Adware.Win32.FusionCore.AD
Downloader.Win32.Funshion.gen (KASPERSKY); Riskware/FusionCore (FORTINET)
Windows


Threat Type: Adware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Adware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites. It may be manually installed by a user.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Adware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It may be manually installed by a user.
Installation
This Adware drops the following files:
- %User Temp%\is-{5 Random Characters}.tmp\{Malware name}.tmp
- %User Temp%\is-{5 Random Characters}.tmp\OqIEFuprtaC.dll
- %User Temp%\is-{5 Random Characters}.tmp\itdownload.dll
- %User Temp%\is-{5 Random Characters}.tmp\isxdl.dll
- %User Temp%\nsd{Random Characters}\csshover3.htc
- %User Temp%\nsd{Random Characters}\css\ie6_main.css
- %User Temp%\nsd{Random Characters}\css\main.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\browse.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\checkbox.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\progress-bar.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\button-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg-corner.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg2.png
- %User Temp%\nsd{Random Characters}\images\Loader.gif
- %User Temp%\nsd{Random Characters}\locale\AF.locale
- %User Temp%\nsd{Random Characters}\locale\AZ.locale
- %User Temp%\nsd{Random Characters}\locale\BE.locale
- %User Temp%\nsd{Random Characters}\locale\BG.locale
- %User Temp%\nsd{Random Characters}\locale\BS.locale
- %User Temp%\nsd{Random Characters}\locale\CA.locale
- %User Temp%\nsd{Random Characters}\locale\CS.locale
- %User Temp%\nsd{Random Characters}\locale\DA.locale
- %User Temp%\nsd{Random Characters}\locale\DE.locale
- %User Temp%\nsd{Random Characters}\locale\EL.locale
- %User Temp%\nsd{Random Characters}\locale\EN.locale
- %User Temp%\nsd{Random Characters}\locale\ES.locale
- %User Temp%\nsd{Random Characters}\locale\ET.locale
- %User Temp%\nsd{Random Characters}\locale\EU.locale
- %User Temp%\nsd{Random Characters}\locale\FA.locale
- %User Temp%\nsd{Random Characters}\locale\FI.locale
- %User Temp%\nsd{Random Characters}\locale\FR.locale
- %User Temp%\nsd{Random Characters}\locale\GU.locale
- %User Temp%\nsd{Random Characters}\locale\HE.locale
- %User Temp%\nsd{Random Characters}\locale\HI.locale
- %User Temp%\nsd{Random Characters}\locale\HR.locale
- %User Temp%\nsd{Random Characters}\locale\HT.locale
- %User Temp%\nsd{Random Characters}\locale\HU.locale
- %User Temp%\nsd{Random Characters}\locale\HY.locale
- %User Temp%\nsd{Random Characters}\locale\ID.locale
- %User Temp%\nsd{Random Characters}\locale\IS.locale
- %User Temp%\nsd{Random Characters}\locale\IT.locale
- %User Temp%\nsd{Random Characters}\locale\JA.locale
- %User Temp%\nsd{Random Characters}\locale\KA.locale
- %User Temp%\nsd{Random Characters}\locale\KK.locale
- %User Temp%\nsd{Random Characters}\locale\KO.locale
- %User Temp%\nsd{Random Characters}\locale\KU.locale
- %User Temp%\nsd{Random Characters}\locale\LO.locale
- %User Temp%\nsd{Random Characters}\locale\LT.locale
- %User Temp%\nsd{Random Characters}\locale\LV.locale
- %User Temp%\nsd{Random Characters}\locale\MK.locale
- %User Temp%\nsd{Random Characters}\locale\ML.locale
- %User Temp%\nsd{Random Characters}\locale\MR.locale
- %User Temp%\nsd{Random Characters}\locale\MS.locale
- %User Temp%\nsd{Random Characters}\locale\NE.locale
- %User Temp%\nsd{Random Characters}\locale\NL.locale
- %User Temp%\nsd{Random Characters}\locale\NO.locale
- %User Temp%\nsd{Random Characters}\locale\PA.locale
- %User Temp%\nsd{Random Characters}\locale\PL.locale
- %User Temp%\nsd{Random Characters}\locale\PT.locale
- %User Temp%\nsd{Random Characters}\locale\RO.locale
- %User Temp%\nsd{Random Characters}\locale\RU.locale
- %User Temp%\nsd{Random Characters}\locale\SK.locale
- %User Temp%\nsd{Random Characters}\locale\SL.locale
- %User Temp%\nsd{Random Characters}\locale\SQ.locale
- %User Temp%\nsd{Random Characters}\locale\SR.locale
- %User Temp%\nsd{Random Characters}\locale\SV.locale
- %User Temp%\nsd{Random Characters}\locale\TA.locale
- %User Temp%\nsd{Random Characters}\locale\TE.locale
- %User Temp%\nsd{Random Characters}\locale\TH.locale
- %User Temp%\nsd{Random Characters}\locale\TL.locale
- %User Temp%\nsd{Random Characters}\locale\TR.locale
- %User Temp%\nsd{Random Characters}\locale\UK.locale
- %User Temp%\nsd{Random Characters}\locale\UR.locale
- %User Temp%\nsd{Random Characters}\locale\UZ.locale
- %User Temp%\nsd{Random Characters}\locale\VI.locale
- %User Temp%\nsd{Random Characters}\locale\YO.locale
- %User Temp%\nsd{Random Characters}\locale\ZH.locale
- %User Temp%\nsd{Random Characters}\locale\ZU.locale
- %User Temp%\ns14AB5EB1\7E72237D.tmp
- %User Temp%\is-{5 Random Characters}.tmp\rkinstaller.exe
- %User Temp%\is-{5 Random Characters}.tmp\rkverify.exe
- %User Temp%\ns14AB5EB1\0BB0D08C_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %Program Files%\PCMate Free EXE Lock\unins000.dat
- %Program Files%\PCMate Free EXE Lock\unins000.exe
- %Program Files%\PCMate Free EXE Lock\goup.exe
- %Program Files%\PCMate Free EXE Lock\version.dat
- %Program Files%\PCMate Free EXE Lock\PCMate Free EXE Lock Update.exe
- %Program Files%\RelevantKnowledge\rlservice.exe
- %Program Files%\PCMate Free EXE Lock\icon.ico
- %Program Files%\PCMate Free EXE Lock\lamecore.dll
- %Program Files%\RelevantKnowledge\rlls.dll
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock on the Web.url
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock.lnk
- %Programs%\PCMate Free EXE Lock\More Free Tools.url
- %Programs%\PCMate Free EXE Lock\Uninstall.lnk
- %Desktop%\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Windows\Start Menu\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Internet Explorer\Quick Launch\PCMate Free EXE Lock.lnk
- %Program Files%\RelevantKnowledge\rlls64.dll
- %Program Files%\RelevantKnowledge\rlvknlg64.exe
- %Program Files%\RelevantKnowledge\rlvknlg32.exe
- %Program Files%\RelevantKnowledge\rlvknlg.exe
- %System%\rlls.dll
- %Application Data%\PCMate Free EXE Lock New Version Available\update.dat
- %Programs%\RelevantKnowledge\Privacy Policy and Terms of Service.lnk
- %Programs%\RelevantKnowledge\About RelevantKnowledge.lnk
- %Programs%\RelevantKnowledge\Support.lnk
- %Programs%\RelevantKnowledge\Uninstall Instructions.lnk
- %Application Data%\PCMate Free EXE Lock New Version Available\PCMateFreeEXELock.exe
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Programs% is the folder that contains the user’s program groups, which is usually C:\Windows\Start Menu\Programs or C:\Documents and Settings\{User name}\Start Menu\Programs on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs on Windows Vista, 7, and 8.. %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Application Data% is the current user's Application Data folder, which is usually C:\Documents and Settings\{user name}\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Roaming on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
It adds the following processes:
- netsh firewall add allowedprogram program = "%Program Files%\relevantknowledge\rlvknlg.exe" name = rlvknlg.exe mode = ENABLE scope = ALL
(Note: %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Autostart Technique
This Adware drops the following file(s) in the Windows User Startup folder to enable its automatic execution at every system startup:
- %User Startup%\PCMate Free EXE Lock Update.lnk
(Note: %User Startup% is the current user's Startup folder, which is usually C:\Windows\Profiles\{user name}\Start Menu\Programs\Startup on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Start Menu\Programs\Startup on Windows NT, C:\Documents and Settings\{User name}\Start Menu\Programs\Startup on Windows 2003(32-bit), XP and 2000(32-bit), or C:\Users\{user name}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit), 10(64-bit).)
Other System Modifications
This Adware adds the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: Setup Version = 5.6.1 (u)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: App Path = %Program Files%\PCMate Free EXE Lock
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
InstallLocation = %Program Files%\PCMate Free EXE Lock\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: Icon Group = PCMate Free EXE Lock
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: User = {Current user}\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: Language = en_1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
DisplayName = PCMate Free EXE Lock 8.8.1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
UninstallString = UninstallString
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
QuietUninstallString = "%Program Files%\PCMate Free EXE Lock\unins000.exe" /SILENT
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Publisher = PCMate Software, Inc.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
URLInfoAbout = http://www.{BLOCKED}ware.com/
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
HelpLink = http://www.{BLOCKED}ware.com/
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
URLUpdateInfo = http://www.{BLOCKED}ware.com/
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
NoModify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
NoRepair = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
InstallDate = {Current Date}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
EstimatedSize = 1159
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_owner = 1
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_hhsize = 3
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_num_child = 2
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_region = AL
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_zip = 123123
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
BundleOfferActionUid =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
UninstallString = %Program Files%\RelevantKnowledge\rlvknlg.exe -bootremove -uninst:RelevantKnowledge
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
DisplayName = RelevantKnowledge
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
Publisher = TMRG, Inc.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
EstimatedSize = 5400
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
DisplayVersion = 1.3.338.311
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Name = x-ns1CnVdsWhT48y,x-ns2EAXCsH$M853
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
HK_Path = %System%\rlls.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
HK64_Path = %System%\rlls64.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
LD64_Path = %Program Files%\RelevantKnowledge\rlvknlg64.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
KS_Path = %Program Files%\RelevantKnowledge\rlls.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
SV_Path = %Program Files%\RelevantKnowledge\rlservice.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
RunLine = %Program Files%\relevantknowledge\rlvknlg.exe –boot
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
ServiceName = RelevantKnowledge
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
OSSProxyPID = 3052
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
SendContentIDToServer = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Capabilities = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
ExtCapabilities = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
OptionsBitmask = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
RevertPath = %Program Files%\RelevantKnowledge\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Installed = 77 47 00 00
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Ipcountry = PH
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
instLanguage = 1033
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
UninstURL = http://www.{BLOCKED}owledge.com/con{BLOCKED}all.aspx?siteid=2600&campaign_id=878
Other Details
This Adware adds the following registry keys:
HKEY_CURRENT_USER\Software\Microsoft\
RestartManager\Session0000
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
HKEY_LOCAL_MACHINE\SOFTWARE\FreeExeLock
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
It connects to the following website to send and receive information:
- rp.{BLOCKED}verseapplication.com
- dpd.{BLOCKED}studies.com
- http://www.{BLOCKED}temsoftware.com/downloadfile/PCMateFreeEXELockFull.exe
- post.{BLOCKED}studies.com
- {BLOCKED}nloadpr.com
It does the following:
- It displays the following during installation:
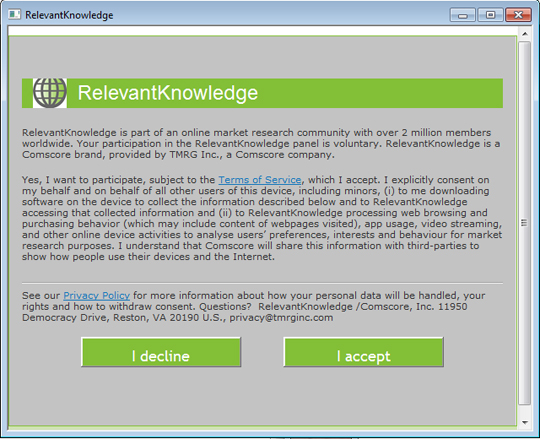
SOLUTION
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Restart in Safe Mode
Step 4
Remove Adware.Win32.FusionCore.AD by using its own Uninstall option
Step 5
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry. Before you could do this, you must restart in Safe Mode. For instructions on how to do this, you may refer to this page If the preceding step requires you to restart in safe mode, you may proceed to edit the system registry.
- In HKEY_CURRENT_USER\Software\Microsoft\RestartManager
- Session0000
- Session0000
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
- PCMate Free EXE Lock_is1
- PCMate Free EXE Lock_is1
- In HKEY_LOCAL_MACHINE\SOFTWARE
- MC_MediaProSoft_DDMP_PP
- MC_MediaProSoft_DDMP_PP
- In HKEY_LOCAL_MACHINE\SOFTWARE
- FreeExeLock
- FreeExeLock
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{d08d9f98-1c78-4704-87e6-368b0023d831}
- Config
- Config
Step 6
Search and delete these files
- %User Temp%\is-{5 Random Characters}.tmp\{Malware name}.tmp
- %User Temp%\is-{5 Random Characters}.tmp\OqIEFuprtaC.dll
- %User Temp%\is-{5 Random Characters}.tmp\itdownload.dll
- %User Temp%\is-{5 Random Characters}.tmp\isxdl.dll
- %User Temp%\nsd{Random Characters}\csshover3.htc
- %User Temp%\nsd{Random Characters}\css\ie6_main.css
- %User Temp%\nsd{Random Characters}\css\main.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\browse.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\checkbox.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\progress-bar.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\button-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg-corner.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg2.png
- %User Temp%\nsd{Random Characters}\images\Loader.gif
- %User Temp%\nsd{Random Characters}\locale\AF.locale
- %User Temp%\nsd{Random Characters}\locale\AZ.locale
- %User Temp%\nsd{Random Characters}\locale\BE.locale
- %User Temp%\nsd{Random Characters}\locale\BG.locale
- %User Temp%\nsd{Random Characters}\locale\BS.locale
- %User Temp%\nsd{Random Characters}\locale\CA.locale
- %User Temp%\nsd{Random Characters}\locale\CS.locale
- %User Temp%\nsd{Random Characters}\locale\DA.locale
- %User Temp%\nsd{Random Characters}\locale\DE.locale
- %User Temp%\nsd{Random Characters}\locale\EL.locale
- %User Temp%\nsd{Random Characters}\locale\EN.locale
- %User Temp%\nsd{Random Characters}\locale\ES.locale
- %User Temp%\nsd{Random Characters}\locale\ET.locale
- %User Temp%\nsd{Random Characters}\locale\EU.locale
- %User Temp%\nsd{Random Characters}\locale\FA.locale
- %User Temp%\nsd{Random Characters}\locale\FI.locale
- %User Temp%\nsd{Random Characters}\locale\FR.locale
- %User Temp%\nsd{Random Characters}\locale\GU.locale
- %User Temp%\nsd{Random Characters}\locale\HE.locale
- %User Temp%\nsd{Random Characters}\locale\HI.locale
- %User Temp%\nsd{Random Characters}\locale\HR.locale
- %User Temp%\nsd{Random Characters}\locale\HT.locale
- %User Temp%\nsd{Random Characters}\locale\HU.locale
- %User Temp%\nsd{Random Characters}\locale\HY.locale
- %User Temp%\nsd{Random Characters}\locale\ID.locale
- %User Temp%\nsd{Random Characters}\locale\IS.locale
- %User Temp%\nsd{Random Characters}\locale\IT.locale
- %User Temp%\nsd{Random Characters}\locale\JA.locale
- %User Temp%\nsd{Random Characters}\locale\KA.locale
- %User Temp%\nsd{Random Characters}\locale\KK.locale
- %User Temp%\nsd{Random Characters}\locale\KO.locale
- %User Temp%\nsd{Random Characters}\locale\KU.locale
- %User Temp%\nsd{Random Characters}\locale\LO.locale
- %User Temp%\nsd{Random Characters}\locale\LT.locale
- %User Temp%\nsd{Random Characters}\locale\LV.locale
- %User Temp%\nsd{Random Characters}\locale\MK.locale
- %User Temp%\nsd{Random Characters}\locale\ML.locale
- %User Temp%\nsd{Random Characters}\locale\MR.locale
- %User Temp%\nsd{Random Characters}\locale\MS.locale
- %User Temp%\nsd{Random Characters}\locale\NE.locale
- %User Temp%\nsd{Random Characters}\locale\NL.locale
- %User Temp%\nsd{Random Characters}\locale\NO.locale
- %User Temp%\nsd{Random Characters}\locale\PA.locale
- %User Temp%\nsd{Random Characters}\locale\PL.locale
- %User Temp%\nsd{Random Characters}\locale\PT.locale
- %User Temp%\nsd{Random Characters}\locale\RO.locale
- %User Temp%\nsd{Random Characters}\locale\RU.locale
- %User Temp%\nsd{Random Characters}\locale\SK.locale
- %User Temp%\nsd{Random Characters}\locale\SL.locale
- %User Temp%\nsd{Random Characters}\locale\SQ.locale
- %User Temp%\nsd{Random Characters}\locale\SR.locale
- %User Temp%\nsd{Random Characters}\locale\SV.locale
- %User Temp%\nsd{Random Characters}\locale\TA.locale
- %User Temp%\nsd{Random Characters}\locale\TE.locale
- %User Temp%\nsd{Random Characters}\locale\TH.locale
- %User Temp%\nsd{Random Characters}\locale\TL.locale
- %User Temp%\nsd{Random Characters}\locale\TR.locale
- %User Temp%\nsd{Random Characters}\locale\UK.locale
- %User Temp%\nsd{Random Characters}\locale\UR.locale
- %User Temp%\nsd{Random Characters}\locale\UZ.locale
- %User Temp%\nsd{Random Characters}\locale\VI.locale
- %User Temp%\nsd{Random Characters}\locale\YO.locale
- %User Temp%\nsd{Random Characters}\locale\ZH.locale
- %User Temp%\nsd{Random Characters}\locale\ZU.locale
- %User Temp%\ns14AB5EB1\7E72237D.tmp
- %User Temp%\is-{5 Random Characters}.tmp\rkinstaller.exe
- %User Temp%\is-{5 Random Characters}.tmp\rkverify.exe
- %User Temp%\ns14AB5EB1\0BB0D08C_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %Program Files%\PCMate Free EXE Lock\unins000.dat
- %Program Files%\PCMate Free EXE Lock\unins000.exe
- %Program Files%\PCMate Free EXE Lock\goup.exe
- %Program Files%\PCMate Free EXE Lock\version.dat
- %Program Files%\PCMate Free EXE Lock\PCMate Free EXE Lock Update.exe
- %Program Files%\RelevantKnowledge\rlservice.exe
- %Program Files%\PCMate Free EXE Lock\icon.ico
- %Program Files%\PCMate Free EXE Lock\lamecore.dll
- %Program Files%\RelevantKnowledge\rlls.dll
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock on the Web.url
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock.lnk
- %Programs%\PCMate Free EXE Lock\More Free Tools.url
- %Programs%\PCMate Free EXE Lock\Uninstall.lnk
- %Desktop%\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Windows\Start Menu\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Internet Explorer\Quick Launch\PCMate Free EXE Lock.lnk
- %Program Files%\RelevantKnowledge\rlls64.dll
- %Program Files%\RelevantKnowledge\rlvknlg64.exe
- %Program Files%\RelevantKnowledge\rlvknlg32.exe
- %Program Files%\RelevantKnowledge\rlvknlg.exe
- %System%\rlls.dll
- %Application Data%\PCMate Free EXE Lock New Version Available\update.dat
- %Programs%\RelevantKnowledge\Privacy Policy and Terms of Service.lnk
- %Programs%\RelevantKnowledge\About RelevantKnowledge.lnk
- %Programs%\RelevantKnowledge\Support.lnk
- %Programs%\RelevantKnowledge\Uninstall Instructions.lnk
- %Application Data%\PCMate Free EXE Lock New Version Available\PCMateFreeEXELock.exe
Step 7
Restart in normal mode and scan your computer with your Trend Micro product for files detected as Adware.Win32.FusionCore.AD. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


