Ransomware Recap: January 1 - 13, 2017
 On January 1 2017, the state of California took its fight against ransomware a step further after a new law, one that specifically categorizes ransomware as a crime, took effect. Based on Senate Bill 1137 put forth in early 2016 and duly approved on September 27, 2016, the legislation drew broad support for seeking to enforce more specific penalties to identified ransomware perpetrators. This includes up to four years of prison time and a US$10,000 fine.
On January 1 2017, the state of California took its fight against ransomware a step further after a new law, one that specifically categorizes ransomware as a crime, took effect. Based on Senate Bill 1137 put forth in early 2016 and duly approved on September 27, 2016, the legislation drew broad support for seeking to enforce more specific penalties to identified ransomware perpetrators. This includes up to four years of prison time and a US$10,000 fine.
This makes California the second state to enact a law that specifically categorizes ransomware as a crime, after Wyoming did the same in 2014. While this move strengthens the authorities' continuing commitment to put a stop to ransomware’s surge, crafting and enacting a law does not necessarily guarantee an end to these extortion schemes.
In early January, another academic institution was reportedly hit by ransomware. The Los Angeles Community College District (LACCD) resorted to paying a ransom amounting to $28,000 to perpetrators behind the attack on Los Angeles Valley College (LAVC). In a release, LAVC President Erika Endrijonas confirmed that the infection took place on December 30, 2016. The malware spread across the entire network, disrupting several computer, online, email, and voice mail services.
The school and district officials did not disclose the type of ransomware used in the attack, but based on their report, a ransom note left in one of the institution’s servers threatened to delete the corresponding private key needed for recovering their files after a seven-day deadline. The ransom was then paid in time for the resumption of classes through the cybersecurity insurance policy. The school staff then received the decryption keys to unlock and regain access to systems and data one at a time.
During the same week, schools in the U.K. were also hit by a series of ransomware attacks. ActionFraud UK National Fraud & Cyber Crime Reporting Center issued an alert to warn schools of a recent spate of scams that led to ransomware infections.
According to the security warning, fraudsters hid behind the guise of government officials from the “Department of Education” and cold-called establishments. The calls tricked the staff into sharing the personal email or contact number of the head teacher or financial administrator so as to send sensitive files on exam procedures and mental health assessments. Once the information is revealed, an email containing a malicious .zip file attachment triggers the download of ransomware, which will encrypt files and demand ransom of up £8,000 or US$9,800.
Other British schools have been targeted using a similar modus. Reports note that other scammers have also used the Department for Work and Pensions and telecommunications providers to trick targets into running malware onto their systems.
Here are other notable ransomware stories from the past two weeks:
Merry X-Mas
The first week of January saw the entry of a new ransomware family that says "the Yuletide season is not over." Security researchers discovered Merry X-Mas ransomware (with samples detected by Trend Micro as RANSOM_EXMAS.A, RANSOM_EXMAS.E and RANSOM_EXMAS.D) being distributed through spam emails posing as a consumer complaint from the Federal Trade Commission.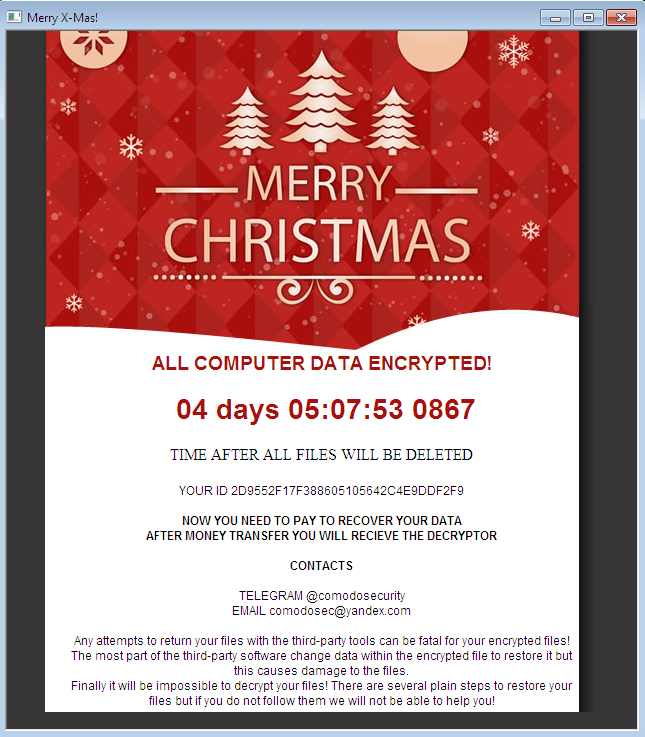
Figure 1 Merry X-Mas ransom note
A legitimate-looking link that supposedly points to the document of the actual complaint will trigger the download of a file named, complaint.pdf.exe. When the file is opened, the installer will remain idle in the background for some time before it begins the encryption process. It will then scan for targeted extensions and encrypt files, before appending either .PEGS1, .MRCR1, or .RARE1 extensions to the filenames of the locked files. Payment instructions will then be communicated to the victim either by email or Telegram, with an undisclosed ransom amount.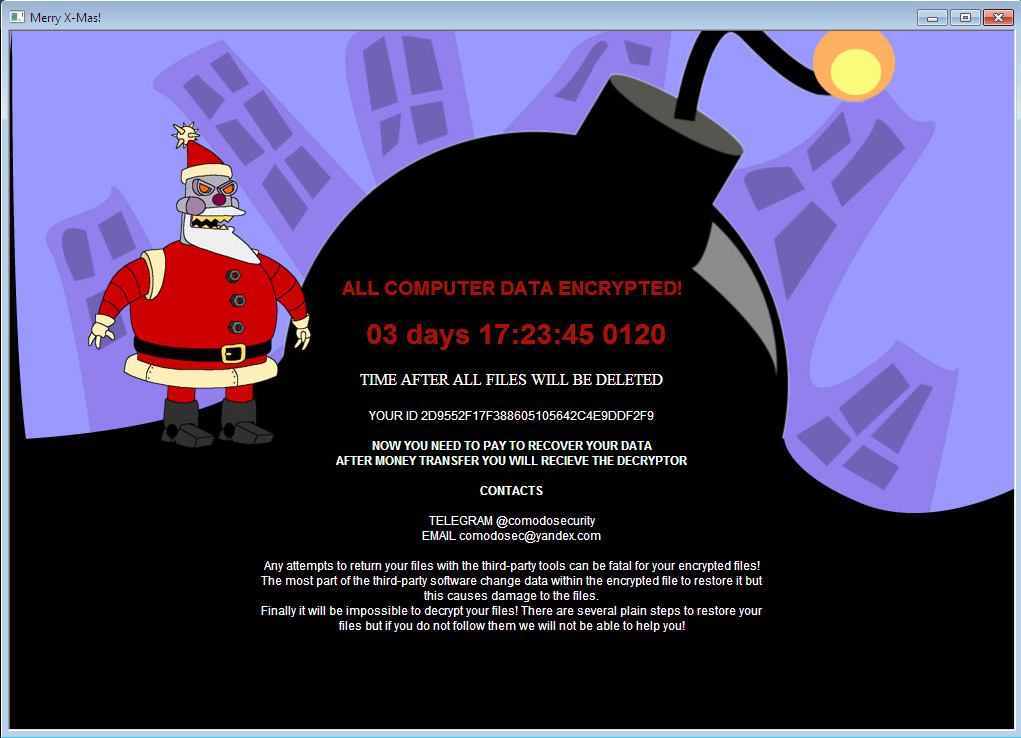
Figure 2 Ransom note found in the new variant of Merry X-Mas
Shortly after the first few variants of Merry X-Mas were reported, a new variant also made it rounds. The second wave of attacks showed a variant (detected by Trend Micro as RANSOM_EXMAS.C) exhibiting different behaviors and evolved capabilities. This time, would-be victims are sent a bogus court attendance notice with a link that downloads a malicious file. It was later found out that this variant, once downloaded, also drops another malware, DiamondFox, which is used by the ransomware operators to collect data such as sensitive files and passwords from infected hosts. Sold in the underground, DiamondFox, is capable of turning infected hosts into DDoS bots, stealing credit card credentials from PoS systems and browser credentials, among others.
FSociety
In August 2016, ransomware developers paid homage to popularHollywood TV series, Mr. Robot with a variant dubbed FSociety ransomware (detected by Trend Micro as RANSOM_CRYPTEAR.SMILA) and in November, this spawned another variant (detected by Trend Micro as RANSOM_REMINDMEFSOCIETY.A) based on Hidden Tear called Remind Me.
At the onset of 2017, ransomware developers once again made its presence felt with a new variant (detected by Trend Micro as RANSOM_FSOCIETY.C), which analysts describe as a feeble attempt to create a screen locker. On January 2, its developers took to Twitter to introduce themselves and challenge security vendors, including Trend Micro, of their entry with a link to a VirusTotal page.
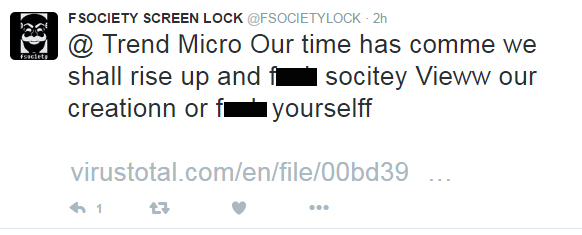
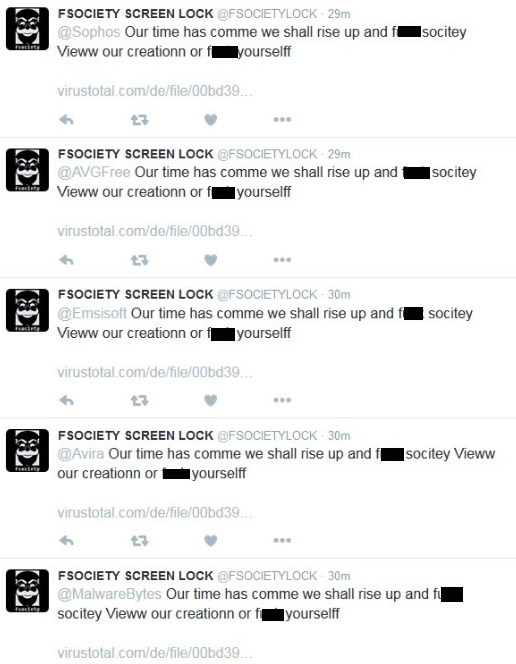
Figure 3 Twitter posts from the developers of the new FSociety Locker variant
It appears that the variant fails to create the kind of impact it claims to make. Upon execution in a machine, it will try to establish a boot persistency mechanism by adding a binary 26 times to the Startup folder. But this routine goes to waste as it force-restarts the machine after displaying a screen locking image—an indication that this variant could either be still in development or simply faulty.

Figure 4 Screenlocker background
Another variant of FSociety (detected by Trend Micro RANSOM_FSOCIETY.D) seen in the first two weeks of 2017 is another screenlocker. It does not have encrypting capabilities, but it will lock the machine and display an image with three buttons in Portuguese that translates to “Credits”, “Make the Payment”, and “How to Buy Bitcoin”.
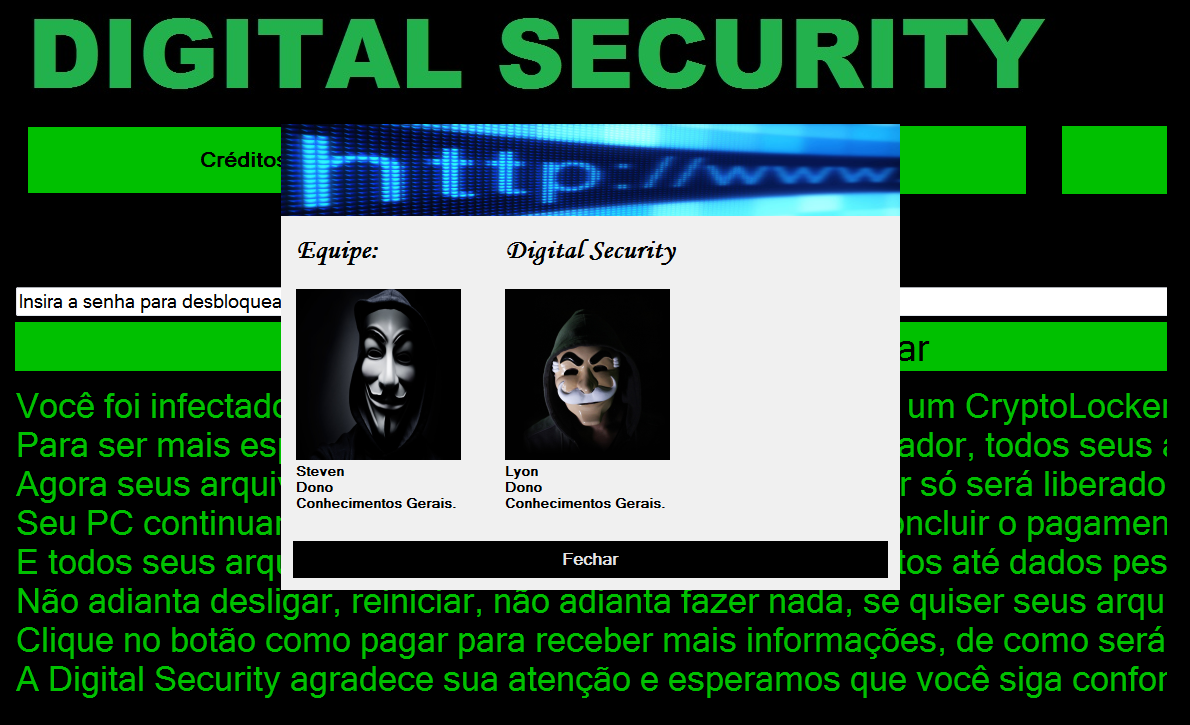
Figure 5 Screen locker background
This particular variant asks for a ransom of 0.033 bitcoins, or $29. Interestingly, this variant shows signs of ongoing development as typing in the password “senha”, which means “password” in Portuguese, unlocks the screen.
KillDisk
Before 2016 ended, we have reported that the creators of KillDisk updated the malware with a ransomware feature that encrypts targeted files and appends them with string "do not touch crypted file.” Right after encryption, it locks the user out of the machine, displaying a ransom note.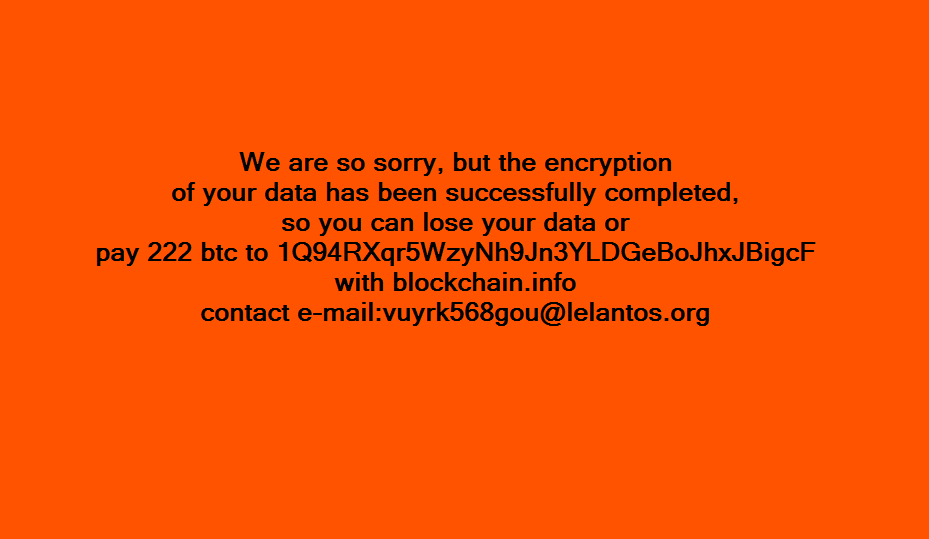
Figure 6 KillDisk ransom note used in its Windows variant
Researchers have since seen a Linux variant (detected by Trend Micro as RANSOM_KILLDISK.A) that works differently from the Windows version. This variant encrypts files using Triple-DES, encrypting each file using varying sets of 64-bit encryption keys. It scans and targets folders and appends files with “DoN0t0uch7h!$CrYpteDfilE".
It will then display its ransom screen using the GRUB bootloader, a standard Linux bootloader, with text similar to the ones used by the Windows variant. Researchers also noted an issue regarding its encryption process, where this version does not save its encryption key either on disk or online. This would mean that a victim will not be able to recover the encryption files. However, it was later discovered that a flaw in this variant would allow researchers to recover encrypted files—a hole that does not exist in its Windows counterpart.
Edgelocker
EdgeLocker (detected by Trend Micro as RANSOM_EDGELOCKER.A) stealthily gets into a system and encrypts files with the use of standard RSA cryptography. Upon encryption, this variant appends the extension .edgel to the file names of the locked files.
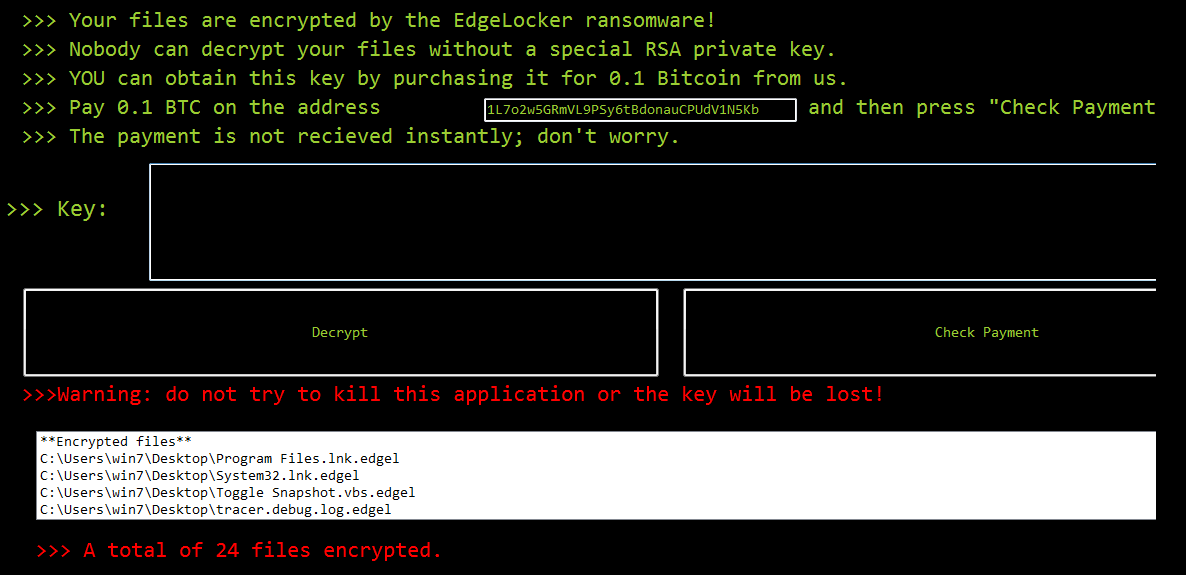
Figure 7 EdgeLocker ransom note
Following encryption, this variant opens a pop-up window showing the ransom demand of 0.1 bitcoin, or around $89.
Firecrypt
A variant of JanBleed called FireCrypt (detected by Trend Micro as RANSOM_BLEEDGREEN.A) surfaced at the beginning of the year. Reports have uncovered how the author behind this ransomware variant utilizes a command-line application to automate the process by which it puts together samples, with capabilities to modify its settings.
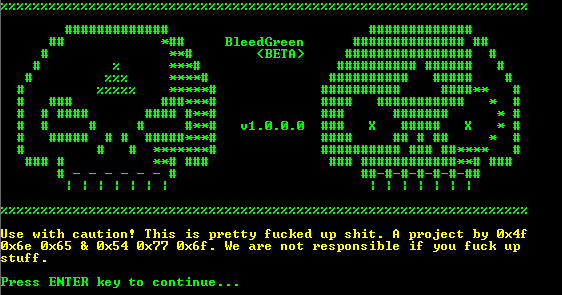
Figure 8 BleedGreen builder used by FireCrypt author
Its builder, BleedGreen (detected by Trend Micro as RANSOM_EDA2BLEEDGREEN), is used by the author to create unique ransomware executables. It also has options to include features in the malware to be generated seen in the image below: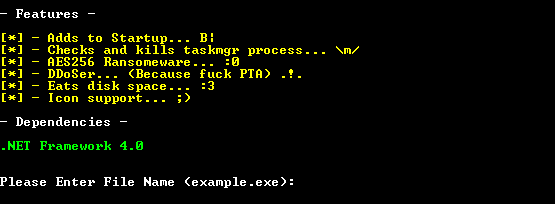
This builder, however, is considered as low-end, compared to builders used by other ransomware operations that offer an array of other options like identifying a bitcoin address for payment transactions, contact email address, and ransom amount.
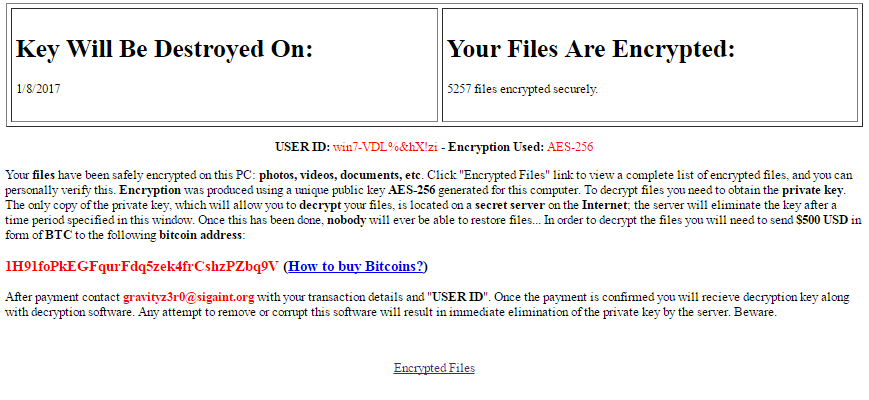
Figure 9 FireCrypt Ransom note
Once installed into a victim's machine, FireCrypt disables the system’s Task Manager and starts encryption of a list of 20 file types through AES-256 algorithm. It will then rename the locked files by appending the extension name .firecrypt. Following encryption, it drops a ransom note on the desktop of the infected machine. It contains a unique user ID and a ransom demand of $500 to be sent in bitcoins to a bitcoin wallet.
Spora
Spam emails hiding under the guise of fake invoices are reported to be carrying a new ransomware family named Spora (with samples detected by Trend Micro as RANSOM_SPORA and RANSOM_SPORA.B), a Russian word for “spore”. Researchers have taken notice of some features that make it a rather polished variant. These messages contain malicious .zip files with HTA files using double extensions, either as PDF.HTA or DOC.HTA, to trick would-be victims into clicking. Once the bait is taken, the ransomware will begin its routine, first by extracting a Javascript file that triggers the extraction of an executable.
Spora is capable of continuing its operations without the need to connect to a C&C server. Far from other variants, it only targets a select number of file types and does not append any extensions to the encrypted files. Following encryption, it drops a ransom note and a .KEY file to the victim’s desktop, which will then be used to synch the machine with the decryption portal.
.png)
Figure 10 Spora ransom note
Written in Russian, the ransom note contains payment instructions and unique user IDs. By uploading the .KEY file, details of the encryption unique to the victim will be displayed.
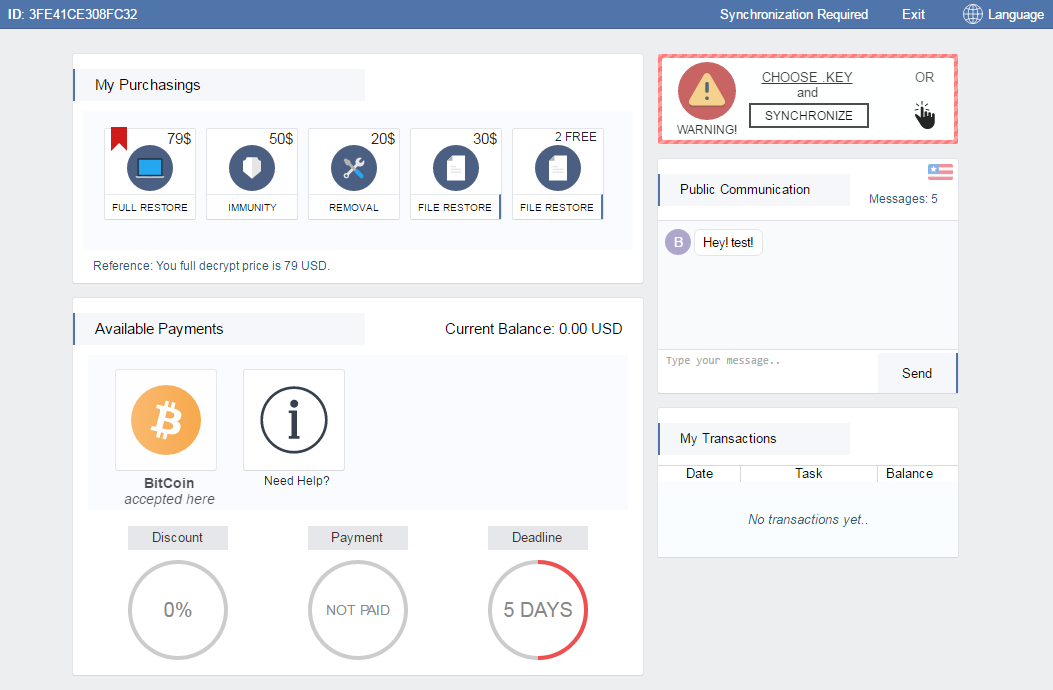
Figure 11 Spora decryption portal dashboard
According to reports, ransom prices range from $79 to $280. A polished dashboard, complete with tips, are made available to cater to the needs of the victim. It has also a chat box, available payments and deadline countdown in days.
Ransomware solutions:
Trend Micro offers different solutions to protect enterprises, small businesses, and home users to help minimize the risk of getting infected by ransomware:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks