Bogus Facebook Messenger Installer Leads to a Backdoor
Publish date: 2011年4月20日
Social networking sites have become the preferred medium for connecting with friends and family as well as for sharing information. Cybercriminals are taking advantage of this fact, launching targeted attacks on social media users. While these attacks are not entirely new, they remain persistent.
In line with this, TrendLabs engineers recently found a new threat that may imperil Facebook users.
How does the malware arrive on users' systems?
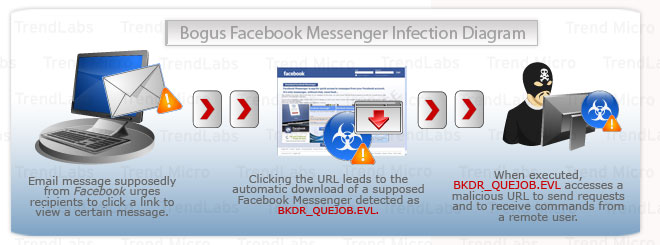
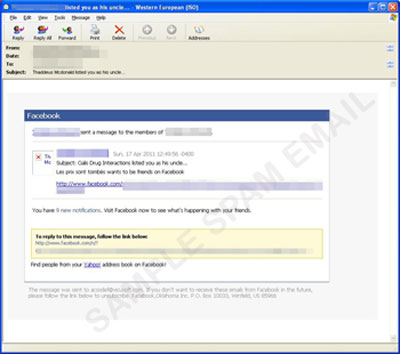
The malicious file (aka FacebookMessengerSetup.exe), detected as BKDR_QUEJOB.EVL, arrives via spammed messages posing as a Facebook notification. The email message urges the recipient to click a URL to view a certain message. Clicking the URL, however, leads to the automatic download of the fake application installer.
When executed, BKDR_QUEJOB.EVL opens TCP port
1098 to listen for commands from a remote user. These commands may include
updating the malicious file, downloading and executing files, and starting certain
processes. It also connects to {BLOCKED}.{BLOCKED}.216.50 to send requests and to receive
commands from a remote user, hence compromising a system’s security. The
backdoor program also identifies the antivirus installed on the system, if any.
It then sends this information to an SMTP server with the address smtp.{BLOCKED}il.ru via email. Apart
from this, it also determines the OS version installed on the system.
Is this type of attack new?
No, as TrendLabs engineers have come across several threats
that ride on Facebook’s immense
popularity. In fact, we recently reported spam informing users that their Facebook passwords are unsecure. The said spammed message comes with a malicious attachment detected as TROJ_DOFOIL.VI. We also spotted a fake stalker tool detected as HTML_FBSPAM.ASM
that supposedly lets users know who visits their profiles. We also found a bogus Facebook toolbar detected as IRC_ZAPCHAST.HU that supposedly helps users more easily connect with friends. Finally, we also spotted attacks taking advantage of Facebook’s credit feature, which led to the creation of an event that led curious users who click a malicious link to certain Canadian Pharmacy sites.
How does this malware affect users?
BKDR_QUEJOB.EVL poses as a Facebook Messenger Installer. Unsuspecting
users who execute this backdoor program thus gives a remote malicious user an
opportunity to execute any command on their systems.
Why are Facebook-related scams
noteworthy?
Cybercriminals
often ride on the popularity of social networking sites like Facebook and Twitter to lure victims. These sites’ ever-growing population of
active users will only entice more and more cybercriminals to target them. Cybercriminals
often capitalize on the implicit level of trust social networking site users
place on their contacts, thus tricking them to click malicious links.
While
Facebook scams are no longer uncommon,
these still pose huge risks like system infection as well as data and identity
theft for users. In fact, stolen social media site login credentials and other
personally identifiable information (PII) usually end up in the hands of
cybercriminals.
To
know more about other social media threats, read “Spam,
Scams, and Other Social Media Threats.”
Are Trend Micro product users protected from
this malware?
Yes, the Trend
Micro™ Smart Protection Network™ email reputation
technology prevents spammed messages from even reaching users’ inboxes. The Web
reputation technology, on the other hand, blocks access to the malicious URL. Finally,
the file reputation technology prevents the execution of the backdoor program on
users’ systems. It also effectively detects and deletes the known components of
this and similar attacks.
What can users do to prevent the execution of
this malware on their systems?
Users should be wary of dubious-looking email
messages even if these come from known sources. It is also advisable to stay
abreast of the latest threat information. Awareness can prevent data loss and system
infection.
Expert Insights
"Facebook is becoming more and more a very good platform for infection. It's easy to become a developer, therefore creating malicious applications. This, coupled with the tendency we have of trusting our own contacts, makes it a good platform to spread bad links. Let's not forget that bad links are today's web version of malicious files. You click on one and you're infected." —David Sancho, Senior Threat Researcher
