The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
By Dr. Fyodor Yarochkin, Vladimir Kropotov, and Robert McArdle
 Download the Full Research Paper (PDF)
Download the Full Research Paper (PDF)
Download the Appendix
Introduction
The Russian-speaking cybercriminal underground remains the most sophisticated, resilient, and impactful ecosystems within the global cybercrime landscape. The underground and its participants exhibit several defining characteristics, such as the use of advanced tools and techniques, specialized forums and marketplaces dedicated to numerous services (both virtual and physical), plus a deeply ingrained culture of secrecy and collaboration. Over the years, it has consistently been at the forefront of cybercriminal innovation, pioneering new attack methods that other threat actors eventually adopted.
Even as it undergoes changes driven by new technologies, evolving cybercriminal business processes, and geopolitical events, the underground continues to shape global cyberthreats. It has expanded activities into previously untapped sectors, such as telecom infrastructure and IoT devices, which when combined with shifts in financial and logistical operations due to sanctions, highlights the underground’s adaptability and resilience.
These developments pose significant risks to businesses, governments, and individuals, emphasizing the need for a risk- and threat-intelligence-driven defense strategy. Organizations must adopt a Cyber Risk Exposure Management (CREM) framework that prioritizes a deep understanding of adversaries to effectively mitigate these threats.
Making use of comprehensive intelligence and anticipating shifts in the threat landscape are essential to staying ahead of emerging risks. A robust risk and threat intelligence-based approach requires not only tactical awareness but also a strategic understanding of adversaries, their evolving tactics, and the broader cybercriminal ecosystem. Defenders must recognize that effective cybersecurity goes beyond reactive measures — it requires a long-term, intelligence-driven strategy that continuously adapts to emerging threats. With decades of in-depth coverage, Trend Micro provides unparalleled insights into the Russian-speaking cybercriminal underground, offering organizations the intelligence necessary to proactively combat evolving threats.
Our research, ”The Russian-Speaking Underground,” marks the 50th installment and the culmination of our ongoing series, which started in 2012, analyzing the Russian-speaking cybercriminal underground. Over the course of this series, we have tracked the underground’s evolution, documenting its innovation, adaptability, and growing influence on the global cybercrime ecosystem. This milestone shows the depth and breadth of our investigations, providing a comprehensive understanding of how this ecosystem has shaped and continues to shape cyberthreats.
It is divided into two key sections: the main body and an appendix. The main body presents a high-level overview of the Russian-speaking cybercriminal underground, highlighting its evolution, impact, and emerging trends. Meanwhile, the appendix provides a deeper look into the specific tools, schemes, and operational tactics employed by cybercriminals, offering a more granular examination of their methods.
The Defining Characteristics of the Russian-Speaking Underground
Unlike other cybercriminal networks, the Russian-speaking underground operates across multiple territories, making it particularly formidable. The underground’s impact extends beyond traditional financially motivated cybercrime alone, as nation-state actors and profit-driven cybercriminals have begun seeing overlaps in objectives and operations.
Cultural factors play a significant role in shaping the pathways of Russian-speaking cybercriminals and their operations. The educational system, rooted in the USSR model, emphasized mathematics, engineering, and problem-solving skills, fostering a mindset that proved beneficial for cybercriminal activities. With free access to high school and university education in many Russian-speaking countries, individuals can acquire strong technical skills, lowering the barrier to entry into cybercrime. Many young individuals, even before graduating, already possess enough knowledge to take on basic underground activities and may even be already be well-integrated into the cybercriminal supply chain.
Beyond technical skills, cultural experiences influence how cybercriminals operate. Growing up in high-stress environments equips individuals with plenty of resilience and adaptability — critical traits for cybercrime operations. Additionally, an ingrained cautiousness makes Russian-speaking cybercriminals highly wary of outsiders, leading to strict vetting processes that include using underground-specific slang or proving past criminal activity.
Due to the underground’s fear of law enforcement infiltration, newcomers who fail to exhibit cultural familiarity are often rejected. This cautious approach extends even to forum security, with measures like culturally specific CAPTCHAs implemented to filter out non-native participants.
One of the defining features of the Russian-speaking underground is its strict rules of engagement, which are rigorously enforced. Reputation is the foundation of this ecosystem and is the primary determinant of an individual’s status and opportunities.
Figure 1. Examples of basic forum rules in a Russian-speaking underground forum (Procrd)
Members of the underground can be categorized into various roles, including forum administrators, sellers, service providers, buyers, watchers, strangers, and scammers. Each of these roles interacts differently with the concept of reputation and rely on it to navigate the cybercriminal landscape.
For example, forum administrators and moderators rely on trust to sustain their platforms, while sellers and service providers use reputation to strengthen their brand and establish credibility. Buyers generally do not require reputation unless purchasing unique assets, where trust becomes integral to avoid leaking valuable information. Watchers and strangers primarily observe or engage infrequently, with reputation only mattering in specific cases, such as gaining access to restricted content. Finally, scammers exploit others through impersonation and fraud, particularly on less regulated platforms.
Emerging Trends in the Underground Landscape
Advancements in technology and data accessibility are transforming cybercriminal business models, leading to significant shifts in underground behavior and monetization tactics.
The rise of ransomware double extortion schemes has driven mass data breaches, exposing sensitive personal information on a massive scale. This access to personally identifiable information (PII) has become an important asset for cybercriminals, not only fueling extortion but also enabling new identity-based fraud schemes. Additionally, the widespread availability of biometric data on social media, combined with AI-powered deepfake technology, has streamlined the creation of fake identities for threat actors.
Web3 technologies, including NFTs, the metaverse, and blockchain platforms have gained significant traction over the past few years. However, its rise and the irresistible combination of high-value assets and users lacking security knowledge has made Web3 a prime target for threat actors. Attackers exploit popular social media platforms like Twitter, Discord, TikTok, Instagram, and Threads to execute their schemes, using specialized slang such as “mammoth” to describe their targets. (referencing the idea that, like a Mammoth, easy targets for scams will never go extinct).
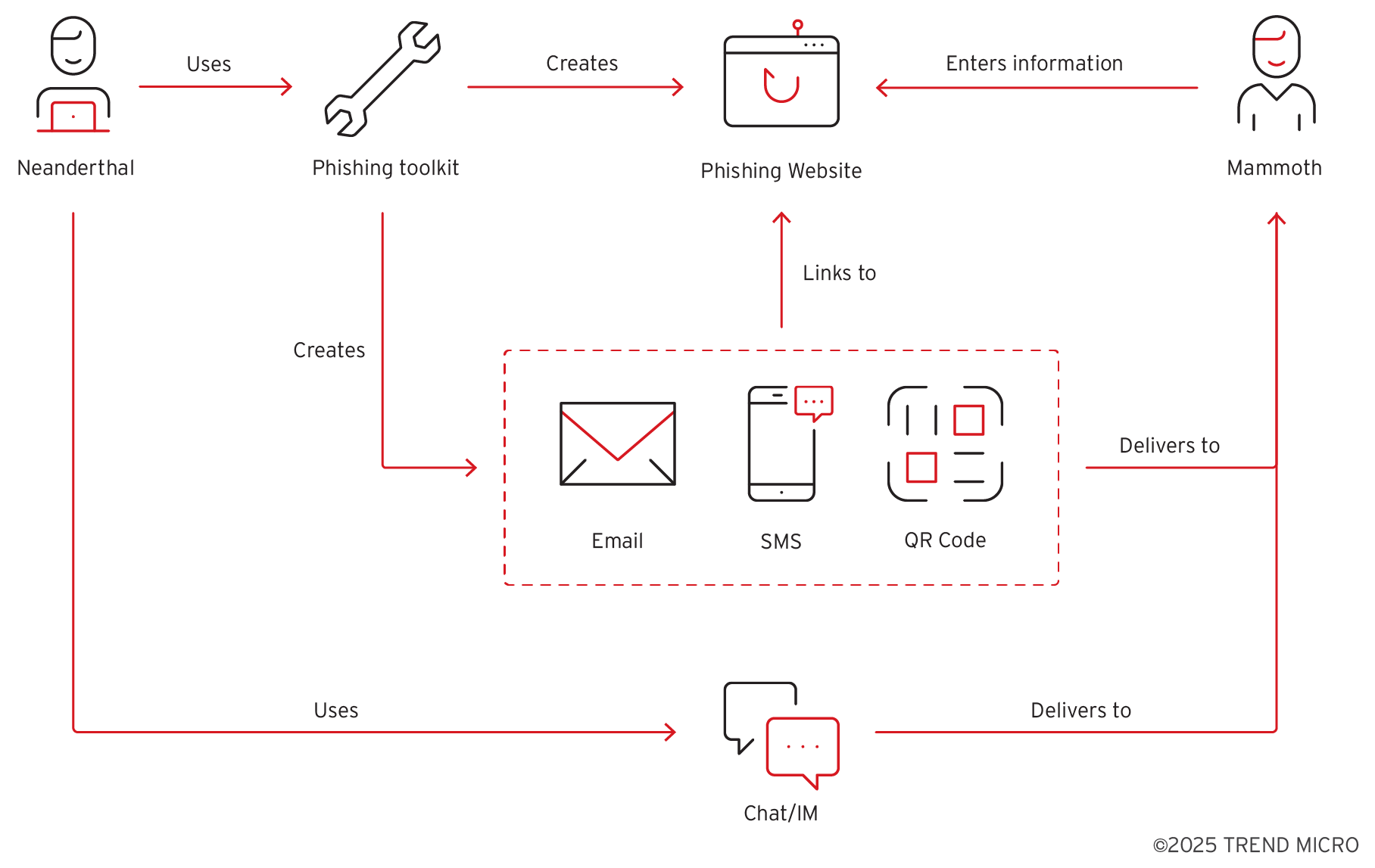
Figure 2. A scam business process, where the term “neanderthal” refers to threat actors who consider themselves “mammoth shepherds”
A common scam method involves attackers taking control of social media accounts (preferably verified ones with established activity) and using tactics such as engaging with influencers to create a credible online presence. Attackers then impersonate legitimate Web3 projects, luring victims into downloading malicious software that drains their digital assets. The use of automation, bots, and third-party services allows these scams to operate at scale, making Web3 fraud a lucrative scheme for cybercriminals.
Sanctions and economic restrictions have led to shifts in underground financial flows. Reshipping fraud has surged, while cryptocurrency has become even more ingrained in the ecosystem. Moreover, legitimate businesses are increasingly using gray financial services to circumvent economic restrictions.
The Evolving Role of Ransomware
Ransomware remains a contentious topic within the Russian-speaking underground, as open discussions about it are often prohibited to avoid unwanted scrutiny from external parties. Despite their profitability, ransomware attacks are seen as overly bold and attention-grabbing by many underground communities. Consequently, most platforms enforce strict bans on any business dealings linked to ransomware. However, this does not prevent ransomware groups from purchasing services on regular trading platforms or covertly recruiting new members.
Ransomware groups continue to thrive, with developments such as recent leaks of ransomware source code have providing opportunities for emerging threat actors to develop new variants. Furthermore, while discussions of ransomware payloads are generally avoided, supporting services — such as Initial Access Brokers selling access to compromised organizations — remain widely available. In fact, many ransomware groups function as affiliate programs, heavily relying on these services for their continued operations.
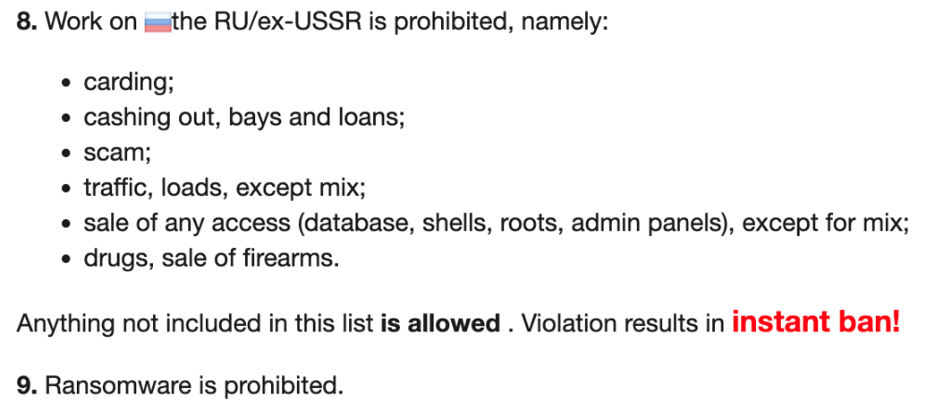
Figure 3. Forum rules showing ransomware discussion as a banned topic
Phishing and Account Takeovers
Phishing in the Russian-speaking underground is a highly developed field, with developers focusing on creating phishing kits rather than just selling them. Russian-speaking forums provide ample employment opportunities for skilled individuals (like those who can clone banking sites for supporting phishing kits) in niche markets.
Phishing attacks can vary in scale, from mass campaigns to highly targeted attacks. The underground ecosystem also offers extensive resources, including tools, services, and comprehensive tutorials, to assist cybercriminals in refining their phishing tactics.
Cybercriminals use phishing and credential-stuffing attacks to infiltrate organizations, often using social engineering tactics to gain access to sensitive systems. These activities fuel underground supply chains that provide access to corporate networks.
Stolen credentials and data harvested through phishing campaigns are frequently traded or sold on these underground marketplaces. These can include anything from corporate login credentials to full financial profiles (or even AI-related accounts as seen in the following image):
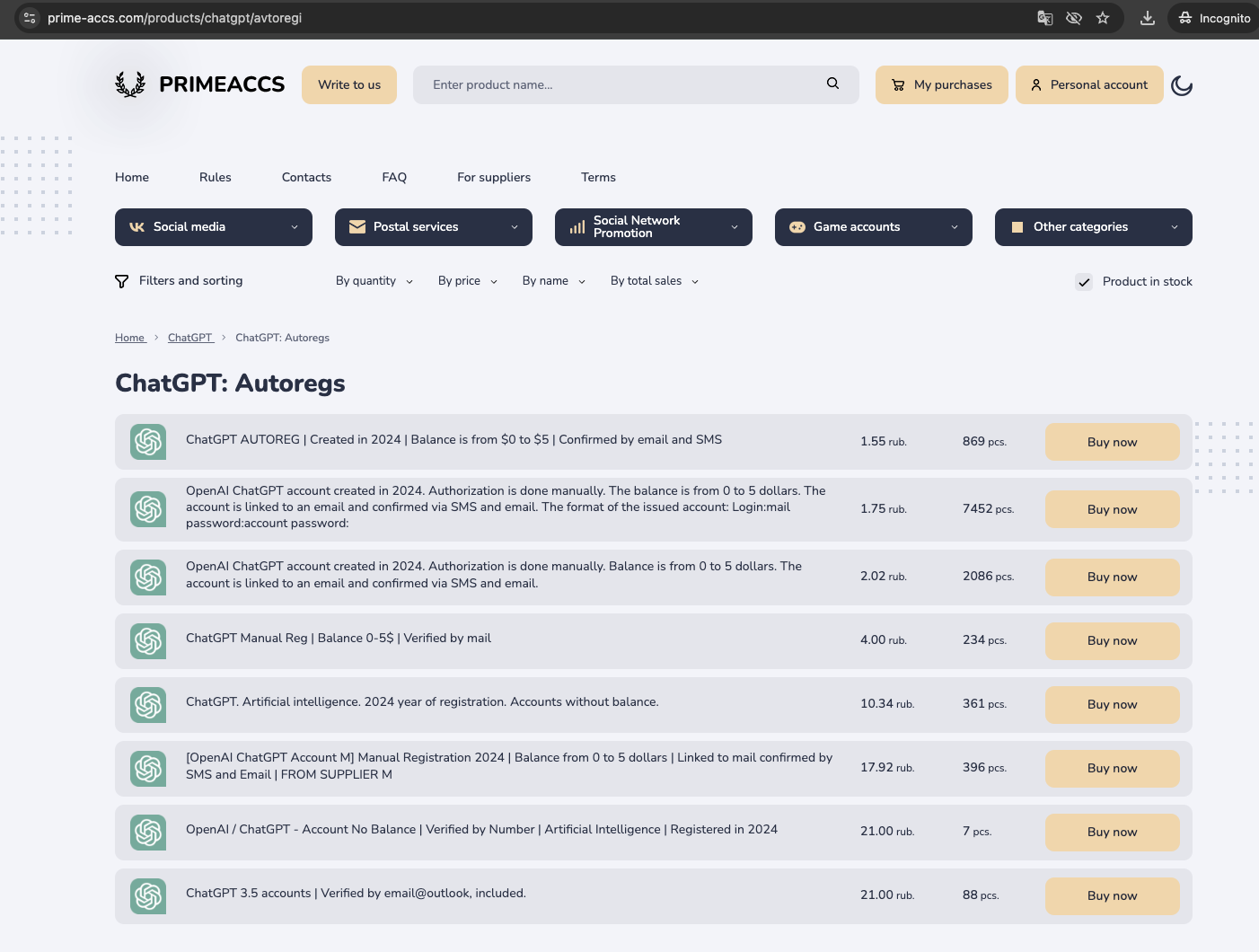
Figure 4. Stolen ChatGPT accounts priced in Russian ruble (as little as $US 0.02 per account)
Cyber-Physical Crime Integration
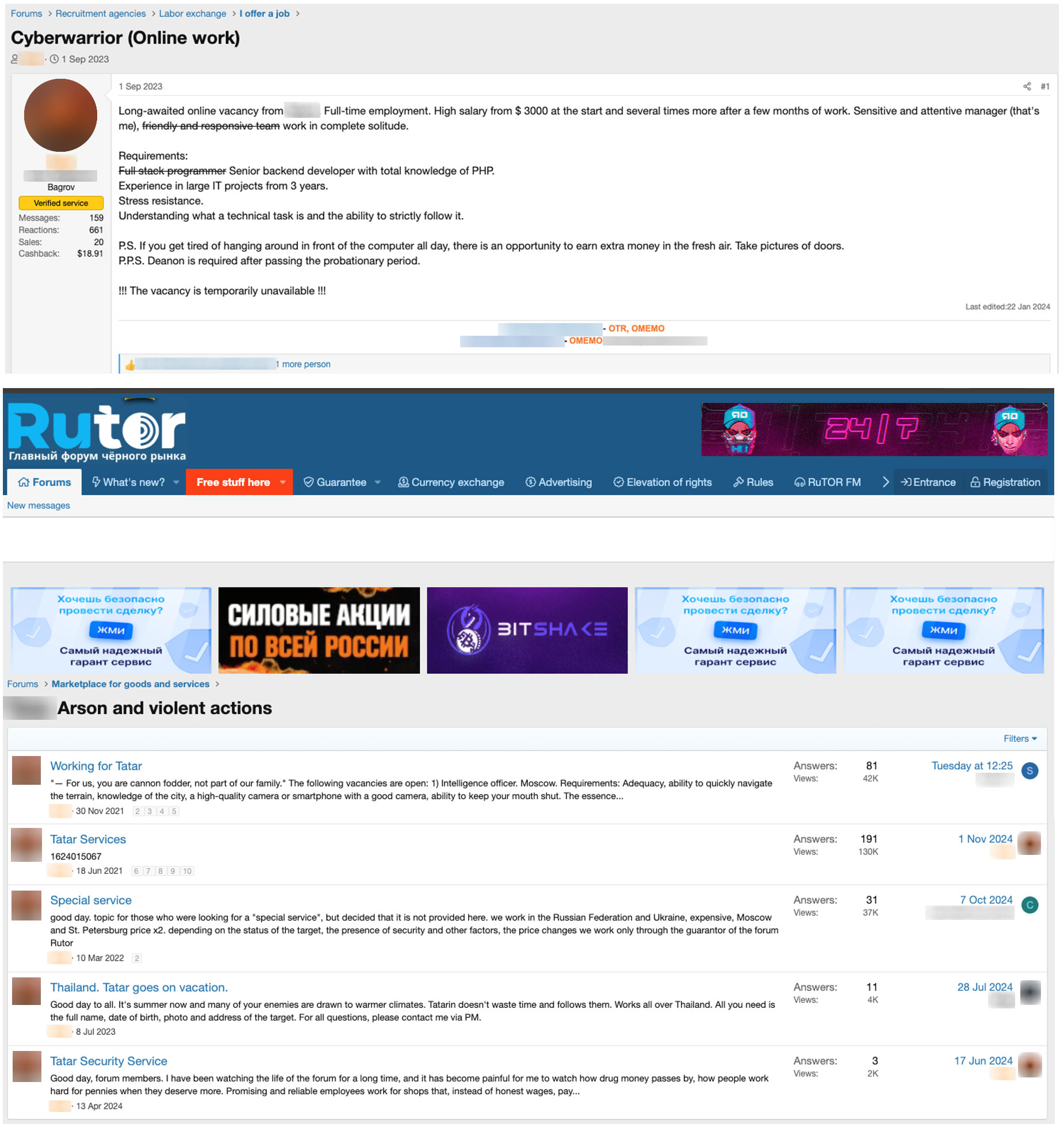
A growing trend in the Russian-speaking underground is the intersection of cybercrime with traditional organized (and physical) crime. Cybercriminals increasingly offer services such as “violence-as-a-service” and intelligence-gathering on behalf of physical crime groups.
Figure 5. Offerings posted by a threat actor involved in both cybercrime and physical crime
These services often integrate open-source intelligence (OSINT) and human intelligence (HUMINT) techniques. Advertisements for such services have appeared on underground forums, sometimes alongside job postings for tech-related roles, highlighting the convergence of cyber and physical crime.
Beyond physical violence, underground markets also offer psychological operations (psyops) aimed at harassing and intimidating victims. These tactics include persistent threatening calls, SIM card blocking, and other disruptive actions, with discussions on such services attracting significant attention within underground communities.
Geopolitical and Social Changes Impacting Cybercrime
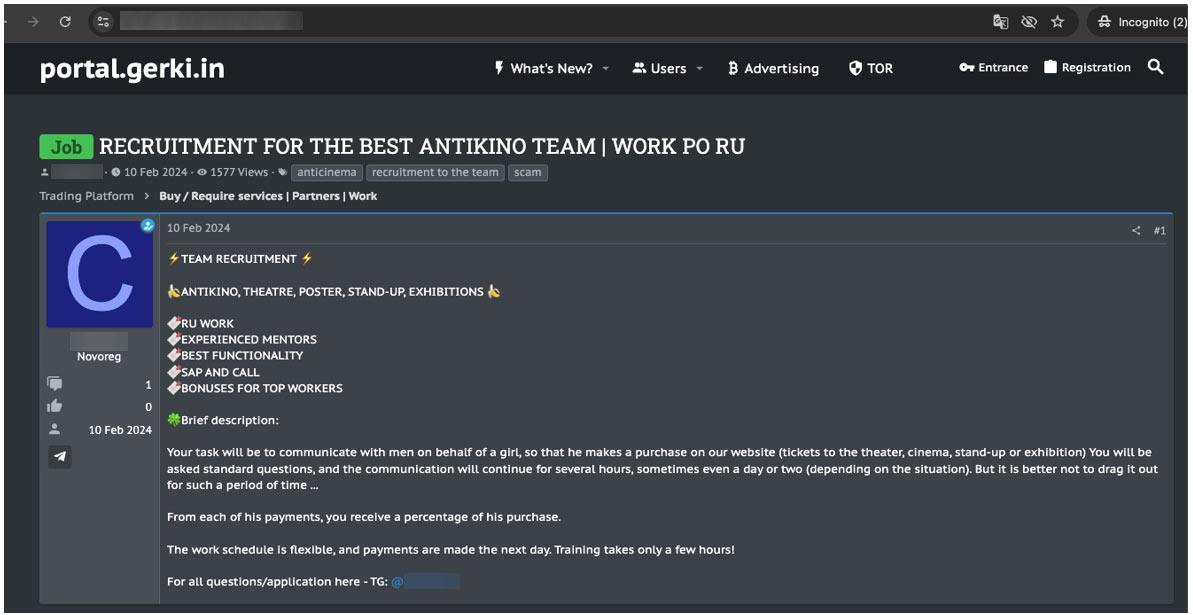
The geopolitical landscape significantly influences cybercriminal priorities. The ongoing conflict between Russia and Ukraine, among other regional tensions, has altered cybercriminal relationships and the scope of "acceptable targets." These shifts have impacted digital, financial, and physical supply chains, affecting how underground actors conduct operations. One of the most notable changes is the increased willingness to break the long-standing "Do not work in RU" rule, as some criminals now perceive a lower risk of law enforcement collaboration due to geopolitical tensions. This shift has led to an increase in cyberattacks targeting both Russia and Ukraine, with underground forums hosting job postings and services aimed at exploiting these regions.
Figure 6. Job posting for scams in Russia
Government-aligned threat actors are also using underground cybercriminal services to achieve strategic objectives while maintaining plausible deniability. By combining financially motivated attacks with politically driven campaigns, threat actors can obscure their involvement in cyber operations. Hacktivism has also seen an increase as ideological motivations drive cybercriminal and nation-state groups to target governments, military organizations, and critical infrastructure. These attacks are often disguised as activism but serve broader criminal or political agendas.
Sanctions and economic restrictions have forced cybercriminals to seek new cash-out methods and relocation options, broadening the underground's geographical reach. Simultaneously, there has been growing collaboration between Russian- and Chinese-speaking cybercriminal communities, with Chinese actors increasingly engaging in Russian-speaking forums. These groups have become major players in initial access brokering, exploit trading, and recruiting cybercriminal talent, further globalizing the cybercrime ecosystem.
Conclusion
The cyber risk landscape for organizations has shifted due to the increasing capabilities of cybercriminals, the reshaping of cultural ties and ethical boundaries, closer international collaboration, and the growing synergy between cybercrime and nation-state-backed groups. These changes have shifted the cybersecurity focus towards a more risk-driven approach to attack surface defense.
With greater financial resources, cybercriminals can implement more sophisticated monetization schemes that exploit advanced tools and vulnerabilities. Meanwhile, international collaboration has introduced new attacker capabilities and business processes across geographical regions. Changes in ethical boundaries have expanded the range of targets to include critical industries and previously off-limits locations.
Geopolitical events, particularly conflicts like the Russia-Ukraine war, have reshaped the Russian-speaking cyber underground, altering targeting rules, alliances, and operational priorities. While criminals previously avoided attacks on Russian-speaking regions, reduced law enforcement risks and rising hostility have led to increased targeting of both Russia and Ukraine.
These shifts have disrupted trust within cybercriminal communities, forcing adaptation in monetization strategies and operational networks. Sanctions have driven many criminals to relocate, expanding the underground market’s operations.
The increasing collaboration between nation-state-aligned actors and cybercriminal groups further complicates the threat landscape, with groups selling or purchasing access to compromised systems for financial or strategic gain.
To address these evolving threats, governments and businesses must integrate leading security platforms, advanced threat intelligence, and strategic analysis into their Cyber Risk Exposure Management (CREM) procedures, ensuring they can effectively counter the increasing sophistication and coordination of cyber threats.
For a deeper understanding of these trends and their implications, read our research paper, “The Russian-speaking Underground,” the 50th installment in our ongoing series. This report provides a comprehensive analysis of the evolving underground cybercriminal landscape, detailing key developments, emerging threats, and the influence of geopolitics and culture on cybercrime. Download the full paper to stay ahead of the latest underground activities and their impact on global security.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Related Posts
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- The Future of Social Engineering
- Metaverse or Metaworse? How the Apple Vision Pro Stacks Up Against Predictions
- Understanding Hacktivists: The Overlap of Ideology and Cybercrime
- Across the Span of the Spanish Cybercriminal Underground: Current Activities and Trends
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks