Rising From the Underground: Hacktivism in 2024
Trend Research
We have been looking at the hacktivism landscape to help the United Nations Interregional Crime and Justice Research Institute (UNICRI) understand this cybercriminal phenomenon for its paper on the topic. The UNICRI paper was released today at a launch event held at the United Nations headquarters where we gave an overview on emerging trends in the underground.
Hacktivism refers to cybercriminal attacks that often involve breaking into systems for politically or socially motivated purposes, usually to make a statement in support of a cause or against governments or organizations.
In our close monitoring of this criminal phenomenon, it comes as no surprise that hacktivism is on the rise alongside the increased polarization of the political landscape; the latest conflicts in Ukraine and Palestine notably have accelerated this trend.
The hacktivist attacks we see more often are distributed denial-of-service (DDoS) attacks, where hacktivist groups recruit volunteers, pooling along with them their internet bandwidth, to a deluge of requests to the victim’s web server with the objective of overwhelming it and rendering it inoperative. It’s a simple scheme: Volunteers only need to point their DDoS tools to the target site and select the “Attack” button. There’s no knowledge required, just the willingness to attack the site.
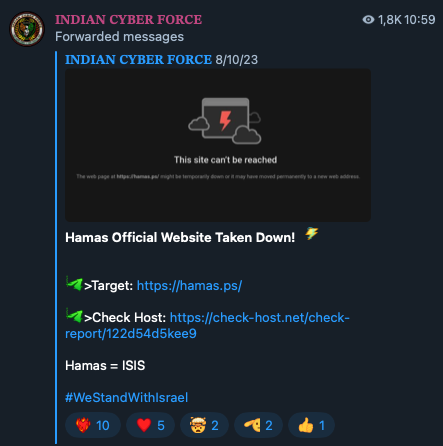 Figure 1. A hacktivist group’s announcement of a successful DDoS attack on the Hamas website
Figure 1. A hacktivist group’s announcement of a successful DDoS attack on the Hamas website
Other hacktivist cyberattacks involve data theft and more complex tactics. These are performed by politically motivated and skilled hackers who happen to align with a certain group’s ideology. We have already seen hacktivist attacks that involve website defacement and information leaks targeting critical infrastructure, all with the observable intent to cause reputational damage.
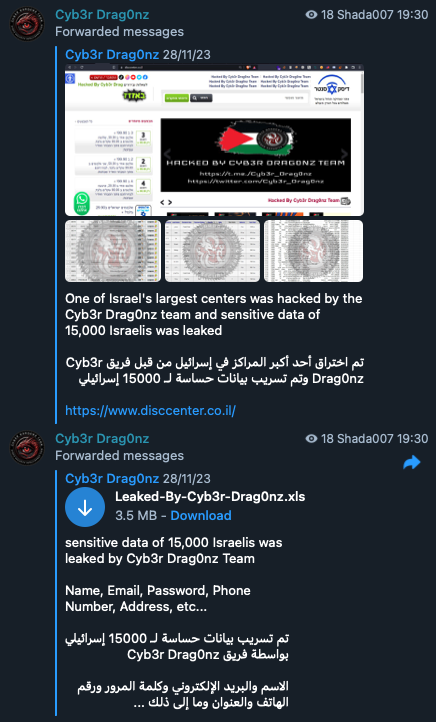 Figure 2. A hacktivist group’s announcement of a successful website defacement and subsequent publication of stolen data
Figure 2. A hacktivist group’s announcement of a successful website defacement and subsequent publication of stolen data
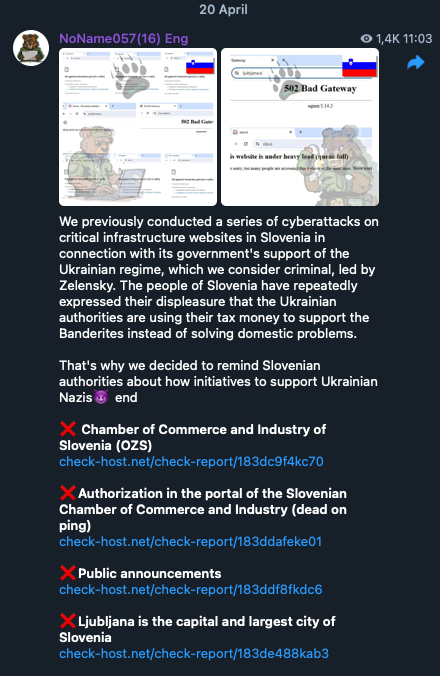 Figure 3. A hacktivist group’s announcement of several web defacement attacks on Slovenian critical infrastructure sites in connection with the country’s alignment with Ukraine in the Russia-Ukraine conflict
Figure 3. A hacktivist group’s announcement of several web defacement attacks on Slovenian critical infrastructure sites in connection with the country’s alignment with Ukraine in the Russia-Ukraine conflict
These hacktivist communities are usually a mix of skilled hackers and volunteers with no technical background. Nowadays, we rarely see them organizing themselves on deep web sites such as closed web forums or Tor sites; the use of encrypted chat services such as Telegram is also an increasingly common method used by these communities to coordinate attacks. The transition toward publicly accessible platforms lowers the barrier of entry for collaborators who do not have the technical background to get into deep web sites, and it also gives us the advantage of being able to observe and monitor their activity. These encrypted chat service channels also serve the purpose of telling the world about the attack.
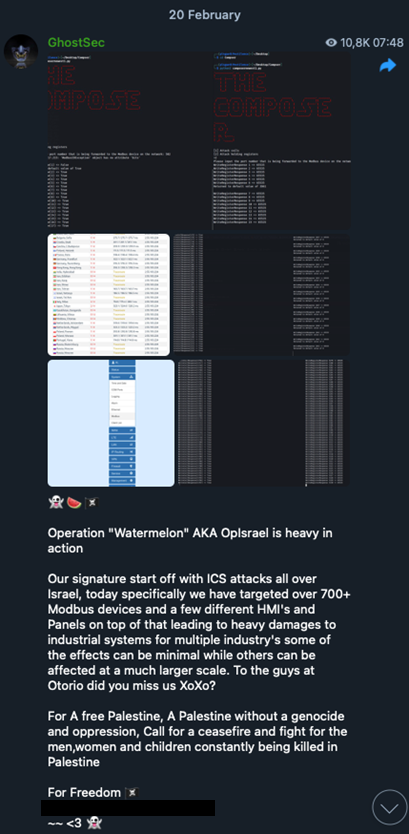 Figure 4. A hacktivist group’s announcement of a successful attack on industrial systems in connection with the Hamas-Israel conflict
Figure 4. A hacktivist group’s announcement of a successful attack on industrial systems in connection with the Hamas-Israel conflict
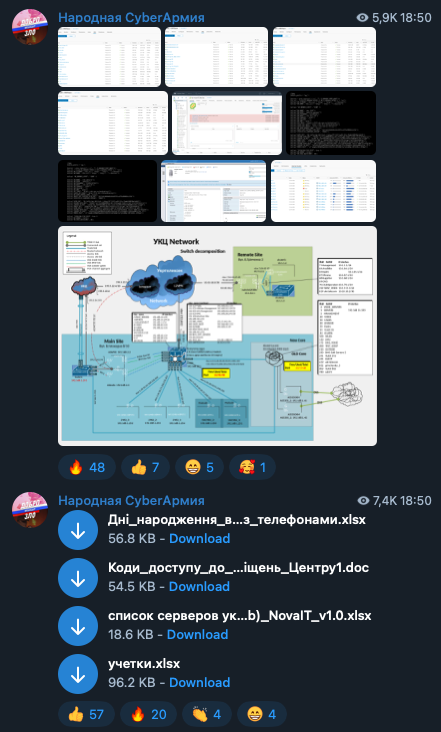 Figure 5. A hacktivist group’s information leak release of a Ukrainian government site’s network infrastructure
Figure 5. A hacktivist group’s information leak release of a Ukrainian government site’s network infrastructure
The joint report of UNICRI and the United Nations Office of Counter Terrorism (UNOCT) contextualizes hacktivism today, defines cybercrime-as-a-service in the underground, and provides a summary of the attacks we have been observing. We are proud to have lent our expertise and given advice during the report’s creation, as well as to have been a part of the report’s launch to give context on cybercrime-as-a-service and trends in the underground.
The hacktivism landscape continues to be a focus area in our research, and you can look forward to more publications that will provide more comprehensive coverage on several hacktivist groups, studies of real-life examples of their attacks, and discussions of our observations on how these groups align themselves in ideological divisions.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks