From Russia with Love (of Malicious Apps)
Publish date: 2012年7月9日
2012 has been great year for the popular photo–sharing app Instagram. Its Android version has been a resounding success with 5M downloads just days after its launch. Instagram was also acquired by Facebook for $1B.
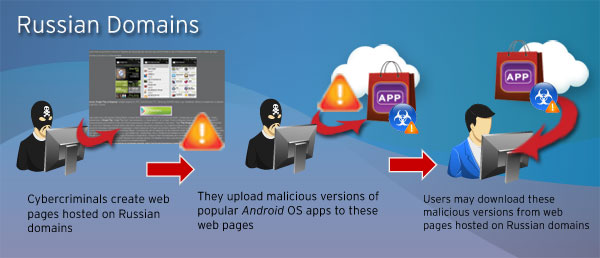
But there is also a catch for such popularity. Cybercriminals have taken advantage of Instagram’s success by offering a fake Instagram app for Android users. This does not appear to be an isolated incident. We have also found other malicious apps hosted on Russian domains, including fake versions of Farm Frenzy and Flash Player. There was even a website that mimicked Google Play.
In a previous blog entry, we wrote about developers who typically host Trojanized or malicious apps on third-party app stores hosted in China. But Russian sites hosting Android malware are giving their Chinese counterparts a run for their money. Based on data from the Smart Protection Network™, there has been an increase in Russian domains peddling malicious apps this year. From 2,946 URLs in 2011, the number of Russian domains hosting Android malware went up to 6,734 for July 2012.
Why are malicious Android apps now being hosted on Russian domains?
As previously mentioned, third-party app stores hosted in China are the usual hot spots for malicious Android apps. Because of Android’s popularity in the country and the intermittent access to Google Play in China, third-party stores became a viable option for Chinese mobile users. Naturally, cybercriminals grabbed this opportunity to distribute their own malicious apps via these third-party app stores
Russian domains are now figuring in on the Android mobile threat landscape. This may be attributed to the stricter rules imposed by China Internet Network Information Center (CNNIC) during the latter part of 2010. The organization changed some of its domain registration rules which require applicants to submit a formal paper-based application containing the registrant’s identification, among other things. These enforced rules and China’s determination to clean up its act may have deterred anonymity-seeking cybercriminals from registering domains hosted in the country.
Russia on the other hand, remained lax with their domain registration regulations. This may have prompted cybercriminals to revert to using Russian domains.
What are the noteworthy Android apps hosted on Russian domains?
Below are some noteworthy malicious apps we’ve seen available on web pages hosted on Russian domains.
Farm Frenzy 3
We uncovered malicious versions of the popular game Farm Frenzy. Based on our analysis, the malicious app detected as ANDROIDOS_FAKE.DQ is a premium service abuser that sends messages to specific premium numbers.
Rogue Instagram for Android and Angry Birds Space
Instagram and Angry Birds are two of the most sought-after titles downloaded by millions. This compelled cybercriminals to create their own malicious versions. Detected as ANDROIDOS_SMSBOXER.A, this fake app seeks permissions to send a query using short numbers. Instead, it just sends a message to a particular number. The rogue app also connects to specific URLs.
Fake Flash Player App
We found a fake Adobe Flash Player app available on a web page hosted on another Russian domain. To entice users to download this fake app, the page claims that it is compatible with any Android OS version. Once users download and install this app, the site connects to a different URL to download a malicious .APK file detected as ANDROIDOS_BOXER.A. This malware is a premium service abuser that sends messages to premium numbers without the user’s consent or knowledge.
Others
Fake Google Play Site
When the Android Market was renamed to Google Play, cybercriminals took advantage of this by creating their own version of Google Play. The fake version of Google Play was hosted on Russian domains and led users to rogue apps detected as ANDROIDOS_SMSBOXER.AB. This is a premium abuser type of mobile malware, which subscribes infected devices to premium services without the user’s permission.
Why is this trend noteworthy?
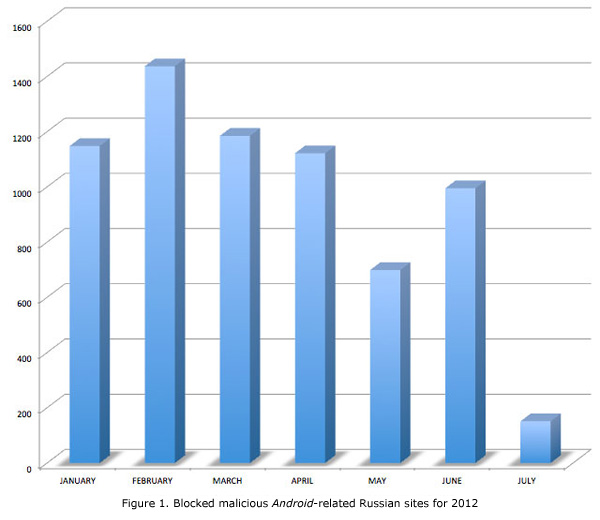
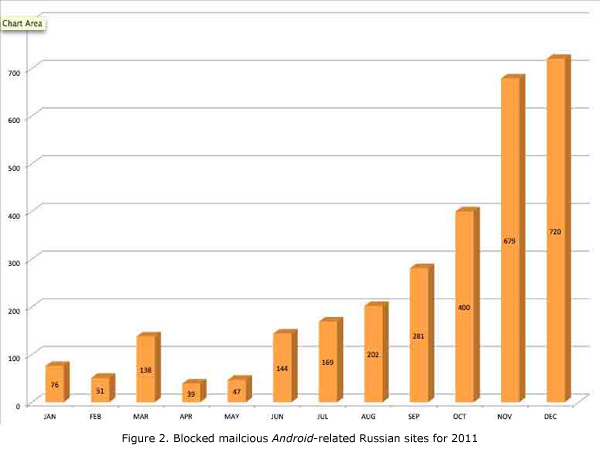
Malicious and Trojanized apps are not limited to Google Play and Chinese third-party stores. Based on the Smart Protection Network™�data, we blocked a total of 6,734 malicious Android-related sites hosted on Russian domains since January 2012 up to July 4, 2012. This is an increase from the number of blocked Russian websites in 2011, which totaled 2,946.
Based on the mobile apps they have copied so far, malicious developers behind the Russian domains are also riding on their popularity. The highly anticipated Instagram for Android, for example, was downloaded 5M times less than a week after its release. Naturally, cybercriminals who may have wanted to take part of the Instagram craze created their own versions and hosted these on their own web pages. The people behind the fake Google Play page also took advantage of the recent renaming of Android Market, in hopes that some users may confuse this site for the legitimate one.
Once installed in the mobile device, premium service abusers like ANDROIDOS_SMSBOXER.A send messages to particular premium numbers without the user’s consent. In turn, affected users are left with unnecessary charges for these sent messages.
Who are affected?
This proliferation of malicious Russian sites hosting fake apps affects users with mobile devices running on Android OS. In their desire to download popular apps not yet available on Google Play, users may seek alternative web pages that supposedly host these apps. As mentioned, the fake version of Google Play may dupe users into thinking that it is a legitimate site.
How do I protect myself from this threat?
Download from Google Play. Though Google Play inadvertently hosted a few dubious apps, the official site is still the best bet to download safe apps for users of Android-based smartphones.
Scrutinize every app you download. Be wary of downloading apps from third-party stores. A better option is to download apps available on Google Play, though certain malicious apps find their way there, too. As such, scrutinize apps before downloading these.
Do your research. Familiarize yourself with trusted developers. Make it a habit to read reviews and ratings for the apps to know if apps exhibit any suspicious routines and to know other users’ feedback.
Read app permissions carefully. It is typical for apps to seek certain permissions from mobile devices in order to function. However, malicious apps may ask for more permissions than actually needed. Thus, it’s important to carefully read and understand these permissions.
Invest in a trusted mobile security app. Sometimes being careful isn’t always enough. Malicious apps may slip through the cracks at certain moments, thus investing on a trusted mobile security can help you identify malware before even reaching your smartphone/mobile device.
What kind of protection does Trend Micro offer for these Russian sites and the malicious apps they offer?
Trend Micro protects users’ mobile devices via Trend Micro Mobile Security, which detects and deletes malicious apps, when you download one via your mobile device. For users who download via the web, Trend Micro Smart Protection Network™ blocks access to these malicious Russian web pages.
FROM THE FIELD: EXPERT INSIGHTS
Many Android threats arrive via third-party app stores. While the app stores are not necessarily malicious, they simply do not have the resources to adequately curate submissions. As a result, malicious, repackaged, and pirated applications are frequently found in these independent app stores. - Kervin Alintanahin, Threat analyst
With additional inputs from Paul Pajares