Blackhole Exploit Kit Spam Run Uses Xanga
Publish date: 03 de agosto de 2012

In this blackhole exploit kit spam run, spammers use a legitimate email notification template from Xanga. From the email's content, it lures users into clicking a malicious link. Once the URL is clicked, it redirects to a site hosting a malicious JavaScript.
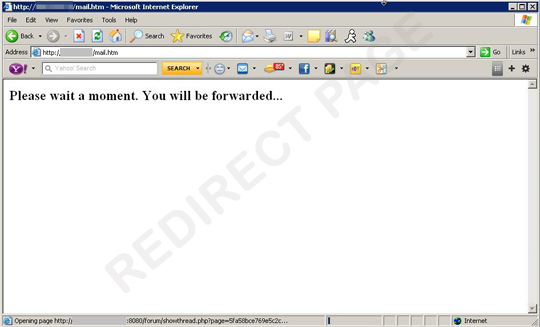
While users patiently wait for the website to load, the script is already pointing them to a blackhole exploit kit server where an exploit code starts to execute to deliver its final payload. A .JAR file is executed, and proceeds to download other malicious files into the victims machine.
Trend Micro™ Smart Protection Network™ protects users from this threat by blocking the spam mail samples, as well as any related malicious URLs and malware.
Fecha/hora de bloqueo del spam: 03 de agosto de 2012 GMT-8
TMASE
- Motor TMASE:6.8
- Patrón TMASE: 9082