Hacked or Spoofed: Digging into the Malaysia Airlines Website Incident
Less than a month after the hack of United States Central Command (USCENTCOM or CENTCOM) Twitter and YouTube accounts, the hacker group that claimed responsibility for it has redirected visitors of the Malaysia Airlines (MAS) official website on Monday, January 26 to another site displaying the following:

Image source: @PzFeed Twitter post
It's believed that the 404 message could be referring to the Malaysian Airlines flight MH370 that has gone missing in March 2014.
MAS confirms that “its Domain Name System (DNS) has been compromised where users are re-directed to a hacker website when www.malaysiaairlines.com URL is keyed in” in a statement released on January 26 in its Facebook account.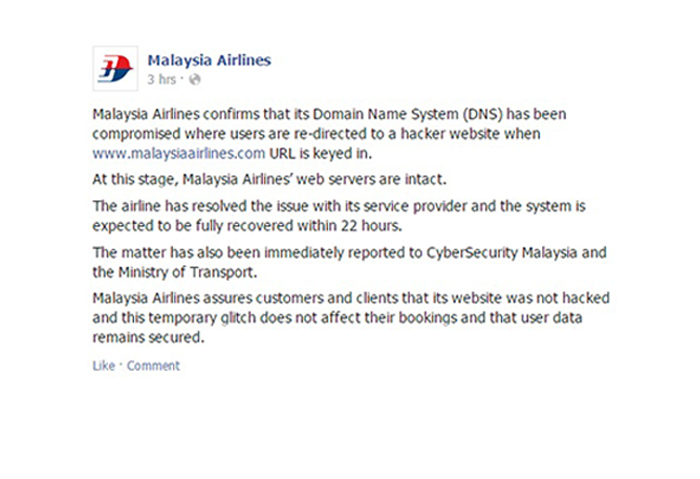
MAS denies that their systems have been hacked and maintains that their web servers are intact, despite news reports that describe it as a hacking incident.
This response come at the heels of a series of tweets that alleged “Cyber Caliphate” Twitter user @LizardMafia released after the incident spread to the public, hinting at stolen information, as shown below: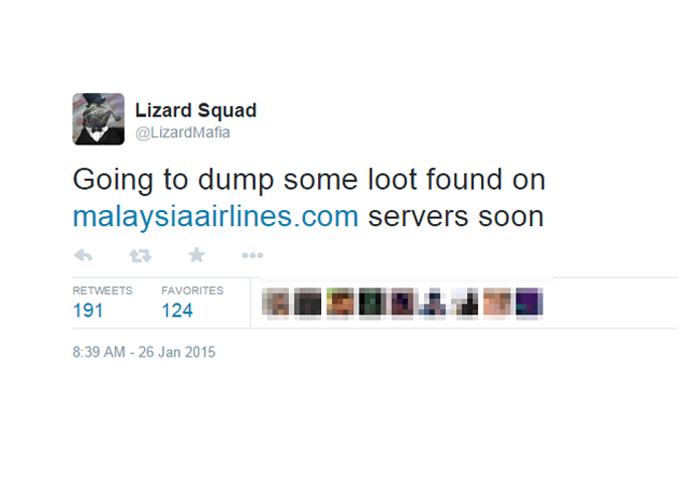
Hacked, Spoofed, or Defaced?
The group's motivations for targeting the MAS website are yet to be made clear, but the way they compromised the site and the extent of the damage can vary.
MAS ruled out hacking from the list of possibilities. The term “hacking” itself is highly problematic here given that it typically implies acts where individuals create and modify computer software to get inside a system’s servers.
Based on how MAS pointed to the compromise of their Domain Name System (DNS) and said that their “web servers are intact,” it is highly probable that the website was attacked using a “DNS spoofing attack.” These attacks alter DNS service providers’ settings, and not the actual website owner’s servers, by changing the stored IP address of the legitimate site to one that leads to an IP address of a fake site.
The DNS spoofing attack vector used against the MAS website may have been committed through cache poisoning. In essence, the cybercriminals abused the cached IP address in the DNS server to redirect site visitors.
The term “website defacement” also comes into the picture given that it covers attacks that change the appearance of websites, usually inserting political messages into them. Given that visitors saw a different site from what they expected, this may be considered a form of website defacement although the website was technically untouched.
[Read: Defining website defacement]
What Can We Learn From This?
Website owners are put in the limelight in cases of DNS spoofing and defacement such as this, even as the technical glitches or vulnerabilities was on the side of the service provider. As such, one proactive practice is to thoroughly research which service provider to trust. Website owners need to look into the security measures observed by these providers when packaging web hosting services. They should also probe into the track record of potential providers, taking note to see how agile and accurate they are in cases of anomalies in the website.
In response, cases like this should act as a wake up call for service providers to harden their DNS servers to avoid being compromised on their end.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks