The Click Fraud Malware: How MIUREF Turns Users into Cybercriminal Accomplices
Publish date: 2014年2月27日
Click fraud is but one of the cybercriminal’s more insidious ways of earning ill-gotten revenue. But what is it, really? And how does MIUREF, a malware family that recently rose in infection counts during early January 2014 inflict it upon users? Read on to find out all the answers, and how users can prevent themselves from becoming an accessory to this roguish cybercriminal scheme.
What is Click Fraud?
Click fraud is a type of fraud where a person or automated software (typically malware) imitates the action of a legitimate user clicking on a web browser advertisement. The purpose of this is to generate ‘clicks’ for that advertisement even though there is no interest in the advertisement itself.
The main beneficiary of this particular type of fraud are ad agencies, or those behind the advertisement’s posting – as they generally charge by the amount of times an advertisement is clicked.
However, cybercriminals can profit through these, either as a hired party by the ad agencies themselves, or by using the malware involved to spread even more damaging malware.
What is MIUREF?
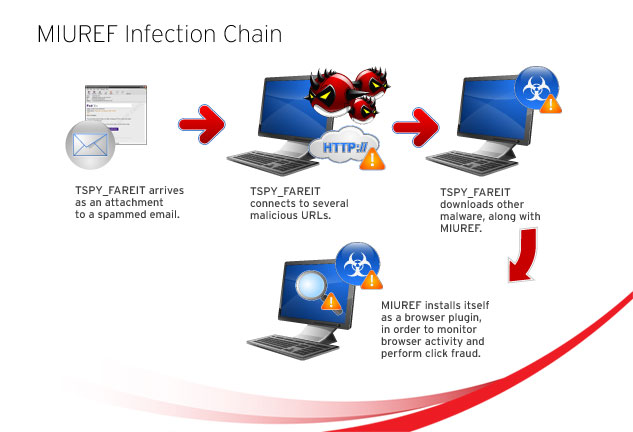
MIUREF is a Trojan that facilitates click fraud. Discovered on November 2013, it was recently detected to affect a number of countries, with the most affected being the United States, Japan, France and Australia. The infections were detected during the period of January 1, 2014 to February 17, 2014.
It installs itself as a browser plugin to hide itself from detection as well as ensure that it loads itself every time the system’s internet browser is executed.
MIUREF is also known to be used as additional payload of other malware. The most recent variants detected have been spotted to be a downloaded payload of the malware family TSPY_FAREIT.
It should be noted that click fraud is only one of MIUREF’s possible malicious purposes.
How does MIUREF get into systems?
MIUREF can enter a system in various ways:
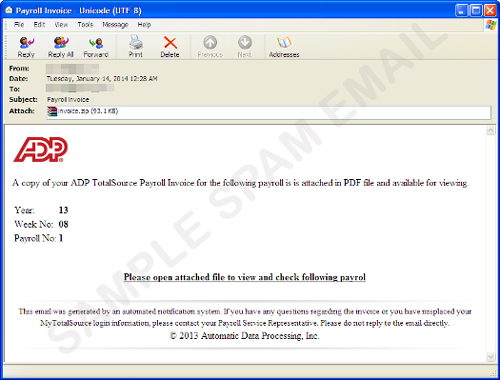
- As an attachment in spam mails (sample below):
- As a file downloaded voluntarily downloaded from the internet(disguised as a an application cracker)
- A file downloaded by other malware
- As a file downloaded through Java vulnerability exploits.
Based on the reported infections as of January 2014, the most common arrival method for MIUREF is currently through spammed mails.
What is MIUREF’s malicious routines?
MIUREF’s malicious routines mainly facilitate click fraud. Once it successfully infiltrates a system, it installs itself as a browser plugin to monitor browser activities, display pop-up ads as well as execute malicious scripts. It also redirects users to possibly malicious websites whenever users attempt to click on search engine results, such as when searching for products or services they plan on purchasing.
How does MIUREF affect users?
MIUREF as a threat does not affect users directly – it only turns them and their systems as accessories for click fraud. However, the fact remains that it is very possible for the cybercriminal to turn MIUREF’s click-fraud activity into one that facilitates more malicious routines.
For example, the ad that MIUREF performs the click fraud on may be a malicious ad that instantly downloads malware onto the user’s system.
The malicious ad could also lead to a scam site, where the user is tricked into buying/paying money for a service or product that they may never receive.
MIUREF’s browser activity tracking could also lead to the user’s privacy being violated.
We must note that while the above scenarios have not happened yet, the fact remains that they are indeed possible.
Why is this threat notable?
Click fraud as a threat may be dismissed or underestimated by users due to it not affecting them directly as other threats would. As such, it could leave users vulnerable to the complications that may arise should MIUREF’s routines begin to feature much more malicious ones, such as the following:
- Information theft
- Identity theft/fraud
- Privacy loss due to browser activity tracking
- Compromise of system security
Are Trend Micro users protected from this threat?
Trend Micro protects users from this threat by detecting the related email messages from the user’s email inboxes via email reputation services. The malware is also detected and deleted if found in the system via file reputation services, while web reputation services blocks access to the domains where MIUREF variants connect to.
What can users do to prevent these threats from affecting their computers?
With MIUREF’s most common method of arrival being through spam attachments, it’s a good idea for users to practice safe email habits, such deleting any suspicious mail received without opening or viewing them, as well as refraining from opening any suspicious attachments and/or links. Users should also take care to avoid looking for illegal workarounds to licensed software, as cybercriminals may disguise malware such as MIUREF as key generators and cracks.
FROM THE FIELD: EXPERT INSIGHTS
"Since MIUREF commonly arrives via spammed mails (mostly financial-related), users should be more aware of incoming mails and treat attachments with suspicion and/or skepticism."
–Rhena Inocencio, Threat Response Engineer