WannaCry/Wcry Ransomware: What Your IT/Sysadmins Need to Do
 WannaCry/
WannaCry/
If your system was in sleep mode during WannaCry’s attacks last weekend, there’s a good chance that your machine escaped WannaCry’s slew of attacks last weekend. But what happens when you wake the system up? The short answer: the kill switch will still prevent the ransomware’s encryption routine. This is a window of opportunity IT/system administrators and information security (InfoSec) professionals can take advantage of to patch or update vulnerable systems, preventing threats like WannaCry from affecting them in the future.
Here are actionable things you can do to check if your systems and networks were affected by the ransomware’s attacks during the weekend.
[READ: Latest update on Trend Micro’s protections for WannaCry ransomware]
Machines in sleep mode will not be infected, so patch them immediately.

Based on Trend Micro’s analysis and simulations of WannaCry, the ransomware attack will not be successful if the machines are in sleep mode—even with Transmission Control Protocol (TCP) port 445 open and unpatched.
Part of WannaCry ransomware’s attack chain involves connecting to and infecting more systems. If it tries to connect to a machine in sleep mode, it will receive a “socket error” and fail to access it. Consequently, the malware will move to the next IP and attempt to access machines connected to it.
This presents a window of opportunity for the IT/system administrators to mitigate, if not prevent a WannaCry infection by immediately patching the vulnerability that the ransomware leverages to infect systems.
[From the Security Intelligence Blog: A technical overview of the WannaCry/
What happens when you “wake up” the machine?
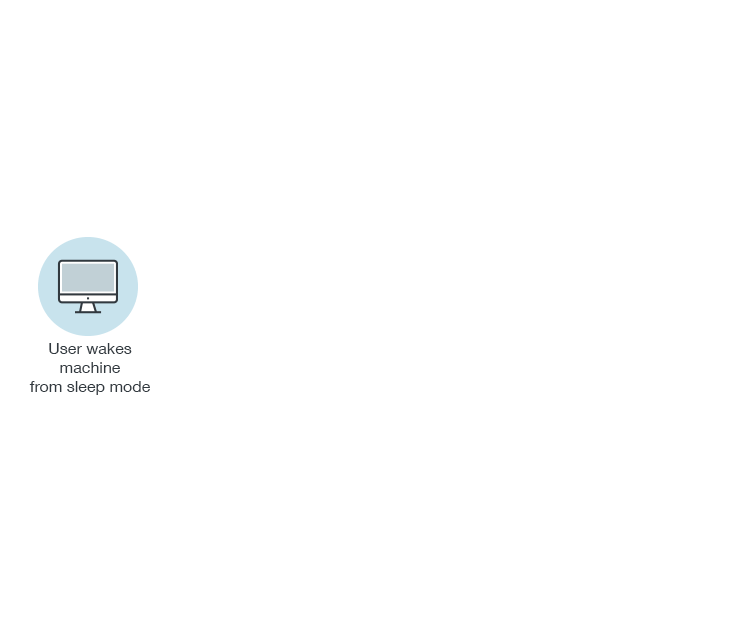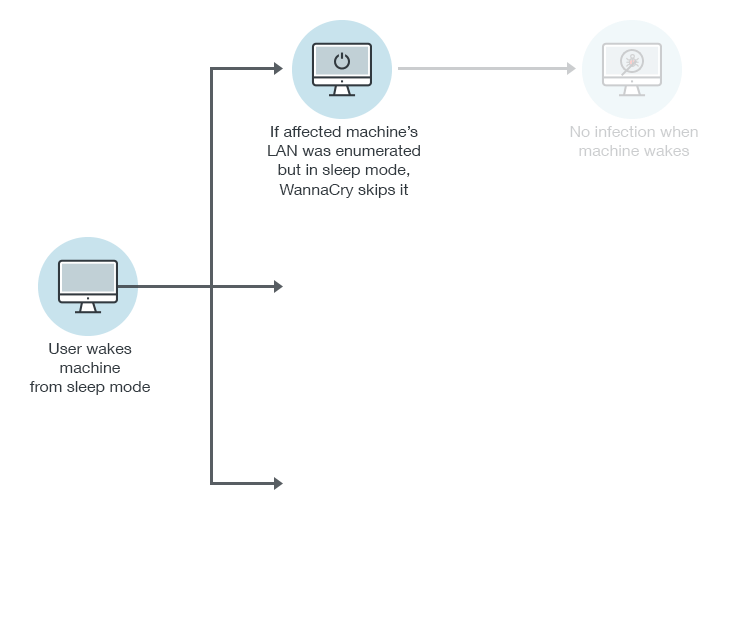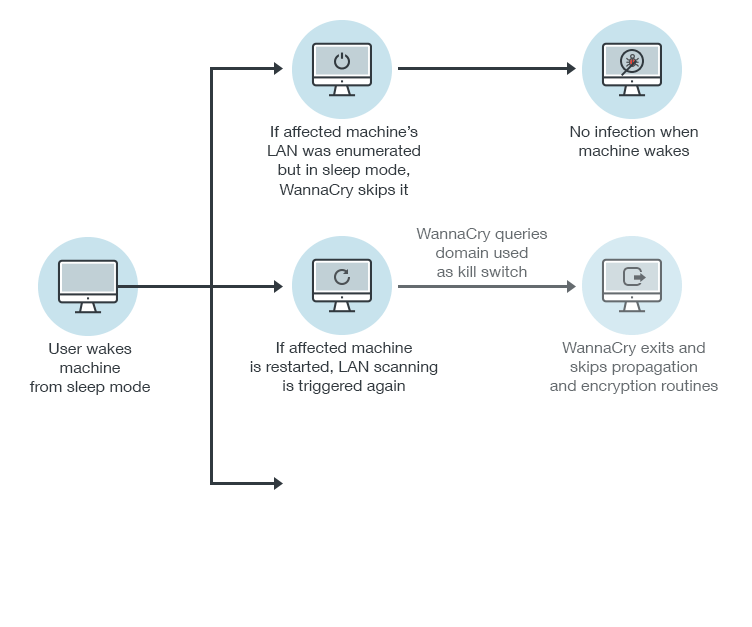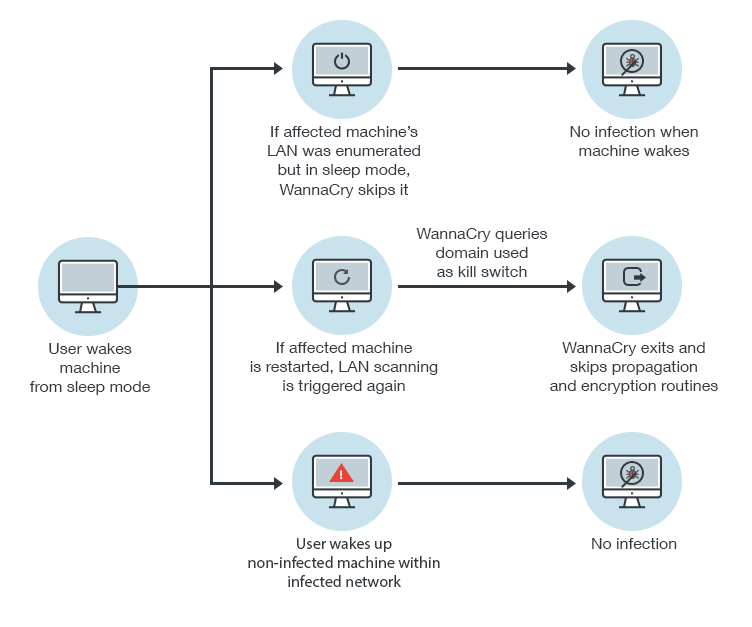
WannaCry scans the system’s Local Area Network (LAN) upon initial infection and
Restarting the initially infected machine, however, will prompt the LAN scanning routine again. Fortunately, WannaCry has a “kill switch”. Part of WannaCry’s infection routine involves sending a request that checks for a live URL/domain. If its request returns showing that the URL is alive or online, it will activate the kill switch, prompting WannaCry to
