Exploits & Vulnerabilities
ZDI-CAN-25373: Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns
Trend Zero Day Initiative™ (ZDI) uncovered both state-sponsored and cybercriminal groups extensively exploiting ZDI-CAN-25373 (aka ZDI-25-148), a Windows .lnk file vulnerability that enables hidden command execution.
Summary
- Trend Zero Day Initiative™ (ZDI) identified nearly 1,000 malicious .lnk files abusing ZDI-CAN-25373 (aka ZDI-25-148), a vulnerability that allows attackers to execute hidden malicious commands on a victim’s machine by leveraging crafted shortcut files.
- The attacks leverage hidden command line arguments within .lnk files to execute malicious payloads, complicating detection. The exploitation of ZDI-CAN-25373 exposes organizations to significant risks of data theft and cyber espionage.
- The vulnerability has been exploited by state-sponsored APT groups from North Korea, Iran, Russia, and China. Organizations across the government, financial, telecommunications, military, and energy sectors have been affected in North America, Europe, Asia, South America, and Australia.
- Organizations should immediately scan and ensure security mitigations for ZDI-CAN-25373, maintain vigilance against suspicious .lnk files, and ensure comprehensive endpoint and network protection measures are in place to detect and respond to this threat. Trend Micro customers are protected from possible attempts to exploit the vulnerability via rules and filters that were released in October 2024 and January 2025.
The Trend Zero Day Initiative™ (ZDI) threat hunting team identified significant instances of the exploitation of ZDI-CAN-25373 (aka ZDI-25-148) across a variety of campaigns dating back to 2017. Our analysis revealed that 11 state-sponsored groups from North Korea, Iran, Russia, and China have employed ZDI-CAN-25373 in operations primarily motivated by cyber espionage and data theft.
We discovered nearly a thousand Shell Link (.lnk) samples that exploit ZDI-CAN-25373; however, it is probable that the total number of exploitation attempts are much higher. Subsequently, we submitted a proof-of-concept exploit through Trend ZDI's bug bounty program to Microsoft, who declined to address this vulnerability with a security patch.
State-sponsored APT groups exploiting ZDI-CAN-25373 for espionage and data theft
While tracking the exploitation of ZDI-CAN-25373, we discovered the widespread abuse of this vulnerability by numerous threat actors and APT groups. These threats include a mix of state-sponsored as well as non-state-sponsored APT groups. Many of these groups demonstrated a high degree of sophistication in their attack chains and have a history of abusing zero-day vulnerabilities in the wild.
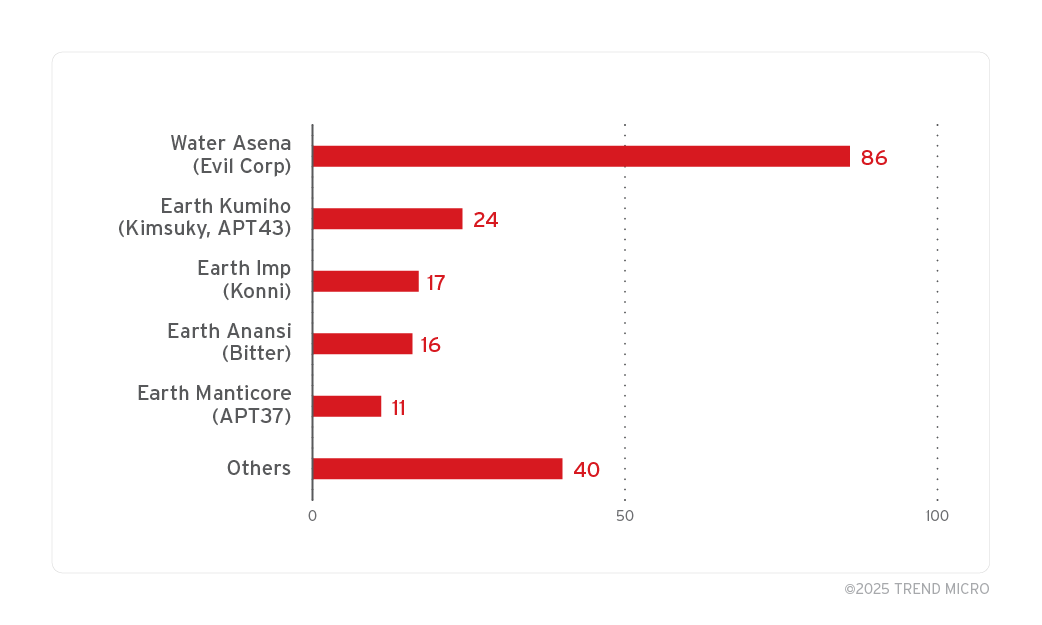
The raw data for Figure 1 may be found here.
The samples shown in Figure 1 have been attributed to APT groups with a high degree of confidence. The Trend ZDI threat hunting team has uncovered hundreds of additional samples that cannot be confidently attributed at this time, but nonetheless exploited ZDI-CAN-25373 in the wild.
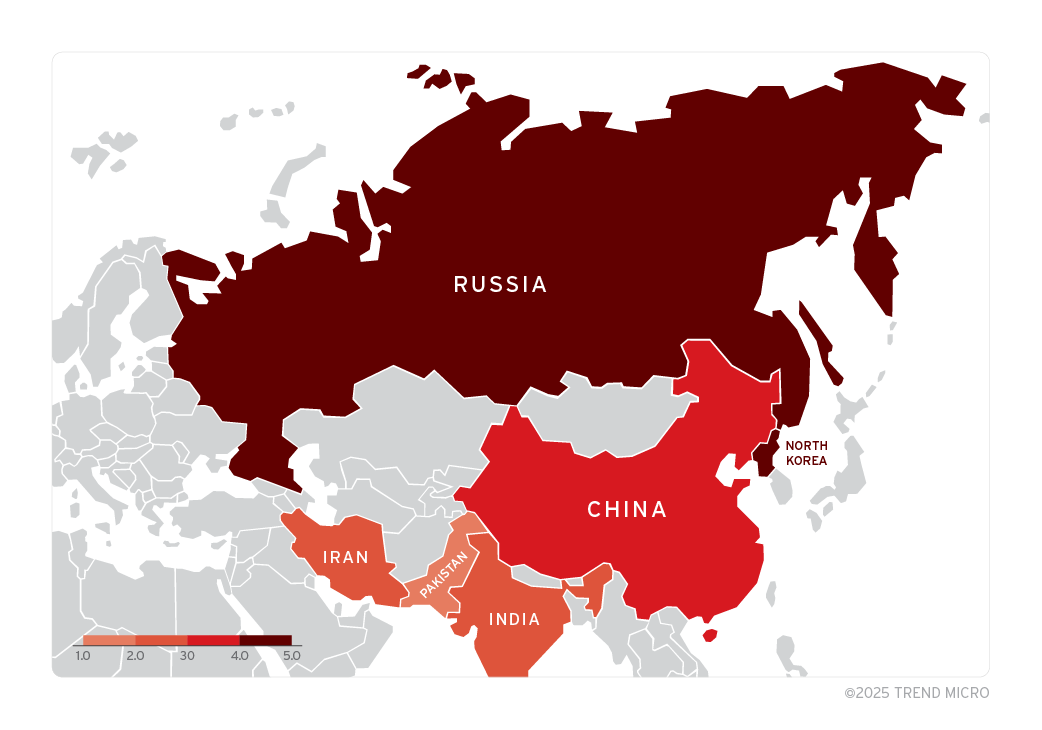
Figure 2 highlights the number of APT groups exploiting ZDI-CAN-25373 as part of their attack chains by country of origin. These APT groups contain a mixture of state-sponsored, state-adjacent, and cybercrime groups. We’ve isolated the state-sponsored APT groups in Figure 3 of these APT groups with known countries of origin.

Nearly half of the state-sponsored threat actors that exploit ZDI-CAN-25373 are reported to originate from North Korea. It is noteworthy that a significant majority of North Korea's intrusion sets have targeted ZDI-CAN-25373 at various times. This observation underscores a trend of cross-collaboration, technique, and tool sharing among different threat groups within North Korea’s cyber program.
In our analysis of the campaigns that exploit ZDI-CAN-25373 and their associated intrusion sets, we have found that nearly 70% are primarily focused on espionage and information theft (Figure 4). In comparison, over 20% are directed toward achieving financial gain. In some instances, threat actors with a primary motivation towards espionage may fund their espionage efforts with financially motivated campaigns.

Targeted sectors and risk
In the campaigns associated with ZDI-CAN-25373 and their corresponding intrusion sets that we monitor, we have identified a substantial volume of telemetry indicating that a diverse range of state-sponsored and cybercriminal threat actors have been targeting multiple sectors (Figure 5).
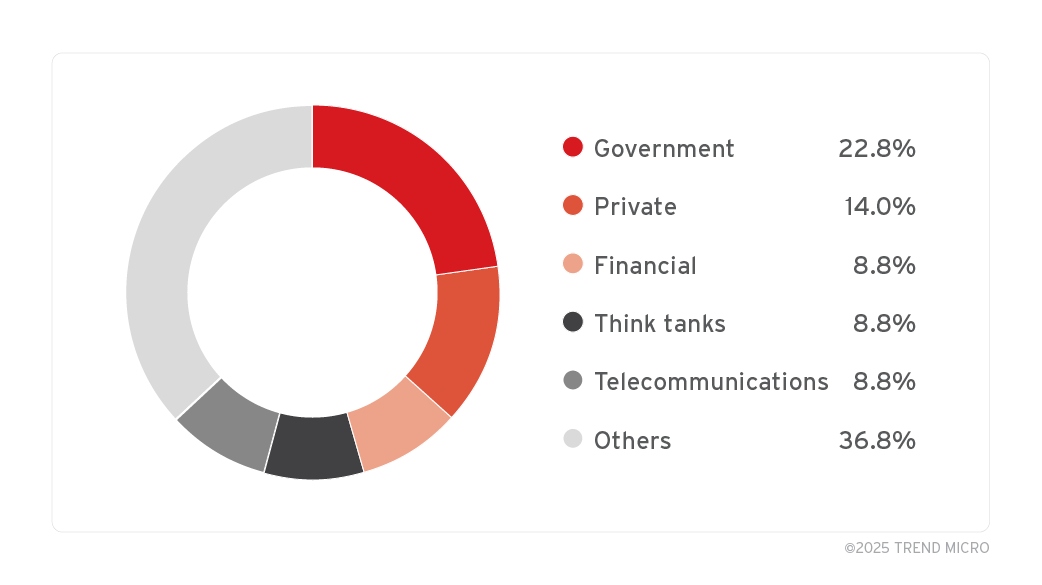
The raw data for Figure 5 may be found here.
In our analysis of the exploitation landscape of ZDI-CAN-25373, we’ve identified the following sectors of particular risk for targeted attacks, including:
- Government
- Private
- Financial, including cryptocurrency-related
- Think tanks, including non-governmental organizations (NGOs)
- Telecommunications
- Military and defense
- Energy
Organizations that fall within these sectors are at higher risk for exploitation and should scan and ensure security mitigations for ZDI-CAN-25373 immediately, as well as remain vigilant of .lnk files in general. Additionally, organizations are encouraged to investigate potential compromise or attempts to compromise systems use ZDI-CAN-25373 as an intrusion vector. as an intrusion vector.
Exploring malware payloads
Of the .lnk files exploiting ZDI-CAN-25373 and campaigns we tracked, we were able to recover some of the malware payloads or correlate them through Trend Micro threat telemetry. This highlights the diverse use of various malware payloads and loaders in campaigns exploiting ZDI-CAN-25373.
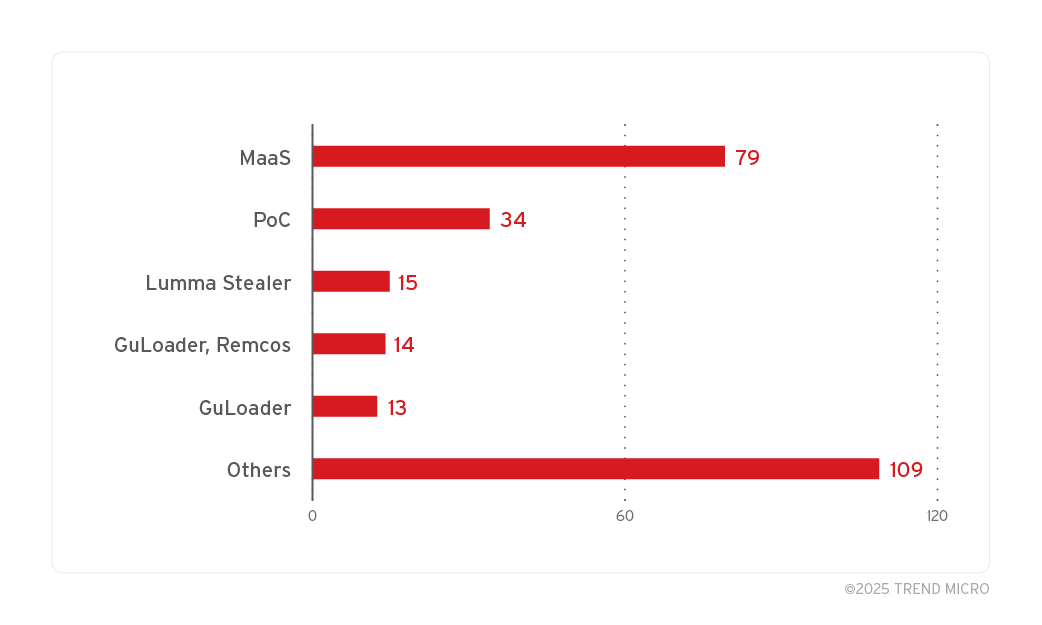
The raw data for Figure 6 may be found here.
In Figure 6, for samples shown under “Malware-as-a-Service” (MaaS), we were not able to recover the specific malware payload used, but the observed origin domains commonly served MaaS and commodity malware payloads. The “PoC” row denotes proof-of-concept samples retrieved. These were likely used during the attack chain development lifecycle. An interesting observation we discovered while tracking these intrusion sets, and malware was that Water Asena (Evil Corp) had been exploiting ZDI-CAN-25373 in their Raspberry Robin campaigns.
Victimology
Of the samples we analyzed, a majority were submitted from North America, including the US and Canada. However, due to the number of APT groups exploiting ZDI-CAN-25373, the victimology is much broader, also affecting Europe, Asia, South America, Africa and Australia (Figure 7).

The raw data for Figure 7 may be found here.
When placed on a map as shown in Figure 8, we can see that the exploitation of ZDI-CAN-25373 is widespread, with a focus on North America, South America, Europe, East Asia and Australia. It’s important to note that the scope of impact is likely much larger, as Figure 8 shows only samples the Trend ZDI threat hunting team was able to recover.
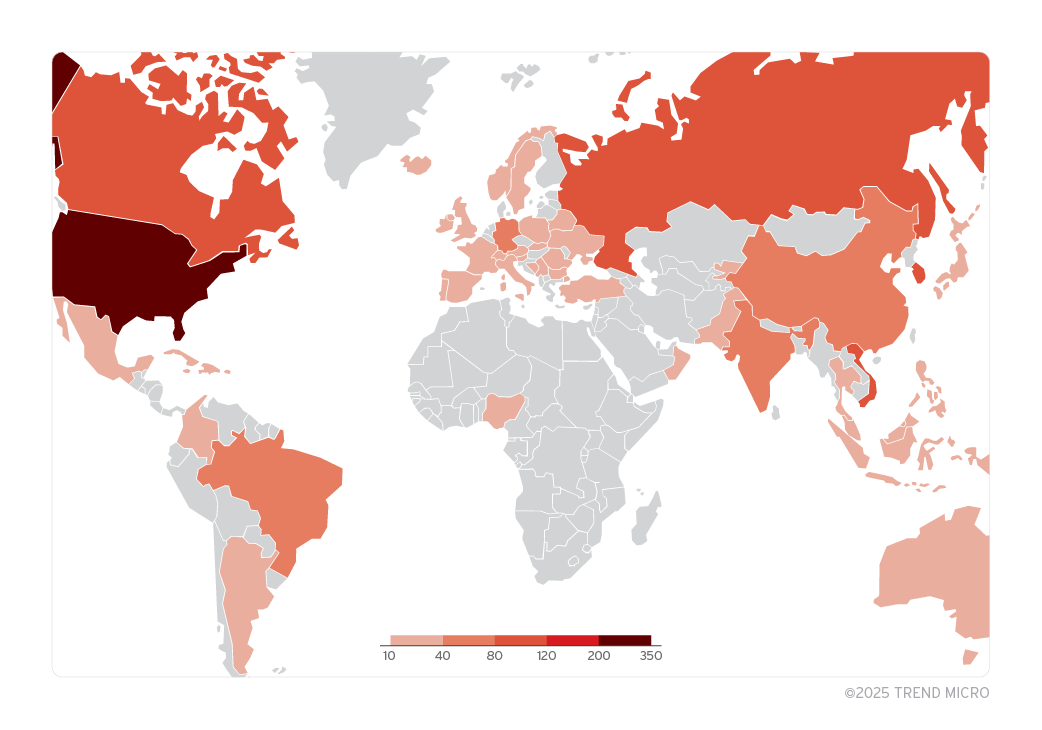
The raw data for Figure 8 may be found here.
Technical details
ZDI-CAN-25373 relates to the way Windows displays the contents of shortcut (.lnk) files through the Windows UI. By exploiting this vulnerability, an attacker can prepare a malicious .lnk file for delivery to a victim. Upon examining the file using the Windows-provided user interface, the victim will not be able to tell that the file contains any malicious content. The sections below explain the vulnerability in further detail.
MS-SHLLINK (.lnk) file format
A Windows Shortcut file, also known a Shell Link file (.lnk), is a type of binary file used by the Windows operating system to act as a shortcut to a file, folder or applications. This file type is popular with threat actors due to the fact that command line arguments can be embedded inside the .lnk files Target field, which can lead to code execution on the victim machine. This section will cover the basics of the Windows Shortcut (MS-SHLLINK) binary format as they relate to understanding the exploitation of ZDI-CAN-25373.
ShellLinkHeader
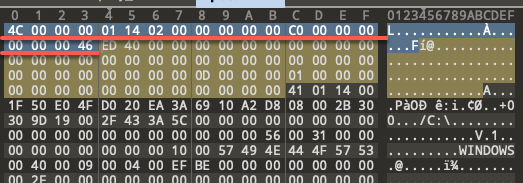
Every .lnk file starts with the ShellLinkHeader structure. Within ShellLinkHeader, there are two mandatory fields that contain the same values across every .lnk file (Table 1). These are the fields HeaderSize and LinkCLSID (Figure 9). These two fields can be used as magic bytes to determine whether or not a file is a .lnk file.
| Field | Value |
| HeaderSize (4 bytes, offset 0x0000) | 0x0000004C |
| LinkCLSID (16 bytes, offset 0x0004) | 00021401-0000-0000- C000-000000000046 |
Table 1. Mandatory fields in the ShellLinkHeader structure
LinkFlags
The LinkFlags structure appears after the HeaderSize and LinkCLSID. It contains flags specifying which structures are additionally present in the .lnk file. Of special importance is the HasArguments flag. When this flag is set, the .lnk will contain a COMMAND_LINE_ARGUMENTS structure (Figure 10). As part of the .lnk binary format, additional COMMAND_LINE_ARGUMENTS may be passed to the .lnk file’s Target. In a malicious .lnk file, these may be additional command line parameters to download and install malicious payloads through cmd.exe, powershell.exe, or other LOLbin binaries. This is often abused by threat actors who use .lnk files as part of their attack chains and is present in the exploitation of ZDI-CAN-25373.

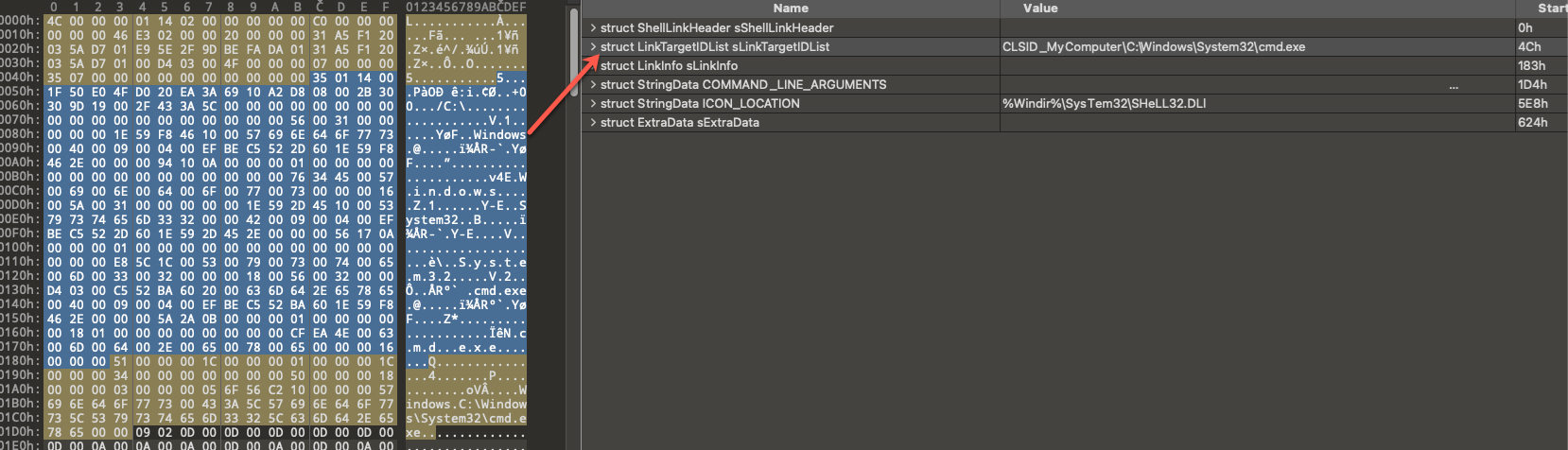
LinkTargetIDList
This structure contains the target of the .lnk file, as shown in Figure 11. When this structure is used, the HasLinkTargetIDList flag will be set in the LinkFlags section.
COMMAND_LINE_ARGUMENTS
When the HasArguments flag is set in the LinksFlags structure, the COMMAND_LINE_ARGUMENTS structure will be present. This structure stores command line arguments that will be passed to the specified target is when the shortcut is activated (Figure 12). This is often used in .lnk file-based attacks for code execution.
ICON_LOCATION
Threat actors also commonly abuse the ICON_LOCATION structure to control what icon is displayed by the .lnk file, as shown in Figure 13.
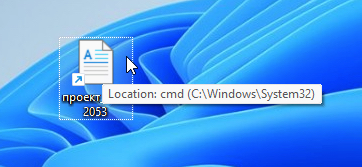
In attack campaigns that utilize .lnk files, threat actors will often change the icon to confuse and entice the victim into executing the shortcut. Since Windows always suppresses display of the .lnk extension, threat actors will often add a “spoof” extension such as .pdf.lnk along with a matching icon to further trick users. A .lnk file will usually have an arrow on the lower-left side of the icon.
Vulnerability details
To exploit ZDI-CAN-25373, the threat actors carefully crafted .lnk files with padded whitespace characters within the COMMAND_LINE_ARGUMENTS structure (Table 2).
| Hex Value | Output |
| \x20 | Space |
| \x09 | Horizontal Tab |
| \x0A | Line Feed |
| \x0B | Vertical Tab |
| \x0C | Form Feed |
| \x0D | Carriage Return |
Table 2. Whitespace characters used to exploit ZDI-CAN-25373
If a user inspects a .lnk file containing this malicious padding, Windows will not be able to show the malicious arguments within the allotted space in the user interface (Figure 14). The impact of this exploit is that the command line arguments that will be executed by the .lnk file are completely hidden from the user’s view.

To inspect the Target field of samples exploiting ZDI-CAN-25373 and the contents of the COMMAND_LINE_ARGUMENTS structure, third-party tools are required.

When viewing a sample using a hex editor, one can observe large numbers of Space (\x20) characters within the COMMAND_LINE_ARGUMENTS structure (Figure 16).

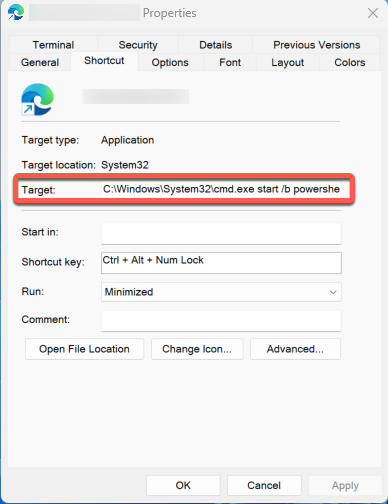
We made an interesting observation in cases where the threat actor padded the COMMAND_LINE_ARGUMENTS with Line Feed (\x0A) and Carriage Return (\x0D) characters. In this instance, when inspecting the properties of the .lnk file, only a single highlightable character in the Target field is shown (Figure 17).

During our analysis, we discovered that some North Korean threat actors, such as Earth Manticore (APT37) and Earth Imp (Konni), tended to use extremely large .lnk files with large amounts of whitespace and other junk content to further evade detection. Earth Imp used files with a median size of 3.32MB, with a maximum file size of 70.1MB. Earth Manticore used files with a median size of 33.33MB, with a maximum file size of 55.16MB.
ZDI-CAN-25373 is an example of (User Interface (UI) Misrepresentation of Critical Information (CWE-451). This means that the Windows UI failed to present the user with critical information. Similar to a previous discovery we made, it is a failure to properly represent security-critical information to the user. By exploiting ZDI-CAN-25373, the threat actor can prevent the end user from viewing critical information (commands being executed) related to evaluating the risk level of the file.
Conclusion
The threat posed by APTs originating from nation-states, as well as from sophisticated cybercriminals, poses a significant risk to the confidentiality, integrity, and availability of data maintained by governments, critical infrastructure, and private organizations globally. Among the 11 state-sponsored APT groups leveraging ZDI-CAN-25373, a majority have a documented history of exploiting zero-day vulnerabilities in attacks in the wild. These vulnerabilities present substantial risks, as they target flaws that remain unknown to software vendors and lack corresponding security patches, thereby leaving governments and organizations vulnerable to exploitation. As geopolitical tensions and conflicts escalate, an increase in the sophistication of threat actors and the utilization of zero-day vulnerabilities is anticipated to rise, as both nation-states and cybercriminals endeavor to gain a competitive advantage over their adversaries. This growing prevalence of zero-day exploitation necessitates the implementation of comprehensive security solutions to safeguard critical assets and industries effectively. This vulnerability was disclosed to Microsoft via Trend ZDI's bug bounty program; Microsoft classified this as low severity and this will not be patched in the immediate future.
To make software more secure and protect customers from zero-day attacks, Trend ZDI works with security researchers and vendors to patch and responsibly disclose software vulnerabilities before APT groups can deploy them in attacks. The Trend ZDI threat hunting team also proactively hunts for zero-day attacks in the wild to safeguard the industry.
Proactive security with Trend Vision One™
Organizations can protect themselves from attacks such as those employed by APT groups with Trend Vision One™ – the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry's first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
When faced with uncertain intrusions, behaviors, and routines, organizations should assume that their system is already compromised or breached and work to immediately isolate affected data or toolchains. With a broader perspective and rapid response, organizations can address breaches and protect its remaining systems, especially with robust Endpoint and Network Security solutions. The platform’s security operations capabilities stop adversaries with unrivalled visibility—enriched by native sensors and third-party telemetry. Detect, investigate, and respond proactively with the power of security operations, SIEM, and SOAR. Leaving attackers with no place left to hide.
Trend protections for ZDI-CAN-25373
The following protections have been available to Trend Micro customers:
Trend Vision One™ - Network Security
- TippingPoint Intrusion Prevention Filter: 44844 - HTTP: Microsoft Windows LNK File UI Misrepresentation Vulnerability (ZDI-25-148)
The following Network Security protections will be officially made available on March 25:
- Deep Discovery Inspector (DDI) Relevance Rule: 5351 - Microsoft Windows LNK File UI Misrepresentation Remote Code Execution Exploit (ZDI-25-148) - HTTP(RESPONSE)
- Trend Vision One™ XDR for Networks OAT Entry: 5351 - Microsoft Windows LNK File UI Misrepresentation Remote Code Execution Exploit (ZDI-25-148) - HTTP(Response)
Trend Vision One™ – Endpoint Security, Trend Micro™ Deep Security™
- 1012182 - Microsoft Windows LNK File UI Misrepresentation Vulnerability Over HTTP (ZDI-25-148)
- 1012183 - Microsoft Windows LNK File UI Misrepresentation Vulnerability Over SMB (ZDI-25-148)
More Trend rules and filters can be found here.
Trend Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Vision One customers can access a range of Intelligence Reports and Threat Insights. Threat Insights helps customers stay ahead of cyber threats before they happen and allows them to prepare for emerging threats by offering comprehensive information on threat actors, their malicious activities, and their techniques. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and effectively respond to threats.
Trend Vision One Intelligence Reports App [IOC Sweeping]
- ZDI-CAN-25373: Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns
Trend Vision One Threat Insights App
- Threat Actors: Water Glashtyn, Earth Iktomi, Water Poukai, Water Cetus, Earth Balayang, Fire Tengu, Earth Imp, Water Asena, Earth Akurra, Earth GelertEarth Iktomi, Water Poukai, Water Cetus, Earth Balayang, Fire Tengu, Earth Imp, Water Asena, Earth Akurra, Earth Anansi, Earth Gelert, Earth Vetala, Earth Kapre, Earth Preta, Earth Tengshe, Earth Lusca
- Emerging Threats: ZDI-CAN-25373: Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Detect suspicious cmd.exe or powershell.exe execution from LNK files
eventSubId:2 AND (processFilePath:\"*\\cmd.exe\" OR processFilePath:\"*\\powershell.exe\") AND parentFilePath:\"*.lnk\"
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Yara Threat Hunting Rule
Use this YARA rule to find files exploiting ZDI-CAN-25373:
rule ZTH_LNK_EXPLOIT_A
{
meta:
author = "Peter Girnus"
description = "This YARA file detects padded LNK files designed to exploit ZDI-CAN-25373."
reference = "https://www.trendmicro.com/en_us/research/25/c/windows-shortcut-zero-day-exploit.html"
target_entity = "file"
strings:
$magic = {4C 00 00 00 01 14 02 00}
$spoof_a = {20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00}
$spoof_b = {09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00}
$spoof_c = {0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00}
$spoof_d = {0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00}
$spoof_e = {11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00}
$spoof_f = {12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00}
$spoof_g = {13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00}
$spoof_h = {0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00}
condition:
$magic at 0x00 and ($spoof_a or $spoof_b or $spoof_c or $spoof_d or $spoof_e or $spoof_f or $spoof_g or $spoof_h)
}
Indicators of compromise
The indicators of compromise for this entry can be found here.

