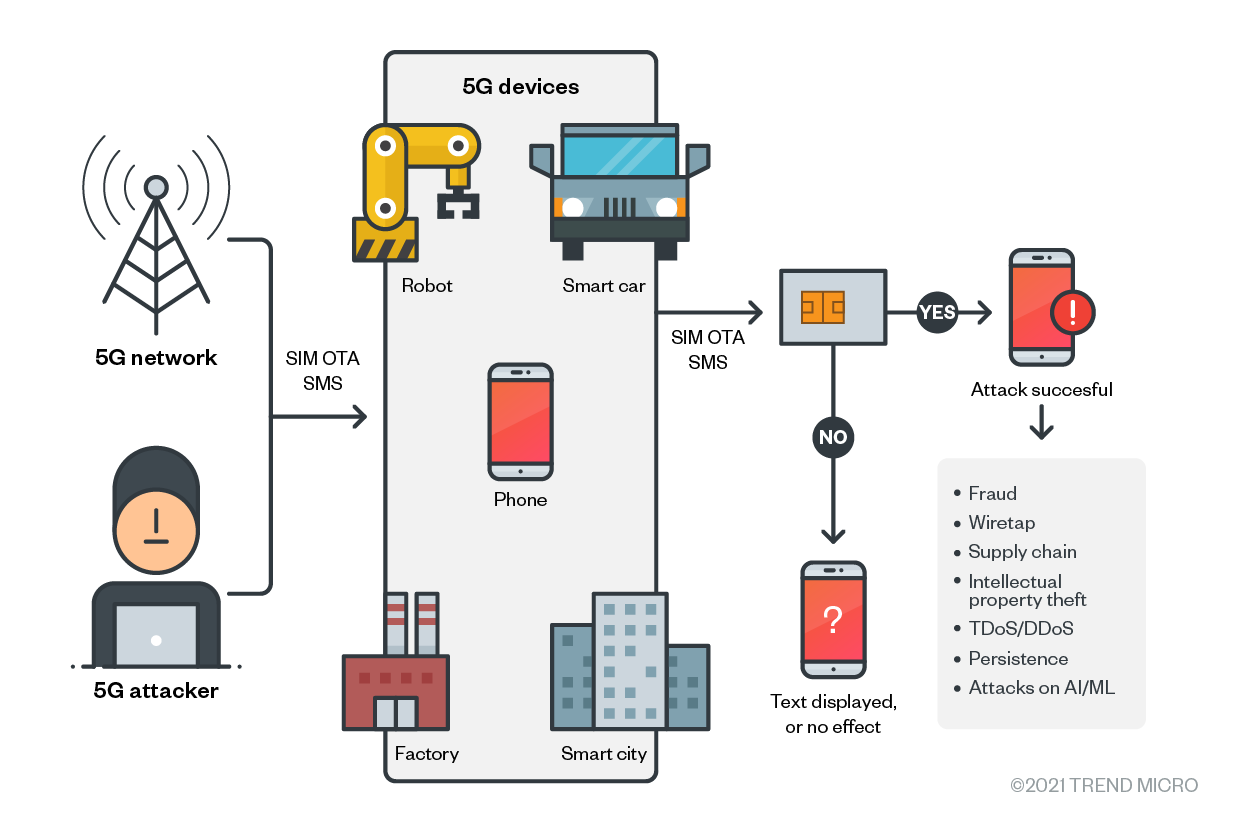
Any kind of device that uses cellular radio will rely on SIM connectivity. Examples include cellphones, connected cars, many IT networks (such as those for disaster recovery redundancy), and an increasing number of IoT devices, robots, and drones.
Figure 3. An attacker using 5G network and connected devices to commit fraudulent attacks on legitimate users
When devices use SIMs for connectivity, the cost is billed to the SIM card inside them. When a device (for example, a robot, a phone, an IoT traffic light, or smart factory equipment) has fraud performed against the SIM or the billing account that it represents, the wireless service provider (aka WSP or the mobile phone company) will detect that fraudulent activity and block the device. If the device is itself a gateway (such as a smart factory small cell gateway), the entire campus network factory that it serves will be blocked. If the fraud is performed across a range of phone numbers representing a fleet of connected or autonomous vehicles, the SIMs of the fleet will then be blocked. Similarly, if the IoT traffic lights of a smart city perform fraud, they will be blocked.
In a similar way, if robots are SIM-enabled and managed by the public telecom network, they will commonly be SIM-configured as “all services active.” This means that the robot and mobile devices can then actually place long distance calls, send SMS, and initiate data sessions. A group of robots (or other mobile devices) can also make coordinated attacks on other mobile devices. A more detailed explanation of this can be found in Trend Micro’s research, “IoT and Satellite Security in the Age of 5G.”
Figure 4. SIM-enabled mobile devices attacking other devices
Figure 5. All services active: Attackers can abuse a device to push traffic across a fake carrier in a portable container, manipulate the traffic, and push it out across another network type. Since one network can’t see another’s traffic, neither of the networks can tell that the signal has been altered.
Recommendations that telcos or IT teams can request their provider for:
- Federation with finance for anti-fraud rules. One way that attacks might be detected in the long term (weeks) is by harmoniously unifying network logs with financial information. Billings should be expected at a certain amount from a certain place, and anything else will generate an alert.
- Velocity checks or “impossible travel.” The geolocation of SIMs and IP addresses can be mapped to the earth. Access from two locations in a short period when those locations are thousands of kilometers apart is a clear indication of fraud. This is also called “impossible travel” since the access could be (for instance) 10 minutes apart, yet 1000 km apart, indicating a speed of 100 km per minute between each access. No normal subscriber would do this, so it is safe to assume that abuse has occurred.
- Fraud Management System (FMS): An FMS will detect patterns from events that are considered traditionally fraudulent activities. If the FMS has enough access to harmonious, federated logs, many fraudulent activities will be detected simply by following patterns of abuse that have been used by people for thousands of years.
Calling Line ID Spoofing
When in a resort hotel, it is often convenient to order room service, which involves identifying a room number as equivalent to a person, and therefore to their respective billable account.
In telecom, this “room number” is the phone number. Just as a person can ask that food be sent to an incorrect room — either by accident or with malicious intent — a person can send traffic to an incorrect phone number. One way is to fake the phone number that shows up on the devices’ call display, the calling line ID (CLID).
CLID spoofing is a legitimate standards-based activity used for many legitimate purposes. This can include masking the individual desks of a call center behind a 1-800 number, for instance. It can also be abused to mask a criminal.
Attacks that use CLID or calling number spoofing work similarly to spoofing the source IP address when firewall security policies are IP-based. At the same time, the level of trust to a known phone number is higher since, for many years, this was promoted as a good security practice by financial institutions, government authorities, and telecommunications companies themselves. Such recommendations often include phrases like “Verify that the text or voicemail is coming from a known phone number.” While verifications like these are definitely good, these are not enough, for which there are several reasons:
- Attacks that deploy carrier-line ID spoofing have been happening in the wild for years.
- Services that implement those attacks are now available to cybercriminals and sold in underground forums at very low costs, starting from US$10.
- The current state of technology gives opportunities to initiate attacks at scale since the process is already automated. Telegram bots that are capable of spoofing caller IDs and voice modification (or are capable of putting these up to scale) are present in this market.
There are many attack scenarios that break this trust mechanism, and these scenarios have been used for decades. Majority of those attacks are often related to the impersonation of well-known numbers that belong to organizations. As an example of this action, customers can receive SMS or calls from a number that belongs to a bank. The SMS or the call will include some actions that a client is expected to take due to a particular “reason.” However, those actions will lead to a phishing site, where the customer might unintentionally share their credentials with an attacker. In other cases, the actions will lead to the fraud committed against those customers. Similar attack scenarios can be implemented by an attacker wherein calls appear to originate from a number that is trusted by an organization. This scenario is feasible in government-to-government or government-to-business interactions.
Attackers also often impersonate the phones of government authorities and law-enforcement bodies as part of scam operations. There are also opposite scenarios where the phone number of a customer is used as an authenticator during calls to organizations. Many banks that use phone-based transaction authentication, as well as retailers and online shops with loyalty programs, are capable of transparently identifying their customers during incoming calls. However, this trust is also exploited by attackers to impersonate or take over customer accounts.
Spoofing of a source phone number is an important part of large-scale fraud, where actors use their unique skills to persuade, change, and influence targeted audiences. When it is necessary to convince a target to receive a call, it can be made to appear that the call originates from a phone that belongs to a high-profile person (like a politician or a company executive). The most innocent scenario of this attack would involve high-ranking public officials receiving calls from numbers that they identify as belonging to other officials, but are actually made by phone prankers.
For ordinary people, attack scenarios can include requests by SMS from someone they know (such as a close relative) asking them to transfer money. The context is that the money is urgently needed to handle an emergency. The text message involved then contains a link to a particular e-wallet linked to another phone.
There are also many industrial routers that provide an “SMS backup channel” to reset a device and set critical parameters when the LTE data link becomes unavailable. The channel is either limited to “trusted phone numbers,” or does not require an SMS from trusted phone numbers to provide a password. CLID spoofing, however, could break the security mechanism of these industrial devices.
Examples:
Australia’s Cyber Security Center (ACSC) released an alert in November 2020 to warn users of scammers impersonating government agencies and requesting access to computers or requesting to purchase specific items.
Meanwhile, the Portland Police Bureau also warned the community of an ongoing police scam fraud with callers impersonating law enforcement officers asking for money to avoid imprisonment or a warrant for their arrest.
In July 2020, Singapore’s Ministry of Law warned citizens of scammers either impersonating officers or using automated messages saying that the ministry could not locate a citizen and that they are being called to pick up documents or parcels.
Recommendations that telcos or IT teams can request their provider for:
It is important to understand that originating phone numbers can be easily spoofed at low costs and that this attack can be implemented at scale. This means that it is still necessary to double-check the origin of incoming calls and text messages, but only as a part of well-defined and multilayered defense strategy. At the technical level, mitigation strategies for these attacks can be significantly improved by empowering existing processes with data from telecom logs that are related to the origin of an SMS or a call.
TDoS Extortion
When visiting the Islands of Telecom on vacation and away from mainland IT, tourists hope that the “weather” will be nice. However, just like mainland IT, the Islands of Telecom sometimes have bad weather. When this happens, some of the activities that tourists want to do and places that they want to visit might be unavailable — this is what happens during a DoS in telecom, or during a telephony DoS (aka TDoS).
The core concept of DoS can be done in many ways beyond the traditional “lots of traffic thrown at X” volumetric or quantitative model. A qualitative DoS is one in which the service is “turned off” for the user, and could involve very little traffic volume, unlike a volumetric DoS. A means of performing this qualitative DoS involves the criminal abuse of existing business processes for managing fraud. Since telcos are compelled to pay for fraud themselves, they will detect and block phone numbers and SIM cards tracked as originating detectable fraud. By blocking the source of fraud, the telco performs a TDoS against the criminal’s victim. This approach to DoS can be thought of as a “black flag,” wherein fraud is done expressly for the purpose of having a secondary person (or company) being caught and blocked.
If the fraud being done from the SIM and phone number is within the range of the intended DoS victim, the victim will look like a fraudster to the telco. The victim or fraudster will then be caught and blocked, resulting in the DoS of all the phone calls and data connectivity. At this point, the victim looks like a fraudster and will be treated as highly suspicious from then on; this means that getting the account or SIM unblocked will be difficult. As fraudsters make calls to telco call centers to get the victim’s services restored (allowing the fraud to continue), it becomes difficult for the telco to tell the difference between true victims and fake victims. During a black flag fraud, this is exploited to prolong the outage.
In addition, since outages of this type might involve someone having to get in a car, a boat, or even a plane to physically travel to a telco service office and personally request the reconnection of services (it is important to remember that the victim might have no connectivity or ability to place a phone call), the black flag fraud is useful for extortion as well.
This extortion can involve either the false assertion that the attacker can restore services (even though they cannot), or the true assertion that they can stop doing the attack repeatedly. It is important to note that the more times the attack occurs, the less likely the victim can have their legitimate services restored. Paying the extortionist therefore becomes more attractive the longer the outage and the more times it is performed.
Examples:
- One type of crime is called international revenue sharing fraud (IRSF)
A series of fraudulent telecom activities were performed against a number of islands in the Pacific. Since the customer base in the area is too low to cost-justify running expensive submarine telecom cables across the bottom of the ocean, the islands use expensive satellite connectivity instead.
The attacker performed fraud across the satellite link’s phone number range, meaning that the satellite and the islands beneath it were denied services when the serving telco detected and blocked the criminal abuse. This attack was repeated several times, with the outage being prolonged each time due to the loss of trust resulting from the repeated fraud losses by the telco.
Portions of the Pacific Islands have also been blocked as the result of the fraud. When denied services due to being victimized by fraud (and as a result of the islands being geographically separated), individuals had to travel to the mainland to have connectivity restored each time. This class of attack would work equally well against cruise ships, remote mineral mines, and remote towns and villages. In the near future, this will have a special effect on autonomous vehicles and drones, which might not have a co-located person to fix the situation.
Extortion is an obvious extension of this class of abuse since the effect of the attack becomes more and more severe when either repeated or prolonged. More details on telecom fraud can be found here.
Figure 6. Coverage of the Pacific Islands Telecommunications Association (PITA) caught in a series of telecom frauds. Map courtesy of PITA.
Recommendations that telcos or IT teams can request their provider for:
Organizations or users can build a strong relationship with their telecom’s internal sales account executive so that they can bypass customer service and the inevitable anti-fraud conversations on their behalf to get connectivity services restored. The salesperson will be motivated to help since they might receive commission based on the revenue generated from them as a customer. Note, however, that the telco might have some liability over the fraud cost of restoring service. As a customer, they can leverage the gap between these two processes to get services restored, but only if the relationship with the account executive is strong enough to have them “do someone a favor.”
Of course, to contact the salesperson, the telco will need an alternative means of communication, the appropriate contact information, and the ability to keep the relationship up-to-date if the contact is moved to another account and replaced with another representative.
Whaling by SIM-jacking
When visiting the Islands of Telecom, tourists will want to see the sights and do activities, including whale watching. Just as in IT, whales are “big fish” and considered especially important people in telecom.
VIPs include people with special resources, access, or power. They include executives like CEOs, journalists, celebrities, and influencers such as professional athletes, actors, and social media stars. Whales can also include very specific people who might not consider themselves important but who have very significant resources such as valuable information or the ability to authorize large payments.
“Whaling” comes from the term “phishing” but deals with much “bigger” phish (that is, whales or VIPs). When a criminal performs whaling, there are a number of techniques, such as business email compromise (BEC), that are convenient for attackers but that are also increasingly being blocked by email filters. Another approach is the collection of attacks variously known as SIM hijacking, SIM swapping, wireless number porting, or simply SIM-jacking.
SIM-jacking is a high-impact attack in that it redirects the cellphone traffic of the whale to the attacker. At that point, the attacker can originate voice calls or messages to other employees (for example, to authorize large amounts for bank transfers). The attacker can also intercept SMS-based MFA codes.
When a whaling attack uses SIM-jacking, the most convenient method for the criminal to use is social engineering. There are multiple points of attack and multiple people whose access can be exploited: people with control over SIM traffic, provisioning, customer service, and tech support can all be valid points of attack for social engineering a criminal’s access to perform SIM-jacking. One valid point can also be social-engineered as part of a penetration in which the others are SIM-jacked to gain control of their ability to further SIM-jack the entire customer base.
Examples:
The places (and therefore the people in it) that an attacker might choose to enter in an organization to perform whaling include:
A self-management website. Traditional IT vulnerabilities in a subscriber self-management website or in a customer management application allow the addition of another subscriber (the criminal). Once added, the criminal can reset the password, preventing non-criminal subscribers from undoing the account hijack of the SIM.
A user profile and a user management interface. User profile is the means of controlling the capabilities and privileges of a group of SIM cards. Call routing and user management are also very powerful in the control of SIM behaviors. Controlling these behaviors allows control of one or more SIMs and functions as SIM-jacking for all the SIMs affected.
A SIM card subscription management interface. Telecom business analysts, sales people, and other staff members have the ability to take action on behalf of a customer. When social-engineered or hacked, an employee can take powerful actions on behalf of an attacker instead.
Recommendations that telcos or IT teams can request their provider for:
This attack requires several elements to detect or prevent it. Missing one or more will allow an attacker to continue the attack with only small inconveniences. The elements are the following:
- Move to a non-SMS means of MFA such as an authenticator app (like Duo).
- Employ a federated IAM system, wherein there is a harmoniously united set of logs and identifiers for identity and access management.
- Treat all accounts with the ability to manipulate SIM accounts as both privileged and powerful. This might require rethinking IAM controls over customer service, tech support accounts, and retail onboarding accounts, among others.
- Implement a zero trust architecture to prevent lateral movement between account roles and between traditional IT accounts and SIM management accounts as well.
The integration of telecommunications infrastructure for almost all critical verticals has been an ongoing trend, further reinforced by the opportunities that were brought about by 5G to organizations. This integration is expected to become further intertwined with the plans for and onset of 6G. From a financial perspective, in particular, it will become nearly impossible to avoid such integration. In deploying these new technologies to existing processes, however, governments and businesses can open and enable even more capabilities but at the same time change the attack surface for these organizations.
As a result, IT teams will need to become aware of the telecom risks to IT assets. Telecommunications concepts, vocabulary, and equipment are very different from those of IT, and therefore will require different skills, training, and mastery. While most IT security standards provide a list of recommendations, most of the time they advise “contacting your provider” (such as an internet service or a mobile telco provider) when these services don’t work. In contrast, security and IT teams can find the incident escalation paths well in advance of telecom incidents involving IT to reduce incident response times.
In this report, we used typical IT, OT, and InfoSec terms and concepts to illustrate how important it is to adjust security risks when organizations initiate integration with telecom. The innovation and cost-saving measures driven by competitive market pressure around 5G, automation, security, and fraud reduction are expected to continue in 6G, as we see unity between industries and verticals that were traditionally separate. New dependencies and vulnerabilities will therefore emerge from cost-saving unities (examples of these unities include those observed with banking, telecom, and power utilities). Furthermore, the dynamic complexity of these networks, when intertwined, will force the changing relationships of vendors and third parties as well. One example is the granted access to enterprise crown jewels for functions to potentially become unaccountable and unlogged.
Security technologies such as Trend MicroTM Mobile Network Security have been evolving simultaneously in response to these changes. Notably, risks and solutions can be different depending on the critical assets’ differences, like electronic government functions, smart factories, smart cities, financial payment systems, autonomous vehicles, and drones. One way to approach these varying risks is through unity in security logging, which would allow for visibility and granular logging to be fed into advanced systems for security baselining.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Cellular IoT Vulnerabilities: Another Door to Cellular Networks
- UNWIRED: Understanding the Unforeseen Risks in Evolving Communication Channels
- Open RAN: Attack of the xApps
- Krytyczna skalowalność: Prognozy Trend Micro dotyczące bezpieczeństwa na rok 2024
- Trend Micro Security Predictions for 2024: Critical Scalability

 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks