From Infection to Extortion: Watch TorrentLocker In Action
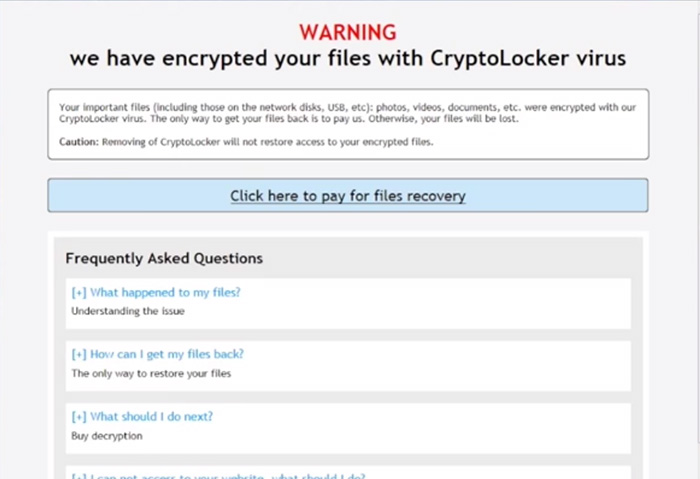 It’s rare to see malware at work without having to deal with its ruinous consequences, but here and now, through a Deakin University-Trend Micro collaborative effort, we present a video of the notorious TorrentLocker—a ransomware variant used in attacks that targeted users in the ANZ (Australia-New Zealand) region—in action. The video in full details every step of the infection process, showing just how sophisticated and damaging this ransomware could be.
It’s rare to see malware at work without having to deal with its ruinous consequences, but here and now, through a Deakin University-Trend Micro collaborative effort, we present a video of the notorious TorrentLocker—a ransomware variant used in attacks that targeted users in the ANZ (Australia-New Zealand) region—in action. The video in full details every step of the infection process, showing just how sophisticated and damaging this ransomware could be.
[More: TorrentLocker and Its Effect on the Australian Web Threat Landscape]
Ever since TorrentLocker emerged in the threat landscape, it has affected users from all over the world, preventing victims from accessing their own files and documents unless they fork over a hefty fee (in the video, we see that the required ransom is A$598, or US$491). With no way to recover their files due to the encryption method used, victims without up-to-date backups are faced with the hard decision of either losing their data and starting from scratch, or paying the ransom. The former has them dealing with the obvious hit in productivity (or revenue, in a business setting) and the latter option has them not only suffering a financial loss they shouldn’t have to deal with, but also the onus of financing these cybercriminals.
Thankfully, it’s not a hopeless cause, as the video also depicts the series of voluntary steps that users have to undertake before TorrentLocker infects their computers. Users still have to go to the spoofed website, enter the CAPTCHA, then download the offered archive, and so on – steps where infection can be avoided if they are not carried out.
And the only way to enable the users to be able to stop themselves from executing these steps is to increase their awareness of the threat – how it presents itself, how it tricks them with a social engineering lure, and how bad the archive they’re being asked to download is.
Information is the key to stopping TorrentLocker and other ransomware threats.
You can view the video in full below.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks