By Numaan Huq, Vladimir Kropotov, Philippe Lin, Rainer Vosseler
Trend Micro Research for VicOne
The rapid advancements in technology and data integration in the automotive industry have turned connected vehicles into complex data hubs that constantly generate, consume, and transmit large volumes of data. While this evolution toward a data-driven ecosystem has spawned many opportunities, including ways to improve vehicle functionalities and create new revenue streams, it has also given rise to new avenues that could be abused for malicious intent. Therefore, stakeholders need to be cognizant of looming threats, considering how vital vehicle data security is for the ecosystem to flourish.
Often, collection of vehicle data is done without users’ knowledge, let alone their manifest consent. Data collection details are also usually buried in the fine print of purchase agreements. This lack of clarity and transparency is cause for concern as it creates possibilities for data misuse or abuse, not to mention infringement of data protection laws.
To address such concerns, we embarked on a study for VicOne, the subsidiary of Trend Micro dedicated to automotive cybersecurity. Titled “Automotive Data: Opportunities, Monetization, and Cybersecurity Threats in the Connected Vehicle Landscape,” our research paper focuses on privacy and security concerns associated with vehicle data. In it, we discuss and examine different categories of vehicle data, how this data can be used and monetized, and cybersecurity threats that might arise from the misuse or abuse of this data.
The automotive data ecosystem
The automotive data ecosystem is a network of entities including connected vehicles, car manufacturers (OEMs), Tier 1 (T1) and Tier 2 (T2) suppliers, data brokers, and data consumers, all interlinked through data flows.
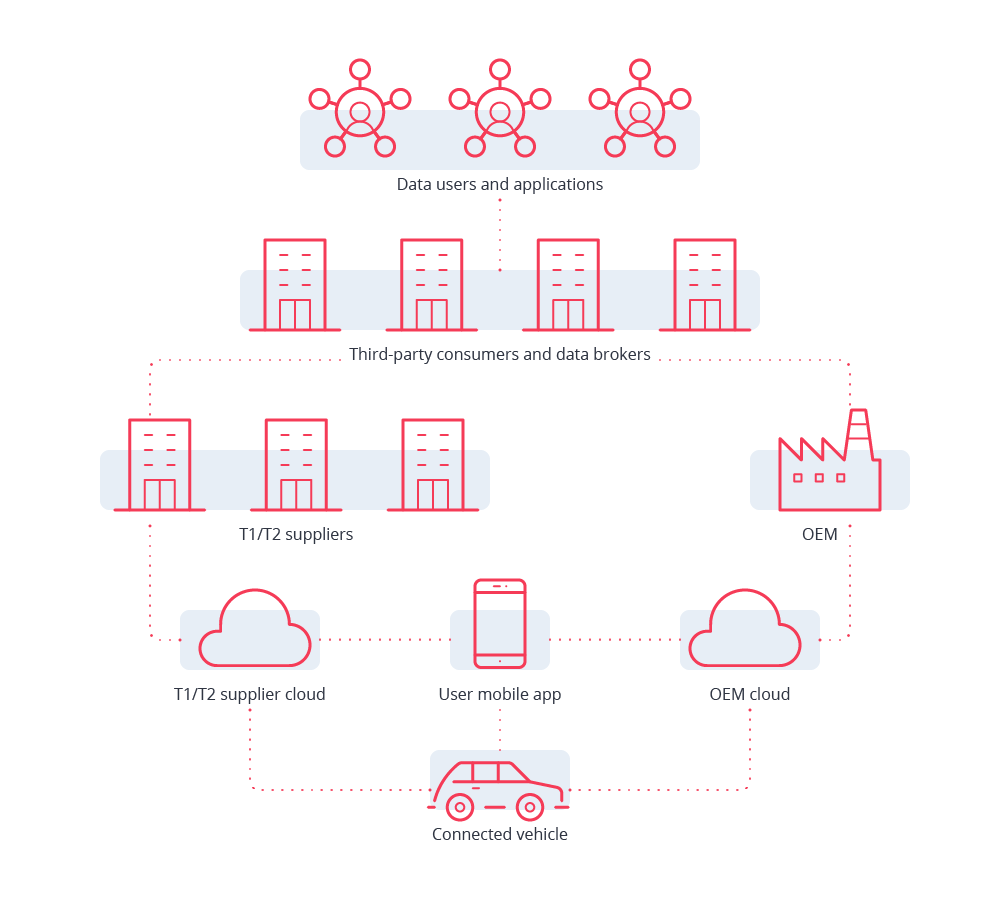 Figure 1. The automotive data ecosystem
Figure 1. The automotive data ecosystem
A key process in this ecosystem is data collection, which takes place through multiple channels established by OEMs or other trusted parties such as T1 or T2 suppliers. While the generation and transmission of vehicle data is a long-known fact, the kind of data that is sent back to the OEM/T1/T2 clouds remains largely unknown to the general public, so concerns about data privacy, security, and usage warrant careful consideration.
Our research discusses the ways in which OEMs and third parties use and monetize vehicle data. Examples of data monetization are fast becoming commonplace as we see subscription services being offered for vehicles. It is only a matter of time before cybercriminals set their sights on automotive data especially when monetization opportunities increase and start producing substantial revenue.
While the cybercriminal market for connected car data is still in its early stages, we anticipate its inevitable growth in the foreseeable future as third parties’ use of vehicle data significantly increases. The likelihood of a large-scale attack against connected cars targeting data is not far-fetched, and more sophisticated attacks like vehicle hacking and fleet takeover are also possibilities and no longer confined to the realm of science fiction.
Cyberthreats affecting connected cars
Instances of vehicle data leakage via Message Queuing Telemetry Transport (MQTT) brokers are among our research findings. Created for machine-to-machine (M2M) communications, MQTT is a lightweight protocol for publish-subscribe messaging. It allows devices to exchange messages over unreliable networks with minimal bandwidth and power consumption.
During our research, we also found API calls between vehicles and OEM/T1/T2 clouds in Trend Micro telemetry data. We found vehicle API communications denoting performance of actions such as remote start/stop, door lock/unlock, and telematic collection in our telemetry logs.
Such security gaps in data handling processes could enable malicious actors to exploit vulnerabilities and perform a variety of activities that could jeopardize data privacy and security, including:
- Vehicle tracking: A targeted vehicle could be tracked via access of its real-time location information, and thus could pose risks to the privacy and security of its driver and passengers. Also, real-time vehicle tracking could enable surveillance of high-profile individuals and their assets.
- Driver profiling: Malicious actors can extrapolate drivers’ personal habits, lifestyles, and routine locations from information on driving patterns. This puts privacy at risk if such data is misused.
- Data leak: Unsecure data transmission in the ecosystem could leak personally identifiable information (PII), maintenance data, fuel consumption, and other operational data, thus emphasizing concerns on the possibility of revealing sensitive information.
- Data manipulation: Access to data can enable attackers to create fake alerts in a vehicle or alter performance data, paving the way for false diagnostics or potentially dangerous driving settings.
- Data ransoming: Vehicle data is a natural extension of traditional IT data, so cybercriminals could employ old tricks to encrypt or prevent access to vehicle data stored in the OEM/T1/T2/broker clouds and demand a ransom for victims to regain access.
- Social engineering: Malicious actors could devise targeted social engineering attacks based on insights that can be drawn from collected data.
- Infrastructure disruption: Malicious actors could develop and execute attacks on critical infrastructure to impair essential services, such as those that use ambulances and utility vehicles.
- Espionage activities: Adversaries could draw insights from automotive data to perform industrial or corporate espionage, which could endanger business operations, strategies, and competitive advantages.
Insights and recommendations
One of the key insights from our research findings is that the vehicle data ecosystem is vast and intricate — owing to how vehicles have transformed into complex data hubs and how the data they generate, consume, and transmit can be repurposed to create new data products and monetization opportunities. New revenue streams can be developed, ranging from the creation of driver profiles to traffic data–powered targeted advertising.
But as the usage and monetization of automotive data grow, the incentive for cybercriminals to target vehicle data also becomes stronger. There is a plethora of possible exploits that malicious actors can pursue, emphasizing the urgency of putting cybersecurity measures in place within the automotive industry and data-centric third parties. The need for agencies to legislate and enforce data privacy laws to protect drivers and passengers should also be addressed as part of a proactive approach.
As the automotive data ecosystem evolves, stakeholders should collectively strive to strike a balance between encouraging innovation and ensuring the security and privacy of vehicle data collection and usage, as these considerations go hand in hand.
We provide the following recommendations to strengthen automotive cybersecurity:
- Implement robust data protection measures. As we anticipate the volume of vehicle data to grow exponentially in the coming years, implementing strong security measures is crucial. These should cover encryption of data at rest and in transit, API and cloud storage security, periodic security audits, and penetration testing to identify and address vulnerabilities early on.
- Inform users. It is incumbent on OEMs and other stakeholders to inform users about data collection practices, potential risks, and how to protect vehicle data. Users should be given clear, easy-to-understand privacy policies and instructions on how to adjust data collection settings or how to opt out completely.
- Secure vehicle APIs. API security is vital because cybercriminals have long considered APIs as an attack vector. Consider measures such as strong authentication, rate limiting, and regular monitoring of API activity to quickly detect and respond to threats.
- Regulate data collection and usage. There is a need to push for clear regulations on the collection, storage, and use of vehicle data. Legislation should define who has access to data, how long it is stored, and for what purposes it can be used.
- Develop secure middleware APIs. Since middleware APIs in connected cars can provide cybercriminals easy access to the vehicles’ electrical/electronic (E/E) architectures and electronic control units (ECUs), developers of these APIs should embed security features in their design, such as robust authentication and encryption, to prevent unauthorized access.
To gain more relevant insights on automotive data–centric cyberthreats and our recommendations on how these risks can be proactively addressed, read our research paper titled “Automotive Data: Opportunities, Monetization, and Cybersecurity Threats in the Connected Vehicle Landscape.” This paper is part of the VicOne Automotive Cybersecurity Report 2023.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks