Data Protection Solutions Spring from Exposed PoS Threat
Healthcare providers are attractive targets for cybercriminals because they hold huge repositories of valuable information. The data most hospitals hold range from credit card information and social security numbers to private medical records and health insurance credentials. This month showed that cybercriminals are as eager as ever to access these repositories as Banner Health, one of the largest non-profit health systems in America, suffered a sophisticated cyberattack where hackers were able to acquire the personal and financial data of 3.7 million individuals.
A number of news outlets reported on July 7th that Banner Health discovered that attackers gained access to the point-of-sale network connected to their food and beverage outlets. Hackers were able to obtain customers’ credit card information, from client names to card numbers and verification codes. After further investigation, Banner found that systems holding the personal data of patients and healthcare providers were also compromised. The information exposed may include patient and doctors’ names, addresses, insurance information, health plan details, dates of service, social security numbers and more.
Since credit both card data and personal information were stolen—data which is housed on separate systems—this particular breach has caught the attention of the healthcare industry.
Similar cases and probable causes
A breach like this could be caused by not just one specific malware but by multiple threats. Trend Micro has seen and documented something similar with Operation Black Atlas, a widespread campaign that Trend Micro has been tracking for some time. Trend Micro found that the PoS component of Black Atlas was just an add-on to a bot, like Gorynych or Diamond Fox, which gathers and steals information. Explicitly, the PoS modules in Gorynych or Diamond Fox could be enabled as an option by the cybercriminal. The bot also contains other modules that could be optionally activated, like a keylogger component that cybercriminals can use for their operation.
Black Atlas targeted small to midrange businesses from different industries, including healthcare. The operators used separate malware like different tools in a Swiss Army knife, with each having a specific functionality and purpose. They followed a multi-stage plan, first gathering information with one set of tools, and then using a second set of tools to gain further access to the business’ system. After gaining access, the criminals would install a PoS threat and then gather financial and other valuable data.
The chain of infection, from PoS to other systems in the network, can be compared to the events of the Banner Health breach.
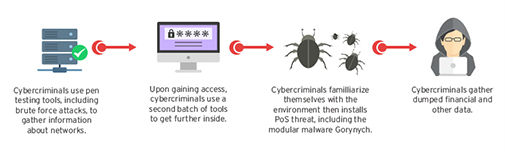
Operation Black Atlas infection chain
Another possible cause is network organization. The system containing the PoS data and the system containing the doctors’ and patients’ personal data could have been housed on one network, or a "flat network". These designs are known for convenience, but not for security. If hackers had access to one system on a flat network, they could easily access the rest.
This breach is a stark reminder for organizations to follow recommended security measures and find effective solutions to protect their data. Here are some suggestions:
- Implement a firewall or Access Control List (ACL) on remote access services
- Change default credentials of PoS systems and other internet-facing devices, or check if your third-party vendor has done so
- Segregate your network to prevent lateral attacks
- Larger organizations should eliminate unnecessary data, and keep tabs on what’s left
- Ensure essential controls are met, regularly check that they remain so
- Monitor and mine event logs
- Evaluate your threat landscape and prioritize treatment strategy
For operators that handle credit card payments, the Payment Card Industry Data Security Standard (PCI-DSS) requirements should be followed strictly, particularly when it comes to the segmentation of networks. And segmentation isn’t just a priority for billing purposes, but also for the security of Protected Health Information (PHI). The healthcare industry standards are outlined in the Health Insurance Portability and Accountability Act of 1996 (HIPAA), which states “institutions that can effectively isolate the PHI from other data are most effective at maintaining control over this information.”
As hackers come up with increasingly sophisticated schemes, the healthcare industry has to stay one step ahead. Healthcare enterprises have to adopt a layered security approach that allows them to oversee, control, and protect servers, networks, and the wide matrix of user devices and endpoints that are used in the company.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One