Ransom.Win32.MIMIC.D
Ransom:Win32/Mimic.MA!MTB (MICROSOFT)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It does not have any propagation routine.
It does not have any backdoor routine.
It gathers certain information on the affected computer.
It drops files as ransom note. It avoids encrypting files with the following file extensions.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following files:
- %User Temp%\7ZipSfx.000\7za.exe → legitimate 7zip application, deleted afterwards
- %User Temp%\7ZipSfx.000\DC.exe → detected as HackTool.Win32.DEFENDERCONTROL.Z, deleted afterwards
- %User Temp%\7ZipSfx.000\ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe → Mimic ransomware, deleted afterwards
- %User Temp%\7ZipSfx.000\Everything.exe → legitimate Everything application, deleted afterwards
- %User Temp%\7ZipSfx.000\Everything.ini → deleted afterwards
- %User Temp%\7ZipSfx.000\Everything2.ini → deleted afterwards
- %User Temp%\7ZipSfx.000\Everything32.dll → legitimate dll used by Everything.exe, deleted afterwards
- %User Temp%\7ZipSfx.000\Everything64.dll → password protected archive containing malicious payload, deleted afterwards
- %User Temp%\7ZipSfx.000\gui35.exe → deleted afterwards
- %User Temp%\7ZipSfx.000\gui40.exe → GUI used by Mimic ransomware, deleted afterwards
- %User Temp%\7ZipSfx.000\xdel.exe → legitimate sdelete application, deleted afterwards
- %User Temp%\7ZSfx000.cmd → used to delete the sample and itself
- Copy of files dropped in %User Temp%\7ZipSfx.000:
- %AppDataLocal%\{Generated GUID}\7za.exe
- %AppDataLocal%\{Generated GUID}\DC.exe
- %AppDataLocal%\{Generated GUID}\Everything.exe
- %AppDataLocal%\{Generated GUID}\Everything.ini
- %AppDataLocal%\{Generated GUID}\Everything2.ini
- %AppDataLocal%\{Generated GUID}\Everything32.dll
- %AppDataLocal%\{Generated GUID}\Everything64.dll
- %AppDataLocal%\{Generated GUID}\gui35.exe
- %AppDataLocal%\{Generated GUID}\gui40.exe
- %AppDataLocal%\{Generated GUID}\systemsg.exe → copy of ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe
- %AppDataLocal%\{Generated GUID}\xdel.exe
- %AppDataLocal%\{Generated GUID}\session.tmp
- %AppDataLocal%\{Generated GUID}\global_options.ini
- %System%\GroupPolicy\Machine\Registry.pol
- %System%\GroupPolicy\gpt.ini
- %System Root%\temp\session.tmp
It adds the following processes:
- %User Temp%\7ZipSfx.000\7za.exe i
- %User Temp%\7ZipSfx.000\7za.exe x -y -p{Archive File Password} Everything64.dll
- %User Temp%\7ZipSfx.000\ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe
- cmd /c "%User Temp%\7ZSfx000.cmd"
- %AppDataLocal%\{Generated GUID}\systemsg.exe
- %AppDataLocal%\{Generated GUID}\gui40.exe
- %Program Files%\Everything\Everything.exe" -startup
- %AppDataLocal%\{Generated GUID}\DC.exe /D
- %AppDataLocal%\{Generated GUID}\systemsg.exe -e watch -pid {Current Process PID} -!
- %AppDataLocal%\{Generated GUID}\systemsg.exe" -e ul1;
- %AppDataLocal%\{Generated GUID}\systemsg.exe" -e ul2;
- powercfg.exe -H off
- powercfg.exe -SETACVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETACVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETACVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -SETDCVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETDCVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETDCVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -SETACVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETACVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETACVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -SETDCVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETDCVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETDCVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -S 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c
- powercfg.exe -S e9a42b02-d5df-448d-aa00-03f14749eb61
- ping 127.2 -n 5 & fsutil file setZeroData offset=0 length=20000000 \"%s\" & cd /d \"%s\" & Del /f /q /a *.exe *.bat
- ping 127.2 -n 5 & fsutil file setZeroData offset=0 length=20000000 \"%s\" & cd /d \"%s\" & Del /f /q /a *.exe *.ini *.dll *.bat *.db
- powershell.exe -ExecutionPolicy Bypass \"Get-VM | Stop-VM\"
- powershell.exe -ExecutionPolicy Bypass \"Get-VM | Select-Object vmid | Get-VHD | %{Get-DiskImage -ImagePath $_.Path; Get-DiskImage -ImagePath $_.ParentPath} | Dismount-DiskImage\"
- powershell.exe -ExecutionPolicy Bypass \"Get-Volume | Get-DiskImage | Dismount-DiskImage\"
- bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
- bcdedit.exe /set {default} recoveryenabled no
- wbadmin.exe DELETE SYSTEMSTATEBACKUP
- wbadmin.exe delete catalog -quiet
- reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v "AllowMultipleTSSessions" /t REG_DWORD /d 0x1 /f
- reg add "HKLM\system\CurrentControlSet\Control\Terminal Server" /v "fSingleSessionPerUser" /t REG_DWORD /d 0x0 /f
- reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "c:\windows\system32\cmd.exe"
- notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- %AppDataLocal%\{Generated GUID}\xdel.exe -accepteula -p 1 -c {Encrypted Drive}
- wevtutil.exe cl security
- wevtutil.exe cl system
- wevtutil.exe cl application
- cmd.exe /d /c "ping 127.2 -n 5 & fsutil file setZeroData offset=0 length=20000000 "%AppDataLocal%\{Generated GUID}\systemsg.exe" & cd /d "%AppDataLocal%\{Generated GUID}" & Del /f /q /a *.exe *.ini *.dll *.bat *.db"
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It creates the following folders:
- %User Temp%\7ZipSfx.000
- %AppDataLocal%\{Generated GUID} →File attribute set to HIDDEN and SYSTEM
- %System Root%\temp
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.)
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- {Derived from the string "WhosYourBunny"}
Autostart Technique
This Ransomware adds the following registry entries to enable its automatic execution at every system startup:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg = %AppDataLocal%\{Generated GUID}\systemsg.exe
Other System Modifications
This Ransomware adds the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
exefile\shell\open\
command
(Default) = "%1" %*
HKEY_USER\S-1-5-21-2019512041-4230814187-3178073052-1000_CLASSES\exefile\
shell\open\command
(Default) = "%1" %*
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows Defender\Real-Time Protection
DisableRealtimeMonitoring = 1
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
HidePowerOptions = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
HidePowerOptions = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
NoClose = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
StartMenuLogOff = 1
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Control\FileSystem
LongPathsEnabled = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
DataCollection
AllowTelemetry = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Winlogon
AllowMultipleTSSessions = 1
HKEY_LOCAL_MACHINE\system\CurrentControlSet\
Control\Terminal Server
fSingleSessionPerUser = 0
HKEY_LOCAL_MACHINE\Software\Classes\
mimicfile\shell\open\
command
(Default) = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
HKEY_LOCAL_MACHINE\Software\Classes\
.ELENOR-corp-{Victim ID}
(Default) = mimicfile
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg.exe = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
It modifies the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\
Microsoft\Windows Defender
DisableAntiSpyware = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows Defender
DisableAntiSpyware = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
services\WinDefend
Start = 3
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{Service with "sql","backup", or "database" in its Name}
Start = 4
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
shutdownwithoutlogon = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
System
ConsentPromptBehaviorAdmin = 5
(Note: The default value data of the said registry entry is 5.)
HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\
Windows\CurrentVersion\Policies\
System
legalnoticetext = {Contents of Ransom Note}
(Note: The default value data of the said registry entry is {Empty}.)
HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\
Windows\CurrentVersion\Policies\
System
legalnoticecaption = {Space}
(Note: The default value data of the said registry entry is {Empty}.)
It deletes the following registry keys:
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows\System
DisableCmd =
HKEY_CURRENT_USER\Software\Policies\
Microsoft\Windows\System
DisableCmd =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg.exe =
HKEY_CURRENT_USER\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg.exe =
Propagation
This Ransomware does not have any propagation routine.
Backdoor Routine
This Ransomware does not have any backdoor routine.
Rootkit Capabilities
This Ransomware does not have rootkit capabilities.
Process Termination
This Ransomware terminates the following services if found on the affected system:
- WSearch
- pla
- DusmSvc
- defragsvc
- DoSvc
- wercplsupport
- SDRSVC
- TroubleshootingSvc
- Wecsvc
- fhsvc
- wbengine
- PcaSvc
- WerSvc
- SENS
- AppIDSvc
- BITS
- wuauserv
- SysMain
- DiagTrack
- diagnosticshub.standalonecollector.service
- dmwappushservice
- WMPNetworkSvc
It terminates the following processes if found running in the affected system's memory:
- taskmgr.exe
- tasklist.exe
- taskkill.exe
- perfmon.exe
- Everything.exe
It terminates processes or services that contain any of the following strings if found running in the affected system's memory:
- sql
- backup
- database
Information Theft
This Ransomware gathers the following information on the affected computer:
- Processor architecture
- Number of processors
- RAM information
- OS version
- Username
- Computer name
- If executed with elevated privileges or not
- User groups
- Affected machine IP address
- Network adapter name
- Network shares
- Network drives
- If the full version of .NET Framework 4 is installed on the affected system or not
Other Details
This Ransomware encrypts files with the following extensions:
- tib
- sql
- sqlite
- sqlite3
- sqlitedb
- mdf
- mdb
- adb
- db
- db3
- dbf
- dbs
- udb
- dbv
- dbx
- edb
- exb
- 1cd
- fdb
- idb
- mpd
- myd
- odb
- xls
- xlsx
- doc
- docx
- bac
- bak
- back
- zip
- rar
- dt
- 4dd
- 4dl
- abcddb
- abs
- abx
- accdb
- accdc
- accde
- accdr
- accdt
- accdw
- accft
- ade
- adf
- adn
- adp
- alf
- arc
- ask
- bacpac
- bdf
- btr
- cat
- cdb
- chck
- ckp
- cma
- cpd
- dacpac
- dad
- dadiagrams
- daschema
- db-shm
- db-wal
- db2
- dbc
- dbt
- dcb
- dct
- dcx
- ddl
- dlis
- dp1
- dqy
- dsk
- dsn
- dtsx
- dxl
- eco
- ecx
- epim
- fcd
- fic
- fm5
- fmp
- fmp12
- fmpsl
- fol
- fp3
- fp4
- fp5
- fp7
- fpt
- frm
- gdb
- grdb
- gwi
- hdb
- his
- hjt
- ib
- icg
- icr
- ihx
- itdb
- itw
- jet
- jtx
- kdb
- kexi
- kexic
- kexis
- lgc
- lut
- lwx
- maf
- maq
- mar
- mas
- mav
- maw
- mdn
- mdt
- mrg
- mud
- mwb
- ndf
- nnt
- nrmlib
- ns2
- ns3
- ns4
- nsf
- nv
- nv2
- nwdb
- nyf
- oqy
- ora
- orx
- owc
- p96
- p97
- pan
- pdb
- pdm
- pnz
- qry
- qvd
- rbf
- rctd
- rod
- rodx
- rpd
- rsd
- s2db
- sas7bdat
- sbf
- scx
- sdb
- sdc
- sdf
- sis
- sl3
- spq
- sqlite2
- te
- temx
- tmd
- tps
- trc
- trm
- udl
- usr
- v12
- vis
- vpd
- vvv
- wdb
- wmdb
- wrk
- xdb
- data
- xld
- xmlff
- 7z
It does the following:
- It does not proceed with its behavior when the affected system's operating system is Windows XP or older.
- It uses the following GUI to control the operation of the ransomware:
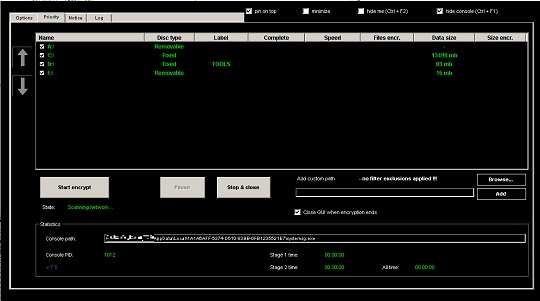
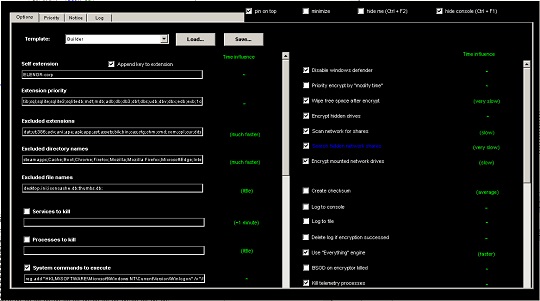
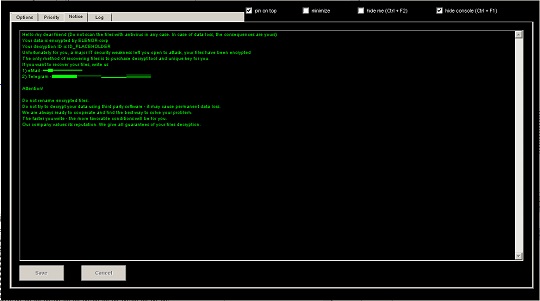
- It encrypts fixed and removable drives and network shares.
- It abuses Everything APIs to search for files to encrypt.
- It stores a session key in %AppDataLocal%\{Generated GUID}\session.tmp to resume encryption if the process is interrupted.
- It disables Windows Defender.
- It disables the affected system's ability to sleep, hibernate, or enter power-saving mode.
- It uses Powershell to stop all running VMs, identify VHDs associated with VMs and unmounts them.
- It empties the recycle bin.
- It uses WQL to delete volume shadow copies.
- It enables multiple remote desktop sessions to the affected system.
- It sets sethc.exe (Sticky Keys) to open cmd.exe.
- It clears security, system, and applicaiton event logs.
- It disables Windows telemetry.
- It sets itself to be one of the last processes terminated during system shutdown.
It accepts the following parameters:
- -dir → directory for encryption
- -e all → encrypt all (default)
- -e local → encrypt local files
- -e net → encrypt files on network drives
- -e watch
- -e share → encrypt files on network shares
- -e ul1 → unlock certain memory addresses from another process
- -e ul2 → unlock certain memory addresses from another process
- -prot → protects the ransomware from being killed
- -pid → process identifier (PID) of the previously-running ransomware
- -tail
It does not exploit any vulnerability.
Ransomware Routine
This Ransomware avoids encrypting files with the following strings in their file path:
- desktop.ini
- iconcache.db
- thumbs.db
- ntuser.ini
- boot.ini
- ntdetect.com
- ntldr
- NTUSER.DAT
- bootmgr
- BOOTNXT
- BOOTTGT
- session.tmp
- Decrypt_ELENOR-corp_info.txt
It avoids encrypting files found in the following folders:
- steamapps
- Cache
- Boot
- Chrome
- Firefox
- Mozilla
- Mozilla Firefox
- MicrosoftEdge
- Internet Explorer
- TorBrowser
- Opera
- Opera Software
- Common Files
- Config.Msi
- Intel
- Microsoft
- Microsoft Shared
- Microsoft.NET
- MSBuild
- MSOCache
- Packages
- PerfLogs
- Program Files
- Program Files (x86)
- ProgramData
- System Volume Information
- tmp
- Temp
- USOShared
- Windows
- Windows Defender
- Windows Journal
- Windows NT
- Windows Photo Viewer
- Windows Security
- Windows.old
- WindowsApps
- WindowsPowerShell
- WINNT
- $RECYCLE.BIN
- $WINDOWS.~BT
- $Windows.~WS
- :\Users\Public\
- :\Users\Default\
- %AppDataLocal%\{Generated GUID}
(Note: %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It appends the following extension to the file name of the encrypted files:
- .ELENOR-corp-{Victim ID}
It drops the following file(s) as ransom note:
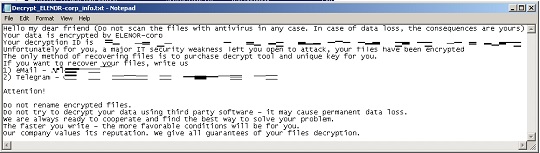
- {Root of Encrypted Path}\Decrypt_ELENOR-corp_info.txt
- %Desktop%\Decrypt_ELENOR-corp_info.txt
It avoids encrypting files with the following file extensions:
- ELENOR-corp-{Victim ID}
- dat
- ut
- 386
- adv
- ani
- ape
- apk
- app
- asf
- assets
- bik
- bin
- cas
- cfg
- chm
- cmd
- com
- cpl
- cur
- dds
- deskthemepack
- diagcab
- diagcfg
- diagpkg
- dll
- dmp
- drv
- dsf
- epub
- exe
- fnt
- fon
- gif
- hlp
- hta
- htm
- html
- ico
- ics
- idx
- inf
- info
- ini
- ipch
- lib
- log
- manifest
- mid
- mod
- msc
- msi
- msp
- msstyles
- msu
- mui
- mxf
- nls
- nomedia
- ocx
- otf
- pak
- pif
- ps1
- py
- rc
- reg
- resource
- ress
- rgss3a
- rm
- rmvb
- rom
- rpa
- rpgmvo
- rpgmvp
- rpy
- rpyc
- rtf
- rtp
- rvdata2
- sfcache
- shs
- snd
- so
- swf
- sys
- tak
- theme
- themepack
- tiger
- tmp
- torrent
- ts
- ttc
- ttf
- h
- cpp
- unity3d
- usm
- vbs
- vob
- vsix
- wav
- winmd
- woff
- wpx
- wv
- xex
- xml
SOLUTION
Step 1
Trend Micro Predictive Machine Learning detects and blocks malware at the first sign of its existence, before it executes on your system. When enabled, your Trend Micro product detects this malware under the following machine learning name:
Step 2
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 3
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 4
Restart in Safe Mode
Step 5
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- systemsg = %AppDataLocal%\{Generated GUID}\systemsg.exe
- systemsg = %AppDataLocal%\{Generated GUID}\systemsg.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\open\command
- (Default) = %1 %*
- (Default) = %1 %*
- In HKEY_USER\S-1-5-21-2019512041-4230814187-3178073052-1000_CLASSES\exefile\shell\open\command
- (Default) = %1 %*
- (Default) = %1 %*
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection
- DisableRealtimeMonitoring = 1
- DisableRealtimeMonitoring = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchIndexer.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchProtocolHost.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchApp.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CompatTelRunner.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsqmcons.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tasklist.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskkil.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\perfmon.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\shutdown.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\logoff.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- HidePowerOptions = 1
- HidePowerOptions = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- HidePowerOptions = 1
- HidePowerOptions = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- NoClose = 1
- NoClose = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- StartMenuLogOff = 1
- StartMenuLogOff = 1
- In HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\FileSystem
- LongPathsEnabled = 1
- LongPathsEnabled = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\DataCollection
- AllowTelemetry = 0
- AllowTelemetry = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- AllowMultipleTSSessions = 1
- AllowMultipleTSSessions = 1
- In HKEY_LOCAL_MACHINE\system\CurrentControlSet\Control\Terminal Server
- fSingleSessionPerUser = 0
- fSingleSessionPerUser = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe
- Debugger = c:\windows\system32\cmd.exe
- Debugger = c:\windows\system32\cmd.exe
- In HKEY_LOCAL_MACHINE\Software\Classes\mimicfile\shell\open\command
- (Default) = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- (Default) = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- In HKEY_LOCAL_MACHINE\Software\Classes\.ELENOR-corp-{Victim ID}
- (Dafault) = mimicfile
- (Dafault) = mimicfile
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- systemsg.exe = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- systemsg.exe = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
Step 6
Restore these modified registry values
Important:Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this only if you know how to or you can seek your system administrator's help. You may also check out this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
- From: DisableAntiSpyware = 1
To: DisableAntiSpyware = 0
- From: DisableAntiSpyware = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender
- From: DisableAntiSpyware = 1
To: DisableAntiSpyware = 0
- From: DisableAntiSpyware = 1
- In HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinDefend
- From: Start = 3
To: Start = 2
- From: Start = 3
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\{Service with sql,backup, or database in its Name}
- From: Start = 4
To: Start = {Default}
- From: Start = 4
- In HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- From: shutdownwithoutlogon = 0
To: shutdownwithoutlogon = 1
- From: shutdownwithoutlogon = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- From: legalnoticetext = {Contents of Ransom Note}
To: legalnoticetext = {Empty}
- From: legalnoticetext = {Contents of Ransom Note}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- From: legalnoticecaption = {Space}
To: legalnoticecaption = {Empty}
- From: legalnoticecaption = {Space}
Step 7
Restore these deleted registry keys/values from backup
*Note: Only Microsoft-related keys/values will be restored. If the malware/grayware also deleted registry keys/values related to programs that are not from Microsoft, please reinstall those programs on your computer.
- In HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System
- DisableCmd
- DisableCmd
- In HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\System
- DisableCmd
- DisableCmd
Step 8
Search and delete these files
- %User Temp%\7ZipSfx.000\7za.exe
- %User Temp%\7ZipSfx.000\DC.exe
- %User Temp%\7ZipSfx.000\ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe
- %User Temp%\7ZipSfx.000\Everything.exe
- %User Temp%\7ZipSfx.000\Everything.ini
- %User Temp%\7ZipSfx.000\Everything2.ini
- %User Temp%\7ZipSfx.000\Everything32.dll
- %User Temp%\7ZipSfx.000\Everything64.dll
- %User Temp%\7ZipSfx.000\gui35.exe
- %User Temp%\7ZipSfx.000\gui40.exe
- %User Temp%\7ZipSfx.000\xdel.exe
- %User Temp%\7ZSfx000.cmd
- %AppDataLocal%\{Generated GUID}\7za.exe
- %AppDataLocal%\{Generated GUID}\DC.exe
- %AppDataLocal%\{Generated GUID}\Everything.exe
- %AppDataLocal%\{Generated GUID}\Everything.ini
- %AppDataLocal%\{Generated GUID}\Everything2.ini
- %AppDataLocal%\{Generated GUID}\Everything32.dll
- %AppDataLocal%\{Generated GUID}\Everything64.dll
- %AppDataLocal%\{Generated GUID}\gui35.exe
- %AppDataLocal%\{Generated GUID}\gui40.exe
- %AppDataLocal%\{Generated GUID}\systemsg.exe
- %AppDataLocal%\{Generated GUID}\xdel.exe
- %AppDataLocal%\{Generated GUID}\session.tmp
- %AppDataLocal%\{Generated GUID}\global_options.ini
- %System%\GroupPolicy\Machine\Registry.pol
- %System%\GroupPolicy\gpt.ininerated GUID}
- %System Root%\temp\session.tmp
Step 9
Search and delete these folders
- %User Temp%\7ZipSfx.000
- %AppDataLocal%\{Generated GUID}
- %System Root%\temp
Step 10
Restart in normal mode and scan your computer with your Trend Micro product for files detected as Ransom.Win32.MIMIC.D. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 11
Restore encrypted files from backup.
Did this description help? Tell us how we did.


