Turning Your Data Against You: Cybercrime’s New Norm?
 Data analysis helps uncover patterns, correlations, and other valuable information that can aid businesses and decision makers. In cybersecurity, data analysis also plays an increasingly crucial role in detecting threats. But what if data analysis is used to perpetrate cybercrime?
Data analysis helps uncover patterns, correlations, and other valuable information that can aid businesses and decision makers. In cybersecurity, data analysis also plays an increasingly crucial role in detecting threats. But what if data analysis is used to perpetrate cybercrime?
In late August this year, a French researcher uncovered a large-scale and publicly accessible spambot named Onliner that used an estimated 80 million compromised email servers to distribute spam, fingerprint potential victims, and infect them with the information-stealing URSNIF malware. Onliner used 711 million accounts in total, amassed from previous data breaches such as the LinkedIn breach.
[From TrendLabs Security Intelligence Blog: New Malicious Macro Evasion Tactics Exposed in URSNIF Spam Mail]
Data is the currency in today’s technology-driven world, and Onliner demonstrated how profitable it is for bad guys. Perhaps the ever-significant value of data is also what's driving the extent and increased sophistication of cyberattacks. In the past, cybercriminals made off with relatively small amounts of data that they reuse for their own modest benefit, like committing identity theft.
Nowadays, cybercriminals are going after bigger data—possibly to cast a wider net and consequently turn in more profit—and using more resources to steal them. The newer the technology is for processing, managing, and storing data, the more attractive it is for cybercriminals to hack and exploit.
The sheer volume and variety of data that enterprises (and end users) create, manage, and store—along with the speed with which they change hands—makes them ideal targets for data theft. Cybercriminals and threat actors, in turn, can repurpose this data or resell them in the underground.
[READ: What do Hackers do with Your Stolen Identity?]
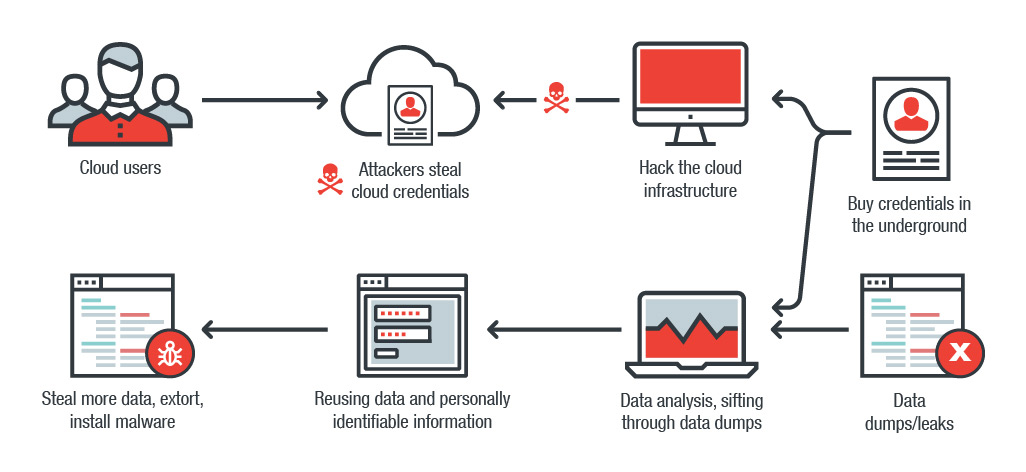
How data is reused to perpetrate online extortion
Using your data against you
How exactly can data be repurposed for cybercrime? The scenario isn’t exactly new, but it's certainly becoming more prevalent: a cybercriminal either steals credentials stored in the cloud or exploits a vulnerability to hack into repositories that store them. The alternatives? Buy them in the underground or salvage dumps of publicly leaked data, then sift through and isolate valuable data, such as credentials or other personally identifiable information.
These credentials are ultimately employed to laterally move within the network to steal more data, hold them hostage through encryption, or infect the infrastructure these credentials are tied to with malware.
[READ: How exposed mainframes can result in business process compromise]
In June 2016, the accounts and personal details compromised in the 2012 LinkedIn data breach were reused to fabricate legitimate-looking phishing emails. They came with a Word document embedded with malicious macro code that retrieved and ran the ZeuS Panda banking Trojan. HDDCryptor, a Master Boot Record-overwriting ransomware that affected the San Francisco Municipal Transportation Agency in 2016, was believed to have been executed using exposed/unsecured remote desktops, given how it’s easy to buy credentials to compromised servers in the underground.
Business process compromise attacks the enterprise’s internal infrastructure for cybercriminal profit
Misusing data this way isn’t just limited to large-scale, spray-and-pray campaigns. In fact, the theft, purchase, and harvest of certain credentials are more of an end-to-end strategy. This means cybercriminals and threat actors can be especially purposeful when choosing victims to attack. In October 2017, customer banking credentials, amassed via phishing campaigns, were reused to distribute spear phishing emails to the targeted bank’s employees that installed a backdoor into the bank’s systems and networks.
[READ: The General Data Protection Regulation (GDPR) highlights privacy in the digital age]
The internet of things is also in the crosshairs, with attacks that leverage the way smart devices collect, process, and analyze data. Last February, smart—but unsecured—teddy bears were reported to have leaked 800,000 account credentials (and 2 million audio recordings), which made the rounds in the underground. Cybercriminals looked to make more profit by holding the database for ransom.
[READ: How do some of biggest cities in the U.S. fare in securing their internet-connected devices?]
Secure your data: no target is too small or big
Data is certainly changing the way enterprises do business. In today’s increasingly connected world, even the simplest or seemingly smallest piece of information, such as an email address, can be utilized by a cybercriminal to mount spam campaigns for profit. For users: think before you click. Cybercriminals can misuse your own data against you, so make sure that the information you share won't expose you to malware and cyberattacks.
Here are some defensive measures that information security professionals and system administrators can do to secure their organization’s data:
- Integrate additional layers of security. Mechanisms like two-factor authentication (2FA) help further secure data; developers should do the same for the applications they create, whether as homegrown corporate apps or for consumers
- Enforce the principle of least privilege. Restricting the ways attackers can laterally move within the system or network helps deter them from accessing sensitive or personal data; mechanisms like firewalls, network segmentation, and data categorization help in this regard, particularly in enterprise settings
- Reduce your attack surface. Back up your data (and equally ensure its integrity) to mitigate the impact of its loss; and secure the tools used to maintain the applications, networks, and systems that store and manage data
- Secure your gateways. Attackers use various infection vectors to ultimately access your data, which is why it's important to secure gateways—from emails and web to mobile, especially if they're used in a Bring Your Own Device environment
- Keep the system and its applications updated. Security gaps in the infrastructure that stores and handles data become doorways for attackers to steal and repurpose the valuable data they can get their hands on, so ensure that they’re updated; virtual patching, for instance, provides protection for legacy systems and others whose patches are unavailable
Trend Micro Solutions
Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. It features high-fidelity machine learning to secure the gateway and endpoint data and applications, and protects physical, virtual, and cloud workloads. With capabilities like web/URL filtering, behavioral analysis, and custom sandboxing, XGen™ protects against today’s purpose-built threats that bypass traditional controls, exploit known, unknown, or undisclosed vulnerabilities, and either steal or encrypt personally-identifiable data. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks