TROJ_KAZY.SMT
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
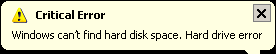
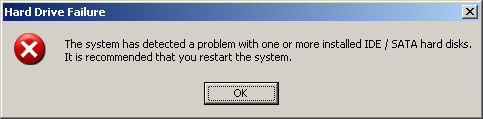
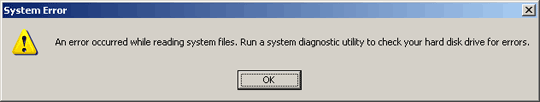
This Trojan sets the attributes of all folders and files in the system to Hidden. It also changes the desktop wallpaper to black. Certain error messages prompts the user that an error is detected and will reboot the machine. These behaviors makes the user think that the system has errors.
This Trojan adds certain registry entries to disable the Task Manager. This action prevents users from terminating the malware process, which can usually be done via the Task Manager.
It connects to certain URLs. It may do this to remotely inform a malicious user of its installation. It may also do this to download possibly malicious files onto the computer, which puts the computer at a greater risk of infection by other threats. As of this writing, the said sites are inaccessible.
It terminates itself if it detects it is being run in a virtual environment. It deletes the initially executed copy of itself.
It displays fake alerts that warn users of infection. It also displays fake scanning results of the affected system. It then asks for users to purchase it once scanning is completed. If users decide to purchase the rogue product, users are directed to a certain website asking for sensitive information, such as credit card numbers.
TECHNICAL DETAILS
477,184 bytes
EXE
Yes
15 Jun 2011
Displays windows, Downloads files
Installation
This Trojan drops the following copies of itself into the affected system:
- %System Root%\All Users\Application Data\{random file name 1}.exe - (XP, 2000, 2003)
- %System Root%\All Users\Application Data\{random file name 2}.exe - (XP, 2000, 2003)
- %System Root%\ProgramData\{random file name 1}.exe - (Vista, 2008, 7)
- %System Root%\ProgramData\{random file name 2}.exe - (Vista, 2008, 7)
- %System Root%\Users\All Users\{random file name 1}.exe - (Vista, 2008, 7)
- %System Root%\Users\All Users\{random file name 2}.exe - (Vista, 2008, 7)
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.)
It drops the following non-malicious files:
- %System Root%\All Users\Application Data\{random file name 2}
- %System Root%\ProgramData\{random file name 2}
- %System Root%\Users\All Users\{random file name 2}
- %Desktop%\{OS Name} Restore.lnk
- %Start Menu%\Programs\{OS Name} Restore\{OS Name} Restore.lnk
- %Start Menu%\Programs\{OS Name} Restore\Uninstall {OS Name} Restore.lnk
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.. %Desktop% is the desktop folder, where it usually is C:\Documents and Settings\{user name}\Desktop in Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\Desktop in Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.. %Start Menu% is the Start Menu folder, where it usually is C:\Documents and Settings\{user name}\Start Menu on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\AppData\Roaming\Microsoft\Windows\Start Menu on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
It creates the following folders:
- %User Temp%\smtmp
- %User Temp%\smtmp\1
- %User Temp%\smtmp\2
- %User Temp%\smtmp\3
- %User Temp%\smtmp\4
- %Start Menu%\Programs\{OS Name} Restore
(Note: %User Temp% is the user's temporary folder, where it usually is C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\AppData\Local\Temp on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.. %Start Menu% is the Start Menu folder, where it usually is C:\Documents and Settings\{user name}\Start Menu on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\AppData\Roaming\Microsoft\Windows\Start Menu on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- 83a5f83b-5aa7-4fa7-bbf5-63829add296e
- 86e8a495-357c-437c-b6e9-13e757bfabab
Autostart Technique
This Trojan adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
{malware file name} = "{malware path and file name}"
Other System Modifications
This Trojan adds the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Attachments
SaveZoneInformation = "1"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Associations
LowRiskFileTypes = "/{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
ActiveDesktop
NoChangingWallPaper = "1"
It modifies the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
StartPage
Favorites = "FF"
(Note: The default value data of the said registry entry is {binary data which contains the pinned programs in the Start Menu, cannot be restored}.)
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\Download
CheckExeSignatures = "no"
(Note: The default value data of the said registry entry is yes.)
It adds the following registry entries to disable the Task Manager:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
System
DisableTaskMgr = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\policies\
system
DisableTaskMgr = "1"
It modifies the following registry entries to hide files with Hidden attributes:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
Advanced
Hidden = "0"
(Note: The default value data of the said registry entry is 1.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
Advanced
ShowSuperHidden = "0"
(Note: The default value data of the said registry entry is 1.)
File Infection
This Trojan adds the following registry entries that act as infection markers:
HKEY_CURRENT_USER\Software
75fa38b7-8b94-4995-ad32-52e938867954 = {blank}
Process Termination
This Trojan terminates the following processes if found running in the affected system's memory:
- MSASCui.exe
Download Routine
This Trojan connects to the following malicious URLs:
- http://{BLOCKED}also.org/404.php?type=stats&affid=431&subid=01
- http://{BLOCKED}attention.org/404.php?type=stats&affid=431&subid=01
- http://{BLOCKED}behavior.org/404.php?type=stats&affid=431&subid=01
- http://{BLOCKED}ant.org/404.php?type=stats&affid=431&subid=01
It accesses the following websites to download files:
- http://{BLOCKED}breathe.org/pica1/431-direct
- http://{BLOCKED}oa.org/pica1/431-direct
It saves the files it downloads using the following names:
- %User Temp%\Adobe_Flash_Player.exe
(Note: %User Temp% is the user's temporary folder, where it usually is C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\AppData\Local\Temp on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
As of this writing, the said sites are inaccessible.
Other Details
This Trojan terminates itself if it detects it is being run in a virtual environment.
It deletes the initially executed copy of itself
Rogue Antivirus Routine
This Trojan displays fake alerts that warn users of infection. It also displays fake scanning results of the affected system. It then asks for users to purchase it once scanning is completed. If users decide to purchase the rogue product, users are directed to a certain website asking for sensitive information, such as credit card numbers.
NOTES:
It is a rogue application disguising itself as a system checker. It purportedly checks the system's hard drives, memory, and settings to improve performance and fix errors. It uses the following name format for its user interface:
- {OS Name} Restore
It terminates and deletes itself if the language of the affected system is any of the following:
- Czech
- Polish
- Russian
- Ukrainian
The malware restores its system modifications if any of the following files exists in the system:
- %System Root%\Documents and Settings\All Users\Application Data\*EDS.txt
- %System Root%\ProgramData\*EDS.txt
- %User Profile%\Desktop\*EDS.txt
This malware can display its fake alerts in any of the following languages:
- English
- French
- German
- Italian
- Russian
- Spanish
- Turkish
If the operating system major version is 5 (XP, 2000, 2003), the malware creates the following registry entry to hide desktop icons:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
NoDesktop = "1"
If the operating system major version is 6 (Vista, 2008, 7), the malware creates the following registry entries to hide desktop icons, recently opened files list, and recently opened programs list:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
{20D04FE0-3AEA-1069-A2D8-08002B30309D} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
{5399E694-6CE5-4D6C-8FCE-1D8870FDCBA0} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
{59031a47-3f72-44a7-89c5-5595fe6b30ee} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
{645FF040-5081-101B-9F08-00AA002F954E} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
{F02C1A0D-BE21-4350-88B0-7367FC96EF3C} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
{20D04FE0-3AEA-1069-A2D8-08002B30309D} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
{5399E694-6CE5-4D6C-8FCE-1D8870FDCBA0} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
{59031a47-3f72-44a7-89c5-5595fe6b30ee} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
{645FF040-5081-101B-9F08-00AA002F954E} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
{F02C1A0D-BE21-4350-88B0-7367FC96EF3C} = "1"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
Start_TrackDocs = "0"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
Start_TrackProgs = "0"
This malware moves specific files in the following directories:
Operating System major version is 5 (XP, 2000, 2003):
- From: %System Root%\Documents and Settings\All Users\Start Menu\
- To: %User Temp%\smtmp\1\
- From: %User Profile%\Application Data\Microsoft\Internet Explorer\Quick Launch\
- To: %User Temp%\smtmp\2\
- From: %System Root%\Documents and Settings\All Users\Desktop\
- To: %User Temp%\smtmp\4\
Operating System major version is 6 (Vista, 2008, 7)
- From: %System Root%\ProgramData\Start Menu\
- To: %User Temp%\smtmp\1\
- From: %User Profile%\Application Data\Roaming\Microsoft\Internet Explorer\Quick Launch\
- To: %User Temp%\smtmp\2\
- From: %User Profile%\Application Data\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\
- To: %User Temp%\smtmp\3\
- From: %System Root%\ProgramData\Desktop\
- To: %User Temp%\smtmp\4\
It then sets the attributes of all folders and files in the system to Hidden. It also changes the desktop wallpaper to black. Certain error messages prompts the user that an error is detected and will reboot the machine. These behaviors make the user think that the system has errors.
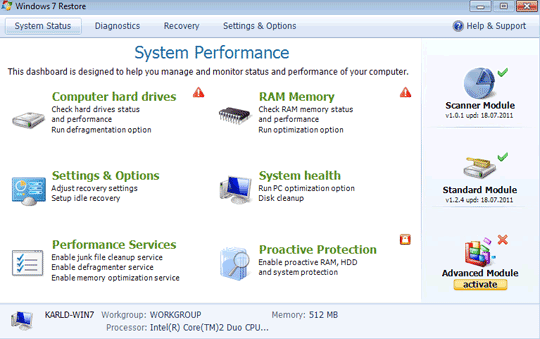
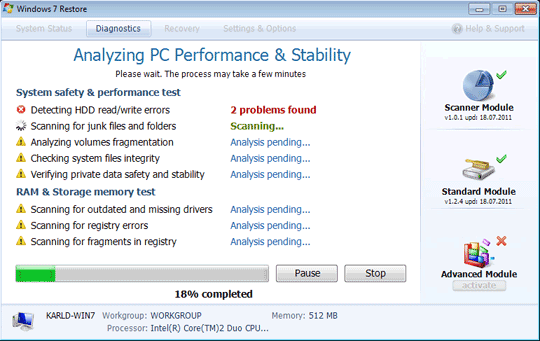
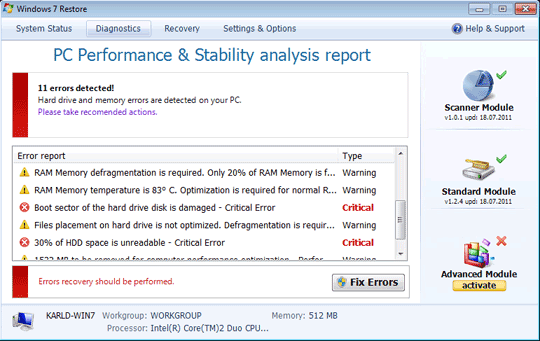
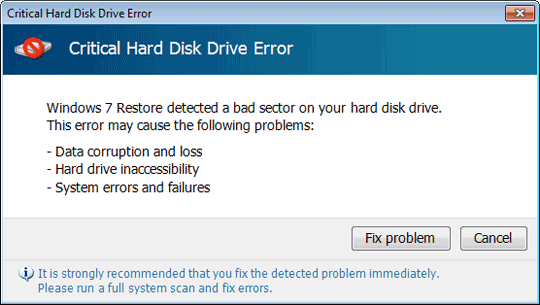
SOLUTION
8.900
8.226.05
15 Jun 2011
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Identify and terminate files detected as TROJ_KAZY.SMT
- Windows Task Manager may not display all running processes. In this case, please use a third-party process viewer, preferably Process Explorer, to terminate the malware/grayware/spyware file. You may download the said tool here.
- If the detected file is displayed in either Windows Task Manager or Process Explorer but you cannot delete it, restart your computer in safe mode. To do this, refer to this link for the complete steps.
- If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps.
Step 3
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- {malware file name} = "{malware path and file name}"
- {malware file name} = "{malware path and file name}"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments
- SaveZoneInformation = "1"
- SaveZoneInformation = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
- LowRiskFileTypes = "/{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq"
- LowRiskFileTypes = "/{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop
- NoChangingWallPaper = "1"
- NoChangingWallPaper = "1"
- In HKEY_CURRENT_USER\Software
- 75fa38b7-8b94-4995-ad32-52e938867954 = {blank}
- 75fa38b7-8b94-4995-ad32-52e938867954 = {blank}
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System
- DisableTaskMgr = "1"
- DisableTaskMgr = "1"
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
- DisableTaskMgr = "1"
- DisableTaskMgr = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- NoDesktop = "1"
- NoDesktop = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {20D04FE0-3AEA-1069-A2D8-08002B30309D} = "1"
- {20D04FE0-3AEA-1069-A2D8-08002B30309D} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {5399E694-6CE5-4D6C-8FCE-1D8870FDCBA0} = "1"
- {5399E694-6CE5-4D6C-8FCE-1D8870FDCBA0} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {59031a47-3f72-44a7-89c5-5595fe6b30ee} = "1"
- {59031a47-3f72-44a7-89c5-5595fe6b30ee} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {645FF040-5081-101B-9F08-00AA002F954E} = "1"
- {645FF040-5081-101B-9F08-00AA002F954E} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {F02C1A0D-BE21-4350-88B0-7367FC96EF3C} = "1"
- {F02C1A0D-BE21-4350-88B0-7367FC96EF3C} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
- {20D04FE0-3AEA-1069-A2D8-08002B30309D} = "1"
- {20D04FE0-3AEA-1069-A2D8-08002B30309D} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
- {5399E694-6CE5-4D6C-8FCE-1D8870FDCBA0} = "1"
- {5399E694-6CE5-4D6C-8FCE-1D8870FDCBA0} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
- {59031a47-3f72-44a7-89c5-5595fe6b30ee} = "1"
- {59031a47-3f72-44a7-89c5-5595fe6b30ee} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
- {645FF040-5081-101B-9F08-00AA002F954E} = "1"
- {645FF040-5081-101B-9F08-00AA002F954E} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
- {F02C1A0D-BE21-4350-88B0-7367FC96EF3C} = "1"
- {F02C1A0D-BE21-4350-88B0-7367FC96EF3C} = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- Start_TrackDocs = "0"
- Start_TrackDocs = "0"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- Start_TrackProgs = "0"
- Start_TrackProgs = "0"
Step 4
Restore this modified registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download
- From: CheckExeSignatures = "no"
To: CheckExeSignatures = "yes"
- From: CheckExeSignatures = "no"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- From: Hidden = "0"
To: Hidden = "1"
- From: Hidden = "0"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- From: ShowSuperHidden = "0"
To: ShowSuperHidden = "1"
- From: ShowSuperHidden = "0"
Step 5
Search and delete this folder
- %Start Menu%\Programs\{OS Name} Restore
Step 6
Search and delete these components
- %System Root%\All Users\Application Data\{random file name 2}
- %System Root%\ProgramData\{random file name 2}
- %System Root%\Users\All Users\{random file name 2}
- %Desktop%\{OS Name} Restore.lnk
- %User Temp%\Adobe_Flash_Player.exe
Step 7
Reset your Desktop properties
Step 8
Scan your computer with your Trend Micro product to delete files detected as TROJ_KAZY.SMT. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
NOTES:
To unhide the files hidden by this malware, perform the following steps:
1. Open a Command Prompt.
For Windows 2000, Windows XP, and Windows Server 2003 users:
Click Start > Run, type CMD in the text box provided, and then press Enter.
For Windows Vista and Windows 7 users:
Click the Start button, type CMD in the Search input field then press Enter.
2. For every drive in the computer, type the following command:
- attrib -h {drive letter}:\*.* /s /d
3. Close Command Prompt. Type exit then press Enter.
To Restore Files to its Original Location:
Open %User Temp%\smtmp and copy the files as follows:
If operating system major version is 5 (XP, 2000, 2003):
From: %User Temp%\smtmp\1\
To: %System Root%\Documents and Settings\All Users\Start Menu\
From: %User Temp%\smtmp\2\
To: %User Profile%\Application Data\Microsoft\Internet Explorer\Quick Launch\
From: %User Temp%\smtmp\4\
To: %System Root%\Documents and Settings\All Users\Desktop\
If operating system major version is 6 (Vista, 2008, 7)
From: %User Temp%\smtmp\1\
To: %System Root%\ProgramData\Start Menu\
From: %User Temp%\smtmp\2\
To: %User Profile%\Application Data\Roaming\Microsoft\Internet Explorer\Quick Launch\
From: %User Temp%\smtmp\3\
To: %User Profile%\Application Data\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\
From: %User Temp%\smtmp\4\
To: %System Root%\ProgramData\Desktop\
After moving the files, delete the folder %User Temp%\smtmp.
Did this description help? Tell us how we did.

