HDDCryptor/Mamba Ransomware Returns to Encrypt Disk and Network Files
By Angelo Deveraturda (Sr. Threat Response Engineer)
A new variant of HDDCryptor aka Mamba (detected by Trend Micro as Ransom.Win64.MCRYPT.SMB) was uncovered recently. The ransomware has been known to use DiskCryptor to encrypt disk and network files and overwrite the Master Boot Record (MBR). Iterations of the ransomware were previously seen in attacks against the San Francisco Municipal Transport Agency (SFMTA) in 2016 and a number of victims in Brazil and Saudi Arabia in 2017.
Old tricks by HDDCryptor/Mamba still at play
The new HDDCryptor variant was found with a modified DiskCryptor component. However, the ransomware’s core capabilities are still similar to those of previous iterations. Ransom.Win64.MCRYPT.SMB can encrypt resources in network shares, for example, drives, folders, files, printers, and serial ports. It abuses a combination of freeware, open-source, and commercially available software to scramble disks and mounted Server Message Block (SMB) drives. It also locks the victim machine’s hard drive by overwriting the MBR with a modified bootloader.
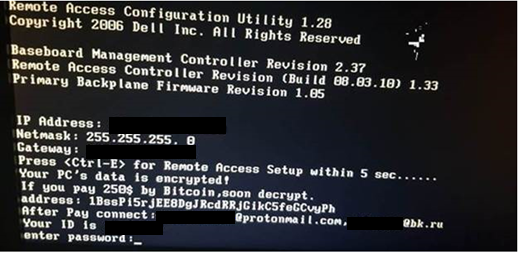
Figure 1. Ransom note of Ransom.Win64.MCRYPT.SMB
Once the infected system reboots, Ransom.Win64.MCRYPT.SMB will display a ransom note that demands US$250 in bitcoins. A look into the variant’s dcapi.dll (API module – main encryptor), a modified DiskCryptor component, reveals the changes in the text of the ransom note of the latest variant from the one in 2016. For example, the contact information provided by the latest variant uses protonmail.com and bk.ru mail clients as opposed to 2016’s yandex.ru.
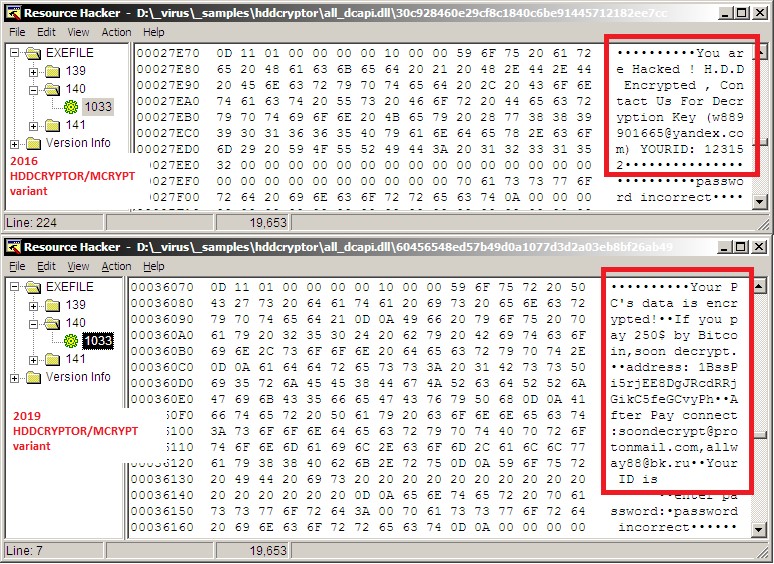 Figure 2. Differences in the ransom note text used by HDDCryptor’s 2016 (top) and 2019 (bottom) variants
Figure 2. Differences in the ransom note text used by HDDCryptor’s 2016 (top) and 2019 (bottom) variants
The modified DiskCryptor executable library component of Ransom.Win64.MCRYPT.SMB also has the same routine and anomaly as those of the 2016 variant. Trend Micro has already deployed several threat hunting rules to actively monitor for other possible variants that will use the same dcapi.dll component with a modified resource.
[Read: WannaCry is still the most detected ransomware family in 2019 1H]
Security recommendations
As evidenced by the HDDCryptor’s reemergence, cybercriminals are still taking advantage of legitimate and open-source tools to go after users and organizations. Such tools may be used to evade detection by traditional security solutions, for example, by not going down the path of obfuscating or encrypting its payload, machine learning and heuristic signature detections will not be triggered. In addition, partially modified tools can confuse detections and can lead to false alarm cases. Such schemes are designed to keep threats, especially the ones used in targeted attacks, stealthy while moving laterally into the network.
Trend Micro™ XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. It infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against advanced malware. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise (IoCs)
|
SHA-256 Hash |
Detection Name |
|
ddda02cbc333b607fdbe4f1b2c4bc10dcc8dde90202cdc531ebf134071a28aaa (dropper)
|
Ransom.Win32.MCRYPT.A |
|
ae74b52c1a580995b9cba3e192db685b4cf1211d2e375591e71b78063f17bbd3 (dcapi.dll)
|
Ransom.Win32.MCRYPT.A |
|
b0b033b6991c2d1dc0a407f699a6eeef7bc6d0dbd9c25278a94383d5b7fb71e4 (dcapi.dll) |
Ransom.Win64.MCRYPT.A |
|
a9d5ca841a883bf301733cbfd21dcd21e7666fe4edaa143b53315289165802fd (dcapi.dll) |
Ransom.Win64.MCRYPT.SMB |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks