Ransom.Linux.BLACKSUIT.THEODBC
Linux/Filecoder.Royal.B trojan (NOD32), Ransom:Linux/BlackSuit.A!MTB (MICROSOFT)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It encrypts files with specific file extensions. It drops files as ransom note.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following files:
- {Malware File Path}\blacksuit_log_{number} → log file
- {Malware File Path}\PS_syslog_ → contains a list of processes with the string vmsyslogd in its name
- {Malware File Path}\PID_ → contains PID of the executed process
- {Malware File Path}\PS_list → contains PID of all running processes
- {Malware File Path}\list_ → contains a list of running virtual machines
It adds the following processes:
- /bin/sh -c ps -Cc|grep vmsyslogd > PS_syslog_
- /bin/sh -c kill -9 {PID} → terminates processes with the string vmsyslogd in its name
- If -killvm is passed as an argument:
- /bin/sh -c esxcli vm process list > list_
- /bin/sh -c esxcli vm process kill --type=soft --world-id={World ID of the VM to terminate}
Other Details
This Ransomware does the following:
- It only encrypts VM related files by default.
- It terminates processes with the string vmsyslogd by default.
- Based on analysis of the codes, this malware has the following capabilities:
- It can terminate VM processes using its World ID and VMX Cartel ID by executing the following commands:
- /bin/sh -c lsof | egrep 'Cartel|%s' > CID_list_
- /bin/sh -c esxcli vm process list > PID_list_
- /bin/sh -c esxcli vm process kill --type=force --world-id={World ID or VMX Cartel ID of the VM to terminate}
- It can drop the following files:
- {Malware File Path}\CID_list_ → contains a list of VMX Cartel IDs
- {Malware File Path}\PID_list_ → contains a list of running virtual machines
- It can terminate VM processes using its World ID and VMX Cartel ID by executing the following commands:
It accepts the following parameters:
- required to proceed to its encryption routine:
- -name {32 byte characters} → used to define Victim ID
- -p {directory} → used to specify a target directory to encrypt
- -percent {0 to 100} → used to define encryption parameter
- -thrcount → used to create a specified number of threads depending on the number of processors of the infected machine
- -skip {text file} → used to specify a text file containing folders to skip
- -killvm → used to terminate VM processes via ESXCLi command
- -allfiles → used to encrypt all files
- -noprotect → does not check if the process has already been started, does not drop the file PID_
- -vmsyslog → does not terminate processes with the string vmsyslogd in its name
- -demonoff → used to display logs on terminal
Ransomware Routine
This Ransomware encrypts files with the following extensions:
- .vmem
- .vmdk
- .nvram
- .vmsd
- .vmsn
- .vmss
- .vmtm
- .vmxf
- .vmx
It avoids encrypting files with the following strings in their file name:
- .blacksuit
- .BlackSuit
- .blacksuit_log_
- .list_
- .PID_
- .PS_list
- .PID_list_
- .CID_list_
- .sf
- .v00
- .b00
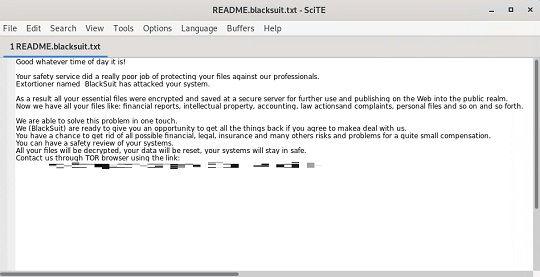
- README.BlackSuit.txt
- README.blacksuit.txt
It appends the following extension to the file name of the encrypted files:
- {Original File Name}.{Original File Extension}.blacksuit
It drops the following file(s) as ransom note:
- {Encrypted Directory}\README.blacksuit.txt
SOLUTION
Step 1
Scan your computer with your Trend Micro product to delete files detected as Ransom.Linux.BLACKSUIT.THEODBC. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Step 2
Restore encrypted files from backup.
Did this description help? Tell us how we did.


