PoC Exploits for Memcached DDoS Attacks Published Online
We saw two record-breaking distributed-denial-of service (DDoS) events in the past two weeks. The first was a landmark 1.35 Tbps DDoS attack on GitHub, then Arbor Networks confirmed that a 1.7 Tbps DDoS attack hit an American service provider five days later. The level of DDoS attacks has been rising quickly since attackers started abusing memcached servers to amplify their resources.
How are memcached servers abused?
The attackers spoof the IP address of their targets and send queries to multiple memcached servers; the response can be 50,000 times larger than the query itself. The method results in heavy malicious traffic bombarding the victim’s site. This technique is similar to the reflection attacks that caused trouble in 2013 and 2014, but uses a different and more powerful service.
Recently, two proof-of-concept (PoC) exploit codes on memcached amplification attacks show how these massive DDoS attacks are initiated. The first of these POCs is called Memcrashed and is in a Python script. It relies on the Shodan search engine to find vulnerable memcached servers, and then involves them in an attack against the target. This can all happen within seconds of running the tool.
The second PoC was released on Pastebin. It is written in C and comes with a compiled list of 17,000 vulnerable memcached servers. The script will launch a DDoS attack using the servers from this list and aimed towards the specified target.
How can users mitigate this threat?
The news of memcached servers being used for DDoS also opened up discussion on solutions. While there are general DDoS protection services available, one researcher described a specific mitigation technique for memcached servers.
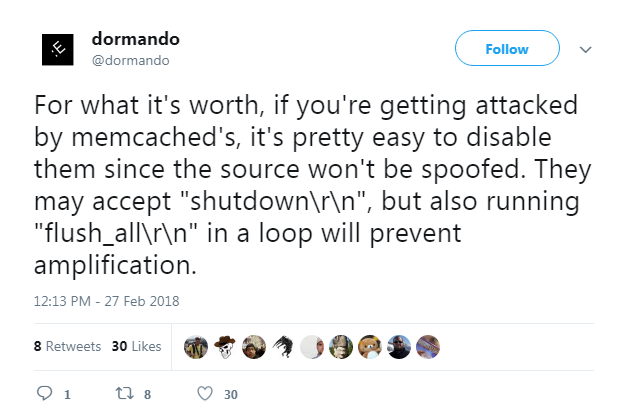
This “kill switch” was tested and deemed completely effective. The “flush all” method essentially invalidates the cache on a vulnerable server, which includes the malicious payload from the DDoS attackers.
Many site owners have since acted, and reports say that the number of visible and vulnerable memcached servers has already dropped since news of the first large DDoS attack came out. The memcached team has also taken steps to address the server abuse by releasing version 1.5.6 in a security release from February 28.
Besides updating servers to the latest version and using the “flush all” mitigation technique, users who are worried about DDoS attacks should also:
- Verify if servers need to be externally accessible and ensure you have as few publicly accessible tools as possible.
- Ensure you have more than one upstream provider so you can fail over to other links if the primary is flooded.
- Ensure your network providers have implemented anti-spoofing (such as BCP38 & 84) so that spoofed packets such as those used in DDoS reflection attacks do not make it to your network.
- Ensure your networks have good traffic monitoring (both in and outbound) using network intrusion tools like Trend Micro™ Deep Discovery Inspector™ and TippingPoint. Trend Micro™ Deep Security™ also provides network security capabilities such as deep packet inspection, intrusion prevention (IPS), and host firewall. We released the following IPS rules for proactive protection from this threat:
- 1008918-Identified Memcached Amplified Reflected Response
- 1008916-Identified Memcached Reflected UDP Traffic
DDoS attacks are rapidly increasing in intensity, and we should expect more frequent attacks now that the PoCs have become public. Cybercriminals are also trying to improve this threat and find ways to monetize the attacks. Users should stay ahead of the curve and take steps to protect their servers before they are compromised.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks