Ransomware MongoLock Immediately Deletes Files, Formats Backup Drives

We have been following a new wave of MongoLock ransomware attacks that immediately
Routine and Behavior
Reminiscent of the MongoLock attacks in September 2018, we found this particular campaign also targeting databases with weak security settings. Further, we found this ransomware being hosted on PythonAnywhere, a Python-based online integrated development environment (IDE) and web hosting service. Accessing hxxp://update.pythonanywhere.com/d, it downloads an executable file named update.exe, while accessing hxxp://update.pythonanywhere.com redirects the user to a mimicked page of a gaming site written in Chinese. As of publishing, the site remains
[Read: New multi-platform Xbash packs obfuscation, ransomware,
As opposed to commonly observed ransomware routines wherein files are encrypted, this variant deletes important data found in drives A and D and drops the ransom note in the database.
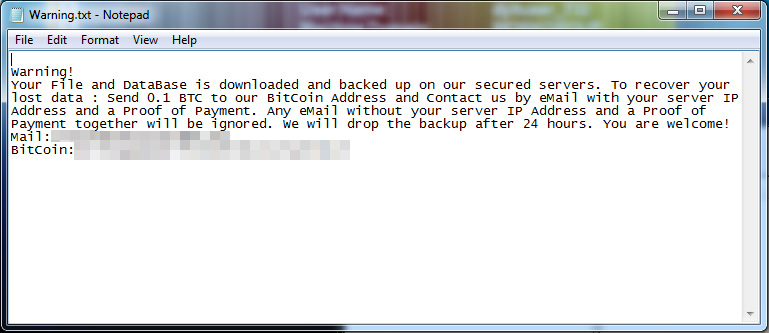
Figure 1.
The ransomware scans and then deletes files found in the Documents, Desktop, Recent, Favorites, Music, Videos, and Recycle Bin folders, and formats the available backup drives. According to the ransom note, copies of the deleted files are uploaded to a URL using an encrypted HTTPS protocol, and we traced the email and command and control (C&C) server hosted in a ToR network. File deletion continues after the infected computer is offline, making the files unrecoverable. Analyzing the sandbox, we found no trace of the database scans and searches, which may imply that the deleted data only affects the physical files found in the specified directories.
[Read: Evolution of Cybercrime]
Following the recent Ryuk ransomware attacks that reportedly halted printing operations of major newspapers in the US, we will continue to follow and investigate this campaign. We suspect that the cybercriminals are still studying the industries and techniques where they can get the most profit, and advise enterprises to revisit and ensure that their security policies and procedures are in place. Administrators are advised to review their online database and server settings to secure them accordingly. To defend against this threat:
- Update your systems and software to prevent cybercriminals from abusing possible entry points and infection channels.
- Practice the 3-2-1 system.
- Use a multi-layered security solution that can scan and block malicious URLs.
[Read: Bridging cybersecurity gaps with managed detection and response]
Trend Micro Solutions
Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. It infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against advanced malware. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise
|
SHA256 |
Detection |
|
698be23b36765ac66f53c43c19ea84d9be0c3d7d81983726724df6173236defa |
Malicious domains/URLs:
- hxxp://update.pythonanywhere.com/d (Arrival vector)
- hxxps://s.rapid7.xyz / 104.27.178.191 (C&C)
With additional insights from Matthew Camacho and Paul Pajares
Update as of January 9, 2019, 7 pm PST:
PythonAnywhere has removed the site.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks