The Middle Eastern and North African Underground: Where Culture and Cybercrime Meet
 View Digital Souks: A Glimpse into the Middle Eastern and North African Underground
View Digital Souks: A Glimpse into the Middle Eastern and North African Underground
How much are Supervisory Control and Data Acquisition (SCADA) port numbers in the cybercriminal underworld? In the Middle Eastern and North African underground, they’re free.
Their underground marketplaces aren’t profit-driven like Russia’s, or China’s. There's an ironic confluence of ideology and cybercrime in this region, where the “spirit of sharing” and sense of brotherhood are the apparent forces behind the distribution of crimeware.
A common practice among its players is to readily hand out codes, malware, and instruction manuals for free. Crypters, typically used to obfuscate malware, as well as SQL injection tools, keyloggers, and basic malware builders, are given away—a reflection of the culture within the regions’ underground scene. Their sense of brotherhood is further exemplified in the way members concertedly plan and launch DDoS and website defacement attacks.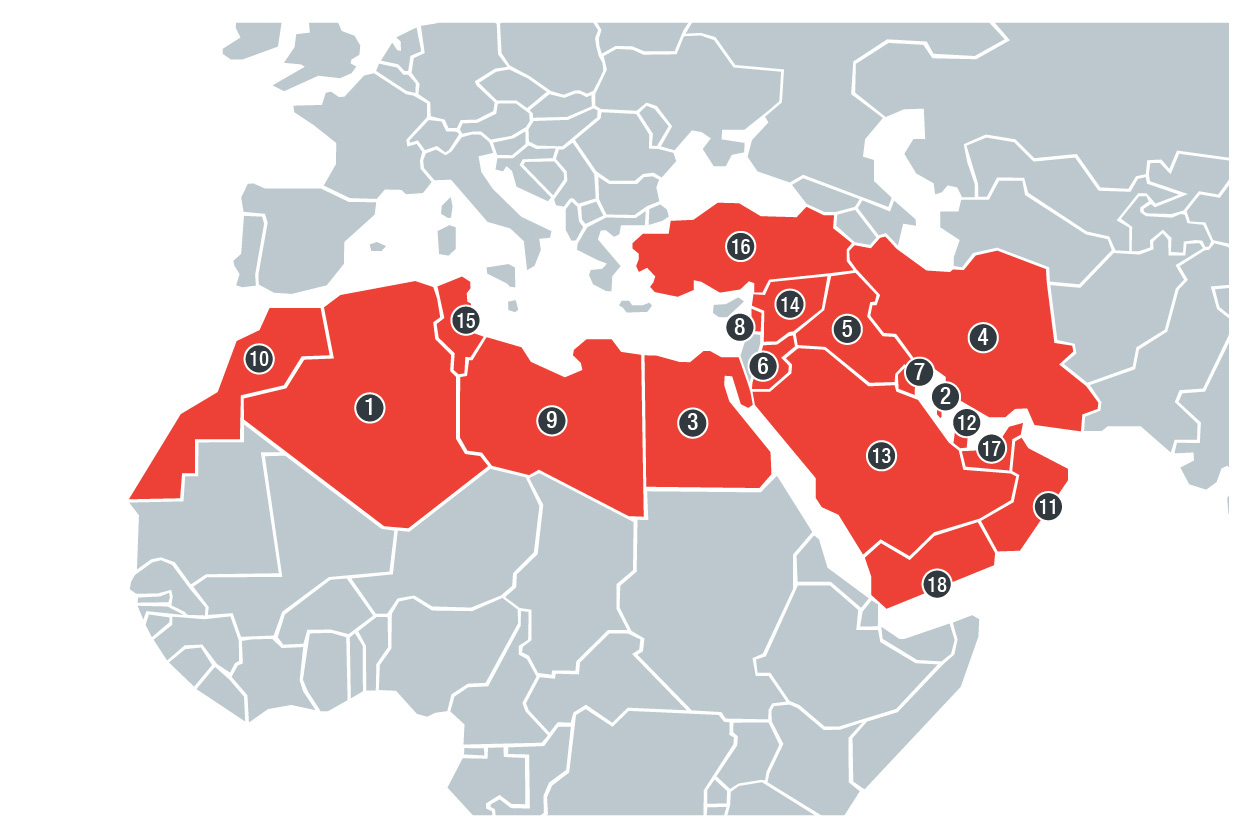
Countries included in our Middle Eastern and North African underground research:
(1) Algeria, (2) Bahrain, (3) Egypt, (4) Iran, (5) Iraq, (6) Jordan, (7) Kuwait, (8) Lebanon,
(9) Libya, (10) Morocco, (11) Oman, (12) Qatar, (13) Saudi Arabia, (14) Syria, (15) Tunisia,
(16) Turkey, (17) United Arab Emirates, and (18) Yemen
We also noticed how cultural pleasantries preceded and concluded all kinds of murky business transactions. Ideology often influences what is sold and traded, motivating the kind of activities that transpire within its forums and sites. Many have dedicated sections espousing their beliefs, grouped with how-to guides on encryption, programming, and reverse engineering.
Our look into these digital souks also revealed how the Middle Eastern and North African underground is not a glass tank like North America’s, but more cautious like the French underground. Potential customers are barred from window-shopping, for instance, and viewing links or full forum posts requires an account. Registration is a lengthy process that involves paying for one’s membership in bitcoins and getting through the language barrier. English-based forums and sites do exist, but there are certain regional variances.
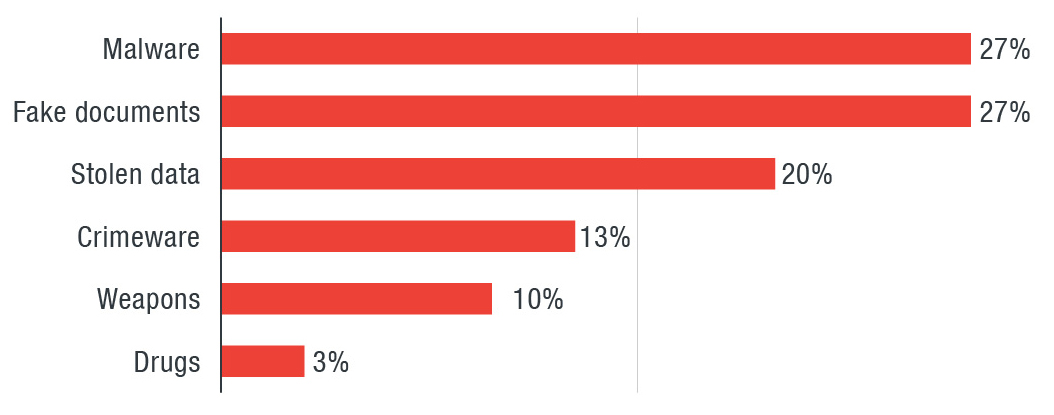
Distribution of wares sold in the Middle Eastern and Northern African underground sites; our research covers a period between July and December 2016, and we updated the price of some of the wares offered during that time in May 2017
The products and services that have become cybercriminal staples across the world are also available in the Middle East and North African underground—credit card dumps, online accounts, credentials, and malware. Stolen identities abound here, in bundles that include passport scans and copies of driver’s license and local utility bills. The marketplaces are also rife with do-it-yourself kits that provide the resources that even beginners can use to launch their own cybercriminal business. Developers typically sell their malware either as a single binary, or a bundle of binary and builder; and in some cases, access to a command-and-control (C&C) infrastructure.


Prices of some of the wares offered in the Middle Eastern and North African underground
Regionalized hosting spaces and access to Remote Desktop Protocol (RDP) servers are offered, along with cashout services that include stolen physical goods. Of note are mobile devices and disposable SIM cards whose purchase in many Middle Eastern and North African countries requires a passport, biometric registration, or personally identifiable document.Other offerings include purportedly secure virtual private networks as well as advanced worms and remote access Trojans. Social media is also abused to peddle contraband. The notorious WannaCry ransomware is sold for $50. Other well-known families are sold, such as CTB-Locker, which we saw peddled by a cybercriminal from the Russian underground.
How much do these products and services cost? What are their real-world implications? And more importantly, what is their underground’s outlook in the grander scheme of cybercrime? Read about it in on our latest addition to our cybercriminal underground research series, “Digital Souks: A Glimpse into the Middle Eastern and North African Underground.”
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks