Ransomware Recap: SLocker Copycats WannaCry
 As the dust of Petya’s outbreak settles, we can all see just how much damage ransomware can cause. But it also revealed another truth: old threats die hard. WannaCry exploited vulnerabilities for which patches were already released. Petya, an old family, used multiple infection vectors. And as we saw last week, ransomware has no shortage of variety—an indication of its maturity in the threat landscape.
As the dust of Petya’s outbreak settles, we can all see just how much damage ransomware can cause. But it also revealed another truth: old threats die hard. WannaCry exploited vulnerabilities for which patches were already released. Petya, an old family, used multiple infection vectors. And as we saw last week, ransomware has no shortage of variety—an indication of its maturity in the threat landscape.
Here were the notable ransomware we’ve spotted from the previous week:
[RELATED: Frequently asked questions about the recent Petya outbreak]
SLocker Android ransomware tries to follow WannaCry’s footsteps
One of the oldest mobile ransomware, Simple Locker, a.k.a. SLocker (detected by Trend Micro as ANDROIDOS_SLOCKER), is also the most diverse. SLocker variants were some of last year’s most detected mobile threats, posing as law enforcement agencies to coerce victims into paying the ransom. By mid-May this year, SLocker resurged with hundreds of unique samples.
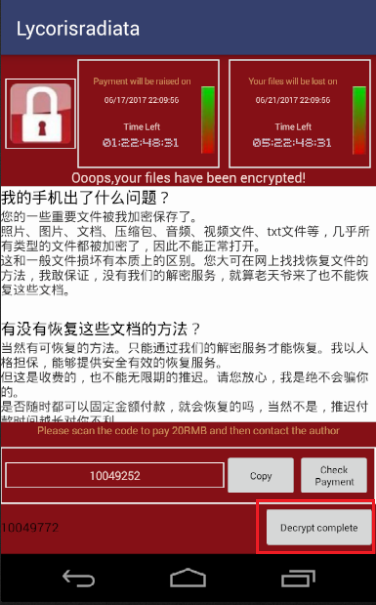
The WannaCry-mimicking SLocker (ANDROIDOS_SLOCKER.OPST) made headlines when its purported developers were arrested. It spread through China-based forums and bulletin boards, and masqueraded as a cheating app for the popular local game, King of Glory Auxiliary.
This version of SLocker is capable of file encryption, which is unique in that many Android ransomware are typically just screen lockers. It doesn’t encrypt system files; it notably scrambles files located in Download, DCIM, and BaiduNetdisk (related to Baidu’s Net Disk file transfer/storage service similar to Dropbox) as well as other directories. Files to be encrypted must not exceed 50 MB. It encrypts downloaded files, as well as text, image, and video files, among others.
The victim is offered three payment options. Some of the samples Trend Micro analyzed led to the same QR code prompting them to pay through a popular mobile payment service QQ. The ransom increases after three days, and threatens to delete the files after a week.
While it might have appeared to be more sophisticated, it's not impossible to decrypt affected files. The files can be decrypted by inputting a particular string of numbers in the field where it asks for a decryption key. This number, which serves as the decryption key, is calculated based on the number included in the extension name appended to the encrypted file. The number is also in the ransomware’s graphical user interface (GUI). Note though that this decryption key isn’t the one used to encrypt the files. This version of SLocker employs AES algorithm to scramble the files.
[Did you know: A version of SLocker mobile ransomware was also a banking Trojan]
ShellLocker gets a Russian flavor
Another old ransomware is ShellLocker, itself a copy of a Github-hosted ransomware project that's still-in-development. When it first emerged, it demanded a ransom of US$100 in bitcoins, which reduced by half in its second version. It retained its original ransom demand in this new version (RANSOM_SHELOCKER.A).
ShellLocker encrypts 151 file types, including types typically used in corporate environments: multimedia design, virtual machine, databases, archives, web application/server-related scripts, and backup.
The ransom note, written in Russian, claims itself to be ForceLocker. It purportedly used AES-256 encryption algorithm to scramble the files, each of which has their own decryption key. Encrypted files are appended with the .L0cked extension.

ShellLocker’s Russian ransom note
[READ: Ransomware families based on old, open-source, and popular families]
ZeroRansom misuses Gmail to communicate to victims
Another ransomware that emerged the previous week is ZeroRansom (RANSOM_ZERO.A), whose operators reportedly abuse Gmail to send encryption keys and communicate with victims. It’s a fairly straightforward file-encrypting malware that scrambles these 28 file types:
.txt, .doc, .docx, .pdf, .ppt, .pptx, .xls, .xlsx, .mp3, .mp4, .jpg, .png, .jpeg, .gif, .db, .data, .database, .sql, .htaccess, .bat", .c, .cpp, .py", .jar, .java, .cs, .sln, .asm
[Infographic: A multilayered defense against ransomware]
While these threats might not appear to be as dangerous as WannaCry or Petya, they are no less of a threat. It’s still important to adopt best practices to mitigate their adverse impact.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
End users and enterprises can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security for Android™ (available on Google Play), and Trend Micro™ Mobile Security for Apple devices (available on the App Store). Trend Micro™ Mobile Security for Enterprise provide device, compliance and application management, data protection, and configuration provisioning, as well as protect devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks