Spam Campaign Leads to Azorult Trojan Spyware
Publish date: 22 de agosto de 2018
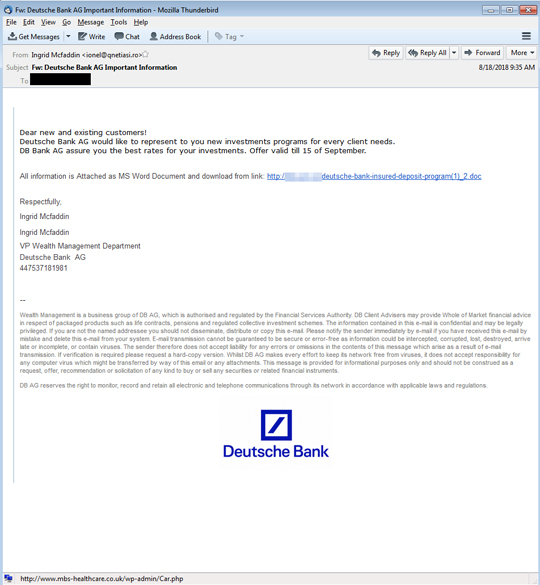
Similar to EMOTET’s arrival, Trojan spyware Azurolt has been spotted coming in the form of a spoofed bank notification. The spam campaign is making the rounds in Germany and UK.
The email prompts the user to download a doc file using the malicious link different from what is displayed:
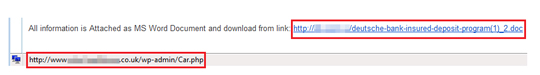
The URL downloads from a fake db.com site:

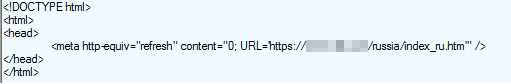
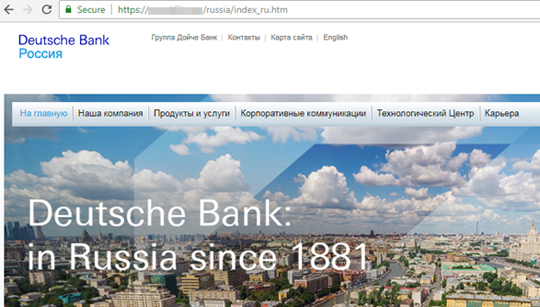
Then redirects to the real db.com:
Once the user enables the macro (detected as W2KM_POWLOAD.NSFGAIBA), it downloads the Godzilla loader (detected as TROJ_ZIGDOLL.A) from the fake db.com site via PowerShell. It then downloads the Azurolt malware (detected as TSPY_AZORULT.A), designed to steal information.
Fecha/hora de bloqueo del spam: 22 de agosto de 2018 GMT-8
TMASE
- Motor TMASE: 8.0
- Patrón TMASE: 4048