Mailsploit Creates Undetectable Spoofed Emails
Security researcher Sabri Haddouche recently reported a collection of critical bugs in major email clients. Exploiting these vulnerabilities could allow an attacker to spoof virtually any email address and bypass detection.
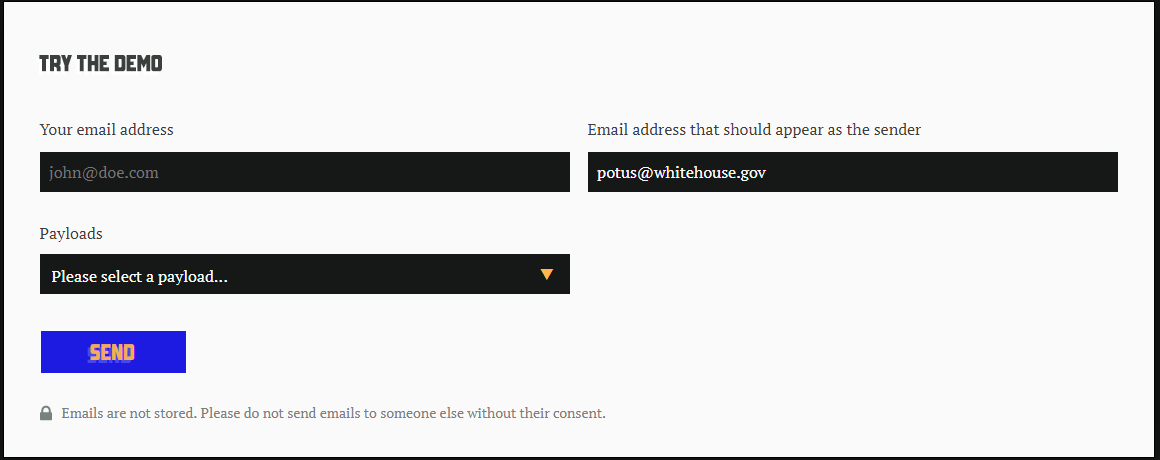
Dubbed Mailsploit, this group of vulnerabilities affects over 30 different mail clients, including prominent applications like Apple Mail, Microsoft Outlook, Mozilla Thunderbird, and Yahoo! Mail. When vulnerable clients are sent fraudulent emails using Mailsploit, they appear to come from completely legitimate senders. In his demo, Haddouche successfully sent an email that appeared to come from ‘potus@whitehouse.gov’.
The Mailsploit page indicates that only 24% of the affected clients have provided fixes as of December 5, which leaves users of numerous other email clients vulnerable to attacks using fraudulent Mailsploit emails. The researcher provides a document tallying the responses of each of the affected products.
Users of vulnerable clients are exposed to a wide range of possible email attacks. BEC scams become much easier to execute because employees won’t be able to distinguish if the email is coming from their boss or a fraudster. Employees are unlikely to question instructions from an email address they recognize as the company CEO’s.
Over the years, email clients have become much smarter about separating spoofed emails from legitimate ones. The authentication protocol Domain-based Message Authentication, Reporting & Conformance (DMARC) is designed to filter out spoofed emails by detecting if the activity is legitimately coming from the sender. According to the researcher, Mailsploit circumvents anti-spoofing mechanisms like DMARC by taking advantage of an old protocol that prescribes how the applications read and display the sender’s email address.
Haddouche's analysis indicates, “In an email, all headers must only contain ASCII characters, including the “From” header. The trick resides in using RFC-1342 (from 1992!), a recommendation that provides a way to encode non-ASCII chars inside email headers in a such way that it won't confuse the MTAs processing the email. Unfortunately, most email clients and web interfaces don’t properly sanitize the string after decoding which leads to this email spoofing attack.”
The email providers were notified of the vulnerabilities months before the release of the report, and as mentioned above, some have fixed the problem. But for all users, now more than ever, it is important to practice safe email habits. Here are some tips on how to keep your mail secure:
- Verify the sender and evaluate the emails you receive—if you aren’t expecting an email from that particular sender, check if it is a legitimate email before replying. Try to contact the sender through other means.
- Keep your applications updated. The email providers were forewarned about Mailsploit to give them time to work on solutions. Make sure you have the latest versions of the apps you use to defend against exploitable bugs and vulnerabilities.
- Enterprise security professionals should adopt security measures such as Sender Policy Framework (SPF), Sender ID, and DomainKeys Identified Mail (DKIM) to protect their organizations from spoofing and other email threats.
- Stay vigilant. Educate yourself on the latest threats, and spread the word to others on your network.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks