A Look at the Threats to Air-Gapped Systems
Air-Gapping is a security measure in which organizations such as the military or utility providers physically disconnect portions of their IT infrastructure from their networks to protect their most critical systems from internet-based attacks . The idea behind air gapping is simple: a physically disconnected device can neither be infected by malware that is propagated via the internet nor can it be affected by command-and-control (C&C) traffic. In theory, air-gapped computers are much more secure than connected systems.
Air-gapped systems typically fall into two categories:
- Critical systems that are disconnected from the rest of the network for security purposes
- Systems that are kept offline due to cost or connectivity issues.
While this entry applies to both situations, it will deal primarily with the first example, as these are the ones that require extra security given their critical nature.
How can attackers possibly infect air-gapped systems?
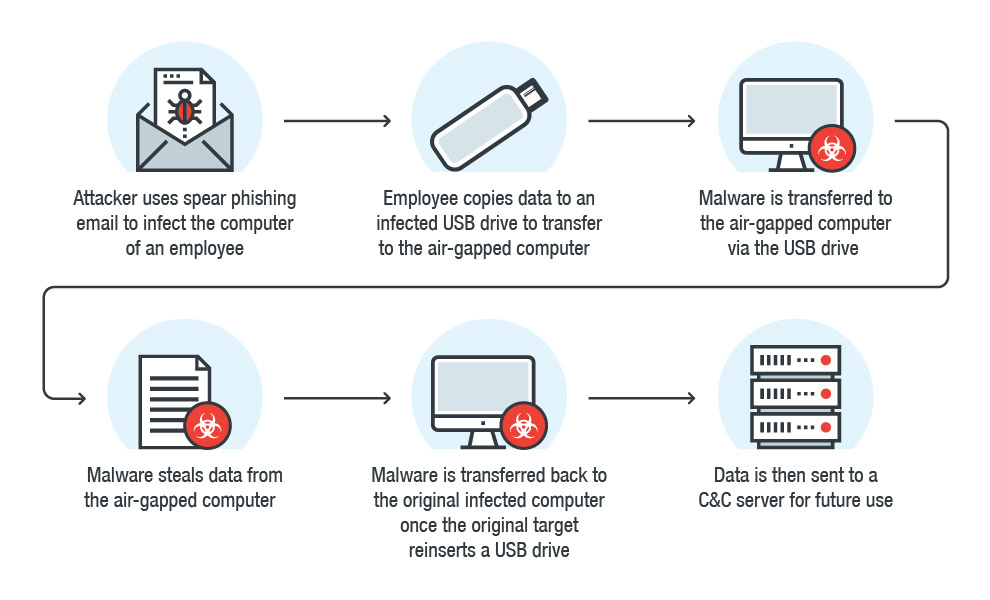 Figure 1: Example of how an air-gapped system can be infiltrated
Figure 1: Example of how an air-gapped system can be infiltratedCompromising an air-gapped system could allow an attacker to steal data from the system via data exfiltration. One example of how this can be accomplished is through the use the use of sound, which has been proven effective for transmitting data—the use of the system’s computer fans and radio frequency emissions from USB connectors are more extreme examples of this. A determined cybercriminal can also use unconventional attack methods to infiltrate air-gapped systems— researchers from Israel's Ben-Gurion University of the Negev and Shamoon College of Engineering demonstrated how this can be done. They created a malware that could “bridge” air-gapped systems via the infrared capabilities of compromised surveillance cameras.
While these kinds of attacks are certainly possible, attacks on air-gapped systems will more likely involve a tactic that has proven to be effective in nearly all kinds of malware attacks: social engineering. By tricking an individual with access to the air-gapped network into inserting a physical drive, an attacker can bypass all the complicated steps needed to pull off an attack successfully.
How IT professionals can secure air-gapped systems
Protecting air-gapped systems involves a multilayered approach to security that starts from the physical setup of the system to the people that interact with it on a regular basis. Here are some strategies that organizations can implement to ensure that their air-gapped systems are secured:
- The top priority for protecting air-gapped systems is to ensure that it is never connected to the internet. Exposure can open up a system to compromise, and given that these systems most likely hold critical information, this can be disastrous.
- Organizations should also ensure that connected peripherals are limited to absolute necessities. USB and CD drives, as well as external hardware like printers, should not be connected to the system, as these have the potential to be avenues of attacks for cybercriminals. USB ports, which are often the most plausible method of infection, can be blocked using simple devices such as USB port locks.
- Given the sensitivity of the data contained within these air-gapped systems, organizations should ensure that this data is encrypted. While this does not prevent data breaches or attacks from occurring, it can prevent cybercriminals from putting the data to use in the event of a successful attack.
- All employees and end users that have access to the air-gapped system should be educated on proper security strategies. Especially important is knowing the different social engineering strategies used in phishing and spear phishing attacks.
While air-gapped systems are certainly more secure by virtue of fewer attack avenues, it doesn’t necessarily mean that these systems are foolproof or that they are automatically safe simply by being disconnected from the network. Organizations that employ these kinds of systems should address all possible gaps in security to ensure that their air-gapped infrastructure is indeed secure.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks