Mobile Safety
 As threats to mobile devices increase, developing good security habits becomes even more important. In this article, we detail current mobile threats and provide tips on how to secure mobile devices.
As threats to mobile devices increase, developing good security habits becomes even more important. In this article, we detail current mobile threats and provide tips on how to secure mobile devices.  Click fraud apps pushed a 100 percent year-over-year increase in malware installed from Google Play in 2018.
Click fraud apps pushed a 100 percent year-over-year increase in malware installed from Google Play in 2018. This research paper provides in-depth information on the operation and structure of a cybercriminal group found using fake banking apps to steal mobile banking credentials from South Korean users.
This research paper provides in-depth information on the operation and structure of a cybercriminal group found using fake banking apps to steal mobile banking credentials from South Korean users.  Sextortion operations aren't new, but a new modus operandi that makes use of malware and mobile devices is emerging in East Asia. This research paper offers an in-depth look at the operation, its perpetrators, as well as their tools and methods.
Sextortion operations aren't new, but a new modus operandi that makes use of malware and mobile devices is emerging in East Asia. This research paper offers an in-depth look at the operation, its perpetrators, as well as their tools and methods.  Don't assume that iOS is safe from malware and attacks. Previous incidents have proven that it's not as safe as you thought. Here are a few ways to tighten up security on your iOS device.
Don't assume that iOS is safe from malware and attacks. Previous incidents have proven that it's not as safe as you thought. Here are a few ways to tighten up security on your iOS device.  There are privacy and security risks involved in connecting to public or 'free' Wi-fi hotspots. Here's a 4-step guide to setting up a virtual private network (VPN) for the times when you have to connect to unfamiliar networks.
There are privacy and security risks involved in connecting to public or 'free' Wi-fi hotspots. Here's a 4-step guide to setting up a virtual private network (VPN) for the times when you have to connect to unfamiliar networks.  To maximize the benefits of BYOD without increasing the risks, companies and their employees need to strike a balance between maintaining employee privacy and having control over corporate data on devices.
To maximize the benefits of BYOD without increasing the risks, companies and their employees need to strike a balance between maintaining employee privacy and having control over corporate data on devices. 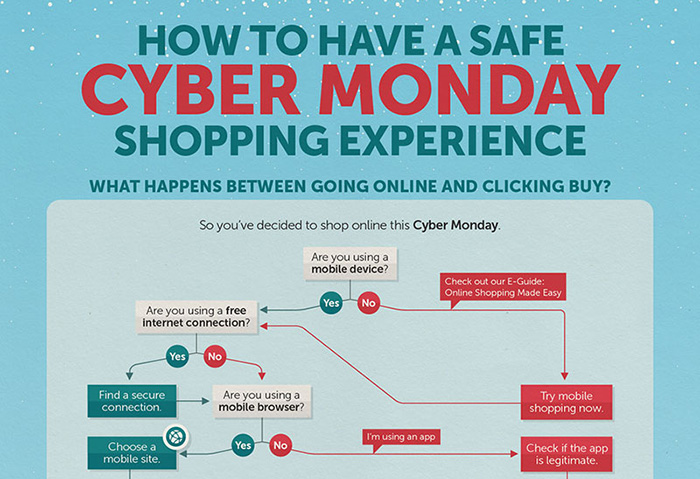 With Cyber Monday sales expected to rake in another record in most online sales in a day, threats are swooping in where people are most available and vulnerable. Secure your mobile shopping by following this flowchart.
With Cyber Monday sales expected to rake in another record in most online sales in a day, threats are swooping in where people are most available and vulnerable. Secure your mobile shopping by following this flowchart.