This shouldn’t be taken for granted, however. This can serve as either a window of
[READ: Multilayered solutions and defense against WannaCry/
What if WannaCry is already in the system?

What happens if the machine is already infected? If mssecvc.exe, one of WannaCry’s components, is already in the system, the kill switch—as long as it is there—will prevent WannaCry’s encrypting component from being dropped in the vulnerable machine. IT/system administrators and InfoSec professionals can still do the necessary incident response and remediation tasks—updating and patching the system in particular.
[READ: WannaCry and the reality of patching]
Patch your systems and implement best practices.
WannaCry underscores the importance of keeping systems and networks regularly patched and updated. Threats like WannaCry abuse vulnerabilities to penetrate security gaps in an organization’s perimeter. This is compounded by the window of exposure between exploitation and the release of a patch; the longer your systems and networks remain vulnerable, the more time it gives attackers to exploit it. Organizations must balance the need to maintain business operations with the need to secure them.
Indeed, keeping attackers at bay is always a race against time for many enterprises. A defense-in-depth approach combining proactive security mechanisms, robust IT policies, and strong security posture in the workplace can help deter threats like WannaCry.
Trend Micro Ransomware Solutions
Enterprises should use a multi-layered approach to mitigate the risks brought threats like ransomware.
Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security can prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–regardless if they’re physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Find more in-depth information on Trend Micro detections and solutions for Trend Micro Deep Security, Vulnerability Protection, TippingPoint, Deep Discovery Inspector, and Trend Micro Home Network Security in this technical support page.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks