Ransomware Spotlight: 8Base
Top affected countries and industries according to Trend Micro threat intelligence data
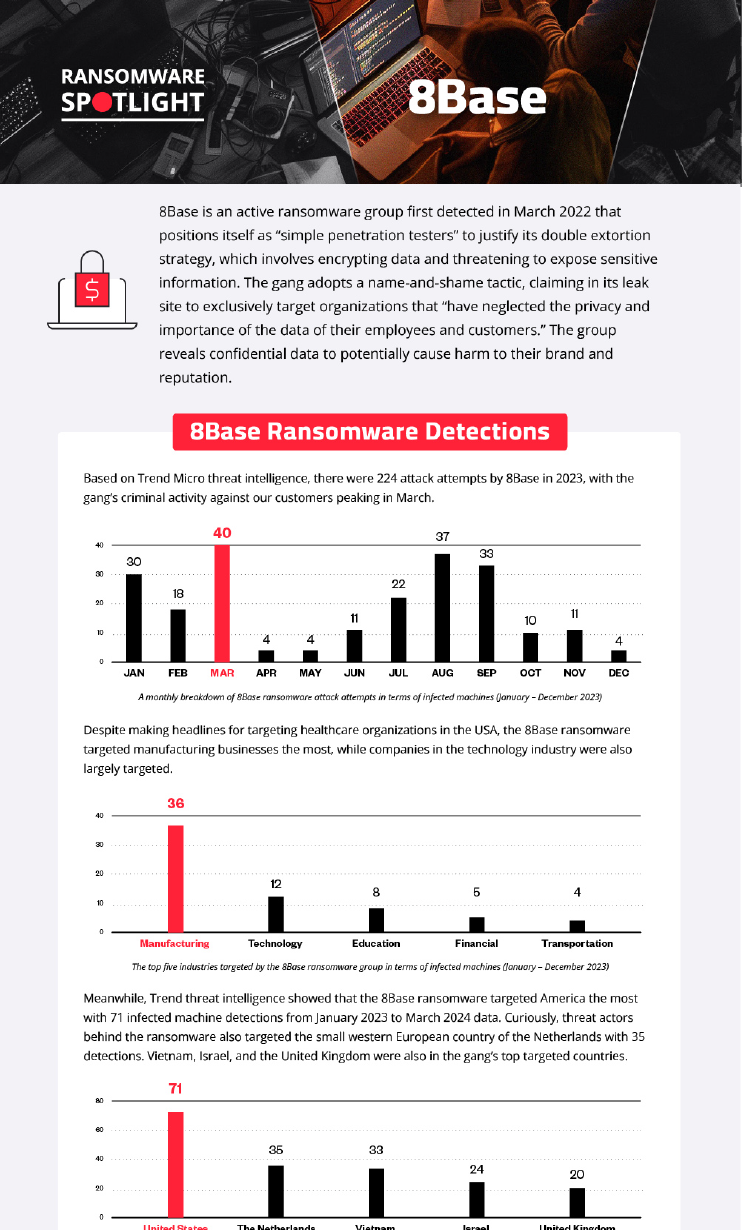
Based on Trend threat intelligence data, there were 224 attack attempts by 8Base in 2023, with the gang’s criminal activity against Trend customers peaking in March.
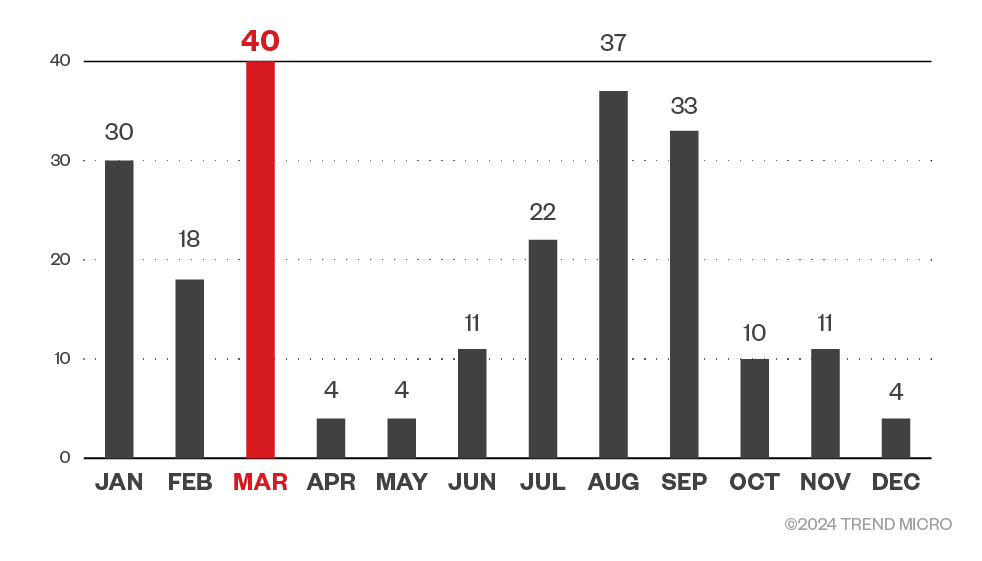
Organizations in the manufacturing industry were targeted the most by 8Base ransomware, while companies in the technology industry were also largely targeted. Beyond the top five industries specified in Figure 2, organizations in healthcare, oil and gas industries, and the government were also targeted by 8Base. It should be noted that the data in Figure 2 covers Trend Micro customers who have chosen to provide information on the industry they belong to.
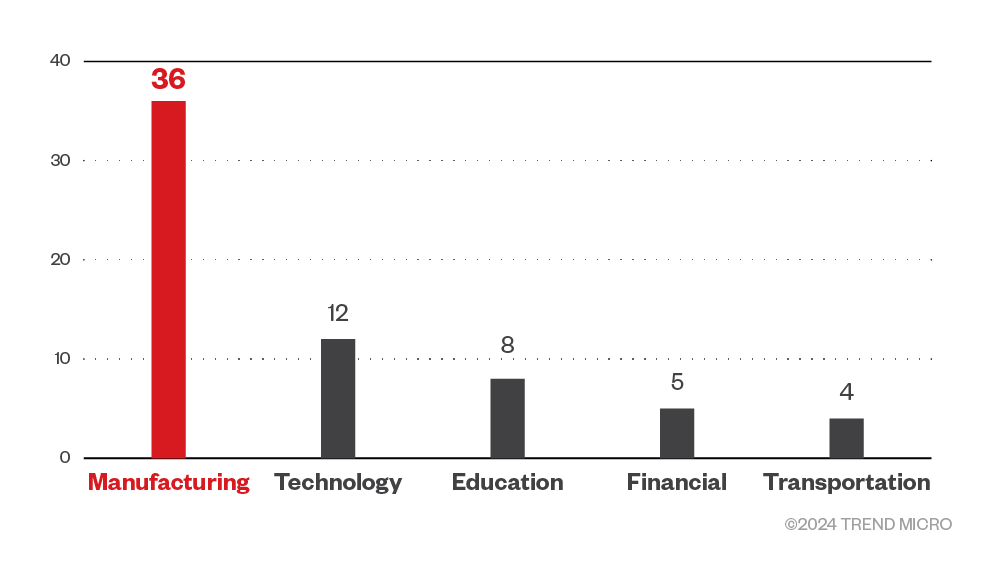
Meanwhile, Trend threat intelligence showed that the 8Base ransomware targeted America the most with 71 infected machine detections from January 2023 to March 2024 data. Curiously, threat actors behind the ransomware also targeted the small western European country of the Netherlands with 35 detections. Vietnam, Israel, and the United Kingdom were also in the gang’s top targeted countries.
Targeted regions and industries
according to 8Base ransomware’s leak site
This section looks at data based on attacks recorded on the leak site of the 8Base ransomware from May 2023 to March 2024.
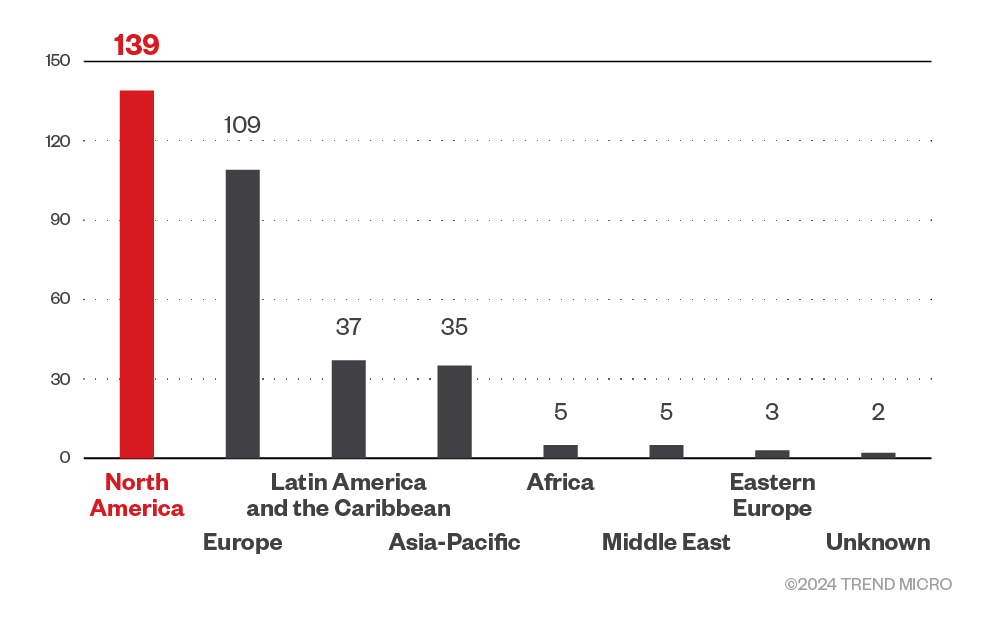
Based on a combination of our open-source intelligence (OSINT) research and an investigation of the leak site, the 8Base ransomware gang targeted organizations in North America the most, while also spending significant time on European corporations.
Figure 4. The distribution by region of 8Base ransomware’s victim organizations
Source: 8Base ransomware’s leak site data and Trend Micro’s OSINT research (May 2023 – March 2024)
A closer look shows that the gang’s efforts were significantly focused on American organizations, but it also targeted Brazilian institutions as well as those from the United Kingdom, France, Canada, and Australia. Interestingly, 8Base ransomware also targeted smaller countries such as Costa Rica, Croatia, and the Bahamas.
Figure 5. The top five countries targeted by 8Base ransomware
Source: 8Base ransomware’s leak site data and Trend Micro’s OSINT research (May 2023 – March 2024)
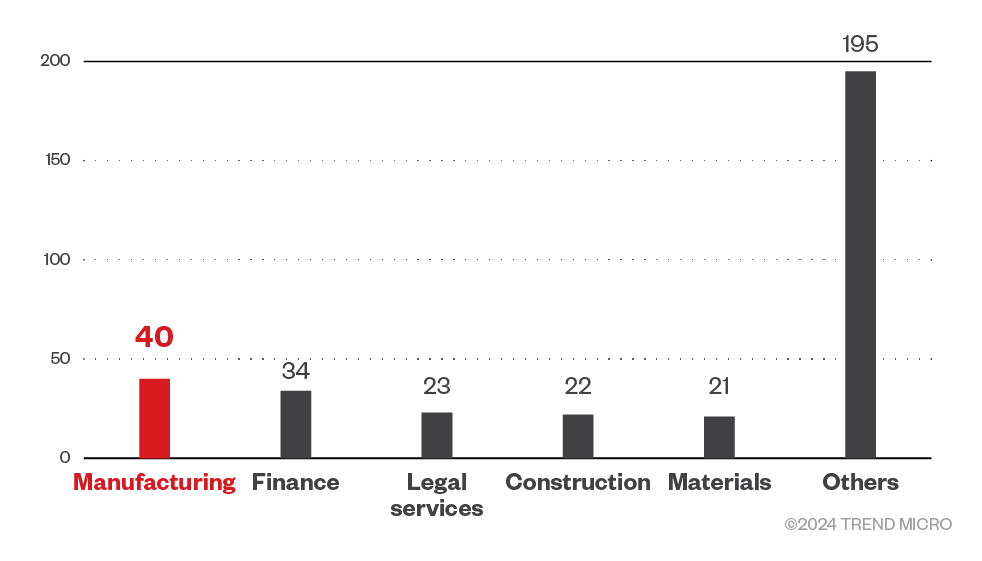
Threat actors behind 8Base ransomware targeted a wide range of sectors including real estate businesses, legal services companies, and hospitality-related establishments. However, they focused their efforts the most on businesses in the manufacturing and finance sectors.
Figure 6. The top 5 sectors targeted by 8Base ransomware
Source: 8Base ransomware’s leak site data and Trend Micro’s OSINT research (May 2023 – March 2024)
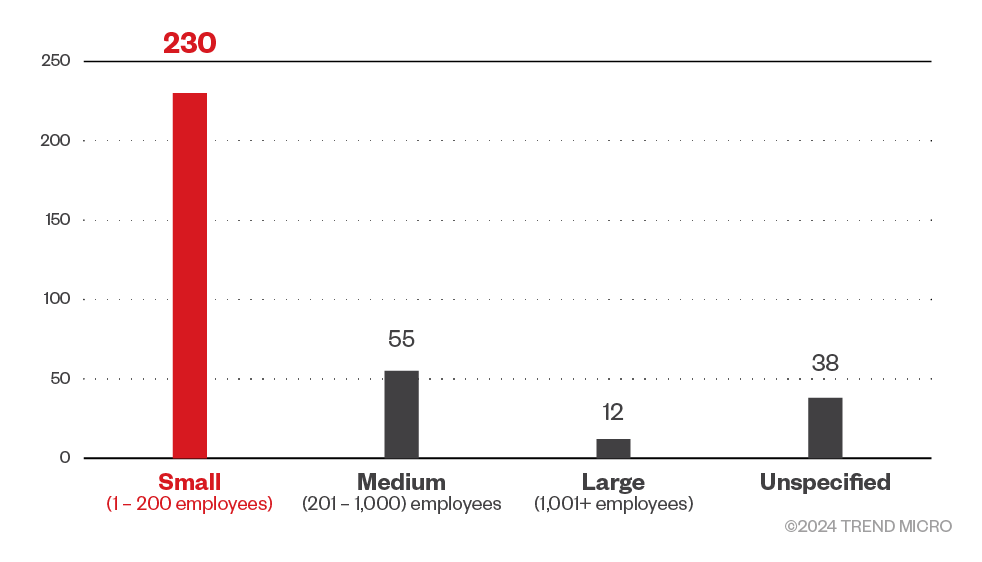
The 8Base ransomware targeted small business the most, despite or perhaps because the gang positioned themselves as pen testers; penetration testing usually aims to identify weak spots in a system’s defenses that can be taken advantage of by attackers. It could be assumed that instead of big corporations, the gang targeted small business to teach them a “lesson” while also gaining profit.
Figure 7. The distribution by organization size of the 8Base ransomware victims
Source: 8Base ransomware’s leak site data and Trend Micro’s OSINT research (May 2023 – March 2024)
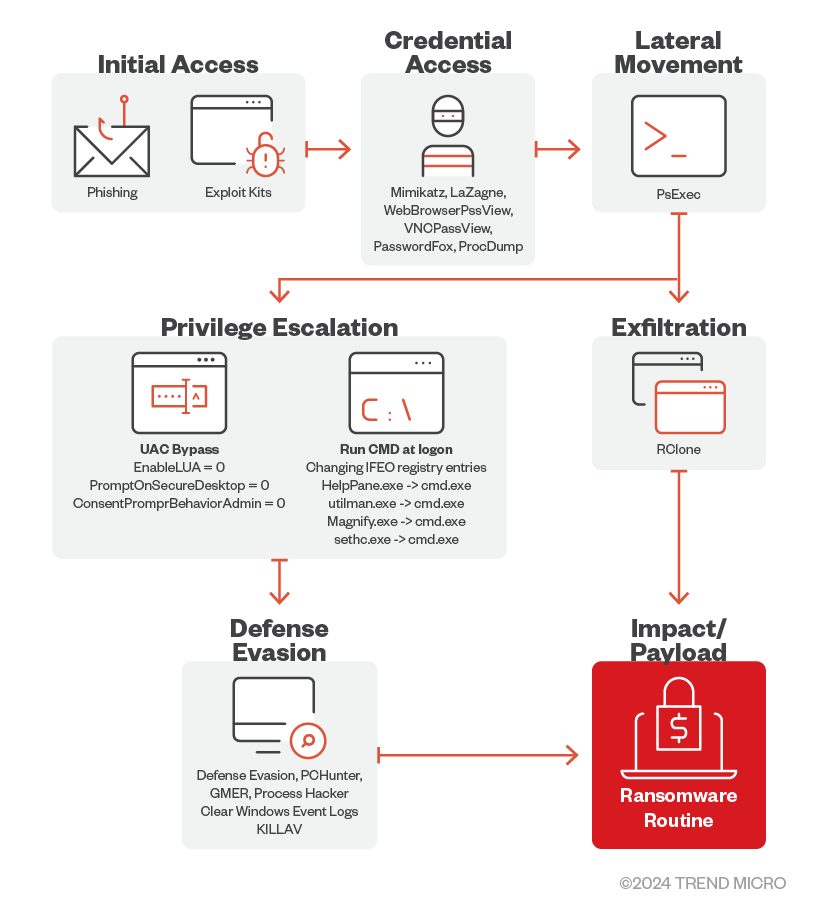
Initial Access
- The 8Base ransomware primarily uses phishing scams for initial access.
Credential Access
- 8Base operators use MIMIKATZ, LaZagne, WebBrowserPassView, VNCPassView, PasswordFox, and ProcDump to retrieve passwords and credentials on their victim’s machines.
Defense Evasion
- For its defense evasion, the 8Base ransomware drops and executes a batch file named defoff.bat detected as KILLAV to disable components of Windows Defender.
- The 8Base ransomware also uses garbage codes, deletes shadow copies, bypasses Cuckoo Sandbox, clears Windows event logs, disables firewalls, and uses SmokeLoader to decrypt and deliver the payload.
- 8Base operators also uses other tools such as PCHunter, GMER, and Process Hacker.
Lateral Movement
- It has been observed that the 8Base ransomware operators use PsExec to deploy the batch file as well as the ransomware binary.
Privilege Escalation
- 8Base ransomware operators modified certain registry entries to bypass User Access Control (UAC).
- They also modified IFEO registry keys to attach cmd.exe to accessibility programs that are accessible from the lock screen.
Exfiltration
- The threat actors behind 8Base ransomware have been detected using the third-party tool and web-service RClone to exfiltrate stolen information.
Impact
- The 8Base ransomware uses AES-256 algorithm to encrypt target files and then encrypts each encryption key using RSA-1024 with a hardcoded public key. The encrypted key is then appended to the end of each encrypted file. It has an embedded configuration (decrypted during runtime) which contains the file extensions, file names, and folders to avoid.
Additional information
- The 8Base ransomware terminates the following processes to avoid conflict in its encryption routine:
- msftesql.exe
- sqlagent.exe
- sqlbrowser.exe
- sqlservr.exe
- sqlwriter.exe
- oracle.exe
- ocssd.exe
- dbsnmp.exe
- synctime.exe
- agntsvc.exe
- mydesktopqos.exe
- isqlplussvc.exe
- xfssvccon.exe
- mydesktopservice.exe
- ocautoupds.exe
- agntsvc.exe
- agntsvc.exe
- agntsvc.exe
- encsvc.exe
- firefoxconfig.exe
- tbirdconfig.exe
- ocomm.exe
- mysqld.exe
- mysqld-nt.exe
- mysqld-opt.exe
- dbeng50.exe
- sqbcoreservice.exe
- excel.exe
- infopath.exe
- msaccess.exe
- mspub.exe
- onenote.exe
- outlook.exe
- powerpnt.exe
- steam.exe
- thebat.exe
- thebat64.exe
- thunderbird.exe
- visio.exe
- winword.exe
- wordpad.exe
- 8Base ransomware avoids encrypting files with the following extensions:
- 8base
- actin
- dike
- acton
- actor
- acuff
- file
- acuna
- fullz
- mmxxii
- 6y8dghklp
- shtorm
- nurri
- ghost
- ff6om6
- mnx
- backjohn
- own
- fs23
- 2qz3
- top
- blackrock
- chcrbo
- g-stars
- faust
- unknown
- steel
- worry
- win
- duck
- fopra
- unique
- acute
- adage
- make
- adair
- mlf
- magic
- adame
- banhu
- banjo
- banks
- banta
- barak
- caleb
- cales
- caley
- calix
- calle
- calum
- calvo
- deuce
- dever
- devil
- devoe
- devon
- devos
- dewar
- eight
- eject
- eking
- elbie
- elbow
- elder
- phobos
- help
- blend
- bqux
- com
- mamba
- karlos
- ddos
- phoenix
- plut
- karma
- bbc
- capital
- wallet
- lks
- tech
- s1g2n3a4l
- murk
- makop
- ebaka
- jook
- logan
- fiasko
- gucci
- decrypt
- ooh
- non
- grt
- lizard
- flscrypt
- sdk
- 2023
- vhdv
- fdb
- sql
- 4dd
- 4dl
- abs
- abx
- accdb
- accdc
- accde
- adb
- adf
- ckp
- db
- db-journal
- db-shm
- db-wal
- db2
- db3
- dbc
- dbf
- dbs
- dbt
- dbv
- dcb
- dp1
- eco
- edb
- epim
- fcd
- gdb
- mdb
- mdf
- ldf
- myd
- ndf
- nwdb
- nyf
- sqlitedb
- sqlite3
- sqlite
- 8Base ransomware avoids encrypting files with the following strings: :
- info.hta
- info.txt
- boot.ini
- bootfont.bin
- ntldr
- ntdetect.com
- io.sys
- suppo
- bin.exe
MITRE tactics and techniques
| Initial Access | Persistence | Privilege Escalation | Defense Evasion | Discovery | Impact |
|---|---|---|---|---|---|
T1566 - Phishing: | T1547.001 - Registry Run Keys / Startup Folder: | T1134.001 - Token Impersonation/Theft T1134.002 - Create Process with Token T1548.002 - Bypass User Account Control T1546.008 - Accessibility Features | T1027.001 - Binary Padding T1497.001 - System Checks T1562.004 - Disable or Modify System Firewall T1140 - Deobfuscate / Decode Files or Information T1070.001 - Clear Windows Event Logs | T1083 - File and Directory Discovery T1082 - System Information Discovery T1135 - Network Share Discovery T1057 - Process Discovery | T1486 - Data Encrypted for Impact T1490 - Inhibit System Recovery T1218.005 - System Binary Proxy Execution: Mshta |
Summary of malware, tools, and exploits used
| Initial Access | Phishing | Technique |
| Credential Access | Mimikatz | Hacktool |
| LaZagne | Hacktool | |
| WebBrowserPassView | Hacktool | |
| VNCPassView | Hacktool | |
| PasswordFox | Hacktool | |
| ProcDump | Tool | |
| Lateral Movement | PsExec | Tool |
| SystemBC | Tool | |
| Defense Evasion | KILLAV | Malware |
| SmokeLoader | Malware | |
| PCHunter | Tool | |
| GMER | Tool | |
| Process Hacker | Tool | |
| Exflitration | RClone | Tool |
| Impact | Phobos Ransomware | Malware |
Security recommendations
While the threat actors behind the 8Base ransomware position themselves as penetration testers, their attacks on organizations cannot be seen as a “public service,” since the group extorts and profits off its victims. Organizations should conduct their own penetration tests and find out weaknesses in their systems before cybercriminals can take advantage of them in the guise of teaching lessons in security. As evidenced in the profile of 8Base ransomware’s victims, no business is too small for a robust and comprehensive security system.
To shield themselves against 8Base ransomware and other similar threats, organizations can implement security frameworks that allocate resources systematically to establish a strong defense strategy.
The following are some best practices that organizations can consider to safeguard themselves from ransomware infections:
Audit and inventory
- Take an inventory of assets and data.
- Identify authorized and unauthorized devices and software.
- Make an audit of event and incident logs.
Configure and monitor
- Manage hardware and software configurations.
- Grant admin privileges and access only when necessary to an employee’s role.
- Monitor network ports, protocols, and services.
- Activate security configurations on network infrastructure devices such as firewalls and routers.
- Establish a software allowlist that executes only legitimate applications.
Patch and update
- Conduct regular vulnerability assessments.
- Perform patching or virtual patching for operating systems and applications.
- Update software and applications to their latest versions.
Protect and recover
- Implement data protection, backup, and recovery measures.
- Enable multifactor authentication (MFA).
Secure and defend
- Employ sandbox analysis to block malicious emails.
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network.
- Detect early signs of an attack such as the presence of suspicious tools in the system.
- Use advanced detection technologies such as those powered by artificial intelligence (AI) and machine learning.
Train and test
- Regularly train and assess employees in security skills.
- Conduct red-team exercises and penetration tests.
A multilayered approach can help organizations guard possible entry points into the system (endpoint, email, web, and network). Security solutions that can detect malicious components and suspicious behavior can also help protect enterprises.
- Trend Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of compromise (IOCs)
The IOCs for the threat discussed in this article can be found here. Actual indicators might vary per attack.
Trend Vision One Hunting Query
Trend Vision One customers can use the following hunting query to search for 8Base ransomware within their system:
fullPath:"*.8base" OR fullPath:"*.eight" OR fullPath:"*\\info.hta" OR fullPath:"*\\info.txt" OR (processFilePath:"*\\mshta.exe" AND objectFilePath:"*\\info.hta")
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime



 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One