Phishing Technique Uses Legitimate-looking Domains to Avoid Detection
By Paul Miguel Babon
 Email threats continued to increase in the time of the pandemic, and the number of phishing URLs rose along with it. Our 2020 mid-year observation on phishing and email threats continue to be true as we close out the year.
Email threats continued to increase in the time of the pandemic, and the number of phishing URLs rose along with it. Our 2020 mid-year observation on phishing and email threats continue to be true as we close out the year.
During our recent tracking efforts, we observed a phishing technique that involves a combination of phishing email and scam pages. This combination comprises an exact URL being the phishing page, and its domain being a scam website.
Behavior
The process starts after a phishing email arrives:
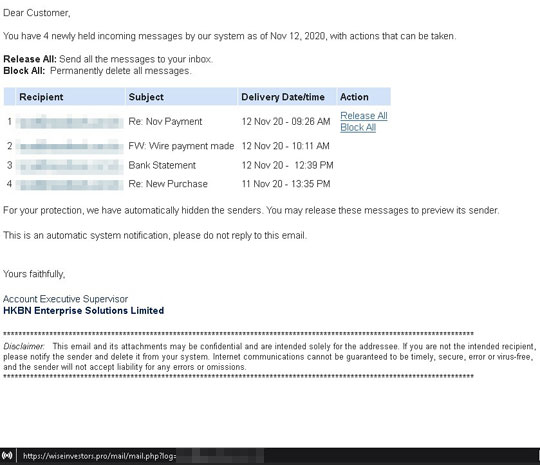
Figure 1. An image of the phishing email that was used
From this email, clicking on the “Release All/Block All” button would direct the user to hxxps://wiseinvestors[.pro]/mail/mail.php?log=, a completely different website unrelated to the email. The content of this link displays a fake login form for an email system:
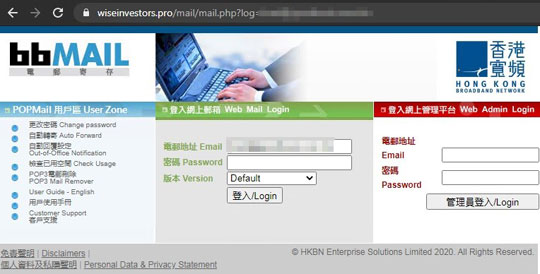
Figure 2. Fake email login page
The preceding screenshots show common practices for most phishing schemes. However, what is notably different from this URL is that the domain itself is also accessible. Accessing the domain hxxps://wiseinvestors[.]pro displays a company page:
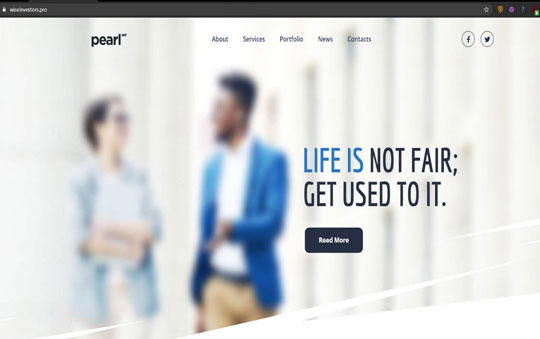
Figure 3. The wiseinvestors[.]pro company page
We determined that this is a fake company based on the following factors:
- Domain Name. The domain name "WiseInvestors" does not match the company brand name it displays, which is "Pearl."" This is because Pearl is a WordPress theme and not a legitimate service.
- Uncommon TLD. The use of .pro, is uncommon for a TLD. Unlike .com, .net, .ph, and the like, uncommon TLDs are usually cheap, which is an advantage for cybercriminals.
- Template Text. Remnants of template text, similar to a “Lorem Ipsum” word block, still exists within the website (Figure 4).
- Domain registration. According to whois records, the domain is less than a year old, which tracks with the age of most malicious domains.

Figure 4. The website text looks unfinished
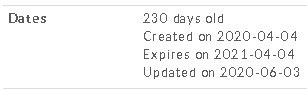
Figure 5. Whois records of wiseinvestors[.]pro
Cybercriminals using this phishing technique are able to avoid real-time detection as the domain needs further scrutiny, which anti-spam and malicious URL-blocking capabilities of common security software can miss. Even if the phishing mail is thwarted, the phishing domain remains undetected, allowing cybercriminals to create more phishing URLs hosted on the domain.
We have seen other examples of this combined phishing-and-scam technique in recent months. Below are some examples:
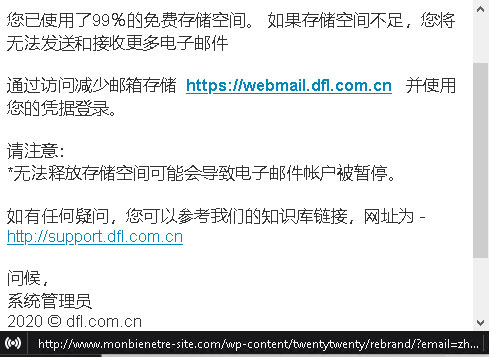
Figure 6. This fake account password notification email in Chinese urges the recipient to click on the link.
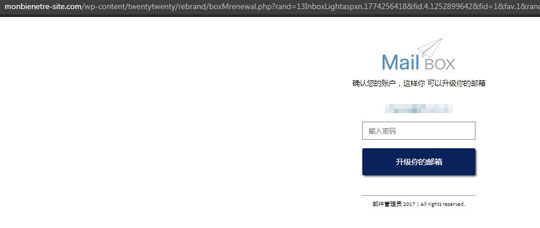
Figure 7. The phishing URL hxxp://webmail[.]dfl[.]com[.]cn leads to a fake login page hosted on hxxp://www[.]monbienetre-site[.]com/wp-content/twentytwenty/rebrand/?{email.}
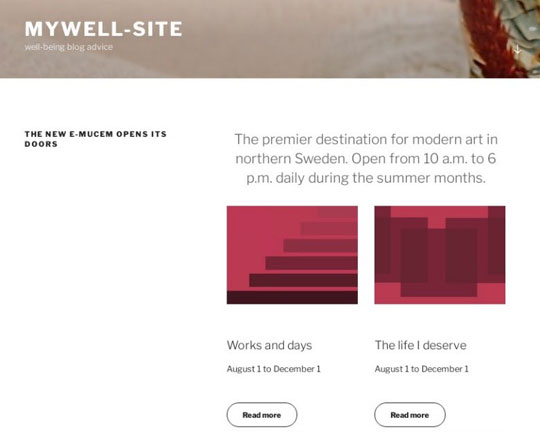
Figure 8. The domain hxxp://www[.]monbienetre-site[.]com poses as a blog site. The scam uses template text. Its content promotes subscriptions at an unusually high price.
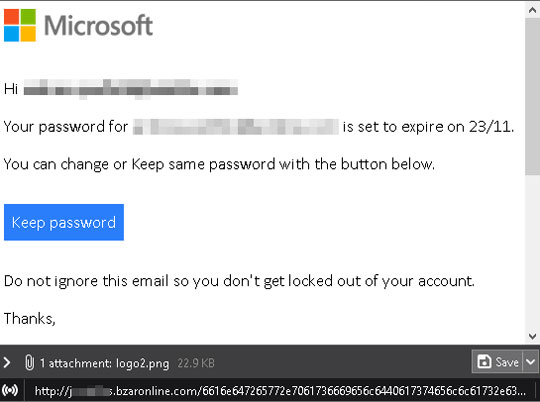
Figure 9. Another fake account password notification email serves as a phishing email. Clicking on "Keep password" will redirect to another page.
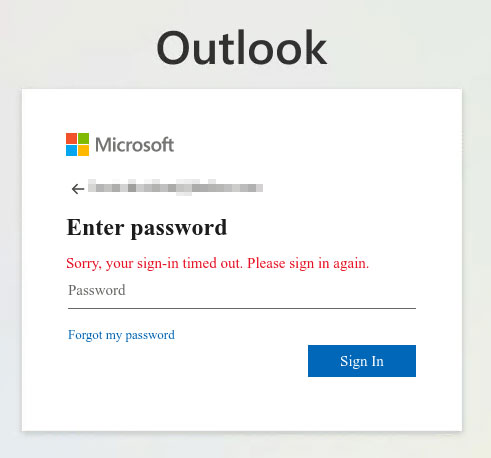
Figure 10. This fake login page is hosted on hxxp://bzaronline[.]com.
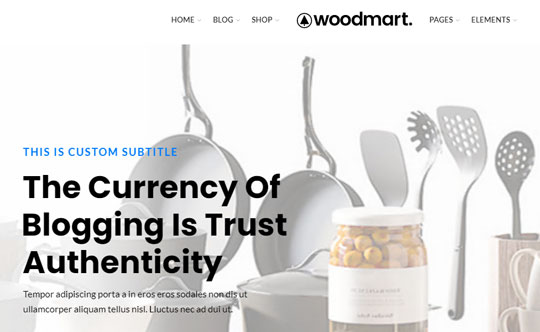
Figure 11. The domain hxxp://bzaronline[.]com displays a template WordPress plugin called WoodMart. Note that WoodMart is legitimate, while the domain is not.
Don't be a victim of phishing and scams
Users can avoid such attacks by following a few best practices before clicking on a link in any email:
- Check the email content properly. Inspect if the information, such as email address, message body, or links, are inconsistent.
- If you click the link from an email, inspect the website. If it seems to display non-malicious content on its home page, it does not mean the website is not malicious. Telltale signs are template texts within the website.
- If you happen to find this on your work computer, alert your security and IT services immediately. They are equipped to inspect further.
For organizations, following security best practices will help minimize the success of similar phishing campaigns. Stopping threats from their initial entry prevents losses. Below are some general security practices to implement:
- Secure email gateways. Secured email gateways thwart threats that are delivered via spam and phishing. They also help users to avoid opening suspicious emails and attachments.
- Regularly back up files.
A multilayered security approach is advised to protect all possible threat entry points. Solutions such as Trend Micro™ Email Security, which uses enhanced machine learning and dynamic sandbox analysis, can stop email threats. Phish Insight provides the most effective phishing simulations and cybersecurity awareness training modules on the market. Powered by Trend Micro, the Phish Insight team creates a simulation template library based on billions of real phishing samples as well as a fully automated and staggered delivery system that makes the simulation emails even more convincing. Not only integrating the best and the most prevalent training modules from around the world, Phish Insight also allows users to customize their own training programs. Phish Insight enhances information security awareness for organizations by empowering people to recognize and protect themselves against the latest cyber threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.

 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks