Study Finds Fake News Spreads Faster Than Real News on Twitter
 In late April 2013, the Associated Press’ (AP) Twitter account surprised its millions of followers after it tweeted that an explosion at the White House injured President Barack Obama. It garnered over 4,000 retweets and became one of the most expensive tweets in history after it caused stock prices to drop. While stock markets rebounded as soon as the tweet was confirmed to be fake, the damage had been done — it cost over $130 billion in stock value losses.
In late April 2013, the Associated Press’ (AP) Twitter account surprised its millions of followers after it tweeted that an explosion at the White House injured President Barack Obama. It garnered over 4,000 retweets and became one of the most expensive tweets in history after it caused stock prices to drop. While stock markets rebounded as soon as the tweet was confirmed to be fake, the damage had been done — it cost over $130 billion in stock value losses.
The incident was cited by the Massachusetts Institute of Technology’s (MIT) recent research, which delved into 126,000 stories tweeted by around 3 million accounts from 2006 to 2017. The researchers, Soroush Vosoughi, Deb Roy, and Sinan Aral, found that fake news stories spread faster and were more likely to be retweeted than true stories. Fake news cascade down to between 1,000 and 100,000 Twitter users. True or verified stories, however, take six times longer to reach 1,500 people. They also note that fake news was frequently retweeted more by humans than bots.
[TrendLabs Research: Fake News Machine: How Propagandists Abuse the Internet and Manipulate the Public]
Their research noted that falsehood “diffused significantly farther, faster, deeper, and more broadly than the truth in all categories of information, and the effects were more pronounced for false political news than for false news about terrorism, natural disasters, science, urban legends, or financial information. We found that false news was more novel than true news, which suggests that people were more likely to share novel information.”
Indeed, fake news’ impact is a perennial challenge for governments, organizations, and individuals alike. This year, in fact, fake news campaigns — whether politically or financially motivated — are expected to continue, along with cyberpropaganda campaigns, using multifarious and well-trodden techniques to spread.
[Related: Exploring the Online Economy that Fuels Fake News]
To further exemplify: Trend Micro’s research in June 2017 looked into the Twitter network of the #MacronLeaks hashtag. The study found that the campaign had a unique community that comprised “gurus,” which are real, human accounts, and “sect followers,” who exhibit the usage behaviors of real followers but may also be bots. On Twitter, fake news campaigns usually involve closely-knit sect followers retweeting the same fake content that gurus post.
Abusing social media platforms like Twitter is just the tip of the iceberg. Trend Micro’s research also found a thriving economy in gray and underground marketplaces dedicated to fake news. Discrediting and silencing a journalist, for instance, can cost US$55,000, while creating a celebrity with 300,000 followers within a month can cost as low as $2,600. The Russian underground uses crowdsourcing as a business model for distributing fake news.
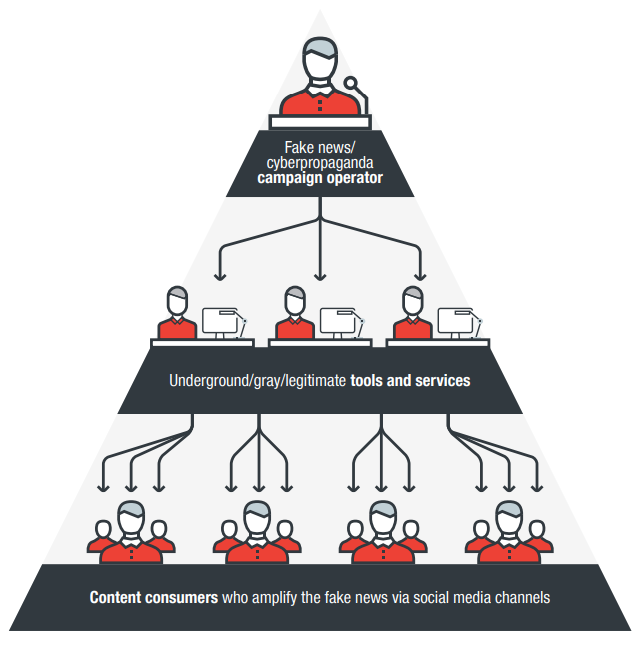
How an operator employs or abuses underground, gray, and legitimate marketplaces to disseminate fake news
Think before retweeting
Apart from posting guidelines for users, Twitter has policies for third-party application developers especially against tweet automation and related activities that serve as distribution channels for fake news. Twitter, along with Facebook and Google, is also exploring ways to combat fake news, including “trust indicators” that enable users to vet the veracity of the content they host.
Twitter also said that it would further collaborate with experts on developing a “health check” mechanism to provide a better environment for public conversations. Twitter provided the data used in MIT’s research.
The readers/users themselves ultimately form the first line of defense against fake news. Spotting red flags such as hyperbolic and clickbait headlines and the absence of credible sources are just some of them. Read beyond the headline, check the sources, and get out of the “filter bubble” by reading from a broader range of reputable sources.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks