HackTool.Win64.EDRSilencer.REDT
Generic.Trojan.EDRStealer.A.E950CF56 (BITDEFENDER)
Windows


Threat Type: Hacking Tool
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
Downloaded from the Internet, Dropped by other malware
This Hacking Tool arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
TECHNICAL DETAILS
381,937 bytes
EXE
No
16 Jul 2024
Arrival Details
This Hacking Tool arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Other Details
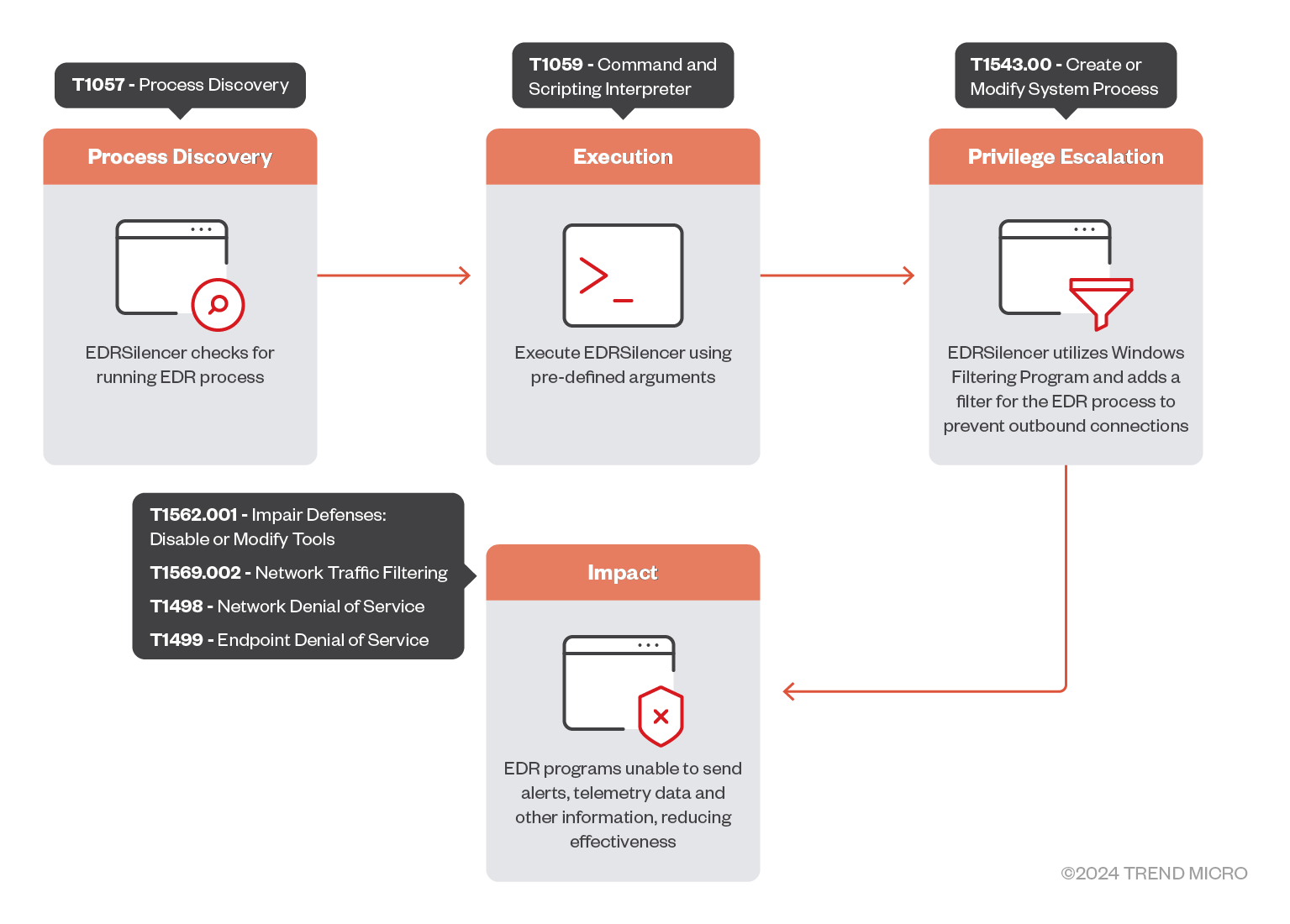
This Hacking Tool does the following:
- It uses the Windows Filtering Platform (WFP) to block the outbound traffic of the following EDR processes:
- Carbon Black Cloud
- RepMgr.exe
- RepUtils.exe
- RepUx.exe
- RepWAV.exe
- RepWSC.exe
- Carbon Black EDR
- cb.exe
- Cybereason
- AmSvc.exe
- CrAmTray.exe
- CrsSvc.exe
- CybereasonAV.exe
- ExecutionPreventionSvc.exe
- Cylance
- CylanceSvc.exe
- Cisco Secure Endpoint (Formerly Cisco AMP)
- sfc.exe
- Elastic EDR
- elastic-agent.exe
- elastic-endpoint.exe
- filebeat.exe
- winlogbeat.exe
- ESET Inspect
- EIConnector.exe
- ekrn.exe
- FortiEDR
- fortiedr.exe
- Harfanglab EDR
- hurukai.exe
- Microsoft Defender for Endpoint and Microsoft Defender Antivirus
- MsMpEng.exe
- MsSense.exe
- SenseCncProxy.exe
- SenseIR.exe
- SenseNdr.exe
- SenseSampleUploader.exe
- Palo Alto Networks Traps/Cortex XDR
- cyserver.exe
- CyveraService.exe
- CyvrFsFlt.exe
- Traps.exe
- Qualys EDR
- QualysAgent.exe
- SentinelOne
- LogProcessorService.exe
- SentinelAgent.exe
- SentinelAgentWorker.exe
- SentinelBrowserNativeHost.exe
- SentinelHelperService.exe
- SentinelServiceHost.exe
- SentinelStaticEngine.exe
- SentinelStaticEngineScanner.exe
- Tanium
- TaniumClient.exe
- TaniumCX.exe
- TaniumDetectEngine.exe
- Trellix EDR
- xagt.exe
- TrendMicro Apex One
- CETASvc.exe
- CNTAoSMgr.exe
- EndpointBasecamp.exe
- Ntrtscan.exe
- PccNTMon.exe
- TMBMSRV.exe
- TmCCSF.exe
- TmListen.exe
- TmWSCSvc.exe
- WSCommunicator.exe
- Carbon Black Cloud
- It can add a WFP filter for a specific process based on user input.
- It can remove all WFP filters created by this tool.
- It can remove a specific WFP filter by filter ID.
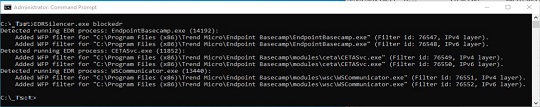
- It displays its logs on a console:
It accepts the following parameters:
- blockedr → Add WFP filters to block the IPv4 and IPv6 outbound traffic of all detected EDR processes
- Block {process full path} → Add WFP filters to block the IPv4 and IPv6 outbound traffic of a specific process (full path is required)
- unblockall → Remove all WFP filters applied by this tool
- unblock {filter ID} → Remove a specific WFP filter based on filter ID
- -h or --help → Shows the help message
SOLUTION
9.800
2.745.00
18 Jul 2024
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Scan your computer with your Trend Micro product to delete files detected as HackTool.Win64.EDRSilencer.REDT. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.