Adware.Win32.FusionCore.AD
Downloader.Win32.Funshion.gen (KASPERSKY); Riskware/FusionCore (FORTINET)
Windows

Tipo de malware
Adware
Destructivo?
No
Cifrado
No
In the Wild:
Sí
Resumen y descripción
It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites. Puede haberlo instalado manualmente un usuario.
Se conecta a determinados sitios Web para enviar y recibir información.
Detalles técnicos
Detalles de entrada
It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Puede haberlo instalado manualmente un usuario.
Instalación
Infiltra los archivos siguientes:
- %User Temp%\is-{5 Random Characters}.tmp\{Malware name}.tmp
- %User Temp%\is-{5 Random Characters}.tmp\OqIEFuprtaC.dll
- %User Temp%\is-{5 Random Characters}.tmp\itdownload.dll
- %User Temp%\is-{5 Random Characters}.tmp\isxdl.dll
- %User Temp%\nsd{Random Characters}\csshover3.htc
- %User Temp%\nsd{Random Characters}\css\ie6_main.css
- %User Temp%\nsd{Random Characters}\css\main.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\browse.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\checkbox.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\progress-bar.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\button-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg-corner.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg2.png
- %User Temp%\nsd{Random Characters}\images\Loader.gif
- %User Temp%\nsd{Random Characters}\locale\AF.locale
- %User Temp%\nsd{Random Characters}\locale\AZ.locale
- %User Temp%\nsd{Random Characters}\locale\BE.locale
- %User Temp%\nsd{Random Characters}\locale\BG.locale
- %User Temp%\nsd{Random Characters}\locale\BS.locale
- %User Temp%\nsd{Random Characters}\locale\CA.locale
- %User Temp%\nsd{Random Characters}\locale\CS.locale
- %User Temp%\nsd{Random Characters}\locale\DA.locale
- %User Temp%\nsd{Random Characters}\locale\DE.locale
- %User Temp%\nsd{Random Characters}\locale\EL.locale
- %User Temp%\nsd{Random Characters}\locale\EN.locale
- %User Temp%\nsd{Random Characters}\locale\ES.locale
- %User Temp%\nsd{Random Characters}\locale\ET.locale
- %User Temp%\nsd{Random Characters}\locale\EU.locale
- %User Temp%\nsd{Random Characters}\locale\FA.locale
- %User Temp%\nsd{Random Characters}\locale\FI.locale
- %User Temp%\nsd{Random Characters}\locale\FR.locale
- %User Temp%\nsd{Random Characters}\locale\GU.locale
- %User Temp%\nsd{Random Characters}\locale\HE.locale
- %User Temp%\nsd{Random Characters}\locale\HI.locale
- %User Temp%\nsd{Random Characters}\locale\HR.locale
- %User Temp%\nsd{Random Characters}\locale\HT.locale
- %User Temp%\nsd{Random Characters}\locale\HU.locale
- %User Temp%\nsd{Random Characters}\locale\HY.locale
- %User Temp%\nsd{Random Characters}\locale\ID.locale
- %User Temp%\nsd{Random Characters}\locale\IS.locale
- %User Temp%\nsd{Random Characters}\locale\IT.locale
- %User Temp%\nsd{Random Characters}\locale\JA.locale
- %User Temp%\nsd{Random Characters}\locale\KA.locale
- %User Temp%\nsd{Random Characters}\locale\KK.locale
- %User Temp%\nsd{Random Characters}\locale\KO.locale
- %User Temp%\nsd{Random Characters}\locale\KU.locale
- %User Temp%\nsd{Random Characters}\locale\LO.locale
- %User Temp%\nsd{Random Characters}\locale\LT.locale
- %User Temp%\nsd{Random Characters}\locale\LV.locale
- %User Temp%\nsd{Random Characters}\locale\MK.locale
- %User Temp%\nsd{Random Characters}\locale\ML.locale
- %User Temp%\nsd{Random Characters}\locale\MR.locale
- %User Temp%\nsd{Random Characters}\locale\MS.locale
- %User Temp%\nsd{Random Characters}\locale\NE.locale
- %User Temp%\nsd{Random Characters}\locale\NL.locale
- %User Temp%\nsd{Random Characters}\locale\NO.locale
- %User Temp%\nsd{Random Characters}\locale\PA.locale
- %User Temp%\nsd{Random Characters}\locale\PL.locale
- %User Temp%\nsd{Random Characters}\locale\PT.locale
- %User Temp%\nsd{Random Characters}\locale\RO.locale
- %User Temp%\nsd{Random Characters}\locale\RU.locale
- %User Temp%\nsd{Random Characters}\locale\SK.locale
- %User Temp%\nsd{Random Characters}\locale\SL.locale
- %User Temp%\nsd{Random Characters}\locale\SQ.locale
- %User Temp%\nsd{Random Characters}\locale\SR.locale
- %User Temp%\nsd{Random Characters}\locale\SV.locale
- %User Temp%\nsd{Random Characters}\locale\TA.locale
- %User Temp%\nsd{Random Characters}\locale\TE.locale
- %User Temp%\nsd{Random Characters}\locale\TH.locale
- %User Temp%\nsd{Random Characters}\locale\TL.locale
- %User Temp%\nsd{Random Characters}\locale\TR.locale
- %User Temp%\nsd{Random Characters}\locale\UK.locale
- %User Temp%\nsd{Random Characters}\locale\UR.locale
- %User Temp%\nsd{Random Characters}\locale\UZ.locale
- %User Temp%\nsd{Random Characters}\locale\VI.locale
- %User Temp%\nsd{Random Characters}\locale\YO.locale
- %User Temp%\nsd{Random Characters}\locale\ZH.locale
- %User Temp%\nsd{Random Characters}\locale\ZU.locale
- %User Temp%\ns14AB5EB1\7E72237D.tmp
- %User Temp%\is-{5 Random Characters}.tmp\rkinstaller.exe
- %User Temp%\is-{5 Random Characters}.tmp\rkverify.exe
- %User Temp%\ns14AB5EB1\0BB0D08C_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %Program Files%\PCMate Free EXE Lock\unins000.dat
- %Program Files%\PCMate Free EXE Lock\unins000.exe
- %Program Files%\PCMate Free EXE Lock\goup.exe
- %Program Files%\PCMate Free EXE Lock\version.dat
- %Program Files%\PCMate Free EXE Lock\PCMate Free EXE Lock Update.exe
- %Program Files%\RelevantKnowledge\rlservice.exe
- %Program Files%\PCMate Free EXE Lock\icon.ico
- %Program Files%\PCMate Free EXE Lock\lamecore.dll
- %Program Files%\RelevantKnowledge\rlls.dll
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock on the Web.url
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock.lnk
- %Programs%\PCMate Free EXE Lock\More Free Tools.url
- %Programs%\PCMate Free EXE Lock\Uninstall.lnk
- %Desktop%\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Windows\Start Menu\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Internet Explorer\Quick Launch\PCMate Free EXE Lock.lnk
- %Program Files%\RelevantKnowledge\rlls64.dll
- %Program Files%\RelevantKnowledge\rlvknlg64.exe
- %Program Files%\RelevantKnowledge\rlvknlg32.exe
- %Program Files%\RelevantKnowledge\rlvknlg.exe
- %System%\rlls.dll
- %Application Data%\PCMate Free EXE Lock New Version Available\update.dat
- %Programs%\RelevantKnowledge\Privacy Policy and Terms of Service.lnk
- %Programs%\RelevantKnowledge\About RelevantKnowledge.lnk
- %Programs%\RelevantKnowledge\Support.lnk
- %Programs%\RelevantKnowledge\Uninstall Instructions.lnk
- %Application Data%\PCMate Free EXE Lock New Version Available\PCMateFreeEXELock.exe
(Nota: %User Temp% es la carpeta Temp del usuario activo, que en el caso de Windows 2000(32-bit), XP y Server 2003(32-bit) suele estar en C:\Documents and Settings\{nombre de usuario}\Local Settings\Temp y en el case de Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) y 10(64-bit) en C:\Users\{nombre de usuario}\AppData\Local\Temp).
. %Program Files% es la carpeta Archivos de programa predeterminada, que suele estar en C:\Archivos de programa).. %Desktop% es la carpeta Escritorio del usuario activo, que en el caso de Windows 98 y ME suele estar en C:\Windows\Profiles\{nombre de usuario}\Escritorio, en el caso de Windows NT en C:\WINNT\Profiles\{nombre de usuario}\Escritorio, en el caso de Windows 2000(32-bit), XP y Server 2003(32-bit) en C:\Documents and Settings\{nombre de usuario}\Escritorio y en el caso de Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) y 10(64-bit) en C:\Users\{nombre de usuario}\Desktop).. %Application Data% es la carpeta Application Data del usuario activo, que en el caso de Windows 98 y ME suele estar ubicada en C:\Windows\Profiles\{nombre de usuario}\Application Data, en el caso de Windows NT en C:\WINNT\Profiles\{nombre de usuario}\Application Data, en el caso de Windows 2000(32-bit), XP y Server 2003(32-bit) en C:\Documents and Settings\{nombre de usuario}\Local Settings\Application Data y en el caso de Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) y 10(64-bit) en C:\Users\{nombre de usuario}\AppData\Roaming.).. %System% es la carpeta del sistema de Windows, que en el caso de Windows 98 y ME suele estar en C:\Windows\System, en el caso de Windows NT y 2000 en C:\WINNT\System32 y en el caso de Windows 2000(32-bit), XP, Server 2003(32-bit), Vista, 7, 8, 8.1, 2008(64-bit), 2012(64bit) y 10(64-bit) en C:\Windows\System32).)Agrega los procesos siguientes:
- netsh firewall add allowedprogram program = "%Program Files%\relevantknowledge\rlvknlg.exe" name = rlvknlg.exe mode = ENABLE scope = ALL
(Nota: %Program Files% es la carpeta Archivos de programa predeterminada, que suele estar en C:\Archivos de programa).
)Técnica de inicio automático
Este malware infiltra el/los archivo(s) siguiente(s) en la carpeta de inicio del usuario de Windows para permitir su ejecución automática cada vez que se inicia el sistema:
- %User Startup%\PCMate Free EXE Lock Update.lnk
(Nota: %User Startup% es la carpeta Inicio del usuario activo, que en el caso de Windows 98 y ME suele estar en C:\Windows\Profiles\{nombre de usuario}\Menú Inicio\Programas\Inicio, en el caso de Windows NT en C:\WINNT\Profiles\{nombre de usuario}\Menú Inicio\Programas\Inicio, en el caso de Windows 2003(32-bit), XP y 2000(32-bit) en C:\Documents and Settings\{nombre de usuario}\Menú Inicio\Programas\Inicio y en en el caso de Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) y 10(64-bit) en C:\Users\{nombre de usuario}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup).
)Otras modificaciones del sistema
Agrega las siguientes entradas de registro:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: Setup Version = 5.6.1 (u)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: App Path = %Program Files%\PCMate Free EXE Lock
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
InstallLocation = %Program Files%\PCMate Free EXE Lock\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: Icon Group = PCMate Free EXE Lock
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: User = {Current user}\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Inno Setup: Language = en_1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
DisplayName = PCMate Free EXE Lock 8.8.1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
UninstallString = UninstallString
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
QuietUninstallString = "%Program Files%\PCMate Free EXE Lock\unins000.exe" /SILENT
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
Publisher = PCMate Software, Inc.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
URLInfoAbout = http://www.{BLOCKED}ware.com/
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
HelpLink = http://www.{BLOCKED}ware.com/
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
URLUpdateInfo = http://www.{BLOCKED}ware.com/
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
NoModify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
NoRepair = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
InstallDate = {Current Date}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
EstimatedSize = 1159
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_owner = 1
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_hhsize = 3
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_num_child = 2
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_region = AL
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
dt_zip = 123123
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
BundleOfferActionUid =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
UninstallString = %Program Files%\RelevantKnowledge\rlvknlg.exe -bootremove -uninst:RelevantKnowledge
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
DisplayName = RelevantKnowledge
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
Publisher = TMRG, Inc.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
EstimatedSize = 5400
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}
DisplayVersion = 1.3.338.311
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Name = x-ns1CnVdsWhT48y,x-ns2EAXCsH$M853
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
HK_Path = %System%\rlls.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
HK64_Path = %System%\rlls64.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
LD64_Path = %Program Files%\RelevantKnowledge\rlvknlg64.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
KS_Path = %Program Files%\RelevantKnowledge\rlls.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
SV_Path = %Program Files%\RelevantKnowledge\rlservice.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
RunLine = %Program Files%\relevantknowledge\rlvknlg.exe –boot
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
ServiceName = RelevantKnowledge
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
OSSProxyPID = 3052
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
SendContentIDToServer = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Capabilities = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
ExtCapabilities = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
OptionsBitmask = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
RevertPath = %Program Files%\RelevantKnowledge\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Installed = 77 47 00 00
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Ipcountry = PH
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
instLanguage = 1033
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
UninstURL = http://www.{BLOCKED}owledge.com/con{BLOCKED}all.aspx?siteid=2600&campaign_id=878
Otros detalles
Agrega las siguientes entradas de registro como parte de la rutina de instalación:
HKEY_CURRENT_USER\Software\Microsoft\
RestartManager\Session0000
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
PCMate Free EXE Lock_is1
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP
HKEY_LOCAL_MACHINE\SOFTWARE\MC_MediaProSoft_DDMP_PP\
878
HKEY_LOCAL_MACHINE\SOFTWARE\FreeExeLock
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{d08d9f98-1c78-4704-87e6-368b0023d831}\Config\OSSProxy\
Settings
Se conecta al sitio Web siguiente para enviar y recibir información:
- rp.{BLOCKED}verseapplication.com
- dpd.{BLOCKED}studies.com
- http://www.{BLOCKED}temsoftware.com/downloadfile/PCMateFreeEXELockFull.exe
- post.{BLOCKED}studies.com
- {BLOCKED}nloadpr.com
Hace lo siguiente:
- It displays the following during installation:
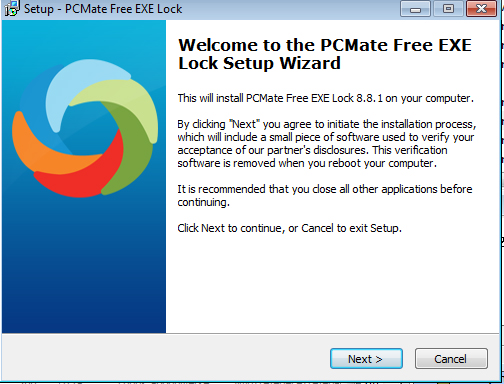
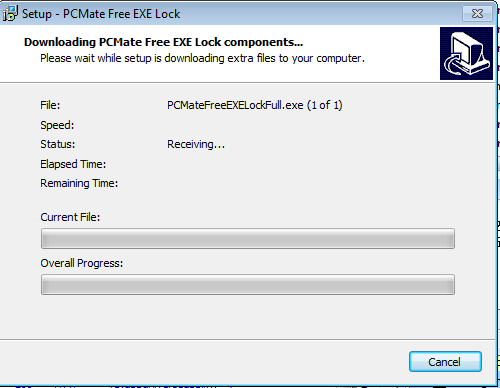
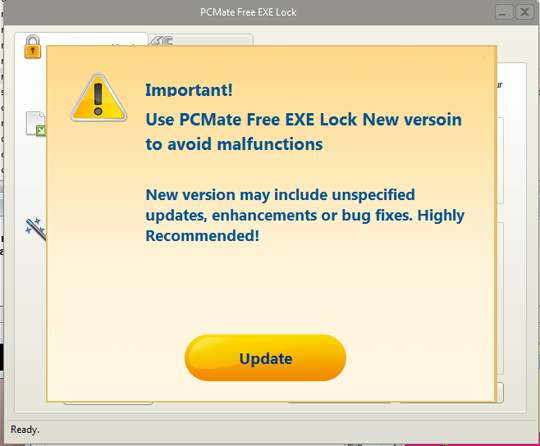
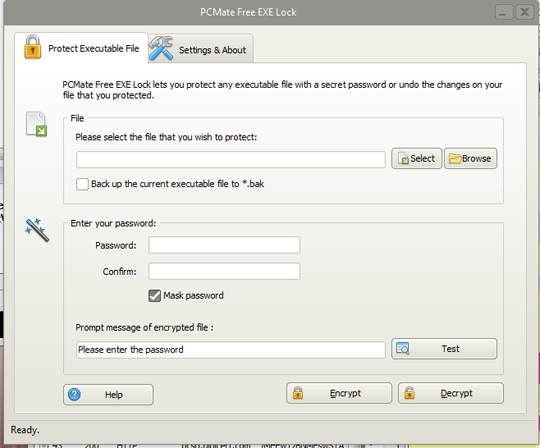
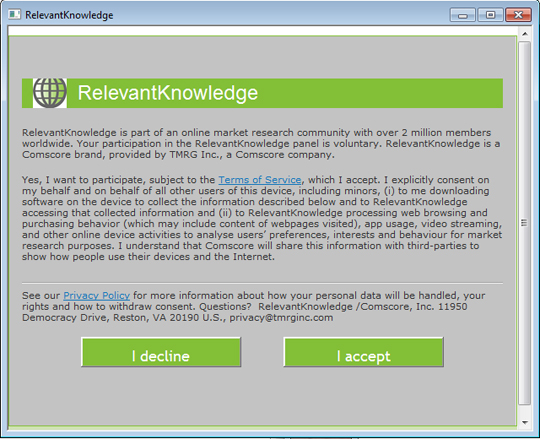
Soluciones
Step 1
Los usuarios de Windows ME y XP, antes de llevar a cabo cualquier exploración, deben comprobar que tienen desactivada la opción Restaurar sistema para permitir la exploración completa del equipo.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Reiniciar en modo seguro
Step 4
Quitar Adware.Win32.FusionCore.AD por medio de su propia opción de desinstalación
Step 5
Eliminar esta clave del Registro
Importante: si modifica el Registro de Windows incorrectamente, podría hacer que el sistema funcione mal de manera irreversible. Lleve a cabo este paso solo si sabe cómo hacerlo o si puede contar con ayuda de su administrador del sistema. De lo contrario, lea este artículo de Microsoft antes de modificar el Registro del equipo.
- In HKEY_CURRENT_USER\Software\Microsoft\RestartManager
- Session0000
- Session0000
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
- PCMate Free EXE Lock_is1
- PCMate Free EXE Lock_is1
- In HKEY_LOCAL_MACHINE\SOFTWARE
- MC_MediaProSoft_DDMP_PP
- MC_MediaProSoft_DDMP_PP
- In HKEY_LOCAL_MACHINE\SOFTWARE
- FreeExeLock
- FreeExeLock
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{d08d9f98-1c78-4704-87e6-368b0023d831}
- Config
- Config
Step 6
Buscar y eliminar estos archivos
- %User Temp%\is-{5 Random Characters}.tmp\{Malware name}.tmp
- %User Temp%\is-{5 Random Characters}.tmp\OqIEFuprtaC.dll
- %User Temp%\is-{5 Random Characters}.tmp\itdownload.dll
- %User Temp%\is-{5 Random Characters}.tmp\isxdl.dll
- %User Temp%\nsd{Random Characters}\csshover3.htc
- %User Temp%\nsd{Random Characters}\css\ie6_main.css
- %User Temp%\nsd{Random Characters}\css\main.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\browse.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\checkbox.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\progress-bar.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\button-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg-corner.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg2.png
- %User Temp%\nsd{Random Characters}\images\Loader.gif
- %User Temp%\nsd{Random Characters}\locale\AF.locale
- %User Temp%\nsd{Random Characters}\locale\AZ.locale
- %User Temp%\nsd{Random Characters}\locale\BE.locale
- %User Temp%\nsd{Random Characters}\locale\BG.locale
- %User Temp%\nsd{Random Characters}\locale\BS.locale
- %User Temp%\nsd{Random Characters}\locale\CA.locale
- %User Temp%\nsd{Random Characters}\locale\CS.locale
- %User Temp%\nsd{Random Characters}\locale\DA.locale
- %User Temp%\nsd{Random Characters}\locale\DE.locale
- %User Temp%\nsd{Random Characters}\locale\EL.locale
- %User Temp%\nsd{Random Characters}\locale\EN.locale
- %User Temp%\nsd{Random Characters}\locale\ES.locale
- %User Temp%\nsd{Random Characters}\locale\ET.locale
- %User Temp%\nsd{Random Characters}\locale\EU.locale
- %User Temp%\nsd{Random Characters}\locale\FA.locale
- %User Temp%\nsd{Random Characters}\locale\FI.locale
- %User Temp%\nsd{Random Characters}\locale\FR.locale
- %User Temp%\nsd{Random Characters}\locale\GU.locale
- %User Temp%\nsd{Random Characters}\locale\HE.locale
- %User Temp%\nsd{Random Characters}\locale\HI.locale
- %User Temp%\nsd{Random Characters}\locale\HR.locale
- %User Temp%\nsd{Random Characters}\locale\HT.locale
- %User Temp%\nsd{Random Characters}\locale\HU.locale
- %User Temp%\nsd{Random Characters}\locale\HY.locale
- %User Temp%\nsd{Random Characters}\locale\ID.locale
- %User Temp%\nsd{Random Characters}\locale\IS.locale
- %User Temp%\nsd{Random Characters}\locale\IT.locale
- %User Temp%\nsd{Random Characters}\locale\JA.locale
- %User Temp%\nsd{Random Characters}\locale\KA.locale
- %User Temp%\nsd{Random Characters}\locale\KK.locale
- %User Temp%\nsd{Random Characters}\locale\KO.locale
- %User Temp%\nsd{Random Characters}\locale\KU.locale
- %User Temp%\nsd{Random Characters}\locale\LO.locale
- %User Temp%\nsd{Random Characters}\locale\LT.locale
- %User Temp%\nsd{Random Characters}\locale\LV.locale
- %User Temp%\nsd{Random Characters}\locale\MK.locale
- %User Temp%\nsd{Random Characters}\locale\ML.locale
- %User Temp%\nsd{Random Characters}\locale\MR.locale
- %User Temp%\nsd{Random Characters}\locale\MS.locale
- %User Temp%\nsd{Random Characters}\locale\NE.locale
- %User Temp%\nsd{Random Characters}\locale\NL.locale
- %User Temp%\nsd{Random Characters}\locale\NO.locale
- %User Temp%\nsd{Random Characters}\locale\PA.locale
- %User Temp%\nsd{Random Characters}\locale\PL.locale
- %User Temp%\nsd{Random Characters}\locale\PT.locale
- %User Temp%\nsd{Random Characters}\locale\RO.locale
- %User Temp%\nsd{Random Characters}\locale\RU.locale
- %User Temp%\nsd{Random Characters}\locale\SK.locale
- %User Temp%\nsd{Random Characters}\locale\SL.locale
- %User Temp%\nsd{Random Characters}\locale\SQ.locale
- %User Temp%\nsd{Random Characters}\locale\SR.locale
- %User Temp%\nsd{Random Characters}\locale\SV.locale
- %User Temp%\nsd{Random Characters}\locale\TA.locale
- %User Temp%\nsd{Random Characters}\locale\TE.locale
- %User Temp%\nsd{Random Characters}\locale\TH.locale
- %User Temp%\nsd{Random Characters}\locale\TL.locale
- %User Temp%\nsd{Random Characters}\locale\TR.locale
- %User Temp%\nsd{Random Characters}\locale\UK.locale
- %User Temp%\nsd{Random Characters}\locale\UR.locale
- %User Temp%\nsd{Random Characters}\locale\UZ.locale
- %User Temp%\nsd{Random Characters}\locale\VI.locale
- %User Temp%\nsd{Random Characters}\locale\YO.locale
- %User Temp%\nsd{Random Characters}\locale\ZH.locale
- %User Temp%\nsd{Random Characters}\locale\ZU.locale
- %User Temp%\ns14AB5EB1\7E72237D.tmp
- %User Temp%\is-{5 Random Characters}.tmp\rkinstaller.exe
- %User Temp%\is-{5 Random Characters}.tmp\rkverify.exe
- %User Temp%\ns14AB5EB1\0BB0D08C_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %Program Files%\PCMate Free EXE Lock\unins000.dat
- %Program Files%\PCMate Free EXE Lock\unins000.exe
- %Program Files%\PCMate Free EXE Lock\goup.exe
- %Program Files%\PCMate Free EXE Lock\version.dat
- %Program Files%\PCMate Free EXE Lock\PCMate Free EXE Lock Update.exe
- %Program Files%\RelevantKnowledge\rlservice.exe
- %Program Files%\PCMate Free EXE Lock\icon.ico
- %Program Files%\PCMate Free EXE Lock\lamecore.dll
- %Program Files%\RelevantKnowledge\rlls.dll
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock on the Web.url
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock.lnk
- %Programs%\PCMate Free EXE Lock\More Free Tools.url
- %Programs%\PCMate Free EXE Lock\Uninstall.lnk
- %Desktop%\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Windows\Start Menu\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Internet Explorer\Quick Launch\PCMate Free EXE Lock.lnk
- %Program Files%\RelevantKnowledge\rlls64.dll
- %Program Files%\RelevantKnowledge\rlvknlg64.exe
- %Program Files%\RelevantKnowledge\rlvknlg32.exe
- %Program Files%\RelevantKnowledge\rlvknlg.exe
- %System%\rlls.dll
- %Application Data%\PCMate Free EXE Lock New Version Available\update.dat
- %Programs%\RelevantKnowledge\Privacy Policy and Terms of Service.lnk
- %Programs%\RelevantKnowledge\About RelevantKnowledge.lnk
- %Programs%\RelevantKnowledge\Support.lnk
- %Programs%\RelevantKnowledge\Uninstall Instructions.lnk
- %Application Data%\PCMate Free EXE Lock New Version Available\PCMateFreeEXELock.exe
- %User Temp%\is-{5 Random Characters}.tmp\{Malware name}.tmp
- %User Temp%\is-{5 Random Characters}.tmp\OqIEFuprtaC.dll
- %User Temp%\is-{5 Random Characters}.tmp\itdownload.dll
- %User Temp%\is-{5 Random Characters}.tmp\isxdl.dll
- %User Temp%\nsd{Random Characters}\csshover3.htc
- %User Temp%\nsd{Random Characters}\css\ie6_main.css
- %User Temp%\nsd{Random Characters}\css\main.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\browse.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\checkbox.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\progress-bar.css
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\button-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg-corner.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg.png
- %User Temp%\nsd{Random Characters}\css\sdk-ui\images\progress-bg2.png
- %User Temp%\nsd{Random Characters}\images\Loader.gif
- %User Temp%\nsd{Random Characters}\locale\AF.locale
- %User Temp%\nsd{Random Characters}\locale\AZ.locale
- %User Temp%\nsd{Random Characters}\locale\BE.locale
- %User Temp%\nsd{Random Characters}\locale\BG.locale
- %User Temp%\nsd{Random Characters}\locale\BS.locale
- %User Temp%\nsd{Random Characters}\locale\CA.locale
- %User Temp%\nsd{Random Characters}\locale\CS.locale
- %User Temp%\nsd{Random Characters}\locale\DA.locale
- %User Temp%\nsd{Random Characters}\locale\DE.locale
- %User Temp%\nsd{Random Characters}\locale\EL.locale
- %User Temp%\nsd{Random Characters}\locale\EN.locale
- %User Temp%\nsd{Random Characters}\locale\ES.locale
- %User Temp%\nsd{Random Characters}\locale\ET.locale
- %User Temp%\nsd{Random Characters}\locale\EU.locale
- %User Temp%\nsd{Random Characters}\locale\FA.locale
- %User Temp%\nsd{Random Characters}\locale\FI.locale
- %User Temp%\nsd{Random Characters}\locale\FR.locale
- %User Temp%\nsd{Random Characters}\locale\GU.locale
- %User Temp%\nsd{Random Characters}\locale\HE.locale
- %User Temp%\nsd{Random Characters}\locale\HI.locale
- %User Temp%\nsd{Random Characters}\locale\HR.locale
- %User Temp%\nsd{Random Characters}\locale\HT.locale
- %User Temp%\nsd{Random Characters}\locale\HU.locale
- %User Temp%\nsd{Random Characters}\locale\HY.locale
- %User Temp%\nsd{Random Characters}\locale\ID.locale
- %User Temp%\nsd{Random Characters}\locale\IS.locale
- %User Temp%\nsd{Random Characters}\locale\IT.locale
- %User Temp%\nsd{Random Characters}\locale\JA.locale
- %User Temp%\nsd{Random Characters}\locale\KA.locale
- %User Temp%\nsd{Random Characters}\locale\KK.locale
- %User Temp%\nsd{Random Characters}\locale\KO.locale
- %User Temp%\nsd{Random Characters}\locale\KU.locale
- %User Temp%\nsd{Random Characters}\locale\LO.locale
- %User Temp%\nsd{Random Characters}\locale\LT.locale
- %User Temp%\nsd{Random Characters}\locale\LV.locale
- %User Temp%\nsd{Random Characters}\locale\MK.locale
- %User Temp%\nsd{Random Characters}\locale\ML.locale
- %User Temp%\nsd{Random Characters}\locale\MR.locale
- %User Temp%\nsd{Random Characters}\locale\MS.locale
- %User Temp%\nsd{Random Characters}\locale\NE.locale
- %User Temp%\nsd{Random Characters}\locale\NL.locale
- %User Temp%\nsd{Random Characters}\locale\NO.locale
- %User Temp%\nsd{Random Characters}\locale\PA.locale
- %User Temp%\nsd{Random Characters}\locale\PL.locale
- %User Temp%\nsd{Random Characters}\locale\PT.locale
- %User Temp%\nsd{Random Characters}\locale\RO.locale
- %User Temp%\nsd{Random Characters}\locale\RU.locale
- %User Temp%\nsd{Random Characters}\locale\SK.locale
- %User Temp%\nsd{Random Characters}\locale\SL.locale
- %User Temp%\nsd{Random Characters}\locale\SQ.locale
- %User Temp%\nsd{Random Characters}\locale\SR.locale
- %User Temp%\nsd{Random Characters}\locale\SV.locale
- %User Temp%\nsd{Random Characters}\locale\TA.locale
- %User Temp%\nsd{Random Characters}\locale\TE.locale
- %User Temp%\nsd{Random Characters}\locale\TH.locale
- %User Temp%\nsd{Random Characters}\locale\TL.locale
- %User Temp%\nsd{Random Characters}\locale\TR.locale
- %User Temp%\nsd{Random Characters}\locale\UK.locale
- %User Temp%\nsd{Random Characters}\locale\UR.locale
- %User Temp%\nsd{Random Characters}\locale\UZ.locale
- %User Temp%\nsd{Random Characters}\locale\VI.locale
- %User Temp%\nsd{Random Characters}\locale\YO.locale
- %User Temp%\nsd{Random Characters}\locale\ZH.locale
- %User Temp%\nsd{Random Characters}\locale\ZU.locale
- %User Temp%\ns14AB5EB1\7E72237D.tmp
- %User Temp%\is-{5 Random Characters}.tmp\rkinstaller.exe
- %User Temp%\is-{5 Random Characters}.tmp\rkverify.exe
- %User Temp%\ns14AB5EB1\0BB0D08C_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %User Temp%\ns14AB5EB1\113261AE_stp.dat.part
- %Program Files%\PCMate Free EXE Lock\unins000.dat
- %Program Files%\PCMate Free EXE Lock\unins000.exe
- %Program Files%\PCMate Free EXE Lock\goup.exe
- %Program Files%\PCMate Free EXE Lock\version.dat
- %Program Files%\PCMate Free EXE Lock\PCMate Free EXE Lock Update.exe
- %Program Files%\RelevantKnowledge\rlservice.exe
- %Program Files%\PCMate Free EXE Lock\icon.ico
- %Program Files%\PCMate Free EXE Lock\lamecore.dll
- %Program Files%\RelevantKnowledge\rlls.dll
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock on the Web.url
- %Programs%\PCMate Free EXE Lock\PCMate Free EXE Lock.lnk
- %Programs%\PCMate Free EXE Lock\More Free Tools.url
- %Programs%\PCMate Free EXE Lock\Uninstall.lnk
- %Desktop%\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Windows\Start Menu\PCMate Free EXE Lock.lnk
- %Application Data%\Microsoft\Internet Explorer\Quick Launch\PCMate Free EXE Lock.lnk
- %Program Files%\RelevantKnowledge\rlls64.dll
- %Program Files%\RelevantKnowledge\rlvknlg64.exe
- %Program Files%\RelevantKnowledge\rlvknlg32.exe
- %Program Files%\RelevantKnowledge\rlvknlg.exe
- %System%\rlls.dll
- %Application Data%\PCMate Free EXE Lock New Version Available\update.dat
- %Programs%\RelevantKnowledge\Privacy Policy and Terms of Service.lnk
- %Programs%\RelevantKnowledge\About RelevantKnowledge.lnk
- %Programs%\RelevantKnowledge\Support.lnk
- %Programs%\RelevantKnowledge\Uninstall Instructions.lnk
- %Application Data%\PCMate Free EXE Lock New Version Available\PCMateFreeEXELock.exe
Step 7
Reinicie en modo normal y explore el equipo con su producto de Trend Micro para buscar los archivos identificados como Adware.Win32.FusionCore.AD En caso de que el producto de Trend Micro ya haya limpiado, eliminado o puesto en cuarentena los archivos detectados, no serán necesarios más pasos. Puede optar simplemente por eliminar los archivos en cuarentena. Consulte esta página de Base de conocimientos para obtener más información.
Rellene nuestra encuesta!

