Sporting Event Threats: Lessons from the 2018 FIFA World Cup
The 21st iteration of the FIFA World Cup, which was held from June to July 2018, was one of the most widely viewed sporting events in history with nearly half of the world’s population tuning in to watch the football tournament. The sheer numbers were staggering. Aside from the viewership, Russia spent an estimated $12 billion to host the event, which also brought in billions in revenue to FIFA and other organizers. In terms of scale, the World Cup is unmatched by few other events.
Of course, an event this size also raises security issues, and it's not just about the need to physically secure everything from the venues and the audience to the players and delegates. The popularity of major sporting events on the internet (for example, the Super Bowl LI generated 240 million Facebook interactions and nearly 28 million tweets) means that security also needs to extend online.
Sporting events and cybercrime
Threat actors capitalizing on massive sporting events is not a new occurrence. These kinds of spectacles present prime targets for cybercriminals looking to maximize their monetization schemes. Some of the most notable examples of sports-related cybercrime attacks from recent history involve the Olympics and the World Cup, arguably the two most significant sporting events of our time.
[READ: Sports-related cybercrime examples]
These campaigns often involve tried-and-true tools and techniques such as spam and phishing to trick users caught up in the festivities. During the last 2018 FIFA World Cup, we found some examples of successful social engineering techniques that tricked users into downloading malware. Despite their simplicity, these attacks often prove to be successful thanks to human curiosity and the sheer amount of people who want to get in on the action.
Android malware disguised as a streaming app
Millions of viewers who don’t have access to feeds from official channels turn to
The app was distributed via a website showcasing popular players such as Lionel Messi and Cristiano Ronaldo:
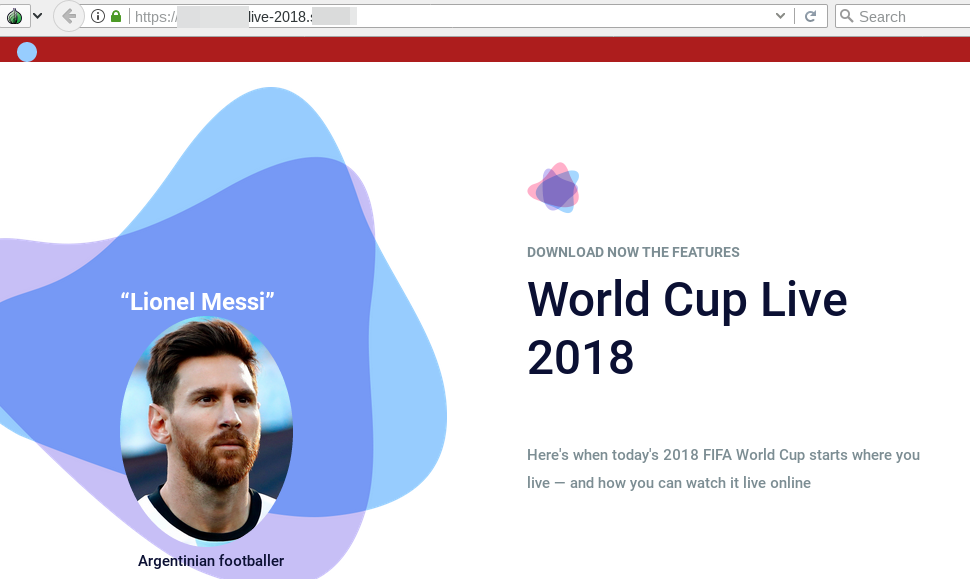
However, this app gave users more than they bargained for. Clicking on the “Download Now” link found in the page with an Android device downloads and installs the malware.
The malware performs a variety of malicious activities, including searching and extracting information (listed below) from the infected device.
- Android Device Name
- Location information
- Sent and received SMS messages
- Audio data of
sniffed call - Files in external storage (PDF,
txt , doc,xls ,xlsx , ppt,pptx )
Malware pretending to be a World Cup “game prediction” document
Another malware sample we sourced and analyzed again takes advantage of fan enthusiasm. This malware came disguised as a document (detected as W2KM_POWLOAD.ZYFG-A) that predicts the outcome of game matches from the 2018 FIFA World Cup.
Opening the document prompts the curious user to enable macro functions. If the user chooses to proceed, a short “analysis” of an upcoming match will be shown:
However, the embedded macro code executes while the user is busy reading the “analysis,” resulting in the download of other scripts and payloads from C&C servers. One of the scripts leads to the download of image files containing an extractable file with a hidden payload.
This executable file can perform multiple functions, including
- Taking screenshots
- Acting as a keylogger
- Searching for
specific file
It also accesses public cloud storage services to upload the gathered information with API keys encoded in itself.
Other potential threats to sporting events
Despite its prevalence, social engineering is not the only threat viewers and participants in sporting events face. Aside from the usual malware-related threats such as fake apps and websites, users are also exposed to non-malware related online scams such as ticket fraud and bogus merchandise offers.
Even legitimate websites can be victims of cybercrime, often via sabotage, defacement or denial-of-service (DDoS) attacks, which can lead to both financial loss and reputation damage.
Defending against these threats
Major sporting events have become a frequent stomping ground for cybercriminals, and there are no signs that this trend will abate soon. As such, it falls to organizations involved in the event and the users to take protective measures to defend themselves from online threats.
For users, being aware of the various social engineering techniques that cybercriminals use will help them avoid these attacks. Caution should always be exercised when visiting unofficial or unauthorized third party websites, especially if these involve downloading applications. The same can be said about downloading documents or clicking links in websites or emails. If a downloaded document specifically asks the user to enable the macro function, as seen in the example above, this is often a sign that the file is malicious in nature.
On the other hand, organizers and organizations connected to the sporting event should take the necessary steps to properly configure and secure their systems and infrastructure. This includes:
- Threat intelligence gathering before, during, and after the event can help paint a picture of the security landscape and the potential threats they can expect.
- The implementation of proper access controls can help control the flow of information and prevent any intrusions into servers and endpoints.
- Checking systems and applications for vulnerabilities will help determine what needs to be updated or fixed before the event itself
- Setting up security compliance audits and certification on contractors or supporting organizations will minimize possible weak points that threat actors can attack.
- All personnel connected to the event should be trained to understand cybersecurity basics, especially if they’re responsible for important systems.
- Implementing a
cyberattack response and remediation plan will help organizers deal with the aftermath of a worst-case scenario.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
- Exploiting Trust in Open-Source AI: The Hidden Supply Chain Risk No One Is Watching
- MCP Security: Network-Exposed Servers Are Backdoors to Your Private Data
- Email Threat Landscape Report: Evolving Threats in Email-Based Attacks
- Deepfake It ‘til You Make It: A Comprehensive View of the New AI Criminal Toolset
 Email Threat Landscape Report: Evolving Threats in Email-Based Attacks
Email Threat Landscape Report: Evolving Threats in Email-Based Attacks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions