Probing the Activities of Cloud-Based Cryptocurrency-Mining Groups
 Download A Floating Battleground: Navigating the Landscape of Cloud-Based Cryptocurrency Mining
Download A Floating Battleground: Navigating the Landscape of Cloud-Based Cryptocurrency Mining
The allure of unauthorized cryptocurrency mining for malicious actors is easy to understand: For less effort than running a full-blown campaign, they can essentially “print money” by using their victims’ resources, at no cost to them other than the work they exert to compromise the systems.
A recent trend among malicious actors engaged in cryptocurrency-mining activities has been to focus their efforts on the cloud. While GPU-based mining remains the preferred method for most legitimate cryptocurrency miners because of its higher profitability, the scalability of the cloud allows CPU-based mining to become profitable, especially when attackers manage to compromise a large number of cloud-connected machines.
In our research paper “A Floating Battleground: Navigating the Landscape of Cloud-Based Cryptocurrency Mining,” we take a look at the landscape of cloud-based cryptocurrency-mining attacks, focusing on the most prominent groups in this space, their battle for cloud resources, and the impact attacks could have on organizations.
The repercussions of a cloud-based cryptocurrency-mining attack extend beyond resource costs
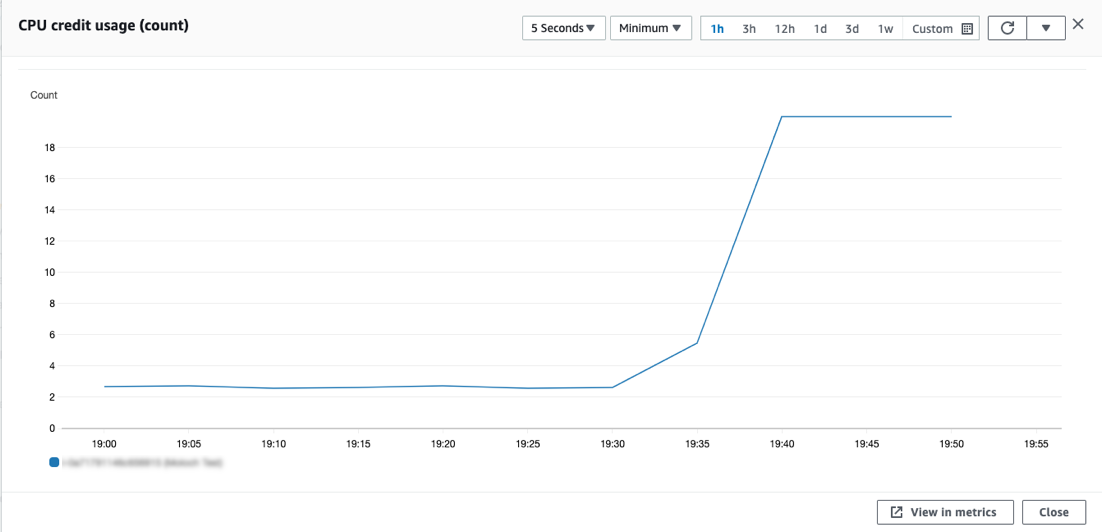
The most obvious impact of a cloud-based cryptocurrency-mining attack on an organization is the resource consumption and cost. Based on our experiment in which we deployed the monero miner XMRig on one of our systems, we saw a significant spike in CPU utilization rate from an average of 13% to 100%. This would translate to a jump in electricity cost from US$20 to US$130 per month, a roughly 600% increase, for a single cloud instance. Multiplying this by the typically large number of instances controlled by an organization, we would get a huge electric bill in the aggregate.
Figure 1. The increase in CPU credit usage for on-demand systems infected with cryptocurrency miners
In addition to the resource costs, a cryptocurrency miner infection could slow down and disrupt the online services of a business. This aspect could actually be more damaging, as it could affect the bottom line and lead to customer dissatisfaction and reputation loss as well as revenue decline.
Beyond the direct monetary impact of an attack, the presence of a cryptocurrency miner in a company’s system also serves as a sign that there are deeper issues in the cloud infrastructure. At first glance, a cryptocurrency-mining attack might not seem as serious a threat as data exfiltration or a ransomware infection. But the method with which malicious actors enter a target’s system is practically the same: They exploit a flaw or weakness that the organization’s security implementation does not or cannot cover.
In essence, we can view a successful cryptocurrency-mining attack as not just a singular cybersecurity incident but as something akin to a canary in a coal mine, that is, it serves as an indicator of poor security hygiene. The tools and techniques used by cryptocurrency-mining groups to gain access to their targets’ systems can also be used by other groups for their own malicious — and perhaps more damaging — purposes.
Cloud-based cryptocurrency-mining groups are varied
Cryptocurrency-mining groups enter cloud deployments through similar methods, typically through the exploitation of a security flaw within target systems, such as an unpatched vulnerability, weak credentials, or a misconfigured cloud implementation. However, each group more or less has its unique traits, from its skill level and experience to the tools and techniques it uses, that set it apart from other groups.
The threat actor group known as Outlaw, for instance, has not changed much from its original campaign. The group tries to gain a foothold in a target’s system either by exploiting vulnerabilities in internet-of-things (IoT) devices and Linux servers or simply by using SSH (Secure Shell) brute-force attacks, after which it installs an IRC (Internet Relay Chat) bot for remote operations. In this case, it seems that Outlaw prefers to keep quiet and keep on doing what works.
In contrast, TeamTNT, which we have covered extensively, has improved steadily since its early appearances. This group prefers to compromise hosts via the exploitation of vulnerable software services, after which it steals credentials for other services to move to other hosts. One of the most notable characteristics of TeamTNT is its loud social media presence, with which it interacts with the public, often pointing out misattributions or complementing security researchers who it feels have done a good job with their analyses.
Figure 2. The Twitter account of TeamTNT
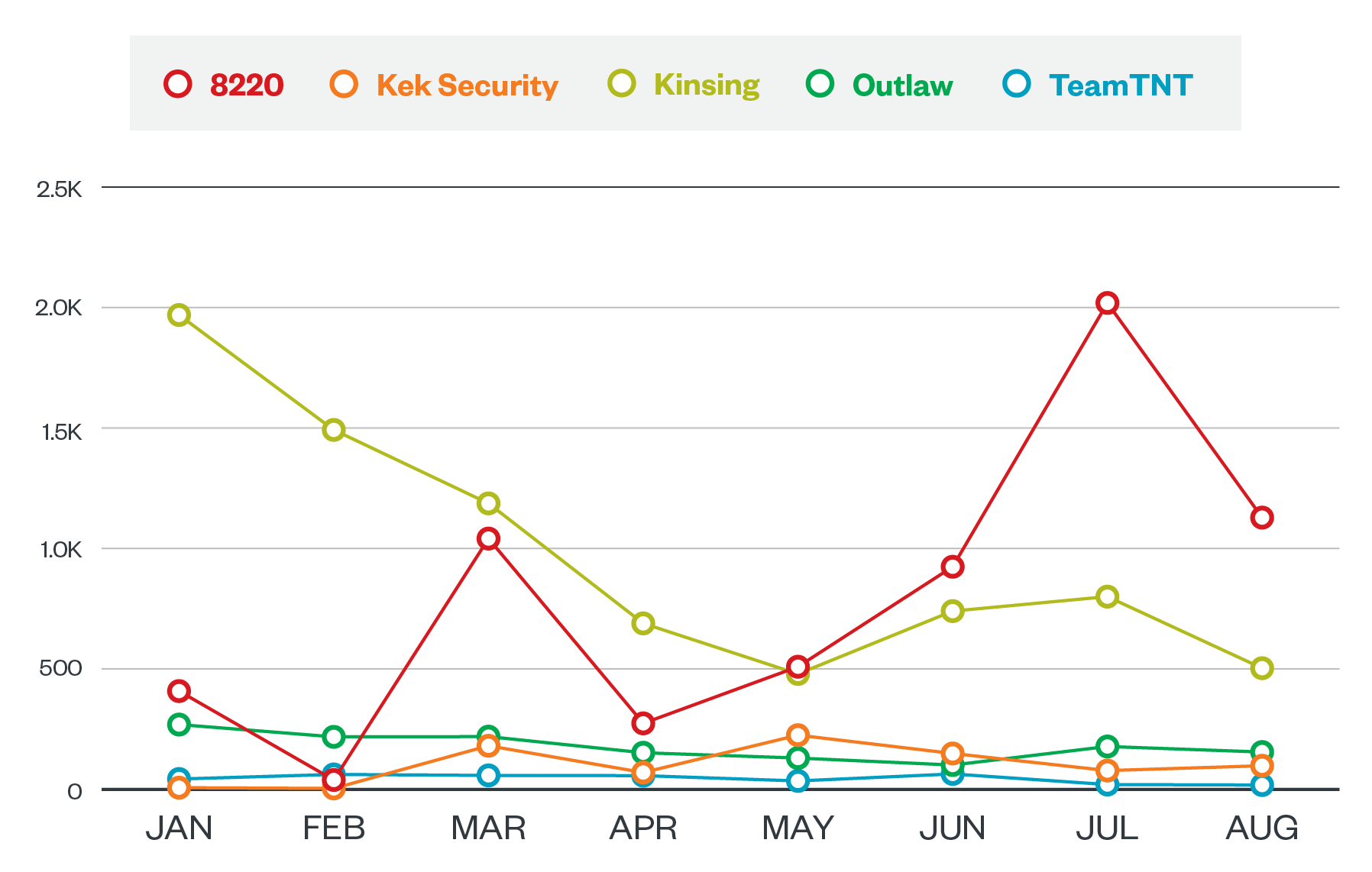
Other groups such as Kinsing and 8220 prefer to lie low and let their actions do the talking. Despite not being as active in the public eye as groups like TeamTNT, these two groups are actually the most active among the ones we analyzed, with beacons to their servers reaching at least 1,000 per month.
Figure 3. A comparison of the monthly activity of cryptocurrency-mining groups from January to August 2021
Kek Security, a relatively new group on the block, hit the ground running with a piece of IRC botnet malware written in Python called Necro, which includes cryptocurrency mining and distributed denial-of-service (DDoS). This group’s notable characteristics include its willingness to integrate new exploits to its tools and its targeting of Windows-based platforms.
There is an ongoing battle for cloud resources
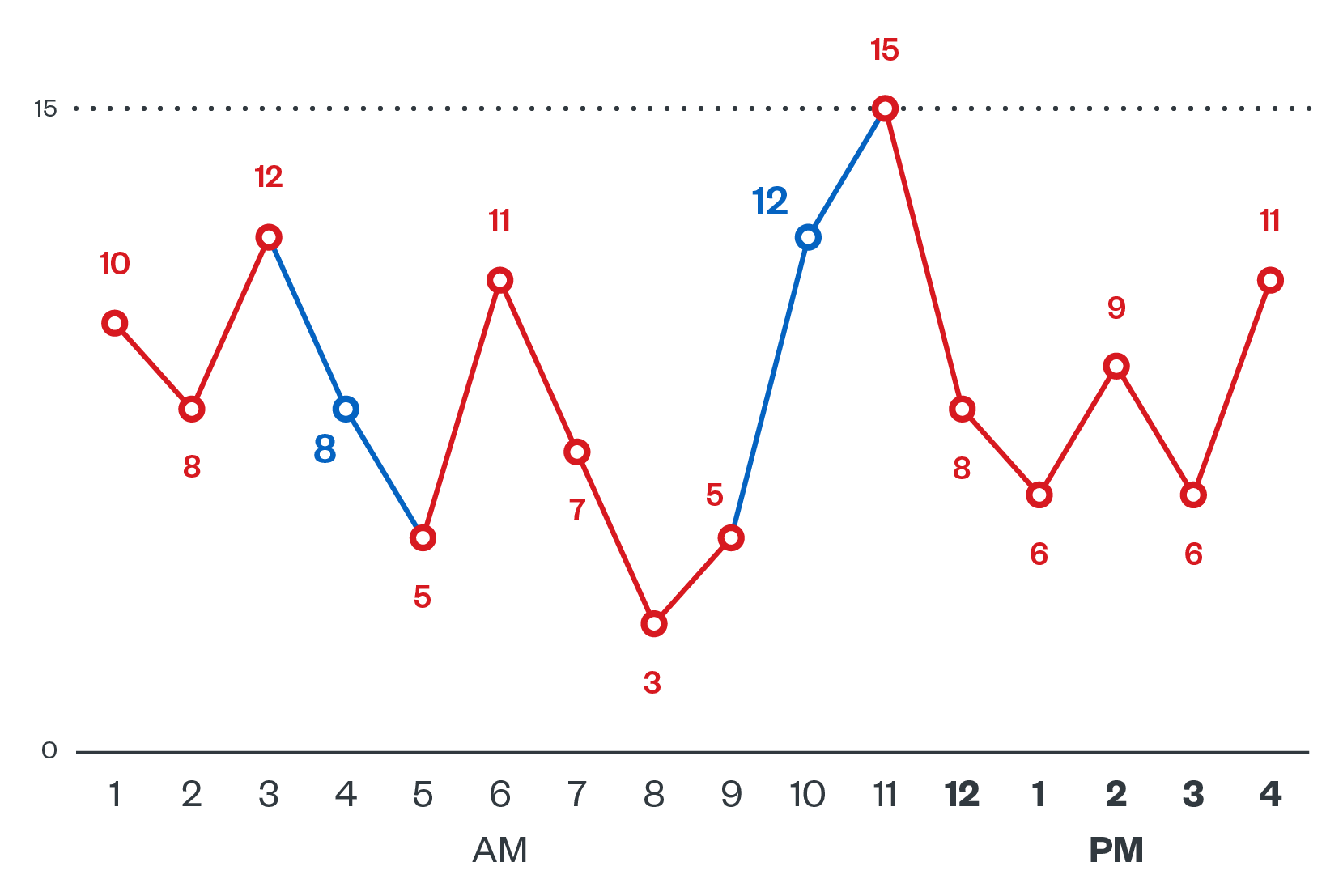
One unique aspect of the illicit cryptocurrency mining landscape is that malicious actor groups do not only have to deal with a target organization’s security systems and staff, but they also have to compete with one another for limited resources. The battle to take and retain control over a victim’s servers is a major driving force for the evolution of these groups’ tools and techniques, prompting them to constantly improve their ability to remove competitors from compromised systems and, at the same time, resist their own removal.
As part of their arsenal, these groups typically implement features such as kill scripts to aid with the deletion of competing cryptocurrency miners, while also strengthening their obfuscation and persistence mechanisms. Some groups avoid the competition altogether by focusing on different aspects of the system, which results in less crossover between rival groups.
One thing is for certain, however: Whoever wins the battle for resources, the victim will always lose.
Figure 4. A typical day showing the back-and-forth control of a cloud instance by Kinsing (red) and 8220 (blue), with the numbers representing inbound control connections
Defense against cloud-based cryptocurrency-mining attacks requires best practices and security solutions
Fortunately, organizations are not helpless when it comes to defending their systems against cloud-based cryptocurrency-mining attacks.
We encourage organizations to strengthen the security of their cloud implementations in general. This includes implementing common best practices such as timely patching and updating of software to lessen the chance of vulnerability exploitation in outdated software versions. Another good practice for security hygiene is minimizing exposure to malicious elements by ensuring that cloud systems are running only the required services and by avoiding the exposure of APIs to the internet, and instead limiting interaction only to administrators and other specific employees. Organizations should also consider deploying tools that can limit and filter network traffic to and from malicious hosts, such as firewalls, intrusion detection and prevention systems (IDS/IPS), and cloud endpoint security products.
It is also a good idea to consult the security guidelines of cloud service providers such as Amazon Web Services, Google Cloud Platform, Microsoft Azure, and Oracle Cloud, since these can help in both the proper configuration and securing of cloud environments.
There are also defenses that are tailored to cloud-based cryptocurrency-mining attacks. For example, rules can be set to monitor resource utilization, track open ports, and check the usage of and changes made to DNS routing. We provide more examples of security best practices and concrete defense strategies in our research paper.
Cloud-based cryptocurrency miners will stay and continue to evolve as they battle both security professionals and one another. Therefore, it is imperative for organizations to stay ahead of the game by knowing more about the threats they could face in the cloud. Our research paper “A Floating Battleground: Navigating the Landscape of Cloud-Based Cryptocurrency Mining” serves as an excellent launching point to learn more about the threat landscape and the malicious actors that inhabit this space.
The indicators of compromise for this paper can be found here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks